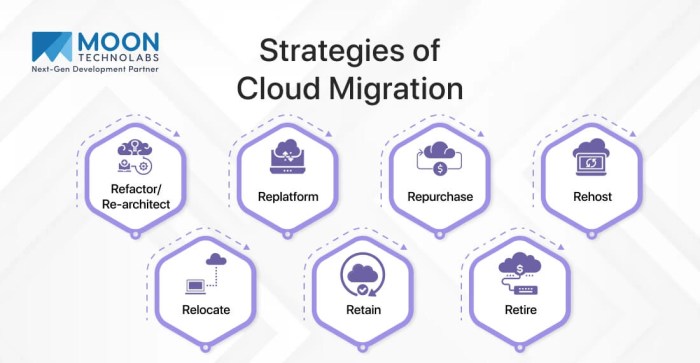
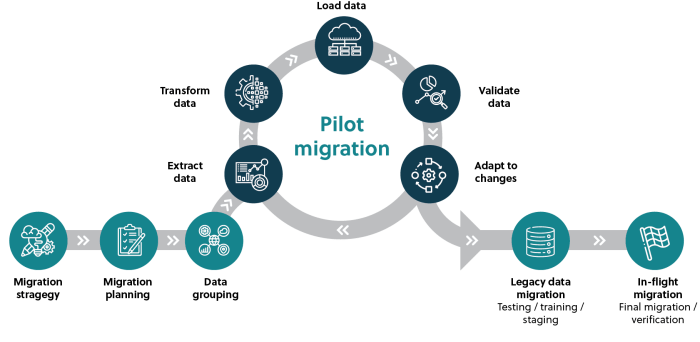
Data migration, the process of transferring data from one system to another, is a complex undertaking. At its heart lies the final cutover plan, a critical roadmap that dictates the precise steps required to transition from the old system to the new. This plan is not merely a checklist; it’s a carefully orchestrated sequence of actions designed to minimize downtime, mitigate risks, and ensure data integrity.
Understanding the intricacies of a final cutover plan is paramount for a successful migration, and this guide will delve into its essential components, from pre-cutover preparations to post-cutover support.
This exploration will provide a comprehensive overview of the final cutover plan, examining its purpose, key activities, and the critical considerations necessary for a smooth transition. We’ll dissect the various stages, including pre-cutover preparations, the execution of the cutover itself, data validation, risk mitigation, rollback procedures, communication strategies, and post-cutover support. The aim is to equip readers with the knowledge and tools to navigate the complexities of data migration with confidence, ultimately leading to a successful and efficient transition.
Definition and Purpose of a Final Cutover Plan
A final cutover plan is a meticulously crafted document outlining the precise steps, timelines, and resources required to transition from a legacy system to a new system, particularly in the context of data migration. Its primary function is to minimize downtime, data loss, and business disruption during the final migration phase. This plan serves as the operational blueprint for the “go-live” event, ensuring a smooth and controlled switchover.
Core Objective of a Final Cutover Plan
The core objective of a final cutover plan is to facilitate a seamless and efficient transition from the source system to the target system. This involves minimizing disruption to business operations, preserving data integrity, and ensuring the availability of the new system. The plan aims to provide a structured and controlled approach, encompassing all necessary activities from data validation to system decommissioning.
Key Components of a Comprehensive Final Cutover Plan
A comprehensive final cutover plan consists of several crucial components, each playing a specific role in the successful migration. These components, when integrated, provide a robust framework for the transition.
- Pre-Cutover Activities: These activities encompass tasks performed before the final migration window. They include:
- Data validation and reconciliation to ensure data accuracy and completeness. This involves comparing data between the source and target systems, identifying and resolving discrepancies. For example, a financial institution might reconcile account balances and transaction histories.
- Final data extraction and transformation. This step prepares the final set of data for migration, ensuring it conforms to the target system’s requirements.
- System and infrastructure readiness checks, including verifying network connectivity, hardware capacity, and software configurations. This stage confirms the readiness of the target environment.
- User training and communication, to prepare users for the new system. This includes providing training materials, user manuals, and communication regarding the cutover process.
- Cutover Execution: This section details the specific steps and timelines for the actual migration. It is the heart of the plan.
