Embark on a journey into the world of secure corporate communications with what is a virtual private network (VPN) for corporate use. This technology has become indispensable for businesses of all sizes, offering a shield against cyber threats and enabling secure access to vital resources. We’ll delve into the core functionalities, dissect the underlying protocols, and explore how VPNs safeguard sensitive data in an increasingly interconnected world.
A VPN creates a secure, encrypted tunnel over the public internet, allowing employees to connect to a corporate network remotely as if they were physically present. This secure connection protects data from eavesdropping and unauthorized access, ensuring confidentiality and integrity. From small startups to multinational corporations, understanding and implementing VPN technology is crucial for maintaining a secure and productive work environment.
Understanding VPNs for Corporate Use

In today’s interconnected world, safeguarding corporate data is paramount. Virtual Private Networks (VPNs) play a crucial role in achieving this, providing a secure and private pathway for data transmission. This section delves into the core aspects of VPNs in a corporate context, explaining their functionality, benefits, and practical applications.
Fundamental Concept and Functionality of Corporate VPNs
A corporate VPN creates a secure, encrypted connection over a public network, such as the internet. It allows employees to access the company’s network resources remotely, as if they were physically present in the office. This is achieved by establishing a “tunnel” through which all data traffic is routed.Here’s how it works:* Encryption: All data transmitted between the user’s device and the VPN server is encrypted, making it unreadable to unauthorized parties.
This protects sensitive information from being intercepted and stolen.
Authentication
The VPN verifies the user’s identity before granting access to the network. This ensures that only authorized personnel can access corporate resources.
Routing
The VPN server acts as an intermediary, routing the user’s internet traffic through the company’s network. This masks the user’s IP address and location, enhancing privacy.
Analogy for Secure Data Transmission
Imagine a VPN as a private, secure tunnel. Consider a scenario where an employee needs to send a sensitive document from a remote location back to the company headquarters.Instead of sending the document through the regular, public internet (which is like sending it through the open mail), the employee uses a VPN. The VPN encrypts the document and places it inside a secure, sealed container.
This container is then transported through a private tunnel (the VPN connection) that only the company headquarters can access. No one can intercept and read the document while it’s in transit. The container is opened only when it arrives safely at its destination.
Core Benefits of Using a VPN for Corporate Data Security and Privacy
Implementing a VPN offers several key advantages for corporate data security and privacy:* Enhanced Data Security: VPNs encrypt all data transmitted over the network, protecting sensitive information from cyber threats such as hacking, eavesdropping, and data breaches. This is particularly crucial when employees are working remotely or using public Wi-Fi networks.* Secure Remote Access: VPNs enable employees to securely access the company’s network resources from anywhere in the world.
This facilitates remote work, allowing employees to access files, applications, and other resources as if they were in the office.* IP Address Masking: VPNs mask the user’s IP address, hiding their actual location and making it more difficult for malicious actors to track their online activities. This enhances privacy and helps protect against targeted attacks.* Bypassing Geo-restrictions: Some companies may use VPNs to bypass geographical restrictions on certain websites or online services.
This allows employees to access necessary resources that might be blocked in their location.* Compliance with Data Privacy Regulations: VPNs can assist companies in meeting data privacy regulations, such as GDPR and CCPA, by providing a secure and private means of transmitting and storing sensitive data.* Protecting Sensitive Communications: VPNs are invaluable for protecting confidential communications, such as emails, instant messages, and video conferences, by encrypting the data exchanged.* Reduced Risk of Man-in-the-Middle Attacks: VPNs protect against “man-in-the-middle” attacks, where attackers intercept communication between two parties.
By encrypting the data, VPNs prevent attackers from reading or altering the data.* Cost-Effectiveness: Compared to other security solutions, VPNs are a cost-effective way to enhance data security and privacy, especially for small to medium-sized businesses.* Improved Productivity: By providing secure and reliable remote access, VPNs can improve employee productivity and collaboration.
Security Protocols and Encryption
Understanding the security protocols and encryption methods employed by Virtual Private Networks (VPNs) is crucial for organizations aiming to protect their sensitive data. The choice of protocol and encryption directly impacts the VPN’s security posture, performance, and compatibility. This section explores the various VPN protocols, their strengths and weaknesses, and the encryption methods they utilize.
VPN Protocol Overview
VPN protocols define the rules and standards for establishing and managing a secure connection between a user’s device and a VPN server. The selection of a protocol significantly influences the VPN’s speed, security, and compatibility across different devices and operating systems. Each protocol offers a unique set of features and trade-offs.
- OpenVPN: OpenVPN is a widely used open-source protocol known for its strong security and flexibility. It supports various encryption algorithms and can operate over both TCP and UDP protocols. This adaptability makes it suitable for a wide range of network environments.
- Strengths: High level of security, strong encryption options, and extensive configuration options.
- Weaknesses: Can be more complex to configure than other protocols and may experience performance limitations on certain hardware.
