In today’s digital landscape, securing web applications is paramount. This is where Dynamic Application Security Testing (DAST) comes into play, acting as a crucial shield against potential cyber threats. DAST is a black-box testing methodology, meaning it assesses applications from the outside, much like a hacker would, without needing access to the source code. This approach allows for the identification of vulnerabilities that might be missed by other testing methods, making it an essential component of a robust security strategy.
DAST tools simulate real-world attacks to uncover security flaws. These tools interact with a running application, probing for weaknesses like SQL injection, cross-site scripting (XSS), and authentication issues. By identifying these vulnerabilities early in the development lifecycle, DAST helps organizations prevent costly security breaches and maintain user trust. It is an automated process, offering a practical way to assess security without in-depth knowledge of the code itself.
Introduction to Dynamic Application Security Testing (DAST)
Dynamic Application Security Testing (DAST) is a crucial practice in software development that helps ensure the security of web applications. Think of it as a security check performed while the application is running, similar to how a car undergoes a road test. It’s designed to identify vulnerabilities that attackers could exploit to gain unauthorized access to sensitive information or disrupt the application’s functionality.
Core Concept of DAST
DAST works by simulating real-world attacks against a running application. It’s like a security professional trying to break into a house to identify weak points. The testing tool interacts with the application’s interface, such as the web browser or APIs, sending various malicious inputs and observing the application’s responses. These responses reveal whether the application is vulnerable to known security threats.
Definition of DAST
DAST, or Dynamic Application Security Testing, is a “black-box” testing methodology used to assess the security of a web application by simulating attacks against a running system. This testing is typically performed after the application is built and deployed to a testing or staging environment. It does not require access to the application’s source code, making it a practical choice for testing third-party applications or components.
Primary Goals of DAST
The main objectives of DAST are centered on identifying and mitigating security risks. These goals ensure the application is robust and secure against various types of attacks.
- Identifying Vulnerabilities: The primary goal is to uncover security flaws, such as cross-site scripting (XSS), SQL injection, and insecure configurations.
- Validating Security Controls: DAST verifies the effectiveness of security measures implemented within the application, such as authentication and authorization mechanisms.
- Providing Actionable Remediation Guidance: DAST tools often provide detailed reports with information about the vulnerabilities found and recommendations for fixing them. This helps developers understand and address the security issues effectively.
- Ensuring Compliance: DAST helps organizations meet regulatory requirements and industry standards related to application security, such as those defined by OWASP (Open Web Application Security Project) or PCI DSS (Payment Card Industry Data Security Standard). For instance, organizations handling financial data must comply with PCI DSS, which includes requirements for regular vulnerability scanning.
- Reducing Risk: By identifying and addressing vulnerabilities early in the software development lifecycle, DAST helps reduce the risk of successful attacks and data breaches. This, in turn, protects the organization’s reputation and financial stability.
How DAST Works
Dynamic Application Security Testing (DAST) tools assess the security of a web application by simulating attacks and observing its responses. This black-box testing approach operates from the outside, interacting with the application as a typical user would, but with the intent of identifying vulnerabilities. DAST tools don’t require access to the application’s source code, making them suitable for testing applications developed internally or by third-party vendors.
Scanning Process of DAST Tools
DAST tools systematically explore the web application, identifying and analyzing its various components and functionalities. The scanning process is designed to mimic real-world attack scenarios, allowing the tools to detect potential security weaknesses.
- Crawling: The DAST tool begins by crawling the web application. This involves following links, submitting forms, and exploring all available resources to map out the application’s structure and identify its various pages, functionalities, and entry points. This process is similar to how search engines index web pages.
- Attack Simulation: Once the application’s structure is understood, the DAST tool simulates various attacks. It sends malicious payloads and requests to the application, designed to exploit common vulnerabilities.
- Response Analysis: The DAST tool monitors the application’s responses to these simulated attacks. It analyzes the HTTP responses (status codes, headers, and content) for signs of vulnerabilities. For example, if an application returns an error message that reveals sensitive information, the DAST tool flags this as a potential security risk.
- Vulnerability Reporting: Based on the response analysis, the DAST tool identifies and reports any detected vulnerabilities. This report typically includes details about the vulnerability, its potential impact, and recommendations for remediation.
Types of Attacks Simulated by DAST Tools
DAST tools simulate a wide range of attacks to uncover various security vulnerabilities. These attacks are designed to test different aspects of the application’s security posture.
- Cross-Site Scripting (XSS): This attack involves injecting malicious scripts into web pages viewed by other users. DAST tools test for XSS vulnerabilities by injecting various payloads into input fields and observing how the application handles them. If the injected script executes, it indicates an XSS vulnerability.
- SQL Injection: SQL injection attacks exploit vulnerabilities in how an application interacts with its database. DAST tools test for this by injecting SQL code into input fields to see if it can be executed. A successful injection could allow attackers to access, modify, or delete sensitive data.
- Cross-Site Request Forgery (CSRF): CSRF attacks trick users into performing unwanted actions on a web application. DAST tools test for CSRF vulnerabilities by attempting to execute actions without proper authorization.
- Authentication and Authorization Issues: DAST tools also test for vulnerabilities related to authentication and authorization mechanisms, such as weak password policies, insecure session management, and insufficient access controls. They might try to bypass login pages or escalate privileges.
- Server Misconfiguration: This involves testing for common server-side misconfigurations, such as insecure HTTP headers, missing security patches, and exposed sensitive files.