- Detailed step-by-step instructions, including precise timings for each task. This level of detail is critical for ensuring a coordinated effort.
- Rollback procedures, in case of unforeseen issues. These procedures Artikel the steps to revert to the original system if the migration fails.
- Communication plan to keep stakeholders informed about progress. This includes predefined communication channels and frequency.
- Roles and responsibilities, clearly defining who is responsible for each task. This ensures accountability and prevents confusion.
- Post-Cutover Activities: These activities are performed after the new system is live.
- Data validation and verification to confirm data integrity in the target system. This involves running tests and checks to ensure that data has been migrated correctly.
- System stabilization and performance monitoring to address any initial issues and optimize performance. This includes monitoring system performance and addressing any identified bottlenecks.
- User support and issue resolution to assist users with any problems they encounter. This involves providing a help desk or support system.
- System decommissioning of the legacy system, including data archiving and physical removal of hardware. This step ensures the complete transition to the new system.
- Contingency Planning: This element addresses potential risks and mitigation strategies.
- Risk assessment and mitigation plans, identifying potential risks and outlining mitigation strategies. This includes identifying risks like data corruption, system failures, or delays.
- Rollback procedures, which are essential for reverting to the old system if the cutover fails. This allows for a quick return to the previous state.
- Backup and recovery plans to ensure data protection and business continuity. These plans Artikel the steps to back up data and recover from any data loss.
Benefits of a Well-Defined Final Cutover Plan
A well-defined final cutover plan offers several significant benefits, contributing to a more successful and less disruptive migration process. These benefits often translate into cost savings and increased operational efficiency.
- Reduced Downtime: A detailed plan with precise timings minimizes the duration of system downtime. Careful planning and execution are crucial for reducing the period during which the system is unavailable. For example, a retail company with a well-executed cutover plan can minimize downtime, ensuring minimal disruption to sales.
- Minimized Data Loss: Thorough data validation and reconciliation processes within the plan significantly reduce the risk of data loss or corruption. This ensures data integrity during the transition.
- Enhanced Business Continuity: Robust rollback procedures and contingency plans ensure business operations can continue even if unexpected issues arise. This protects the business from major disruptions.
- Improved User Acceptance: Well-planned user training and communication efforts increase user confidence and acceptance of the new system. Users who are prepared for the change are more likely to adapt quickly.
- Cost Efficiency: A structured plan helps prevent costly errors and delays, leading to overall cost savings. For example, a manufacturing company can save significant costs by avoiding production downtime and data loss.
- Increased Stakeholder Confidence: A well-defined plan instills confidence in stakeholders, including management, users, and customers. Clear communication and transparency during the cutover process build trust and reduce anxiety.
Pre-Cutover Activities and Preparations
Pre-cutover activities are crucial to a successful migration, laying the groundwork for a smooth transition and minimizing potential disruptions. These activities encompass a range of tasks, from data validation and system configuration to user training and communication, all designed to ensure the target environment is ready to receive the migrated data and applications. Thorough planning and execution of these preparations are essential to mitigate risks and achieve a successful cutover.
Critical Pre-Cutover Tasks
The success of the cutover phase hinges on the meticulous execution of several critical tasks. These tasks, when completed, provide the foundation for a seamless transition. Neglecting any of these tasks can significantly increase the risk of downtime, data loss, or other critical failures during the cutover.
- Data Migration Validation and Reconciliation: This involves verifying the integrity and accuracy of migrated data. Data validation includes comparing data sets between the source and target environments, identifying and resolving discrepancies, and ensuring data consistency. Reconciliation processes confirm that all data has been migrated successfully, and any missing data is identified and addressed before cutover. For example, if migrating customer records, the validation process would involve comparing the number of records, field values (e.g., addresses, phone numbers), and data types between the source and target systems.
Tools like checksums and data comparison utilities are used to ensure data integrity.
- System Configuration and Testing: This encompasses configuring the target environment to match the requirements of the migrated applications and data. This involves setting up servers, databases, network configurations, and security settings. Rigorous testing is then conducted to ensure that all systems and applications function correctly in the new environment. This testing includes unit testing, integration testing, and user acceptance testing (UAT). For instance, after configuring a new database server, tests would involve running queries, verifying data access permissions, and simulating user load to assess performance and stability.