- IPSec (Internet Protocol Security): IPSec is a suite of protocols that secures Internet Protocol (IP) communications. It’s often used in VPNs to provide secure connections. IPSec can operate in two modes: Transport mode (protecting only the payload of the IP packet) and Tunnel mode (encrypting the entire IP packet).
- Strengths: Widely supported and offers robust security. Often used for site-to-site VPN connections.
- Weaknesses: Can be more complex to configure and troubleshoot than OpenVPN, and may have compatibility issues with some network environments.
- WireGuard: WireGuard is a relatively new, open-source protocol designed to be faster, simpler, and more secure than older protocols like OpenVPN and IPSec. It uses a streamlined cryptographic design.
- Strengths: Excellent performance, simpler configuration, and strong cryptographic primitives.
- Weaknesses: Still relatively new, so wider adoption is ongoing, and some older devices may not support it. Configuration can be more complex for those unfamiliar with the underlying concepts.
- SSTP (Secure Socket Tunneling Protocol): SSTP is a VPN protocol developed by Microsoft, designed to work well with Windows operating systems. It uses SSL/TLS for secure communication.
- Strengths: Generally good at bypassing firewalls, because it uses port 443 (HTTPS).
- Weaknesses: Proprietary protocol, which limits the flexibility. Less secure than OpenVPN.
- L2TP/IPSec (Layer 2 Tunneling Protocol/IPSec): L2TP is often paired with IPSec for security. L2TP itself doesn’t provide encryption; IPSec handles the encryption.
- Strengths: Widely supported.
- Weaknesses: Considered less secure than other options, and can be blocked by firewalls. Performance is generally lower than other protocols.
Encryption Methods in VPNs
Encryption is the process of converting data into an unreadable format to protect it from unauthorized access. VPNs employ various encryption algorithms to secure the data transmitted over the VPN tunnel. The strength of the encryption is determined by the algorithm used and the key length.
- AES (Advanced Encryption Standard): AES is a widely adopted symmetric-key encryption algorithm. It is considered very secure and is available in key lengths of 128, 192, and 256 bits. AES-256 is often recommended for the highest level of security.
AES-256 provides a high level of security by using a 256-bit key, which makes it computationally infeasible for attackers to break the encryption using current technology.
- 3DES (Triple DES): 3DES is an older symmetric-key encryption algorithm that encrypts data three times using the Data Encryption Standard (DES) algorithm. It is considered less secure than AES, especially with the availability of more powerful computing resources.
3DES is vulnerable to attacks due to its smaller key size and the advancement in computing power, making it less suitable for modern security requirements.
- ChaCha20: ChaCha20 is a stream cipher known for its speed and security, especially on devices with limited processing power. It is often used in conjunction with the Poly1305 message authentication code.
ChaCha20 is favored for its efficiency on devices where AES performance might be a bottleneck.
- Encryption Key Lengths: The length of the encryption key significantly impacts the security level. Longer key lengths offer stronger protection.
- 128-bit Encryption: Provides a good level of security, suitable for many applications.
- 192-bit Encryption: Offers a higher level of security than 128-bit encryption.
- 256-bit Encryption: Provides the highest level of security, making it very difficult to crack.
Potential Vulnerabilities of Outdated Protocols and Encryption
Using outdated VPN protocols and encryption methods can expose a corporate network to significant security risks. Outdated protocols often have known vulnerabilities that can be exploited by attackers.
- Deprecated Protocols: Protocols like PPTP (Point-to-Point Tunneling Protocol) are considered insecure and should not be used. PPTP uses weak encryption and is susceptible to various attacks.
PPTP’s reliance on weak encryption and its vulnerability to known attacks make it a high-risk option for any organization.
- Weak Encryption Algorithms: Algorithms like 3DES are considered outdated and vulnerable to modern attacks. Their shorter key lengths make them easier to crack.
Organizations should prioritize using strong encryption algorithms like AES-256 to protect their sensitive data.
- Known Exploits: Outdated protocols and encryption methods are often targets of known exploits. Attackers can use these exploits to gain unauthorized access to the network and steal sensitive data.
Keeping VPN software and protocols updated with the latest security patches is crucial to mitigating the risk of known exploits.
- Man-in-the-Middle Attacks: Outdated protocols may be susceptible to man-in-the-middle attacks, where attackers intercept and potentially alter the data transmitted over the VPN.
Regular security audits and penetration testing can help identify and address vulnerabilities in VPN configurations.
Remote Access and Secure Connectivity
A Virtual Private Network (VPN) is a cornerstone of secure remote access for modern corporations. It enables employees to connect to the company network from anywhere in the world, maintaining a high level of security for sensitive data and resources. This section details how VPNs achieve this, the practical steps involved in setting up a connection, and a visual representation of a typical corporate VPN setup.
