What is the anti-corruption layer pattern in system design? It’s a crucial architectural technique for building robust and maintainable systems, particularly when interacting with external sources. This pattern acts as a protective barrier, safeguarding the core application from the complexities and inconsistencies of external systems. Understanding its components, principles, and implementation strategies is vital for crafting effective and resilient software.
The anti-corruption layer pattern in system design is a critical component for managing data integrity and consistency when dealing with external systems. It’s particularly relevant in scenarios where data needs transformation, validation, or adaptation to fit within the internal structure of the application. By isolating the core application from external data sources, this pattern enables greater flexibility and maintainability.
This detailed exploration will cover the defining characteristics, key components, and various implementation approaches.
Defining the Anti-Corruption Layer
The anti-corruption layer pattern in system design is a crucial component for building robust and adaptable systems. It acts as a bridge between the core domain logic and external, potentially inconsistent or incompatible systems. This layer shields the core domain from external complexities, ensuring its integrity and maintainability.This pattern is vital in scenarios where a system interacts with legacy systems, third-party APIs, or databases with unusual schemas.
It allows for a consistent interface while isolating the domain logic from the specific implementation details of these external resources. This promotes a clear separation of concerns, facilitating easier maintenance, testing, and evolution of the system.
Core Principles of the Anti-Corruption Layer
The anti-corruption layer’s core principles revolve around decoupling and abstraction. It aims to create a consistent, predictable interface for the domain logic to interact with external systems, regardless of the underlying complexities. This separation prevents the domain model from being burdened by the intricacies of external data sources, thereby improving maintainability and testability.
Intent and Goals of the Anti-Corruption Layer
The primary intent of the anti-corruption layer is to protect the core domain model from the inconsistencies and complexities of external systems. Its goals include:
- Providing a consistent and well-defined interface to the domain model, irrespective of the external systems it interacts with.
- Maintaining the integrity of the domain model by shielding it from the variations and potential inconsistencies in external data.
- Facilitating easier testing and maintenance by isolating the domain model from external dependencies.
- Enhancing the adaptability of the system by allowing for easier replacement or modification of external systems without affecting the core domain model.
Characteristics Distinguishing the Anti-Corruption Layer
The anti-corruption layer differentiates itself from other approaches by its specific characteristics:
- Abstraction and Consistency: It abstracts the external system’s complexities, presenting a consistent interface to the domain model, regardless of the underlying implementations. This allows for seamless integration with different external systems without impacting the domain model.
- Decoupling: It decouples the domain model from the external systems, promoting maintainability and testability. Changes in external systems do not necessitate changes to the domain model.
- Fault Tolerance: The anti-corruption layer can handle failures or inconsistencies from external systems, preventing these issues from propagating to the core domain model. This crucial characteristic ensures system stability.
- Data Transformation: It often involves transforming data from the external system’s format into the format expected by the domain model. This ensures data integrity and consistency.
Conceptual Diagram of an Anti-Corruption Layer
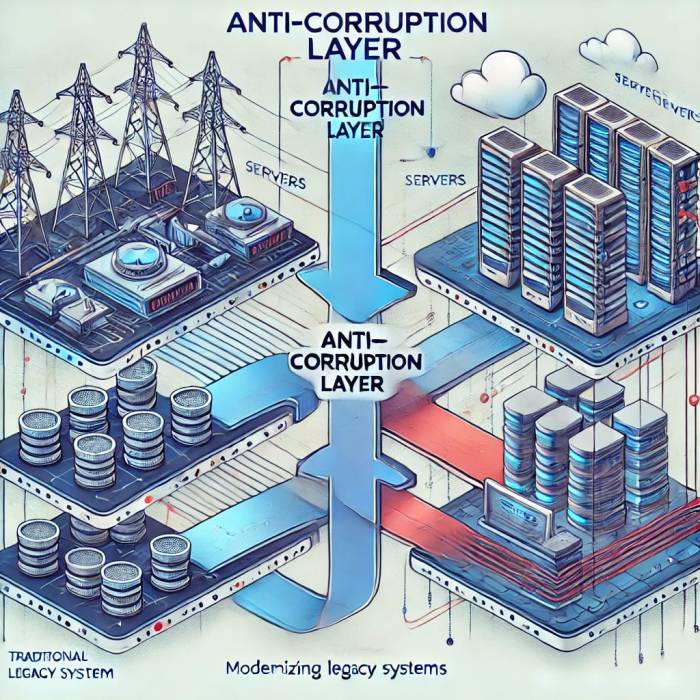
The following diagram illustrates a basic structure of an anti-corruption layer:“`+—————–+ +—————–+ +—————–+| External System | | Anti-Corruption | | Domain Model |+—————–+ +—————–+ +—————–+| Data | –> | Adapter/Mapper | –> | Logic || (e.g., API) | | (Data Conversion)| | |+—————–+ +—————–+ +—————–+“`The diagram depicts the flow of data from an external system to the domain model through the anti-corruption layer.