- User Training and Communication: Training users on the new systems and processes is essential for user adoption and minimizing post-cutover issues. This involves developing training materials, conducting training sessions, and providing ongoing support. Clear and timely communication with all stakeholders, including users, management, and IT staff, is critical to keep everyone informed of the migration progress and any potential disruptions. For example, before migrating an email system, users would be trained on the new email client interface, and support documentation would be provided.
Regular updates would be sent to users, informing them of the cutover schedule and any potential impact on their work.
- Cutover Plan Review and Approval: The final cutover plan, including all pre-cutover activities, the cutover schedule, and rollback procedures, must be reviewed and approved by all relevant stakeholders. This ensures that everyone is aligned on the plan and understands their roles and responsibilities. This also provides an opportunity to identify and address any potential risks or issues before the cutover.
- Rollback Strategy Validation: A robust rollback strategy is critical in case the cutover fails. The rollback strategy should be tested to ensure that the organization can revert to the original state with minimal downtime and data loss. This includes validating the ability to restore data from backups and revert system configurations. For example, before migrating a critical application, the rollback plan should include procedures for restoring the application from a backup, reconfiguring network settings, and reverting to the original database.
Pre-Cutover Preparation Checklist
A comprehensive checklist ensures that all necessary steps are taken before the cutover phase. This checklist serves as a guide to ensure that nothing is overlooked. Each item on the checklist must be addressed and verified as complete before proceeding to the cutover.
- Data Migration Completed and Verified
- Target Environment Configured and Tested
- Application Testing Completed and Approved
- User Training Materials Prepared and Delivered
- Communication Plan Implemented
- Rollback Plan Defined and Tested
- Cutover Plan Reviewed and Approved
- Backup Procedures Verified
- Security Configurations Verified
- Network Connectivity Tested
Workflow Diagram of Pre-Cutover Activities
A workflow diagram visually represents the sequence and dependencies of pre-cutover activities. The diagram illustrates the flow of tasks, from initiation to completion, highlighting the critical path and the relationships between different activities. The use of a flowchart helps to ensure that all activities are performed in the correct order and that dependencies are managed effectively.
Workflow Diagram Description:The diagram is a flowchart, starting with the initiation of the migration project.
The first step is “Data Migration Planning,” leading to parallel branches: “Data Migration” and “Environment Setup.”* Data Migration branches into “Data Extraction,” “Data Transformation,” and “Data Loading.” Each of these branches feeds into “Data Validation and Reconciliation.”
Environment Setup branches into “Hardware Provisioning,” “Software Installation,” and “Configuration.” All these lead into “System Testing” and “User Acceptance Testing (UAT).”
Both “Data Validation and Reconciliation” and “System Testing” (including UAT) feed into “Rollback Plan Validation.” Additionally, the “Rollback Plan Validation” and “Data Validation and Reconciliation” activities are connected to the “Cutover Plan Review and Approval” step.”User Training and Communication” is shown as running parallel to the activities of “Data Migration” and “Environment Setup,” with a final connection to the “Cutover Plan Review and Approval” step.Finally, all these branches converge at “Cutover Plan Review and Approval,” which leads to the “Cutover Phase.”
Cutover Execution
The Cutover Execution phase represents the culmination of all prior planning and preparation. It is the moment when the organization transitions from its legacy systems to the new environment. Meticulous execution is paramount to minimize downtime, data loss, and disruption to business operations. This section Artikels the step-by-step procedures required for a successful cutover, providing a detailed timeline and emphasizing critical considerations.
Step-by-Step Guide
The following steps provide a comprehensive guide to the cutover process, outlining the actions necessary to migrate from the old system to the new system. These steps are presented in a logical sequence, ensuring a structured and controlled transition. The exact steps will vary based on the complexity of the systems and the specific migration strategy.
- Pre-Cutover Verification and Final Data Synchronization: This stage involves a final check of all prerequisites, including hardware, software, and network configurations. Data synchronization is performed to ensure the new system has the most up-to-date data. The goal is to have the least amount of data drift possible, minimizing the amount of manual intervention required during and after the cutover.
- Freeze Period: This critical period, often lasting several hours or days before the cutover, restricts changes to the legacy system. This freeze minimizes data discrepancies and allows for a clean snapshot of the data to be migrated. All non-essential activities on the old system are halted.