Facilitating Secure Remote Access for Employees
VPNs play a critical role in providing secure remote access. They create an encrypted tunnel over the public internet, protecting data in transit. This is particularly crucial for employees working remotely, as their internet connections may not be inherently secure. The VPN ensures that all data transmitted between the remote worker’s device and the corporate network is protected from eavesdropping and unauthorized access.VPNs achieve this secure connection by:
- Encryption: Data is encrypted using robust algorithms, rendering it unreadable to anyone without the decryption key.
- Authentication: VPNs verify the identity of the user before granting access to the network. This often involves usernames, passwords, and sometimes multi-factor authentication.
- IP Address Masking: The VPN assigns a corporate IP address to the remote user, masking their actual IP address and location, thereby increasing privacy.
- Secure Tunneling: The VPN creates a secure tunnel that encapsulates all network traffic, protecting it from interception.
The combination of these features ensures that remote workers can access corporate resources securely, as if they were physically present in the office. This allows employees to work from home, while traveling, or at any location with an internet connection, while maintaining a secure connection to the corporate network.
Setting Up a VPN Connection for a Remote Worker
Setting up a VPN connection for a remote worker typically involves several steps, depending on the specific VPN client and operating system being used. The process usually begins with the IT department providing the necessary credentials and configuration information.The general steps include:
- Installation of VPN Client Software: The remote worker needs to install the VPN client software on their device. This software is usually provided by the company or can be downloaded from the VPN provider.
- Configuration: The user configures the VPN client with the necessary settings. This includes the server address, username, password, and any other authentication requirements provided by the IT department.
- Authentication: The user enters their credentials to authenticate with the VPN server. This step verifies the user’s identity.
- Connection Establishment: Once authenticated, the VPN client establishes a secure connection to the corporate network. This creates the encrypted tunnel.
- Resource Access: After a successful connection, the remote worker can access corporate resources, such as file servers, applications, and internal websites, as if they were connected directly to the office network.
The specific steps and the user interface will vary depending on the VPN client and the operating system. However, the general process remains the same. The IT department often provides detailed instructions and support to ensure that employees can easily set up and use the VPN connection.
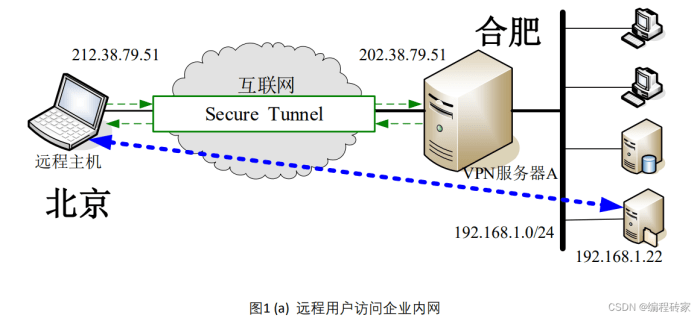
Basic Network Diagram: Corporate VPN Setup for Remote Access
The following network diagram illustrates a basic corporate VPN setup for remote access. The diagram depicts the key components and the flow of data.
The diagram illustrates a network with the following components and their interactions:
- Remote Worker: Represents an employee working remotely, using a laptop or other device. This is the starting point of the secure connection.
- Internet: The public internet, providing the communication channel between the remote worker and the corporate network. The VPN tunnel travels through the internet.
- VPN Client: Software installed on the remote worker’s device, responsible for encrypting and decrypting data, and establishing the secure connection to the VPN server.
- VPN Server: Located within the corporate network, the VPN server receives the encrypted traffic from the remote worker, decrypts it, and forwards it to the internal network resources. The VPN server also handles authentication.
- Firewall: A security device that protects the corporate network from unauthorized access. The firewall allows VPN traffic to pass through, but blocks other unwanted traffic.
- Corporate Network: The internal network containing the company’s servers, applications, and other resources. The VPN server allows remote users to access these resources securely.
The data flow:
The remote worker initiates the connection through the VPN client. The client encrypts the data and sends it over the internet to the VPN server. The VPN server, located behind the corporate firewall, decrypts the data and forwards it to the internal network resources. The responses are then encrypted and sent back to the remote worker through the same path.
Data Protection and Privacy Considerations
Understanding and implementing robust data protection and privacy measures is crucial for any organization, especially when dealing with sensitive corporate information. A Virtual Private Network (VPN) plays a significant role in safeguarding this data by providing a secure and encrypted channel for communication. This section will explore the specific measures a VPN employs to protect sensitive corporate data, address common data privacy threats, and demonstrate how a VPN aids in regulatory compliance.
VPN Measures for Data Protection
A VPN provides several layers of protection to secure sensitive corporate data. These measures work in concert to create a robust security posture.
- Encryption: VPNs encrypt all data transmitted between a user’s device and the VPN server. This means that even if intercepted, the data is unreadable without the proper decryption key. Strong encryption algorithms, such as AES-256, are commonly used to provide a high level of security.