The layer acts as a translator, converting data formats and handling potential inconsistencies. The domain model remains unaware of the specific nature of the external system, ensuring its independence and maintainability.
Identifying Key Components

The anti-corruption layer acts as a crucial intermediary, safeguarding data integrity and ensuring consistency between the external systems and the core application. This intermediary role necessitates a structured approach to component design, enabling seamless interaction and minimizing potential vulnerabilities. Understanding the specific components and their interaction points is vital for effective implementation and maintenance.The anti-corruption layer’s components are designed to translate between the specific formats and structures of external systems and the internal data model of the core application.
This translation process often involves data transformation, validation, and normalization. These processes are critical to maintain data integrity and prevent inconsistencies that could lead to corrupted or inaccurate information within the application.
Different Components within the Anti-Corruption Layer
The anti-corruption layer typically comprises several key components, each with distinct responsibilities. This modular approach facilitates maintainability and adaptability to changing external systems.
- Data Transfer Objects (DTOs): DTOs are data containers used to represent data in a standardized format. They are used for communication between the external systems and the anti-corruption layer. DTOs ensure consistent data structures for various data sources, facilitating efficient data translation. DTOs act as the intermediary for data exchanged, encapsulating and transforming data into the format required by the core application.
For example, an external system might use a JSON format, while the internal application uses a relational database format. DTOs translate between these formats, ensuring consistency and preventing data corruption.
- Adapters: Adapters are responsible for interacting with external systems. They encapsulate the specifics of each external system’s interface, providing a unified interface for the rest of the anti-corruption layer. This encapsulation shields the core application from the complexities of the external systems’ specific communication protocols and formats. Adapters provide a layer of abstraction that allows the core application to interact with external systems without needing to know the details of their internal structures.
This enhances flexibility, allowing for the replacement of external systems without impacting the core application.
- Data Mappers: Data mappers handle the transformation of data between the external formats and the internal data model. They translate data from the external DTOs into the format required by the application’s internal data structures. They are essential for handling discrepancies in data structures between external and internal systems. This process ensures data integrity and prevents inconsistencies that could arise from mismatched data types or structures.
- Validation Logic: This component ensures data validity and consistency. It performs checks on data received from external systems, validating its format, constraints, and business rules. This validation process prevents corrupted or invalid data from entering the system. Validation logic is crucial to maintaining data quality and preventing potential issues further down the line.
Interaction Points
The anti-corruption layer interacts with several parts of the system. Understanding these interaction points is essential for efficient design and implementation.
- External Systems: The adapters directly interact with external systems to retrieve and send data. This interaction is governed by the specific protocols and interfaces of each external system.
- Core Application: The anti-corruption layer serves as a bridge, providing the core application with data in a consistent format, free from external system dependencies.
- Data Storage: The data mappers translate data to and from the internal data structures, which are often stored in a database.
Components, Roles, and Responsibilities
The table below summarizes the components, their roles, and responsibilities within the anti-corruption layer.
| Component | Role | Responsibility |
|---|---|---|
| Data Transfer Objects (DTOs) | Data Representation | Standardize data format for external communication |
| Adapters | External System Interaction | Interact with external systems and handle communication protocols |
| Data Mappers | Data Transformation | Translate data between external and internal formats |
| Validation Logic | Data Integrity | Validate data for consistency and validity |
Illustrative Examples
The anti-corruption layer, a crucial component in robust system design, acts as a buffer between the application and external systems or data sources. This layer ensures data integrity and consistency, safeguarding against inconsistencies or malicious data. Its importance becomes evident in systems handling sensitive information or interacting with legacy systems. This section presents real-world and simplified examples to illustrate its practical application.