- Other Vulnerabilities: DAST tools also test for a wide range of other vulnerabilities, including directory traversal, command injection, and denial-of-service (DoS) attacks.
Steps in a Typical DAST Scan
A typical DAST scan involves several steps, from pre-scan configuration to post-scan reporting. Proper configuration and execution are crucial for obtaining accurate and actionable results.
- Pre-Scan Configuration: Before starting a scan, the DAST tool must be configured. This includes specifying the target URL, authentication details (if required), and scan settings. Users can also configure the scan’s intensity (e.g., low, medium, high) to balance thoroughness and scanning time. It’s also important to define the scope of the scan, excluding parts of the application that are not relevant for security testing.
- Scanning: Once configured, the DAST tool begins the scanning process. It crawls the application, simulates attacks, and analyzes responses. The duration of the scan depends on the size and complexity of the application, and the scan intensity selected.
- Vulnerability Analysis: During and after the scan, the DAST tool analyzes the results. This includes identifying vulnerabilities, assessing their severity, and providing details about how they were detected.
- Reporting: DAST tools generate reports summarizing the scan results. These reports typically include a list of identified vulnerabilities, their severity levels (e.g., critical, high, medium, low), and detailed descriptions of each vulnerability, including steps to reproduce the issue and recommendations for remediation. The reports may also include information about the application’s overall security posture.
- Post-Scan Remediation and Verification: After receiving the report, developers and security teams should address the identified vulnerabilities. This often involves fixing code, updating configurations, or applying security patches. After the remediation, a re-scan is performed to verify that the vulnerabilities have been successfully addressed.
DAST Tools
Dynamic Application Security Testing (DAST) tools are essential for identifying vulnerabilities in web applications and APIs during runtime. These tools simulate attacks to uncover security flaws that could be exploited by malicious actors. Understanding the different types of DAST tools and their features is crucial for selecting the right solution for your application security needs. This section delves into commercial and open-source DAST tools, providing a comparative analysis and highlighting various testing methodologies.
DAST tools offer a wide array of functionalities. The choice of a DAST tool should be based on the specific requirements of the application, the development lifecycle, and the budget available. Key considerations include the supported technologies, the depth of analysis, the reporting capabilities, and the integration with other security tools and development environments.
Commercial DAST Tools: Features Comparison
Commercial DAST tools provide comprehensive features, often including automated vulnerability scanning, detailed reporting, and integration capabilities. The table below compares the features of some popular commercial DAST tools, highlighting their strengths and weaknesses.
| Tool | Key Features | Strengths | Weaknesses |
|---|---|---|---|
| Burp Suite Professional | Automated scanning, manual testing tools, vulnerability analysis, collaboration features, extensibility through extensions. | Highly versatile, comprehensive feature set, excellent for both automated and manual testing, widely adopted by security professionals. | Can be resource-intensive, requires some expertise to use effectively, cost. |
| Netsparker | Automated vulnerability scanning, proof-based vulnerability verification, integrated vulnerability management, support for various web technologies. | Provides proof of exploitability for identified vulnerabilities, reducing false positives, easy to use. | Limited manual testing capabilities compared to Burp Suite, cost. |
| Invicti (formerly Netsparker) | Automated vulnerability scanning, proof-based vulnerability verification, integrated vulnerability management, support for various web technologies. | Accurate vulnerability detection with proof of exploit, reduced false positives, and easy integration with CI/CD pipelines. | Requires training to leverage its full capabilities, can be expensive. |
| Acunetix | Automated vulnerability scanning, advanced scanning capabilities, reporting, integration with issue trackers and CI/CD pipelines. | Strong scanning engine, detailed reporting, supports a wide range of web technologies. | Can be slower than other tools, interface can be complex. |
Open-Source DAST Tools: Capabilities
Open-source DAST tools offer cost-effective solutions for application security testing. While they may not have all the features of commercial tools, they provide valuable capabilities for identifying vulnerabilities. Some popular open-source DAST tools include:
- OWASP ZAP (Zed Attack Proxy): A widely used tool for finding vulnerabilities in web applications. It offers automated scanning, manual testing capabilities, and a comprehensive set of features.
- Wfuzz: A tool for brute-forcing web applications, used to discover hidden resources, and identify vulnerabilities like SQL injection.
- Nikto: A web server scanner that performs comprehensive tests against web servers, checking for outdated software, common vulnerabilities, and configuration issues.
- arachni: A high-performance, open-source web application security scanner that can identify various vulnerabilities.
DAST Testing Methodologies
DAST tools employ different testing methodologies to identify vulnerabilities. The choice of methodology depends on the level of access the tool has to the application and its underlying code. The following table Artikels the different testing methodologies used by DAST tools:
| Testing Methodology | Description | Advantages | Disadvantages |
|---|---|---|---|
| Black-Box Testing | The DAST tool tests the application without access to the source code or internal design. It simulates attacks from an external perspective, like a real-world attacker. | Mimics real-world attacks, identifies vulnerabilities that might be missed by developers, requires no knowledge of the application’s internal workings. | Limited coverage of vulnerabilities, can be time-consuming, may not detect all vulnerabilities. |
| Gray-Box Testing | The DAST tool has partial knowledge of the application, such as access to documentation, architecture diagrams, or user credentials. | Provides a more comprehensive view than black-box testing, allows for more targeted testing, reduces the time required for testing. | Requires some level of knowledge about the application, potential for bias based on the information provided. |
| White-Box Testing | The DAST tool has full access to the source code, design documents, and other internal details of the application. | Provides the most comprehensive coverage, identifies vulnerabilities at the code level, enables more efficient testing. | Requires access to the source code, can be more complex to set up, may require specialized skills. |
Benefits of Using DAST
Integrating Dynamic Application Security Testing (DAST) into the software development lifecycle provides significant advantages in terms of security, efficiency, and cost-effectiveness. By proactively identifying and addressing vulnerabilities, organizations can significantly improve their overall security posture and reduce the risks associated with deploying vulnerable applications.