- Secure Tunnels: VPNs create secure tunnels using protocols like OpenVPN, WireGuard, or IKEv2/IPsec. These tunnels encapsulate the data packets, protecting them from eavesdropping and tampering.
- IP Address Masking: A VPN masks the user’s real IP address, replacing it with the VPN server’s IP address. This makes it difficult for attackers to identify the user’s location and track their online activity.
- Authentication: VPNs use authentication mechanisms to verify the identity of users attempting to connect. This can include usernames and passwords, multi-factor authentication (MFA), or digital certificates.
- Access Control: VPNs allow administrators to control access to corporate resources based on user roles and permissions. This helps to prevent unauthorized access to sensitive data.
- Split Tunneling (if configured): Split tunneling allows only specific traffic to be routed through the VPN, while other traffic uses the regular internet connection. This can be useful for optimizing performance and security. However, it should be carefully configured to avoid security vulnerabilities.
Data Privacy Threats and VPN Mitigation
Various data privacy threats can compromise corporate data. A VPN helps mitigate these threats by implementing several security measures.
- Eavesdropping: Attackers can eavesdrop on unencrypted network traffic, potentially gaining access to sensitive information. A VPN mitigates this threat by encrypting all data transmitted over the network, making it unreadable to unauthorized parties.
- Man-in-the-Middle (MitM) Attacks: In a MitM attack, an attacker intercepts communication between two parties, potentially stealing data or injecting malicious content. VPNs protect against MitM attacks by encrypting the connection and verifying the authenticity of the VPN server.
- Data Breaches: Data breaches can occur when sensitive data is exposed due to weak security measures. A VPN reduces the risk of data breaches by encrypting data in transit and providing secure access controls.
- Unsecured Wi-Fi Networks: Public Wi-Fi networks are often unsecured and vulnerable to attacks. Using a VPN on these networks encrypts the connection, protecting data from potential eavesdropping and theft.
- Malware and Phishing Attacks: While a VPN doesn’t directly protect against malware or phishing, it can add an extra layer of security by masking the user’s IP address and preventing attackers from easily targeting specific devices or networks. Furthermore, by encrypting the connection, it can help prevent attackers from injecting malicious content.
VPN and Compliance with Data Protection Regulations
Many data protection regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), require organizations to implement measures to protect personal data. A VPN can assist organizations in meeting these requirements.
- Data Encryption: GDPR mandates the protection of personal data. A VPN’s encryption capabilities ensure that data is protected during transit, helping organizations comply with GDPR’s security requirements.
- Secure Remote Access: GDPR and CCPA emphasize the importance of securing remote access to personal data. VPNs provide a secure and encrypted channel for remote workers, ensuring that data is protected even when accessed from outside the corporate network.
- IP Address Masking and Location Privacy: While not a direct requirement of GDPR or CCPA, the ability of a VPN to mask IP addresses and protect location data can indirectly assist in complying with data minimization principles and respecting user privacy rights.
- Compliance with Data Transfer Regulations: When transferring data across borders, VPNs can help organizations comply with data transfer regulations by providing a secure and encrypted channel for data transmission. For example, a company based in the United States can use a VPN to securely transmit data to its European subsidiary, adhering to GDPR’s requirements for data transfers outside the EU.
- Auditing and Logging (where applicable): Some VPN providers offer logging capabilities that can be used for auditing purposes. This can help organizations demonstrate their compliance with data protection regulations by providing evidence of secure data handling practices. However, it’s crucial to configure logging appropriately to balance security needs with privacy considerations.
VPN Deployment Methods and Infrastructure
Deploying a Virtual Private Network (VPN) effectively requires careful consideration of various methods and the underlying infrastructure. The choice of deployment method significantly impacts performance, scalability, and security. Understanding the different options available allows organizations to select the solution best suited to their specific needs and resources.
VPN Deployment Methods
Several approaches exist for deploying VPNs, each with its own strengths and weaknesses. The selection process often involves balancing cost, security requirements, and the technical expertise available within the organization. The most common methods include hardware VPNs, software VPNs, and cloud-based VPNs.
To help with the comparison, the following table provides a detailed overview of the advantages and disadvantages of each VPN deployment method:
| Deployment Method | Advantages | Disadvantages | Use Cases |
|---|---|---|---|
| Hardware VPN |
|
|
|
| Software VPN |
|
|
|
| Cloud-Based VPN |
|
|
|
VPN Infrastructure Components
Implementing a corporate VPN involves several key infrastructure components that work together to provide secure remote access. Each component plays a crucial role in ensuring the confidentiality, integrity, and availability of data transmitted over the VPN. These components include servers, firewalls, and authentication systems.
- VPN Servers: VPN servers are the core of the VPN infrastructure. They establish secure tunnels, encrypt and decrypt data, and manage user connections. The type of VPN server selected depends on the chosen deployment method (e.g., a dedicated hardware appliance, a software-based server, or a cloud-based service). Examples of popular VPN server software include OpenVPN, StrongSwan, and Microsoft’s Routing and Remote Access Service (RRAS).