Real-World Example: Financial Transaction Processing
A financial institution’s transaction processing system often interacts with various external systems (e.g., banks, payment gateways). These interactions can involve complex data formats and stringent validation rules. The anti-corruption layer in this scenario plays a vital role. It receives raw transaction data from external sources, validates its format, and transforms it into the internal format required by the core application.
This layer also enforces business rules, such as transaction limits and fraud detection policies. Critically, it isolates the core application from fluctuations in external data formats or unexpected data structures. This ensures the application remains stable and reliable, even as external systems evolve.
Simplified Example: E-commerce Order Processing
Consider a simple e-commerce system that integrates with a shipping provider’s API. The shipping provider’s API might use a different data format and naming conventions than the e-commerce system’s internal representation. The anti-corruption layer would translate the shipping provider’s data into the e-commerce system’s format. Furthermore, it would ensure data validation, such as checking for valid address formats and tracking numbers.
This layer also handles potential errors, like address validation failures, ensuring smooth order processing even with errors from the external system. This ensures data integrity and a smooth customer experience.
Detailed Description of Data Transformation and Business Rules
The anti-corruption layer in the e-commerce example translates the shipping provider’s data structure into the e-commerce system’s structure. This might involve mapping fields like `shippingAddress` to `customerShippingAddress`, and `trackingNumber` to `orderTracking`. Furthermore, the layer validates the shipping address format against predefined rules. If an address is invalid, the layer returns an appropriate error to the application, preventing further processing.
Business rules, such as checking for valid shipping zones, are also enforced. The layer ensures that the application only processes data that meets defined criteria. These transformations are crucial for maintaining data consistency across different systems.
Comparison: With and Without Anti-Corruption Layer
| Feature | With Anti-Corruption Layer | Without Anti-Corruption Layer |
|---|---|---|
| Data Transformation | Data from external systems is transformed into the internal format. | Data from external systems is directly integrated into the core application. |
| Data Validation | Data is validated against predefined rules. | Data validation is not handled. Potentially erroneous data is passed to the application. |
| Business Rules Enforcement | Business rules are enforced to ensure data integrity. | Business rules are not enforced, increasing the risk of invalid or inconsistent data. |
| System Stability | Application remains stable despite changes in external systems. | Application is more susceptible to failures caused by changes in external systems. |
| Error Handling | Errors from external systems are handled gracefully, preventing crashes. | Errors from external systems might crash the application. |
Data Transformations and Validation
The anti-corruption layer acts as a crucial intermediary between external systems and the core application. This layer is responsible for transforming data received from external sources into a format compatible with the application’s internal structure. Data validation ensures that the received data meets specific criteria, preventing inconsistencies and errors within the core application.Data transformation and validation are paramount for maintaining data integrity and consistency.
Errors in data handling can lead to critical issues in the application, impacting its functionality and potentially causing business losses. The anti-corruption layer addresses these concerns, ensuring that only reliable and valid data flows into the core application.
Data Transformation Mechanisms
The anti-corruption layer employs various mechanisms to transform data from external formats into the internal format expected by the application. These mechanisms facilitate seamless data integration. Transformation methods often include mapping fields, converting data types, and normalizing data values. For instance, an external system might store dates in a different format (e.g., YYYY-MM-DD versus MM/DD/YYYY). The anti-corruption layer will convert these to a uniform format used within the application.
Data Validation Strategies
Data validation is a critical aspect of the anti-corruption layer, ensuring that the data received from external sources adheres to predefined rules and constraints. Robust validation mechanisms prevent erroneous data from entering the core application.
- Data Type Validation: This involves verifying that data fields conform to the expected data types (e.g., integers, strings, dates). For example, an email address should be validated to ensure it adheres to the required format. This validation prevents errors in calculations or other operations that might arise from mismatched data types.
- Range Validation: This checks if data values fall within acceptable ranges. For example, an order quantity cannot be negative or exceed a predefined maximum. Such checks ensure the validity of data and prevent unexpected outcomes in the application.
- Format Validation: This checks if data conforms to specific formats, like email addresses, phone numbers, or credit card numbers. This validation prevents data entry errors and ensures data quality.
- Business Rule Validation: This validates data against specific business rules. For example, a product’s price cannot be negative or exceed a certain limit. These checks guarantee that data adheres to established business policies.