Early Vulnerability Identification
DAST’s primary benefit is its ability to detect vulnerabilities early in the development cycle. This proactive approach is crucial for preventing security flaws from reaching production environments, where they can be exploited by malicious actors. This early detection allows developers to fix vulnerabilities before they can cause significant damage.
Cost-Saving Benefits
Implementing DAST offers several cost-saving benefits throughout the software development lifecycle. The earlier vulnerabilities are identified and addressed, the less expensive it is to fix them. This proactive approach helps organizations avoid costly fixes later in the lifecycle, such as post-release patches and potential damage control after a security breach.The following list details the cost-saving advantages of DAST:
- Reduced Remediation Costs: Fixing vulnerabilities during the development phase is significantly cheaper than fixing them after deployment. Post-release fixes often require extensive resources, including developer time, testing, and potential downtime.
- Avoidance of Security Breaches: By identifying and addressing vulnerabilities before deployment, DAST helps prevent security breaches. Breaches can result in significant financial losses, including legal fees, regulatory fines, and reputational damage.
- Improved Developer Efficiency: DAST tools provide detailed reports that help developers quickly understand and address vulnerabilities. This can streamline the remediation process and reduce the time spent on debugging and fixing security flaws.
- Compliance with Security Standards: Many industry regulations and compliance standards, such as PCI DSS and HIPAA, require regular security testing. Using DAST helps organizations meet these requirements, avoiding potential penalties and fines.
- Reduced Risk of Downtime: Security vulnerabilities can lead to application downtime, which can impact business operations and revenue. DAST helps minimize the risk of downtime by proactively identifying and addressing security flaws.
For example, consider a scenario where a web application contains a critical SQL injection vulnerability.
If the vulnerability is discovered during the development phase, the cost to fix it might involve a few hours of developer time and some unit tests. However, if the vulnerability is exploited in a production environment, the cost could escalate dramatically, potentially including the cost of a data breach, legal fees, and reputational damage.
DAST helps organizations avoid these expensive scenarios by identifying and addressing vulnerabilities early in the development lifecycle.
DAST vs. Other Security Testing Methods
Dynamic Application Security Testing (DAST) is a valuable component of a comprehensive application security strategy, but it’s not a standalone solution. Its effectiveness is amplified when combined with other security testing methods. Understanding the differences and relationships between DAST and these other methods is crucial for building a robust security posture.
DAST vs. Static Application Security Testing (SAST)
SAST and DAST are complementary approaches to application security, each with its strengths and weaknesses. They differ significantly in their methodologies, the stage of the software development lifecycle (SDLC) at which they are applied, and the types of vulnerabilities they are best at detecting.SAST, also known as “white-box testing,” analyzes the application’s source code, bytecode, or binaries to identify vulnerabilities.
It examines the code’s structure, control flow, and data flow without executing the application. DAST, on the other hand, operates as a “black-box testing” method, interacting with the running application from the outside, similar to how a malicious actor would.
- Methodology: SAST analyzes code; DAST tests a running application.
- SDLC Stage: SAST is typically used early in the SDLC (during coding and build phases), while DAST is used later (during testing and pre-production).
- Vulnerability Detection: SAST excels at identifying vulnerabilities related to coding errors, such as buffer overflows and insecure coding practices. DAST is effective at finding runtime vulnerabilities, such as cross-site scripting (XSS) and SQL injection.
- False Positives: SAST can sometimes produce false positives due to its analysis of the code without considering runtime behavior. DAST typically has fewer false positives because it observes the application’s actual response to inputs.
- Language Support: SAST tools are often language-specific, requiring separate tools for different programming languages. DAST tools are generally language-agnostic, as they interact with the application through its interface (e.g., HTTP requests).
SAST can identify vulnerabilities early in the development process, reducing the cost and effort of remediation. DAST, however, provides a more realistic view of the application’s security posture by simulating real-world attacks. By using both SAST and DAST, organizations can achieve a more comprehensive and effective application security program.
DAST’s Complementary Role with IAST
Interactive Application Security Testing (IAST) is another security testing method that combines elements of both SAST and DAST. IAST tools run within the application’s runtime environment, providing insights into the application’s internal workings while also testing it from the outside.DAST complements IAST by providing a broader perspective on application security. While IAST offers detailed information about vulnerabilities and their root causes, DAST focuses on the application’s behavior from an external perspective.
- Combined Approach: IAST combines the benefits of SAST (code analysis) and DAST (runtime testing).
- Visibility: IAST offers deep visibility into the application’s internal state, including data flow and code execution. DAST provides a black-box view, focusing on the application’s external behavior.
- Vulnerability Identification: IAST can pinpoint the exact location of a vulnerability in the code, while DAST identifies the vulnerability from an external perspective.