The VPN server is responsible for authenticating users, assigning IP addresses, and managing the encryption keys used to secure the VPN tunnel.
- Firewalls: Firewalls are essential for protecting the VPN server and the internal network from unauthorized access. They filter network traffic based on predefined rules, allowing only authorized traffic to pass through. The firewall can be integrated into the VPN server or implemented as a separate hardware or software appliance. Firewalls are configured to permit VPN traffic while blocking other potentially malicious traffic.
They also often provide intrusion detection and prevention capabilities.
- Authentication Systems: Authentication systems verify the identity of users attempting to connect to the VPN. This can involve usernames and passwords, multi-factor authentication (MFA), or digital certificates. MFA adds an extra layer of security by requiring users to provide two or more verification factors, such as something they know (password), something they have (security token), or something they are (biometric data).
Popular authentication methods include RADIUS, Active Directory integration, and certificate-based authentication.
VPN Management and Administration
Managing a corporate VPN is crucial for maintaining secure and efficient network access. Effective administration ensures that authorized users can connect reliably while preventing unauthorized access and protecting sensitive data. This involves a multifaceted approach encompassing user access control, monitoring, troubleshooting, and ongoing maintenance.
User Access Control and Monitoring
User access control and monitoring are fundamental aspects of VPN administration, ensuring that only authorized individuals can access the network and that their activities are tracked for security and compliance purposes. Implementing robust access controls and actively monitoring VPN usage are vital for maintaining a secure and compliant corporate environment.
- User Authentication and Authorization: Implementing strong authentication methods is essential. This includes using multi-factor authentication (MFA), such as a combination of username/password and a one-time code generated by an authenticator app or sent via SMS. Strong password policies should be enforced, requiring complex passwords and regular password changes. Authorization controls should define user permissions based on their roles and responsibilities within the organization.
This ensures that users only have access to the resources they need.
- Role-Based Access Control (RBAC): RBAC is a critical strategy for managing user permissions effectively. It assigns permissions based on a user’s role within the organization. For instance, a sales representative might have access to CRM systems and sales reports, while a finance employee has access to financial data. This simplifies administration and minimizes the risk of unauthorized access.
- VPN Activity Logging and Monitoring: Comprehensive logging of VPN activity is essential for security and auditing. Logs should record connection attempts, successful and failed logins, data transfer volumes, and user activity within the network. Monitoring tools should be used to analyze these logs, detect suspicious behavior, and generate alerts for potential security breaches.
- Regular Auditing: Regular audits of VPN access logs and user permissions are crucial for identifying and addressing security vulnerabilities. These audits should verify that user access aligns with their current roles and that no unauthorized access has occurred. Any discrepancies should be promptly investigated and resolved.
Troubleshooting VPN Connection Issues
Troubleshooting VPN connection issues requires a systematic approach to identify and resolve problems that can prevent users from accessing the network. Effective troubleshooting ensures that VPN services remain reliable and accessible.
- Connectivity Issues: Connectivity issues are often the first point of investigation. Verify the user’s internet connection to ensure they can access the internet generally. Check the VPN server’s availability and status. Ping the VPN server’s IP address from the user’s device to confirm network reachability.
- Authentication Problems: Authentication failures are a common cause of VPN connection issues. Verify that the user is entering the correct username and password. If MFA is enabled, ensure the user is correctly entering the MFA code. Check the user’s account status to ensure it is not locked or disabled.
- Firewall Restrictions: Firewalls can sometimes block VPN connections. Check the firewall settings on the user’s device and the network firewall to ensure that the necessary VPN ports and protocols are allowed. Commonly used VPN ports include UDP 500, UDP 4500 (for IPsec), and TCP 443 (for SSL/TLS).
- Configuration Errors: Incorrect VPN configuration settings on the user’s device can prevent successful connections. Verify the VPN server address, authentication type, encryption settings, and any other required configuration parameters. Compare the user’s configuration with the correct settings provided by the IT department.
- Client-Side Software Problems: Outdated or corrupted VPN client software can also cause issues. Ensure that the user is using the latest version of the VPN client software. Try reinstalling the VPN client software to resolve potential software conflicts or corruption.
Maintaining and Updating Corporate VPN Infrastructure
Maintaining and updating a corporate VPN infrastructure is crucial for ensuring optimal performance, security, and compliance. This involves regular maintenance, security updates, and infrastructure upgrades.
- Regular Security Updates: Regularly apply security patches and updates to the VPN server software and client software. This addresses known vulnerabilities and protects against emerging threats. Establish a patching schedule to ensure timely updates.
- Infrastructure Monitoring: Implement comprehensive monitoring of the VPN infrastructure, including server performance, network traffic, and connection logs. Use monitoring tools to detect and alert on performance bottlenecks, security threats, and potential issues.