- Final Data Migration: The final data migration involves transferring the most recent data from the legacy system to the new system. This step may include a full data export and import, or an incremental synchronization, depending on the data volume and the chosen migration strategy. The goal is to have the new system ready to operate with the most current data.
- System Shutdown: The legacy system is shut down. This is a crucial step that prevents further data modifications in the old system, and it is a point of no return in the process. It’s also a signal that the new system is taking over.
- System Configuration and Activation: This stage involves configuring the new system with the final settings and activating all necessary components. This includes network configurations, security settings, and application deployments.
- Data Validation and Verification: After the new system is active, rigorous data validation is performed. This step ensures that the data migrated from the legacy system is complete, accurate, and consistent. Automated tools and manual checks are used to identify and rectify any data integrity issues.
- User Training and System Access: End-users are provided with access to the new system, and training sessions are conducted to familiarize them with the new environment. This includes training on new functionalities and workflows.
- Post-Cutover Monitoring and Support: The new system is continuously monitored for performance issues, errors, and other anomalies. A dedicated support team is available to address user queries and resolve any problems that may arise.
Cutover Timeline
The cutover process is carefully orchestrated, following a detailed timeline to ensure all tasks are completed within the allocated timeframe. The following table provides an example of a cutover timeline, with estimated durations for each task. The actual times will vary based on the specific project and the complexity of the systems involved.
| Task | Start Time | End Time | Status |
|---|---|---|---|
| Pre-Cutover Verification and Final Data Synchronization | T-24 hours | T-6 hours | Completed |
| Freeze Period | T-6 hours | T-0 hours | Completed |
| Final Data Migration | T-6 hours | T-3 hours | Completed |
| System Shutdown | T-3 hours | T-2 hours | Completed |
| System Configuration and Activation | T-2 hours | T+1 hour | In Progress |
| Data Validation and Verification | T+1 hour | T+4 hours | In Progress |
| User Training and System Access | T+4 hours | T+8 hours | To Do |
| Post-Cutover Monitoring and Support | T+0 | Ongoing | Ongoing |
Data Migration Validation and Verification
Data migration validation and verification are critical steps in the cutover plan, ensuring the accuracy and completeness of the migrated data. These processes confirm that data is successfully transferred from the source system to the target system without loss or corruption, thereby minimizing the risk of operational disruptions and data inconsistencies. Robust validation and verification methodologies provide confidence in the integrity of the new system and facilitate a smooth transition.
Methods to Validate Successful Data Migration
Successful data migration hinges on employing rigorous validation techniques. These methods encompass a range of approaches, each designed to assess different aspects of the migration process.
- Data Profiling: Data profiling involves analyzing the source data to understand its characteristics, including data types, ranges, completeness, and potential anomalies. This process sets a baseline for comparison after migration. For example, if a customer database has an expected distribution of ages, data profiling helps identify if this distribution is maintained post-migration.
- Sample Data Testing: This technique involves selecting a representative sample of data from the source system and comparing it against the corresponding data in the target system. The selection of samples can be random, stratified, or based on specific criteria (e.g., critical business data). The comparison ensures data accuracy at the record level.
- Checksum Verification: Checksums are calculated for data files or databases before and after migration. Comparing these checksums provides a quick and efficient method to detect data corruption during the transfer process. If the checksums match, it strongly suggests that the data integrity has been maintained. For example, the MD5 checksum algorithm can be used.
- Data Volume Comparison: Comparing the total number of records and the total size of data files between the source and target systems can quickly identify any significant discrepancies. This check acts as a high-level indicator of migration completeness. Any major differences warrant further investigation.
- Business Rule Validation: This validation method involves testing the migrated data against business rules and constraints. For instance, validating that all customer accounts have a valid status or that transaction amounts fall within acceptable ranges. This ensures that the data adheres to the business logic.
Techniques for Verifying Data Integrity After Cutover
Verifying data integrity after the cutover is essential to ensure the reliability and usability of the migrated data. Various techniques can be used to achieve this, ranging from automated tools to manual reviews.
- Automated Data Quality Checks: Employing automated data quality tools to perform regular checks on the target system. These tools can identify inconsistencies, missing values, and data anomalies. The checks can be configured to run periodically, alerting administrators to potential issues.