- Efficiency: IAST can often identify vulnerabilities more quickly than DAST, as it has access to internal application data.
- Coverage: DAST can test all parts of the application that are accessible through the user interface, even those that may not be easily tested with IAST.
IAST’s runtime analysis complements DAST’s external testing by providing more detailed information about vulnerabilities, allowing for faster and more accurate remediation. The synergy between DAST and IAST results in a more complete and effective security testing process.
DAST in the Application Security Testing Landscape
The application security testing landscape is complex, with various testing methods designed to address different aspects of security. DAST plays a crucial role in this landscape, often serving as a central component of a comprehensive security testing strategy.The following diagram illustrates the position of DAST in the application security testing landscape. It highlights the relationship between different testing methods and their respective roles in identifying and mitigating vulnerabilities.
Imagine a layered diagram, starting with the foundation:
- Foundation Layer: Represents the SDLC, including design, coding, building, testing, deployment, and maintenance phases.
- First Layer (Left): SAST, positioned to the left, emphasizing its role in the early phases of the SDLC (coding, building).
- First Layer (Right): DAST, positioned to the right, emphasizing its role in the later phases of the SDLC (testing, deployment).
- Second Layer: IAST, positioned in the middle, overlapping with both SAST and DAST, highlighting its integration of code analysis and runtime testing.
- Third Layer: Penetration Testing, positioned above DAST and IAST, representing manual security assessments that simulate real-world attacks.
- Additional elements: Container security scanning, dependency scanning, and API security testing are also represented, demonstrating the wide range of testing approaches used to ensure application security.
This diagram clearly illustrates that DAST is a key component of a layered security approach. It’s not a standalone solution, but it works in conjunction with other methods to provide a more complete and robust security posture. Organizations that adopt a holistic approach to application security, incorporating DAST alongside SAST, IAST, and penetration testing, are better positioned to protect their applications from a wide range of threats.
Common Vulnerabilities Detected by DAST
Dynamic Application Security Testing (DAST) tools are designed to identify vulnerabilities in web applications by simulating real-world attacks. They operate by interacting with a running application, much like a malicious user would, and analyzing the application’s responses to various inputs. This approach allows DAST tools to uncover a wide range of security flaws that could be exploited by attackers. Understanding the common vulnerabilities DAST detects is crucial for effectively securing applications.
SQL Injection
SQL injection is a type of vulnerability that allows attackers to interfere with the queries that an application makes to its database. This can lead to unauthorized access to data, modification of data, or even complete control over the database server. DAST tools identify SQL injection vulnerabilities by injecting malicious SQL code into input fields and observing the application’s response.
- Example: Consider a website with a login form. An attacker might enter the following into the username field:
' OR '1'='1. If the application doesn’t properly sanitize the input, the resulting SQL query might look like this:SELECT
- FROM users WHERE username = '' OR '1'='1' AND password = 'password'This query would always evaluate to true, bypassing the authentication process and granting the attacker access.
- DAST Detection: DAST tools would inject various SQL payloads, such as those designed to trigger errors or retrieve data, into input fields. If the application’s response indicates a vulnerability, such as an error message revealing database structure or the retrieval of unexpected data, the DAST tool flags the vulnerability.
Cross-Site Scripting (XSS)
Cross-site scripting (XSS) vulnerabilities allow attackers to inject malicious scripts into web pages viewed by other users. These scripts can steal user cookies, redirect users to malicious websites, or deface the website. DAST tools detect XSS vulnerabilities by injecting scripts into input fields and observing how the application renders them in the output.
- Example: A website allows users to post comments. An attacker could inject the following script into a comment:
<script>alert('XSS');</script>. When another user views the comment, the script will execute, displaying an alert box. - DAST Detection: DAST tools will inject various XSS payloads, including JavaScript code, HTML tags, and other malicious scripts, into input fields like comment sections, search boxes, and form fields. If the injected script executes in the user’s browser, the DAST tool identifies an XSS vulnerability. The tool analyzes the application’s response to determine if the input is properly sanitized before being displayed to other users.
Authentication and Authorization Vulnerabilities
DAST tools play a critical role in identifying vulnerabilities related to authentication and authorization mechanisms, which are essential for controlling user access and protecting sensitive data. They simulate various attack scenarios to expose weaknesses in how an application handles user logins, sessions, and permissions.
- Authentication Vulnerabilities: DAST tools test for weak password policies, brute-force attacks, and session management issues. They can identify if an application allows for weak passwords or if there are vulnerabilities in the password reset process.
- Authorization Vulnerabilities: These vulnerabilities arise when users are granted more access than they should have. DAST tools test for issues such as insecure direct object references (IDOR), where users can access resources they are not authorized to view or modify.
- Examples:
- Weak Password Policies: A DAST tool might try to log in with common passwords or test for the ability to create weak passwords.
- Brute-Force Attacks: DAST tools can simulate brute-force attacks to test if the application locks out users after a certain number of failed login attempts.
- Insecure Direct Object References (IDOR): A DAST tool might attempt to access a resource by manipulating the URL or parameters, such as changing a user ID to access another user’s data. For example, if a URL to view a user’s profile is
/profile.php?id=123, an attacker might try changing the ID to/profile.php?id=456to access another user’s profile.