- Capacity Planning and Scalability: Regularly assess the VPN infrastructure’s capacity to handle current and future user demand. Plan for scalability to accommodate growth in user numbers and data traffic. This may involve upgrading server hardware, increasing bandwidth, or deploying additional VPN servers.
- VPN Server Hardening: Implement security best practices to harden the VPN server. This includes disabling unnecessary services, configuring strong encryption protocols, and regularly reviewing server configurations for vulnerabilities.
- Documentation and Training: Maintain up-to-date documentation of the VPN infrastructure, including configuration settings, troubleshooting procedures, and security policies. Provide training to IT staff and users on VPN usage, security best practices, and troubleshooting common issues.
Cost Analysis and ROI of Corporate VPNs
Implementing and maintaining a corporate Virtual Private Network (VPN) involves a range of costs that must be carefully considered to determine the true value and return on investment (ROI). A thorough cost analysis is essential for making informed decisions about VPN solutions and ensuring that the chosen solution aligns with the organization’s budget and security needs. This section delves into the various cost factors, compares different VPN solutions, and provides a basic ROI model to help organizations assess the financial viability of a corporate VPN.
Cost Factors Associated with Corporate VPNs
Several cost factors contribute to the overall expense of implementing and maintaining a corporate VPN. Understanding these costs is crucial for budgeting and making informed decisions.
- Hardware Costs: These include the expenses associated with purchasing and maintaining the physical infrastructure required for the VPN. This might involve dedicated VPN servers, routers, firewalls, and other network appliances. The specific hardware needs depend on the size of the organization, the number of concurrent users, and the required bandwidth.
- Software Costs: These encompass the costs of VPN software licenses, operating system licenses, and any additional security software required for the VPN. Software costs can vary depending on the features, scalability, and vendor. Some vendors offer subscription-based models, while others offer perpetual licenses.
- Implementation Costs: These costs cover the labor and resources required to set up and configure the VPN infrastructure. This includes the time spent by IT staff on tasks such as installing software, configuring network settings, and testing the VPN connection. Implementation costs can also involve hiring external consultants or service providers.
- Ongoing Maintenance Costs: These are the expenses incurred to keep the VPN running smoothly over time. They include the cost of IT staff to manage the VPN, software updates, hardware maintenance, and troubleshooting. These costs can vary depending on the complexity of the VPN and the level of IT support required.
- Bandwidth and Data Transfer Costs: The cost of internet bandwidth and data transfer can significantly impact the overall VPN expenses. Organizations need to ensure they have sufficient bandwidth to support the VPN traffic without impacting network performance. This may involve upgrading internet plans or investing in additional bandwidth capacity.
- Security Audits and Compliance Costs: Organizations may need to conduct regular security audits to ensure the VPN is secure and compliant with industry regulations. These audits can involve hiring external security professionals or utilizing internal resources. There may also be costs associated with achieving and maintaining compliance with data privacy regulations.
- Training Costs: Training costs involve the expenses related to educating IT staff and end-users about the VPN. This includes training on VPN configuration, security best practices, and troubleshooting. Effective training helps ensure that the VPN is used securely and efficiently.
Comparison of Different VPN Solutions
The cost of VPN solutions varies depending on the type of solution chosen. It’s important to compare the costs of different options to determine the best fit for the organization’s needs and budget.
- Hardware-Based VPNs: These solutions involve purchasing and maintaining dedicated hardware appliances. They typically offer high performance and security but can be more expensive upfront due to hardware costs. They also require ongoing maintenance and IT expertise.
- Software-Based VPNs: These solutions use software installed on existing servers or virtual machines. They can be more cost-effective than hardware-based solutions, especially for smaller organizations. However, they may require more IT expertise to configure and manage.
- Cloud-Based VPNs: These solutions are hosted in the cloud and offer scalability and flexibility. They typically involve subscription-based pricing and may have lower upfront costs. Cloud-based VPNs can be a good option for organizations that need to quickly deploy a VPN or scale their VPN capacity. However, organizations need to consider the security and privacy implications of storing their data in the cloud.
- Managed VPN Services: These services provide end-to-end VPN solutions, including hardware, software, and management. They can reduce the burden on internal IT staff and offer a predictable cost structure. However, they may be more expensive than self-managed solutions.
Design of a Basic ROI Model for Corporate VPN Implementation
A basic ROI model can help organizations evaluate the financial benefits of implementing a corporate VPN. This model should include both tangible and intangible benefits.
- Tangible Benefits: These are quantifiable benefits that can be directly measured in monetary terms.
- Reduced Travel Costs: VPNs enable remote access, reducing the need for employees to travel for meetings and other business activities. For example, if an organization saves an average of $500 per business trip, and a VPN reduces travel by 10%, the savings can be easily calculated.
- Increased Productivity: VPNs enable employees to work securely from anywhere, increasing productivity. For instance, if a company has 100 employees, and the VPN increases productivity by 1 hour per day per employee (valued at an average hourly rate of $30), the productivity gains can be quantified.