- Uniqueness Validation: This ensures that data values are unique within a particular context. For example, customer IDs should be unique across all customers. This validation avoids redundancy and maintains data consistency.
Data Preparation for Core Application
The anti-corruption layer meticulously prepares the transformed and validated data for use within the core application. This includes:
- Data Cleaning: The layer cleans up data by removing or correcting inconsistencies or errors. For example, handling missing values or converting non-standard formats to standard formats.
- Data Enrichment: The layer might enrich the data by adding additional relevant information, such as location details based on an address. This step improves the data’s completeness and usability.
- Data Aggregation: Data from multiple sources might be aggregated into a single format. This might involve combining data from different external systems into a unified view.
Illustrative Example
Consider an e-commerce application that integrates with a third-party shipping provider. The shipping provider might send order data in a specific XML format. The anti-corruption layer would transform this XML data into the application’s internal database format. Crucially, it would validate the order data, ensuring that the order ID exists, the quantity is positive, and the shipping address is valid.
Only then would the data be passed to the core application. This example highlights the importance of data transformation and validation to maintain the integrity and consistency of the data.
Business Rules Enforcement
The anti-corruption layer plays a crucial role in enforcing business rules, acting as a gatekeeper between the external system and the internal application. This ensures that data and operations adhere to the specific constraints and policies of the business. By encapsulating these rules within the layer, the core application logic remains isolated and focused on its core functionality.The anti-corruption layer defines and implements business rules in a structured manner.
This separation allows for easier maintenance, modification, and testing of these rules, as they are not embedded within the core application logic. This promotes flexibility and adaptability as business requirements evolve.
Defining Business Rules
Business rules are specific statements that define acceptable actions or conditions within a business process. They are often expressed in a declarative manner, describing the desired behavior rather than the implementation details. These rules are critical to ensuring data integrity and operational consistency. For example, a rule might specify that a customer order cannot exceed a certain value without explicit approval.
Properly defined business rules minimize errors and ensure compliance.
Implementing Business Rules
The anti-corruption layer implements these rules using various techniques. These techniques include but are not limited to:
- Validation: Data received from external systems is validated against the defined business rules. This ensures that the data conforms to expected formats, ranges, and constraints. For instance, validating that a date is within a specific range or that a product code exists in the catalog.
- Authorization: The layer verifies that the user or system initiating the request has the necessary permissions to perform the operation. This prevents unauthorized access or modification of data. For example, only authorized personnel can update customer credit limits.
- Transformation: Data from external sources may need to be transformed to meet the format expectations of the internal system. This transformation process can also apply business rules during the conversion. For instance, converting a currency to the internal system’s currency or translating a unit of measurement.
- Workflow Management: Complex business rules may require a workflow engine to manage the steps involved in processing a request. For instance, an order fulfillment process may require approvals from different departments.
Example Business Rule and Implementation
Consider a business rule stating that “A customer’s order cannot exceed their credit limit.”
- Definition: The business rule states that the total amount of an order cannot be greater than the customer’s pre-approved credit limit.
- Implementation in the Anti-Corruption Layer: The anti-corruption layer receives the order details from the external system. It retrieves the customer’s credit limit from the internal database. It then compares the order total with the credit limit. If the order total exceeds the credit limit, an error is returned to the external system, preventing the order from proceeding further. Otherwise, the order is processed.
Different Types of Business Rules and Enforcement Methods
| Rule Type | Description | Enforcement Method |
|---|---|---|
| Data Validation | Ensuring data conforms to predefined formats and constraints | Input validation, data type checking |
| Authorization | Controlling access to resources based on user roles and permissions | Authentication, authorization checks |
| Workflow Management | Defining steps and approvals required for a process | Workflow engine, task assignment |
| Calculation | Performing calculations based on input values and predefined formulas | Mathematical calculations, formula evaluation |
Adapting to External Systems
The anti-corruption layer’s effectiveness hinges on its ability to seamlessly integrate with various external systems. This necessitates robust mechanisms for handling diverse data formats, communication protocols, and ensuring interoperability. A well-designed layer acts as a translator and validator, shielding the core application from the complexities of external interactions.The adaptability of the anti-corruption layer is crucial for maintaining a consistent and reliable data flow between the internal system and external sources.
This adaptability encompasses the ability to translate different data formats, handle diverse communication protocols, and ensure interoperability with existing systems. It also facilitates the introduction of new external systems without significant changes to the core application.