- Data Auditing: Implementing data auditing mechanisms to track changes made to the data after migration. This allows for the identification of any data modifications that might have occurred and helps in tracing the source of errors. Audit trails provide valuable information for troubleshooting and ensuring data accuracy over time.
- User Acceptance Testing (UAT): Engaging business users in the verification process through UAT. Users test the data within the context of their daily operations, validating that the migrated data meets their needs and that business processes function correctly. This provides a practical assessment of data usability.
- Reconciliation Reporting: Generating reconciliation reports that compare data between the source and target systems. These reports highlight any discrepancies and provide detailed information about the differences. Reconciliation is particularly important for financial data, where accuracy is paramount.
- Performance Testing: Conducting performance testing to ensure that the migrated data does not negatively impact the performance of the target system. Performance tests can assess query response times, data retrieval speeds, and the overall system responsiveness. This ensures that the data migration has not introduced performance bottlenecks.
Performing Data Comparison Between Source and Target Systems
Data comparison is a critical process to ensure the accuracy and consistency of data after migration. This process involves comparing data from the source system with the corresponding data in the target system. Several methods and tools can be used to facilitate this comparison.
- Direct Database Queries: Utilizing SQL queries to compare data directly between the source and target databases. This method allows for the comparison of specific data elements, records, or tables. The queries can be customized to match data based on unique identifiers or other relevant criteria. For instance, a query might compare the number of orders in a specific date range.
- Data Comparison Tools: Employing specialized data comparison tools that automate the process of comparing data between systems. These tools offer features such as data matching, data transformation, and reporting. Examples include tools like Beyond Compare, and DB Comparer, which provide detailed reports on data discrepancies.
- ETL Tools: Leveraging ETL (Extract, Transform, Load) tools to extract data from both source and target systems, transform the data into a consistent format, and then compare the transformed data. ETL tools offer powerful data manipulation capabilities, allowing for complex comparisons.
- Statistical Analysis: Employing statistical methods to compare data distributions and identify anomalies. For example, comparing the average value of a field or performing a chi-squared test to compare the frequency distribution of data. This method is especially useful for detecting subtle data differences.
- Manual Review: In some cases, manual review may be necessary, especially for smaller datasets or for verifying specific data elements that are difficult to compare programmatically. This may involve spot-checking records and verifying data accuracy. This can be a time-consuming but effective way to identify data quality issues.
Risk Assessment and Mitigation Strategies
A critical component of any successful cutover plan is a comprehensive risk assessment and the development of corresponding mitigation strategies. Proactively identifying potential issues and outlining steps to address them is crucial for minimizing disruption and ensuring a smooth transition. This proactive approach allows for the allocation of resources and the establishment of contingency plans, thereby reducing the likelihood of significant setbacks during the cutover execution.
Potential Risks Associated with the Cutover Process
The cutover process, by its nature, involves numerous complex activities and dependencies, making it susceptible to various risks. Understanding these potential pitfalls is the first step in effective risk management. These risks can be categorized based on their origin and impact.
- Technical Failures: These encompass hardware failures, software bugs, network outages, and data corruption during the migration process. A hardware failure, for example, could lead to significant downtime if a critical server malfunctions during data transfer.
- Data Migration Issues: This category includes data loss, data integrity problems, and inconsistencies arising during the transfer of data between systems. Incomplete data migration can lead to inaccurate reporting and business disruption.
- Operational Challenges: These involve issues related to the execution of the cutover plan, such as inadequate staffing, insufficient training, or poor communication. Inadequate training of end-users on the new system can hinder its adoption and productivity.
- External Dependencies: Risks stemming from external factors, such as vendor delays, regulatory changes, or third-party service disruptions, can significantly impact the cutover timeline. A delay in receiving crucial hardware from a vendor can push back the entire project schedule.
- Security Vulnerabilities: This covers potential security breaches during the cutover, including data leaks or unauthorized access to sensitive information. Poorly configured security settings during the transition can leave systems vulnerable.