- Reduced IT Support Costs: VPNs can reduce the need for IT support related to troubleshooting network issues or security breaches.
- Intangible Benefits: These are benefits that are more difficult to quantify but still contribute to the overall value of the VPN.
- Enhanced Security: VPNs provide a secure connection for remote access, protecting sensitive data from unauthorized access.
- Improved Data Privacy: VPNs encrypt data transmitted over the network, protecting sensitive information from interception.
- Increased Employee Satisfaction: VPNs allow employees to work remotely, improving work-life balance and employee satisfaction.
- Compliance with Regulatory Requirements: VPNs help organizations meet data privacy and security regulations.
- ROI Calculation: The ROI can be calculated using the following formula:
- Example:
- Total Costs: $20,000 (hardware, software, implementation, and ongoing maintenance)
- Total Benefits: $30,000 (reduced travel costs, increased productivity, and improved security)
- ROI: [($30,000 – $20,000) / $20,000]
– 100 = 50% - Important Considerations:
- Timeframe: The ROI calculation should be based on a specific timeframe, such as one year or three years.
- Assumptions: Clearly state all assumptions used in the model, such as the average cost of a business trip or the value of an hour of employee time.
- Sensitivity Analysis: Perform a sensitivity analysis to assess how changes in key variables, such as travel costs or productivity gains, affect the ROI.
ROI = [(Total Benefits – Total Costs) / Total Costs] – 100
Use Cases and Practical Applications
Corporations leverage Virtual Private Networks (VPNs) for a multitude of purposes, ranging from securing remote access for employees to safeguarding sensitive data transmitted across public networks. The versatility of VPN technology makes it a crucial component of a robust cybersecurity strategy across diverse industries. Understanding the practical applications of VPNs is essential for businesses seeking to protect their information and maintain operational efficiency.
Securing Communications in Industries Handling Sensitive Information
Industries dealing with sensitive data, such as healthcare and finance, require stringent security measures to protect patient information, financial transactions, and proprietary data. VPNs play a critical role in securing communications within these sectors.VPNs are crucial for these industries because they establish encrypted tunnels for all data transmitted between a user’s device and the corporate network. This encryption protects sensitive information from interception by malicious actors.Here’s how VPNs are used in specific industries:
- Healthcare: Healthcare providers utilize VPNs to secure patient data transmitted between clinics, hospitals, and remote healthcare professionals. VPNs ensure compliance with regulations like HIPAA (Health Insurance Portability and Accountability Act) by encrypting patient records and protecting them from unauthorized access. For example, a hospital may use a VPN to allow doctors to securely access patient medical records from their homes or other locations, ensuring patient confidentiality and data privacy.
- Finance: Financial institutions rely heavily on VPNs to protect sensitive financial transactions, customer data, and internal communications. VPNs encrypt data transmitted during online banking, stock trading, and other financial activities, preventing fraud and data breaches. For instance, a bank might use a VPN to secure communications between its branches, ensuring the secure transfer of financial data and preventing unauthorized access to customer accounts.
- Legal: Law firms use VPNs to secure communications, protecting client confidentiality and privileged information. Lawyers can securely access documents and communicate with clients from anywhere, ensuring the integrity of legal proceedings.
VPN Applications in Various Industries
VPNs offer various applications across different industries, contributing to enhanced security, improved productivity, and streamlined operations. The following bulleted list provides a snapshot of how VPNs are utilized in different sectors:
- Remote Access for Employees: VPNs enable employees to securely access corporate resources, such as files, applications, and internal networks, from remote locations. This is particularly beneficial for companies with a distributed workforce or employees who frequently travel.
- Secure Internet Browsing: VPNs encrypt internet traffic, protecting against eavesdropping and data theft. This is particularly important when employees are using public Wi-Fi networks, which are often vulnerable to security threats.
- Data Protection and Privacy: VPNs protect sensitive data transmitted over the internet by encrypting the data and masking the user’s IP address. This prevents unauthorized access to corporate data and protects employee privacy.
- Bypassing Geo-Restrictions: VPNs can be used to bypass geographic restrictions and access content that is not available in a specific region. This is particularly useful for companies with international operations or employees who need to access region-specific content.
- Secure Communication between Offices: VPNs establish secure connections between different office locations, allowing for secure data transfer and communication. This is especially important for companies with multiple branches or offices located in different geographical areas.
- Secure Cloud Access: VPNs can be used to securely access cloud-based applications and services. This is essential for companies that rely on cloud computing for their operations.
- Compliance with Data Privacy Regulations: VPNs help organizations comply with data privacy regulations such as GDPR (General Data Protection Regulation) by encrypting data and protecting it from unauthorized access.