Data Format Handling
Different external systems employ various data formats, including JSON, XML, CSV, or proprietary formats. The anti-corruption layer must effectively parse and translate these formats into a consistent internal format understandable by the core application. This conversion process often involves data transformation, validation, and potential enrichment based on the specific needs of the application.
Communication Protocol Adaptability
External systems may utilize diverse communication protocols like REST APIs, SOAP Web services, or message queues. The anti-corruption layer should support these varying protocols to enable seamless communication. This involves selecting appropriate libraries and frameworks for each protocol and handling potential differences in request/response structures. Furthermore, the layer should implement robust error handling and retry mechanisms to manage transient network issues or system failures.
Ensuring Interoperability
Interoperability between the internal system and external systems is a key consideration. The anti-corruption layer acts as a bridge, ensuring that data exchanged between systems adheres to defined standards and formats. This layer must be designed with extensibility in mind, allowing for the addition of new external systems and protocols without requiring significant modifications to the core application.
This approach facilitates easier integration and maintenance.
Considerations for External System Interfacing
Careful consideration must be given to the specific requirements of each external system. This involves understanding the data formats, communication protocols, and data validation rules. The anti-corruption layer should be designed to handle potential variations and inconsistencies in external data. This can be achieved by implementing robust validation and transformation procedures to ensure data quality.
- Data Validation: Implementing validation rules to ensure data integrity and consistency from external sources is critical. This prevents unexpected errors and maintains data quality within the application.
- Error Handling: Robust error handling mechanisms are essential to manage potential issues during communication with external systems. This includes appropriate logging, retry mechanisms, and error propagation to the internal system.
- Security Considerations: Security is paramount when interacting with external systems. The anti-corruption layer must incorporate appropriate security measures, such as authentication, authorization, and data encryption, to protect sensitive information.
- Performance Optimization: The anti-corruption layer should be designed to optimize performance during interactions with external systems. Techniques such as caching, batch processing, and efficient data transformations can improve overall system performance.
- Documentation: Comprehensive documentation of the anti-corruption layer’s interaction with external systems is vital. This documentation should include details on data formats, communication protocols, and error handling procedures.
Security Considerations
The anti-corruption layer plays a critical role in safeguarding the integrity and security of data exchanged between the internal system and external sources. Robust security measures are paramount to prevent unauthorized access, data breaches, and manipulation. This section details the security considerations integrated into the anti-corruption layer, outlining how data is protected, and access controls are implemented.
Data Protection and Security During External Interactions
Secure communication channels are crucial when interacting with external systems. Encryption protocols like TLS/SSL should be employed to protect sensitive data transmitted over networks. This ensures that data remains confidential and inaccessible to unauthorized parties during transit. Furthermore, the layer should validate incoming data to prevent malicious input. Input validation techniques should be applied to prevent injection attacks, such as SQL injection or cross-site scripting (XSS).
The layer should also ensure that data transformations do not introduce vulnerabilities or expose sensitive information.
Access Control Mechanisms and Authentication Protocols
Implementing strong access control mechanisms is essential for restricting access to sensitive data and resources. This involves employing appropriate authentication protocols. For example, the anti-corruption layer can utilize industry-standard authentication methods such as OAuth 2.0 or API keys. This approach provides a secure and controlled method for external systems to access internal data. These authentication protocols should be integrated with role-based access control (RBAC) to restrict access based on user roles and permissions.
This will help prevent unauthorized personnel from accessing or manipulating sensitive data.
Security Risks and Mitigation Strategies
A proactive approach to security requires identifying potential risks and implementing appropriate mitigation strategies.
| Security Risk | Mitigation Strategy |
|---|---|
| Unauthorized Access | Implement robust authentication and authorization mechanisms, including multi-factor authentication (MFA) where applicable. Employ role-based access control to limit access to only necessary resources. |
| Data Breaches | Utilize encryption for data at rest and in transit. Regularly assess and patch security vulnerabilities. Employ intrusion detection and prevention systems. |
| Data Tampering | Implement data validation and integrity checks to detect any unauthorized modifications. Employ checksums or digital signatures to verify data integrity. |
| Injection Attacks | Employ parameterized queries and input validation techniques to prevent injection attacks. Use a secure coding framework. |
| Denial-of-Service (DoS) Attacks | Implement rate limiting and other mechanisms to mitigate DoS attacks. Employ load balancing to distribute traffic and prevent overload. |
Scalability and Maintainability
The anti-corruption layer’s design directly impacts the system’s overall scalability and maintainability. A well-structured layer facilitates future enhancements and updates, while a poorly designed one can hinder these crucial aspects. By prioritizing modularity, clear separation of concerns, and adaptable interfaces, the layer can easily adapt to evolving business needs and external system changes.A robust anti-corruption layer is a critical component for long-term system health.