Risk Register and Mitigation Strategies
A risk register is a formalized document that details identified risks, their potential impact, and the strategies for mitigating them. This document serves as a central repository for all risk-related information, allowing for effective monitoring and management.
| Risk | Description | Severity Level (High/Medium/Low) | Probability (High/Medium/Low) | Mitigation Strategy | Contingency Plan | Owner |
|---|---|---|---|---|---|---|
| Data Loss During Migration | Data is lost or corrupted during the transfer process. | High | Medium | Implement robust data validation checks before and after migration; use data replication tools. | Restore data from backups; roll back to the previous system. | Data Migration Team |
| Network Outage | Network connectivity issues during the cutover, disrupting data transfer and system access. | High | Low | Ensure redundant network connections; test network performance thoroughly. | Use alternative network paths; postpone cutover until network stability is restored. | Network Team |
| Application Downtime | Critical applications are unavailable during or after the cutover. | High | Medium | Perform extensive application testing; schedule downtime during off-peak hours; implement rollback procedures. | Roll back to the previous application version; provide manual workarounds. | Application Support Team |
| User Training Deficiencies | Users are not adequately trained on the new system, leading to reduced productivity and increased support requests. | Medium | Medium | Provide comprehensive user training; create user guides and FAQs; establish a help desk. | Offer additional training sessions; provide temporary support staff. | Training Team |
| Vendor Delay | Delays in receiving hardware or software from vendors. | Medium | Low | Establish strong vendor relationships; maintain buffer time in the schedule; identify alternative vendors. | Adjust the cutover timeline; consider using temporary solutions. | Project Manager |
| Security Breach | Unauthorized access or data leakage during the cutover. | High | Low | Implement strong security measures; conduct security audits; encrypt sensitive data. | Contain the breach; notify relevant authorities; restore from secure backups. | Security Team |
Mitigating Common Cutover Challenges
Effective mitigation strategies often involve a combination of technical solutions, process improvements, and proactive communication. The key is to anticipate potential problems and develop plans to address them.
- Data Validation and Verification: Implement rigorous data validation checks before and after the data migration process. This ensures data integrity and completeness. Example: Before migrating customer records, verify that all mandatory fields are populated and that data formats are consistent. After migration, perform sample checks to confirm that data has been accurately transferred.
- Redundancy and Failover Mechanisms: Deploy redundant systems and failover mechanisms to minimize downtime in case of hardware or software failures. Example: Use a cluster of servers for critical applications, so if one server fails, another can automatically take over, ensuring continuous service availability.
- Comprehensive Testing: Conduct thorough testing, including unit testing, integration testing, and user acceptance testing (UAT), to identify and resolve potential issues before the cutover. Example: Simulate the cutover process in a test environment to identify potential bottlenecks and performance issues.
- Detailed Rollback Procedures: Develop and document detailed rollback procedures to revert to the previous system in case of unforeseen problems. Example: Create a step-by-step guide for restoring the previous system from backups and ensuring data consistency.
- Effective Communication: Establish clear and consistent communication channels with all stakeholders, including project teams, end-users, and management. Example: Provide regular status updates, send out alerts during critical phases of the cutover, and have a dedicated help desk to address user queries.
- User Training and Support: Provide adequate user training and support to ensure that users can effectively utilize the new system. Example: Offer online training modules, user manuals, and a help desk to assist users with questions and issues.
- Schedule Buffers: Include buffer time in the cutover schedule to accommodate unexpected delays or issues. Example: Allocate extra time for data migration and testing to provide flexibility in case of unforeseen problems.
Rollback Procedures and Contingency Planning
The success of any migration hinges not only on the successful cutover itself but also on the ability to gracefully handle failures. Rollback procedures and contingency plans are therefore critical components of the final cutover plan, providing a safety net to minimize downtime and data loss in the event of unforeseen issues. These plans ensure business continuity by enabling a swift return to the pre-migration state, or by providing alternative operational paths, should the primary migration efforts encounter obstacles.
Importance of Rollback Plans in Case of Cutover Failures
Rollback plans are essential for mitigating the risks associated with cutover failures. These plans are designed to quickly and efficiently revert to the pre-migration state, reducing the impact of errors or unforeseen complications.
- Reduced Downtime: A well-defined rollback plan minimizes the duration of system outages. The faster the rollback, the less impact on business operations. For example, in a 2018 AWS outage, the swift application of rollback procedures by many affected companies helped limit service interruptions.
- Data Integrity Preservation: Rollback procedures protect data integrity by restoring the system to a known, consistent state before any errors occurred. This prevents data corruption or loss.