Future Trends and Innovations
The landscape of VPN technology is constantly evolving, driven by the need for enhanced security, improved performance, and greater adaptability to changing network environments. Corporate VPNs are at the forefront of these advancements, with several key trends poised to reshape how businesses approach secure remote access and data protection. Understanding these emerging innovations is crucial for organizations seeking to maintain a robust and future-proof cybersecurity posture.
Emerging Trends in VPN Technology
Several trends are gaining momentum in the VPN space, promising to improve security, performance, and user experience. These trends are impacting how corporations leverage VPNs.
- SD-WAN Integration: Software-Defined Wide Area Networks (SD-WAN) are increasingly being integrated with VPNs. This integration enables intelligent traffic routing, prioritizing business-critical applications and optimizing network performance across multiple WAN connections. For example, a company might use SD-WAN to automatically route video conferencing traffic over a high-bandwidth, low-latency path while routing less critical traffic over a more cost-effective connection.
- 5G and Mobile VPNs: The rollout of 5G networks is creating opportunities for faster and more reliable mobile VPN connections. VPNs are being optimized to take advantage of 5G’s increased bandwidth and reduced latency, enabling seamless and secure access to corporate resources from mobile devices. A field service technician, for example, could securely access sensitive customer data on their tablet using a 5G-enabled VPN connection.
- AI-Powered VPNs: Artificial intelligence (AI) and machine learning (ML) are being applied to VPN technology for threat detection, anomaly detection, and automated security policy enforcement. AI can analyze network traffic patterns to identify and respond to potential security threats in real-time. This could include detecting unusual access attempts or identifying malware activity.
- Quantum-Resistant Encryption: As quantum computing advances, the need for encryption algorithms resistant to quantum attacks becomes critical. VPN providers are beginning to incorporate quantum-resistant encryption methods to protect data from potential future threats. This proactive approach ensures long-term data security.
- Cloud-Based VPNs: The adoption of cloud-based VPN services is growing, offering scalability, ease of deployment, and centralized management. Cloud VPNs allow businesses to quickly adapt to changing workforce needs and reduce the burden of managing on-premises hardware. A company expanding its operations can rapidly deploy VPN access for new employees in different locations.
The Role of VPNs in a Zero-Trust Security Model
Zero-trust security is a security framework based on the principle of “never trust, always verify.” VPNs play a crucial role in implementing a zero-trust architecture by providing secure, authenticated access to corporate resources, even when users are outside the corporate network.
- Micro-segmentation: VPNs can be used to create micro-segments within the network, restricting access to only the resources needed by a particular user or device. This minimizes the impact of a potential security breach. For example, a VPN might only allow a financial analyst access to the finance server, while preventing access to other departments’ data.
- Multi-Factor Authentication (MFA): VPNs often integrate with MFA solutions, requiring users to verify their identity through multiple methods, such as passwords, one-time codes, and biometric authentication. This significantly reduces the risk of unauthorized access.
- Device Posture Assessment: VPNs can assess the security posture of a connecting device, ensuring it meets certain security requirements before granting access. This could include checking for up-to-date antivirus software, patched operating systems, and other security configurations.
- Continuous Monitoring and Threat Detection: VPNs can be integrated with security information and event management (SIEM) systems to provide continuous monitoring of network traffic and detect suspicious activity. This allows for rapid response to potential threats.
The future of VPNs in corporate cybersecurity is defined by their evolution towards greater intelligence, adaptability, and integration within comprehensive security frameworks. VPNs will move beyond simple access tools, becoming integral components of zero-trust architectures, leveraging AI for threat detection, and seamlessly integrating with emerging technologies like SD-WAN and 5G. This evolution will ensure that VPNs remain essential for securing remote access and protecting sensitive corporate data in an increasingly complex and dynamic threat landscape.
Final Summary
In conclusion, what is a virtual private network (VPN) for corporate use represents a critical investment in data security, remote access capabilities, and regulatory compliance. By understanding the various aspects of VPN technology, from protocols and deployment methods to management and cost considerations, businesses can effectively fortify their digital defenses and create a more secure and efficient operational environment. The future of corporate cybersecurity will continue to be shaped by VPNs and their evolving role in a zero-trust model.
User Queries
What is the primary benefit of using a VPN for corporate use?
The primary benefit is secure and private access to corporate resources, protecting sensitive data from unauthorized access and cyber threats, especially for remote workers.
What types of encryption are typically used by corporate VPNs?
Common encryption methods include AES (Advanced Encryption Standard) with various key lengths, ensuring a high level of data protection.
Are all VPN protocols equally secure?
No, different protocols offer varying levels of security. Newer protocols like WireGuard are generally considered more secure than older ones like PPTP.
How does a VPN help with compliance regulations like GDPR?
A VPN helps by encrypting data, limiting data exposure, and providing secure access, which supports compliance with data protection regulations by protecting sensitive information.
What are the potential drawbacks of using a VPN?
Drawbacks can include potential performance slowdowns due to encryption overhead, the need for proper configuration and management, and the possibility of vulnerabilities if protocols or configurations are outdated.