Properly isolating business logic from external dependencies ensures the system remains flexible and maintainable as requirements change and new technologies emerge. This modularity is fundamental to the scalability and longevity of any complex system.
Promoting Scalability
The anti-corruption layer promotes scalability by acting as an intermediary, decoupling the core business logic from the intricacies of external systems. This allows the core business logic to be developed and tested independently, ensuring high levels of maintainability and scalability. By encapsulating the specific transformations and validations needed for each external system, the anti-corruption layer isolates the core business logic from any changes in the external systems.
This decoupling significantly enhances the system’s ability to handle increased data volume and user load without impacting the core application.
Impact on Maintainability
The design of the anti-corruption layer has a direct influence on maintainability. Clear separation of concerns, well-defined interfaces, and modular components contribute to easier understanding and modification of the codebase. By isolating the complex interactions with external systems, the anti-corruption layer reduces the impact of changes on other parts of the system. This is especially important in larger, more complex systems where the codebase might span several teams and technologies.
This, in turn, lowers the risk of introducing bugs or unintended consequences when making modifications.
Strategies for Future Enhancements and Updates
Future enhancements and updates are facilitated by the modular nature of the anti-corruption layer. The use of well-defined interfaces and standardized data formats allows for incremental improvements and the addition of new external system integrations without requiring significant modifications to the core business logic.
“Modularity is key. By separating concerns, the anti-corruption layer makes updates and enhancements less disruptive and more manageable.”
Specific strategies include:
- Versioning: Implementing versioning for the layer’s components allows for backward compatibility during updates and simplifies rollback procedures.
- Automated Testing: Comprehensive testing, including unit tests and integration tests, ensures that changes do not introduce regressions and that the layer continues to function correctly with the new implementation.
- Documentation: Thorough documentation, especially of the data transformations, validation rules, and interactions with external systems, aids in understanding and maintaining the layer over time. Clear documentation facilitates knowledge sharing and eases the onboarding of new team members.
Adaptability to Changes
Adaptability to changes is a key feature of the anti-corruption layer. The layer’s modular design allows for easy adaptation to new external systems, updated data formats, or altered business rules. A well-defined interface between the layer and the core business logic minimizes the impact of external system changes. This adaptability reduces the time and effort required to adjust to new requirements and ensures the system’s long-term flexibility.
Techniques include using standardized interfaces, flexible data mapping strategies, and well-defined data validation rules.
- Flexible Mapping Strategies: Employing flexible data mapping strategies allows the layer to handle variations in data structures from different external systems without requiring extensive code changes. Using mapping libraries or frameworks can simplify this process.
- Loose Coupling: Employing loose coupling between the anti-corruption layer and the core business logic is crucial. This ensures that modifications in one area do not necessarily affect the other. Using interfaces and abstract classes helps to maintain this loose coupling.
- Extensibility: Designing the layer with extensibility in mind allows for the addition of new components or features without disrupting the existing functionality. The layer should be open for extension and closed for modification, according to the Open/Closed Principle.
Performance Optimization
The anti-corruption layer’s performance directly impacts the overall system’s responsiveness and efficiency. Optimizing this layer is crucial to ensure smooth data flow and quick responses to requests, preventing bottlenecks that can affect the entire application. Efficient handling of data transformations and validations, coupled with minimizing latency, is paramount for a robust and user-friendly system.Optimizing the anti-corruption layer involves careful consideration of various factors, including data processing techniques, system architecture, and the specific nature of external systems.
By addressing potential performance bottlenecks proactively, the layer can effectively manage high volumes of data and ensure a consistent, high-performance user experience.
Strategies for Optimizing Data Transformations
Data transformations within the anti-corruption layer often involve complex mappings and conversions. Implementing optimized algorithms and utilizing appropriate data structures can significantly improve the efficiency of these transformations.