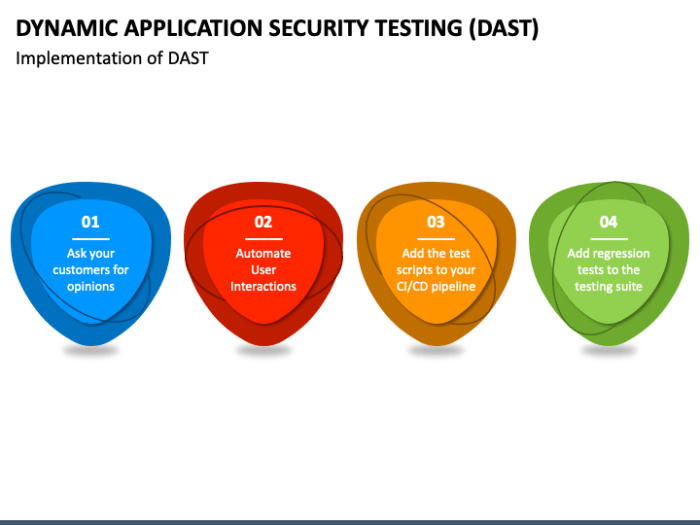
DAST Implementation and Integration
Implementing and integrating Dynamic Application Security Testing (DAST) is crucial for incorporating security into the software development lifecycle (SDLC). This process helps automate vulnerability detection, improve application security posture, and reduce the risk of security breaches. Proper implementation requires careful planning, tool selection, and integration into existing development workflows, especially within Continuous Integration/Continuous Deployment (CI/CD) pipelines.
DAST Implementation in a CI/CD Pipeline
Integrating DAST into a CI/CD pipeline allows for automated security testing throughout the development process. This proactive approach helps identify and remediate vulnerabilities early, reducing the cost and effort associated with fixing them later in the lifecycle. The following steps are generally involved:
- Choose a DAST Tool: Select a DAST tool that aligns with your application’s technology stack, testing requirements, and budget. Consider factors such as scan capabilities, integration options, reporting features, and support for different authentication methods.
- Configure the DAST Tool: Configure the selected DAST tool to access your web application. This includes providing the application’s URL, authentication credentials (if required), and any specific settings related to the testing environment.
- Integrate with CI/CD Pipeline: Integrate the DAST tool into your CI/CD pipeline. This typically involves adding a step to the pipeline that executes the DAST scan after the application has been built and deployed to a testing environment. Most CI/CD tools offer plugins or integrations for popular DAST tools.
- Automate the Scan: Configure the CI/CD pipeline to automatically trigger a DAST scan whenever a new build is deployed to the testing environment. This automation ensures that security testing is performed consistently and frequently.
- Analyze Results: After the DAST scan completes, the results should be analyzed to identify any vulnerabilities. The DAST tool will typically generate reports that highlight detected issues, including severity levels and remediation recommendations.
- Remediate Vulnerabilities: Based on the DAST scan results, developers should address identified vulnerabilities. This may involve fixing code, updating dependencies, or implementing security controls.
- Track and Report: Establish a system for tracking and reporting on the DAST scan results and the remediation efforts. This can include dashboards, reports, and metrics to monitor the application’s security posture over time.
Configuring a DAST Tool for a Specific Web Application
Configuring a DAST tool involves providing the necessary information and settings for the tool to effectively scan a web application. The specific steps vary depending on the DAST tool used, but generally, the following are involved:
- Application URL: Specify the base URL of the web application you want to test. This is the starting point for the DAST tool’s scans. For example,
https://www.example.com. - Authentication: Configure authentication settings if the application requires a login. This may involve providing usernames, passwords, and/or other authentication tokens. Different authentication methods, such as Basic Auth, form-based authentication, or API key-based authentication, will require different configuration. For instance, form-based authentication often involves specifying the login URL, username field, password field, and a success indicator.
- Scan Scope: Define the scope of the scan, which determines the parts of the application that will be tested. This may include specifying which URLs, directories, or parameters to include or exclude from the scan.
- Scan Configuration: Configure the scan settings, such as the scan speed, the types of vulnerabilities to look for, and the HTTP methods to use. For example, you might configure the tool to scan for SQL injection vulnerabilities, cross-site scripting (XSS) vulnerabilities, and other common web application security flaws.
- Attack Payload Configuration: Customize the attack payloads used by the DAST tool to probe for vulnerabilities. Some tools allow you to customize the payload to target specific technologies or vulnerabilities.
- Report Configuration: Configure how the scan results will be reported. This may include specifying the report format, the level of detail to include, and the recipients of the reports.
- Proxy Settings: If the application is accessed through a proxy server, configure the DAST tool to use the proxy settings. This will allow the tool to correctly route its traffic to the application.
- Scheduler (Optional): Set up a schedule for the DAST scans. This can be used to automate scans at regular intervals, such as nightly or weekly.
Workflow Diagram: DAST Integration within a Development Process
The following diagram illustrates the typical workflow for integrating DAST within a development process. This process helps visualize how DAST fits into the broader SDLC, emphasizing the importance of automated security testing.