- Risk Mitigation: Rollback plans act as a critical risk mitigation strategy. They provide a pre-defined pathway to recover from migration failures, reducing the uncertainty and potential damage.
- Stakeholder Confidence: Having a robust rollback plan builds confidence among stakeholders, assuring them that the migration is manageable, even in the face of challenges.
- Compliance and Regulatory Requirements: In some industries, such as finance and healthcare, rollback capabilities are often a regulatory requirement.
Detailed Rollback Procedure
A detailed rollback procedure Artikels the specific steps required to revert to the original system. This procedure should be documented thoroughly and tested rigorously before the cutover.
- Pre-Rollback Checks: Before initiating the rollback, several checks must be performed to ensure the system is in a state suitable for reversion.
- Verify Data Backups: Confirm the integrity and accessibility of pre-migration data backups. These backups are the cornerstone of the rollback process.
- Assess System State: Evaluate the current state of the migrated system. Identify any errors or issues that triggered the rollback decision.
- Document Changes: Record any changes made to the system during the migration that need to be reversed.
- Database Restoration: Restore the database to its pre-migration state using the verified backups. This step often involves restoring the entire database or specific tables.
- File System Restoration: Restore the file system, including application files, configurations, and user data, from the backups.
- Data Synchronization: If any data changes occurred after the initial backup, implement a process to reconcile these changes. This may involve data synchronization tools or manual intervention.
- Application Rollback: Roll back application deployments to their original versions. This may involve redeploying older application versions or reverting configuration files.
- Network Configuration: Reconfigure network settings, such as DNS records and routing rules, to point to the original system.
- Hardware and Software Configuration: Revert any hardware or software configurations made during the migration, such as server settings and software installations.
- Functional Testing: Test critical functionalities to ensure they are working as expected. This includes verifying user logins, data access, and core business processes.
- Performance Testing: Verify the system’s performance.
- Data Validation: Validate the integrity of the restored data by comparing it to the pre-migration state.
- Notification: Inform stakeholders about the successful rollback.
- Issue Analysis: Analyze the root cause of the migration failure to prevent similar issues in the future.
- Documentation Updates: Update the migration documentation based on the lessons learned during the rollback.
Contingency Plans for Various Failure Scenarios
Contingency plans Artikel the actions to be taken in response to specific failure scenarios. These plans should be developed to address potential problems, such as data corruption and system outages.
- Data Corruption: Data corruption can occur during data migration or after the cutover.
- Data Validation Checks: Implement data validation checks before and after the cutover to identify any inconsistencies.
- Data Repair Strategies: Develop strategies to repair corrupted data, such as restoring from backups or using data recovery tools.
- Data Loss Prevention: Employ techniques like data replication and data auditing to prevent data loss.
- System Outages: System outages can be caused by hardware failures, software bugs, or network issues.
- Redundancy and Failover Mechanisms: Implement redundancy and failover mechanisms to ensure high availability. For example, using a redundant server that automatically takes over if the primary server fails.
- Load Balancing: Use load balancing to distribute traffic across multiple servers.
- Disaster Recovery Plans: Have a comprehensive disaster recovery plan in place to restore the system in the event of a major outage. This includes backup and recovery procedures, failover strategies, and communication plans.
- Network Connectivity Issues: Network connectivity issues can disrupt access to the migrated system.
- Redundant Network Paths: Implement redundant network paths to ensure connectivity.
- Monitoring and Alerting: Set up monitoring and alerting systems to detect network issues promptly.
- Failover to Alternate Network: Plan for failover to an alternate network in case of primary network failure.
- Application Failures: Application failures can result from software bugs or compatibility issues.
- Testing and Quality Assurance: Thorough testing and quality assurance are critical before the cutover.
- Application Rollback: Have the ability to roll back to the previous application version.
- Patching and Updates: Implement a process for patching and updating applications to address issues.
Communication Plan and Stakeholder Management

Effective communication and proactive stakeholder management are critical to a successful cutover. A well-defined communication plan ensures all stakeholders are informed of progress, potential issues, and mitigation strategies, fostering trust and minimizing disruption. This section Artikels a comprehensive communication strategy, a stakeholder update template, and best practices for managing expectations during the migration phase.