- Choosing appropriate algorithms: Selecting efficient algorithms for data transformations is crucial. For instance, using optimized sorting algorithms for large datasets, or employing specialized libraries for complex transformations, can reduce processing time. Employing libraries like Apache Commons Math or similar can improve speed by leveraging pre-built optimized code.
- Leveraging caching mechanisms: Caching frequently accessed data transformations can reduce the need for repeated calculations. A well-designed cache strategy can significantly improve response times for subsequent requests involving the same data transformations.
- Asynchronous processing: Deferring time-consuming transformations to separate threads or processes can prevent blocking the main thread. This approach allows the application to respond to other requests while complex transformations run in the background. This is especially important for tasks like large dataset transformations or external API calls that can take considerable time.
Minimizing Latency and Improving Response Times
Minimizing latency and improving response times in the anti-corruption layer is vital for a smooth user experience.
- Optimizing database queries: Efficient database queries are essential for retrieving and manipulating data. Techniques like indexing, query optimization, and proper database schema design are vital to minimize database access time. Employing prepared statements for parameterized queries can enhance security and performance.
- Reducing network overhead: Minimizing network communication is important for reducing latency. Strategies like using caching mechanisms for frequently accessed data or optimizing network protocols can significantly impact response times.
- Utilizing asynchronous communication: Asynchronous communication patterns, such as message queues, can help decouple the anti-corruption layer from external systems. This approach can reduce the impact of delays in external systems on the overall response time.
Handling Large Datasets Efficiently
Handling large datasets efficiently is crucial for the anti-corruption layer’s performance.
- Chunking data: Dividing large datasets into smaller chunks allows for processing in manageable portions. This can significantly improve processing speed and resource utilization, especially for operations like data validation or transformation.
- Utilizing distributed processing frameworks: Frameworks like Apache Spark or Hadoop can be used to process large datasets across multiple machines. This approach can distribute the workload, improving overall processing time, especially for computationally intensive tasks like data aggregation or analysis.
- Stream processing: For continuously incoming data streams, stream processing frameworks can be used to perform transformations and analysis in real-time. This approach is particularly relevant for applications that need to react to new data quickly, such as financial transactions or sensor data.
Performance Bottlenecks and Solutions
Identifying and addressing performance bottlenecks is crucial for maintaining optimal performance.
- External System Delays: Slow responses from external systems can significantly impact the anti-corruption layer’s performance. Solutions include optimizing the external systems, implementing caching mechanisms to store frequently accessed data, and using asynchronous communication.
- Inefficient Data Transformations: Complex or inefficient transformations can lead to performance issues. Solutions involve optimizing algorithms, using specialized libraries, and implementing caching strategies to store intermediate results.
- Inadequate Database Queries: Poorly written database queries can lead to slow retrieval times. Solutions include optimizing query design, indexing appropriate columns, and utilizing query caching techniques.
Different Implementation Approaches
The anti-corruption layer, acting as an intermediary between a system and external sources, can be implemented in various ways. Choosing the right approach is crucial for maintaining maintainability, scalability, and performance. Different methodologies offer varying trade-offs in terms of complexity, flexibility, and efficiency. Understanding these approaches is essential for building robust and adaptable systems.
Comparison of Implementation Strategies
Different approaches to implementing the anti-corruption layer offer varying levels of abstraction, coupling, and maintainability. Direct mapping often leads to tighter coupling with external systems, while more abstract approaches allow for greater flexibility and maintainability. The choice depends on the specific needs of the system, considering factors such as the complexity of external systems, the frequency of changes, and the desired level of maintainability.
Object-Oriented Approach
This approach utilizes object-oriented programming principles to encapsulate the interaction with external systems. Classes are designed to handle specific external interactions, providing a well-structured and maintainable interface. This approach promotes code reuse and reduces the impact of changes in external systems. The use of interfaces allows for greater flexibility in adapting to different external systems without modifying the core system.
For instance, if a new external API is introduced, the anti-corruption layer can be updated without impacting the rest of the application.
Adapter Pattern Approach
The adapter pattern involves creating an adapter class that translates the format and interface of the external system to the format and interface expected by the core system. This approach isolates the core system from the specifics of the external system, making it easier to adapt to changes in the external system without impacting the core system. This approach is particularly suitable when dealing with legacy systems or systems with incompatible interfaces.