+---------------------+ +---------------------+ +---------------------+ +---------------------+ +---------------------+| Developer |----->| Code Commit/Push |----->| Build Process |----->| Deployment to |----->| DAST Scan || Writes Code | | to Repository | | (e.g., Jenkins) | | Testing Env.| | (Automated) |+---------------------+ +---------------------+ +---------------------+ +---------------------+ +---------------------+ | | | | | | | | | | v v v v v+---------------------+ +---------------------+ +---------------------+ +---------------------+ +---------------------+| Unit Tests | | Code Analysis | | Artifact Creation | | Application | | Results Analysis || (Developer) | | (Static Analysis) | | (e.g., .war, .jar)| | Testing |----->| (DAST Tool) |+---------------------+ +---------------------+ +---------------------+ | Environment | +---------------------+ | (Staging/QA) | +---------------------+ | v+---------------------+| Vulnerability || Reports |+---------------------+ | v+---------------------+| Remediation || (Developer) |+---------------------+ | v+---------------------+| Retest/Validation || (Repeat Cycle) |+---------------------+
Description of the Diagram:
The workflow begins with the developer writing code. This code is then committed and pushed to a code repository. This triggers a build process, often handled by a CI/CD tool like Jenkins, which includes static code analysis and unit tests. The build process then creates an artifact, such as a .war or .jar file, and deploys the application to a testing environment (e.g., staging or QA).
After deployment, the DAST tool automatically scans the application. The results of the DAST scan are analyzed, generating vulnerability reports. Developers then remediate the identified vulnerabilities. After remediation, the process often includes retesting or validation, restarting the cycle to ensure security improvements. The cycle emphasizes continuous testing and feedback, integrating security into the entire development process.
Reporting and Analysis of DAST Results
The reporting and analysis phase is crucial for understanding the results of a Dynamic Application Security Testing (DAST) scan. This stage transforms raw scan data into actionable insights, allowing developers and security professionals to address identified vulnerabilities effectively. Comprehensive reports and accurate result interpretation are essential for a successful application security program.
Types of Reports Generated by DAST Tools
DAST tools generate various reports that provide different perspectives on the security posture of an application. These reports are designed to cater to different audiences, from developers to security managers.
- Vulnerability Reports: These are the core reports, detailing the specific vulnerabilities found during the scan. They typically include:
- Vulnerability Name and Description: Clearly identifies the vulnerability (e.g., SQL Injection, Cross-Site Scripting) and provides a detailed explanation.
- Severity Level: Classifies the vulnerability based on its potential impact (e.g., Critical, High, Medium, Low, Informational), often using the Common Vulnerability Scoring System (CVSS).
- Affected URL(s): Specifies the exact URLs where the vulnerability was detected.
- Proof of Concept (PoC): Shows how the vulnerability was exploited or can be exploited, often including the HTTP request and response.
- Recommendations for Remediation: Suggests specific steps to fix the vulnerability, often linking to relevant documentation or resources.
- Executive Summary Reports: These reports provide a high-level overview of the security status, often targeted at management. They include:
- Overall Risk Assessment: Summarizes the overall risk level of the application.
- Number of Vulnerabilities: Provides a count of vulnerabilities by severity level.
- Trend Analysis: Shows the trend of vulnerabilities over time, indicating whether the application’s security is improving or worsening.
- Key Findings: Highlights the most critical vulnerabilities and their potential impact.
- Compliance Reports: These reports help organizations meet compliance requirements, such as those from PCI DSS, HIPAA, or OWASP. They map vulnerabilities to specific compliance standards.
- Mapping to Compliance Standards: Shows how the identified vulnerabilities relate to specific compliance requirements.
- Remediation Status: Tracks the progress of fixing vulnerabilities related to compliance.
- Technical Reports: These reports provide detailed technical information for developers.
- Detailed Technical Information: Includes information such as HTTP requests and responses, payloads used to identify vulnerabilities, and error messages.
- Detailed Trace Information: Traces that can show how the vulnerabilities were found.
- Customizable Reports: Many DAST tools allow users to customize reports to fit their specific needs. This includes the ability to filter results, add custom fields, and generate reports in various formats (e.g., PDF, CSV, HTML).
Interpreting DAST Scan Results
Interpreting DAST scan results involves understanding the data provided in the reports and translating it into actionable insights. This process requires careful analysis and consideration of various factors.
- Understanding Severity Levels: The severity level is the most important factor in prioritizing vulnerabilities.
- Critical: Poses the highest risk, often allowing attackers to gain complete control of the application or access sensitive data.
- High: Can lead to significant data breaches or system compromise.
- Medium: Can lead to moderate data exposure or system disruption.
- Low: Poses a minimal risk and may not require immediate attention.
- Informational: Does not indicate a vulnerability but provides useful information about the application.
- Analyzing Proof of Concepts (PoCs): Reviewing the PoCs provided by the DAST tool helps understand how a vulnerability can be exploited. This information is crucial for:
- Confirming Vulnerabilities: Verifying that the vulnerability is real and not a false positive.
- Understanding the Impact: Assessing the potential damage that could result from an exploit.
- Evaluating False Positives: DAST tools can sometimes report false positives, where a vulnerability is identified but doesn’t actually exist. It’s important to:
- Reviewing the Findings: Examine the details of the reported vulnerability.
- Manually Verifying: Try to reproduce the vulnerability manually to confirm its existence.
- Considering the Context: The context of the application is crucial. For example:
- Application Type: A public-facing web application is generally at higher risk than an internal application.
- Data Sensitivity: Applications handling sensitive data require stricter security measures.
- Business Impact: The potential impact on the business should be considered.
- Cross-Referencing with Other Data: Correlating DAST results with other security data, such as threat intelligence feeds or other security testing results, can provide a more comprehensive view of the application’s security posture.