For example, an adapter can transform data from a legacy database format into a modern data format used within the application.
Facade Pattern Approach
Employing a facade pattern simplifies interactions with external systems by providing a unified interface. This single entry point for all external interactions hides the complexity of multiple external systems. It promotes a cleaner and more manageable interface, making it easier to understand and maintain the interactions with external systems. This approach can be beneficial when dealing with a multitude of external systems, reducing the complexity of the system’s interaction with external sources.
Microservice Architecture Approach
In a microservice architecture, the anti-corruption layer is often implemented as a dedicated microservice. This approach enhances scalability, maintainability, and independent deployment of the anti-corruption layer. Each microservice can be responsible for a specific external system or data source, improving maintainability and allowing for independent evolution of the system. This approach can be beneficial in large-scale systems, allowing for more granular control over external interactions.
Table Summarizing Implementation Approaches
| Approach | Key Characteristics | Pros | Cons |
|---|---|---|---|
| Object-Oriented | Encapsulation, interfaces, maintainability | Flexible, reusable, adaptable | Potentially more complex for simple interactions |
| Adapter | Translates external formats | Adaptable to legacy systems, isolates core system | Can become complex with multiple adapters |
| Facade | Unified interface for external systems | Simplifies interaction, reduces complexity | Limited flexibility for diverse external systems |
| Microservice | Independent, scalable, deployable | Highly scalable, maintainable, independent evolution | Increased complexity, potential for inter-service communication overhead |
Selection Criteria
The selection of an implementation strategy depends on factors such as the complexity of external systems, the frequency of changes, the desired level of maintainability, and the scale of the application. Considering these factors, a well-defined strategy will ensure that the anti-corruption layer is effective and maintainable. The chosen approach should strike a balance between maintaining a robust interface and avoiding unnecessary complexity.
For instance, a small application with stable external systems might benefit from a simpler adapter pattern, while a large-scale application with frequent changes to external systems may prefer a microservice approach.
Closing Summary
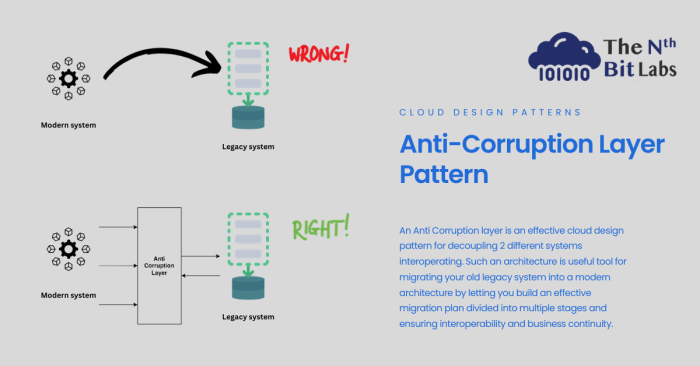
In conclusion, the anti-corruption layer pattern in system design offers a structured and adaptable approach to handling data and interactions with external systems. By implementing this pattern, developers can ensure data integrity, enforce business rules, and maintain a clear separation between the core application and external dependencies. This comprehensive guide provides a thorough understanding of the various aspects of this pattern, enabling developers to effectively leverage its benefits for building robust and maintainable software solutions.
Helpful Answers
What are some common use cases for the anti-corruption layer?
The anti-corruption layer is beneficial whenever data needs transformation or validation from external sources. Examples include integrating with legacy systems, APIs, or third-party services. It’s also crucial for applications dealing with diverse data formats, where ensuring data consistency is paramount.
How does the anti-corruption layer improve maintainability?
By isolating the core application from external dependencies, the anti-corruption layer simplifies maintenance. Changes to external systems or data formats only impact the layer itself, preventing cascading effects on the core application. This separation promotes modularity and reduces the risk of unintended consequences.
What are the key performance considerations for implementing an anti-corruption layer?
Performance is a crucial aspect to consider. Optimizing the layer for efficiency is essential, including techniques for handling large datasets and minimizing latency. Careful consideration of data transformations and validation strategies can significantly impact the performance of the layer.
What are some common challenges when implementing the anti-corruption layer?
Common challenges include choosing the right implementation approach, ensuring proper data validation and transformation, and handling potential errors from external systems. Understanding the specific needs of the external system and designing the layer accordingly is crucial for success.