Prioritizing and Addressing DAST-Identified Vulnerabilities
Prioritizing and addressing vulnerabilities is a critical step in improving application security. This process involves evaluating the risk, assigning resources, and implementing remediation strategies.
- Risk-Based Prioritization: Prioritize vulnerabilities based on their severity, exploitability, and potential impact. A risk matrix can be a useful tool.
- Severity: Critical and High vulnerabilities should be addressed immediately.
- Exploitability: Vulnerabilities that are easy to exploit should be prioritized.
- Impact: Vulnerabilities that can cause significant damage should be prioritized.
- Remediation Strategies: Implement appropriate remediation strategies based on the type of vulnerability.
- Code Changes: Developers should fix the underlying code to address the vulnerability.
- Configuration Changes: Adjust application or server configurations to mitigate the vulnerability.
- Input Validation: Implement robust input validation to prevent injection attacks.
- Output Encoding: Encode output to prevent cross-site scripting (XSS) attacks.
- Assigning Resources: Assign appropriate resources to address vulnerabilities.
- Developers: Responsible for fixing code-related vulnerabilities.
- Security Team: Provides guidance and oversight.
- System Administrators: Responsible for configuration changes.
- Tracking and Monitoring: Track the progress of remediation efforts and monitor the application for new vulnerabilities.
- Vulnerability Management System: Use a vulnerability management system to track vulnerabilities and their remediation status.
- Regular Re-scanning: Rescan the application regularly to ensure that vulnerabilities have been fixed and to identify new ones.
- Verification and Validation: After remediation, verify that the vulnerability has been successfully fixed.
- Retesting: Perform a new DAST scan to confirm that the vulnerability is no longer present.
- Manual Testing: Manually test the application to verify the fix.
- Examples of Prioritization:
- Scenario 1: A DAST scan identifies a critical SQL injection vulnerability on a public-facing e-commerce website that handles customer payment information. This vulnerability should be the top priority for remediation due to its high severity and potential for data breach.
- Scenario 2: A DAST scan identifies a low-severity cross-site scripting (XSS) vulnerability on a blog website. While still important, this vulnerability might be a lower priority than the SQL injection vulnerability. However, it still requires remediation to prevent potential user attacks.
Limitations of DAST
Dynamic Application Security Testing (DAST) is a valuable tool in the application security arsenal, but it’s essential to understand its limitations. While DAST excels at identifying vulnerabilities from an external perspective, it doesn’t provide a complete security picture. Over-reliance on DAST can leave gaps in security coverage, potentially exposing applications to attacks.
Inability to Detect Code-Level Vulnerabilities
DAST operates by interacting with a running application, simulating user actions, and analyzing the responses. This black-box approach has a significant drawback: it cannot directly examine the application’s source code.
- Source Code Visibility: DAST tools do not have access to the underlying code, preventing them from identifying vulnerabilities that exist within the code itself. This includes issues like:
- Logic errors: Flaws in the application’s logic that can lead to unexpected behavior or security breaches.
- Hardcoded secrets: Sensitive information like passwords or API keys embedded directly in the code.
- Poor coding practices: Code that is poorly written and can be exploited.
- Example: Consider a scenario where an application’s authentication mechanism contains a vulnerability where a user can bypass authentication by manipulating a specific parameter in the request. DAST can potentially identify the vulnerability if it’s triggered by a particular request, but it won’t reveal the root cause within the source code.
- Contrast with SAST: Static Application Security Testing (SAST), also known as white-box testing, analyzes the source code directly. SAST tools can detect vulnerabilities at the code level, such as buffer overflows, SQL injection flaws, and cross-site scripting (XSS) vulnerabilities. SAST complements DAST by providing a deeper level of code analysis.
Ineffectiveness in Certain Scenarios
There are situations where DAST’s effectiveness is limited. These limitations often stem from the nature of the application or the testing environment.
- Applications Under Development: DAST tools typically require a functional application to interact with. Testing early-stage development versions, where features are incomplete or unstable, can be challenging.
- Complex Single-Page Applications (SPAs): SPAs that heavily rely on client-side JavaScript and asynchronous operations can pose difficulties. DAST tools may struggle to fully understand the application’s state and interactions, potentially missing vulnerabilities.
- Applications with Complex Authentication: DAST tools can face difficulties navigating complex authentication mechanisms, such as multi-factor authentication (MFA) or federated identity. This can limit their ability to test all functionalities.
- Environments with Restricted Access: If the testing environment does not fully mirror the production environment, DAST might miss vulnerabilities that are specific to the production setup. For example, network configurations, database access, and third-party integrations can influence security.
- Example: Imagine an application that uses WebSockets for real-time communication. DAST tools might struggle to properly analyze the WebSocket traffic, potentially overlooking vulnerabilities in the communication protocol.
Challenges of Sole Reliance on DAST
Relying solely on DAST for application security introduces significant risks. A comprehensive security strategy requires a multi-faceted approach.
- Limited Coverage: DAST provides external testing. It doesn’t address vulnerabilities that reside within the application’s code or internal components.
- False Positives and Negatives: DAST tools can sometimes generate false positives, reporting vulnerabilities that do not exist. Conversely, they can also miss real vulnerabilities (false negatives). This is because they rely on heuristics and pattern matching.
- Time-Consuming and Resource-Intensive: DAST scans can be time-consuming, especially for large applications. They also require significant resources, including dedicated servers and personnel to interpret the results.
- Inability to Detect Design Flaws: DAST focuses on identifying vulnerabilities based on how the application responds to external stimuli. It cannot assess security design flaws, such as insecure architecture or poor user interface design.
- Recommendation: Integrating DAST with other security testing methods, such as SAST, penetration testing, and threat modeling, provides a more robust security posture. This ensures that all aspects of application security are addressed.
Future Trends in DAST
The landscape of application security is constantly evolving, driven by advancements in technology and the increasing sophistication of cyber threats. Dynamic Application Security Testing (DAST) is adapting to these changes, with several key trends shaping its future. These trends aim to improve efficiency, accuracy, and integration within the software development lifecycle.
The Integration of AI and Machine Learning in DAST
Artificial intelligence (AI) and machine learning (ML) are poised to revolutionize DAST. These technologies offer the potential to automate and enhance various aspects of the testing process.
- Automated Vulnerability Detection: AI and ML algorithms can be trained to identify vulnerabilities with greater accuracy and speed. For example, ML models can analyze HTTP responses, identify patterns indicative of SQL injection, and classify vulnerabilities based on their severity. This reduces false positives and the time required for manual analysis.
- Intelligent Test Case Generation: ML can learn from past test results and application behavior to generate more effective test cases. This leads to better coverage and the identification of vulnerabilities that might be missed by traditional methods. This intelligent approach can also prioritize testing based on the application’s risk profile.
- Contextual Analysis and Prioritization: AI can analyze the context of vulnerabilities, considering factors such as the application’s architecture, data flow, and business logic. This enables more accurate prioritization of vulnerabilities, allowing security teams to focus on the most critical issues first.
- Reduced False Positives: ML models can be trained to distinguish between legitimate application behavior and actual vulnerabilities, reducing the number of false positives. This improves the efficiency of security teams and reduces the time spent on remediation.
DAST’s Evolution to Address Modern Web Application Architectures
Modern web applications, often built using microservices, APIs, and cloud-native technologies, present new challenges for DAST. The future of DAST involves adapting to these architectures to maintain its effectiveness.
- API Security Testing: The increasing reliance on APIs necessitates robust API security testing capabilities. DAST tools are evolving to support testing of REST APIs, GraphQL APIs, and other API types, including testing for authentication, authorization, and input validation vulnerabilities.
- Cloud-Native Application Security: DAST is being adapted to test applications deployed in cloud environments, such as AWS, Azure, and Google Cloud. This includes integrating with cloud-native security tools and understanding the unique security challenges of cloud platforms.
- Microservices Architecture Support: Testing microservices requires a different approach than traditional monolithic applications. DAST tools are evolving to support testing of individual microservices, as well as the interactions between them. This involves dynamic analysis of service dependencies and communication.
- Continuous Integration and Continuous Delivery (CI/CD) Integration: DAST is becoming increasingly integrated into CI/CD pipelines, enabling automated security testing throughout the development lifecycle. This allows developers to identify and fix vulnerabilities early in the process, reducing the cost and effort of remediation.
A Vision for the Future of DAST and its Role in Application Security
The future of DAST is one of greater automation, integration, and intelligence. It will play a critical role in ensuring the security of applications in an increasingly complex and threat-filled environment.
- Shift-Left Security: DAST will continue to support the shift-left approach, integrating security testing earlier in the development lifecycle. This will enable developers to address vulnerabilities as they are introduced, reducing the risk of security breaches.
- Proactive Security: DAST will evolve from a reactive tool to a proactive one, providing insights into potential vulnerabilities before they are exploited. This will involve the use of predictive analytics and threat modeling to identify and mitigate risks.
- DevSecOps Integration: DAST will become an integral part of DevSecOps practices, enabling seamless integration of security testing with development and operations activities. This will streamline the development process and improve the overall security posture of organizations.
- Focus on Automation and Efficiency: The future of DAST will be defined by increased automation, reducing the need for manual intervention and improving the efficiency of security testing. This will free up security professionals to focus on more strategic activities, such as threat modeling and risk management.
Epilogue
In conclusion, Dynamic Application Security Testing (DAST) is an invaluable asset in the ongoing effort to secure web applications. From its ability to simulate attacks to its role in identifying vulnerabilities, DAST plays a pivotal role in the software development lifecycle. As technology evolves, so too will DAST, with emerging trends like AI and machine learning further enhancing its capabilities.
By understanding and integrating DAST, organizations can fortify their defenses and protect their valuable assets in an increasingly complex digital world.
FAQs
What is the primary difference between DAST and SAST?
DAST (Dynamic Application Security Testing) examines a running application from the outside, while SAST (Static Application Security Testing) analyzes the source code from the inside. DAST doesn’t require access to the code and simulates attacks, whereas SAST requires the code and analyzes it directly.
How often should DAST be performed?
DAST should be integrated into the software development lifecycle and performed regularly. This can include automated scans as part of the CI/CD pipeline, as well as periodic manual scans, especially after significant code changes or updates.
Can DAST detect all types of vulnerabilities?
No, DAST has limitations. It’s excellent at identifying vulnerabilities that can be detected through external interactions, but it may miss vulnerabilities related to the internal logic or specific coding practices. It’s best used in conjunction with other testing methods like SAST and IAST for comprehensive security coverage.
What are the benefits of using DAST tools?
DAST tools help identify vulnerabilities early, reduce the cost of fixing security issues, and improve the overall security posture of an application. They also help organizations comply with security standards and regulations.