Communication Plan During the Cutover Phase
The communication plan should be a dynamic document, regularly updated to reflect the current status of the cutover. It details the “who,” “what,” “when,” “where,” and “how” of communication.
- Target Audience Segmentation: The plan must identify and segment stakeholders based on their level of involvement and information needs. This includes executive leadership, project teams, end-users, IT support staff, and external vendors. Each group receives tailored communication.
- Communication Channels: Establish preferred communication channels for different types of information. These include:
- Email: For formal updates, announcements, and distribution of the stakeholder update template.
- Project Management Software (e.g., Jira, Asana): For tracking tasks, issues, and providing real-time updates to the project team.
- Instant Messaging (e.g., Slack, Microsoft Teams): For quick communication and resolving immediate issues within the project team.
- Dedicated Website or Intranet Page: A central repository for documentation, FAQs, and cutover status updates accessible to all stakeholders.
- Regular Meetings: Formal meetings for project teams and steering committees to review progress, discuss issues, and make decisions.
- Communication Frequency and Timing: Determine the frequency of communication based on the cutover phase. During critical phases, increase the frequency to hourly or even real-time updates. Regular updates should occur at least daily, and possibly more frequently.
- Content and Messaging: Define the content of each communication type. Ensure messages are clear, concise, and avoid technical jargon where possible, especially for non-technical stakeholders. Content includes:
- Cutover progress against the plan.
- Issues encountered and their resolution status.
- Key decisions made.
- Any changes to the cutover schedule.
- Instructions for end-users, if applicable.
- Roles and Responsibilities: Clearly define who is responsible for creating, distributing, and receiving communications. This includes the project manager, communication lead, and technical leads.
- Escalation Procedures: Establish a clear escalation path for critical issues. This includes who to contact and the expected response times.
- Feedback Mechanisms: Implement methods for stakeholders to provide feedback and ask questions. This may include dedicated email addresses, surveys, or feedback forms on the intranet page.
Template for Stakeholder Communication Updates
A standardized template ensures consistent messaging and provides a framework for updates. The template should be concise and easily understood, providing the most important information.
Template Components:
| Section | Description | Example |
|---|---|---|
| Subject Line | Concise summary of the update and date. | “Cutover Update – Day 3 – June 20, 2024” |
| Executive Summary | Brief overview of the cutover status. | “Cutover is proceeding as planned. Data migration is 95% complete.” |
| Progress Update | Detailed breakdown of activities completed, in progress, and planned. | “Database migration completed. Application deployment is underway.” |
| Issues and Risks | Identification of any issues encountered and the actions taken to resolve them. | “Minor performance issues observed during testing. Resolution is in progress.” |
| Next Steps | Artikel of activities planned for the next reporting period. | “Finalize application deployment. Begin user acceptance testing.” |
| Key Decisions | Summary of decisions made and their impact. | “Approved extension of the cutover window by 2 hours to accommodate data validation.” |
| Contact Information | Contact details for questions and support. | “Contact the Project Manager at [email protected]” |
Best Practices for Managing Stakeholder Expectations
Proactive expectation management is crucial for maintaining stakeholder confidence and preventing misunderstandings. This involves setting realistic expectations, providing timely updates, and being transparent about potential risks.
- Set Realistic Expectations: During the planning phase, involve stakeholders in defining timelines and success criteria. Avoid overpromising.
- Be Transparent: Communicate both successes and challenges honestly and openly. This builds trust.
- Provide Timely Updates: Adhere to the communication plan and provide updates at the agreed-upon frequency.
- Proactively Address Concerns: Anticipate potential concerns and address them in advance. This demonstrates a proactive approach to risk management. For example, if a potential outage is expected, clearly communicate the duration and impact.
- Manage Escalations Effectively: Ensure a clear escalation path for critical issues and respond to escalations promptly.
- Listen and Respond to Feedback: Actively solicit and respond to stakeholder feedback. Use feedback to improve the cutover process and communication.
- Document Decisions: Maintain a clear record of all decisions made and the rationale behind them. This provides a reference point for future discussions and ensures everyone is aligned.
- Celebrate Successes: Acknowledge and celebrate milestones and successes to maintain morale and build momentum.
- Use Visual Aids: Incorporate visual aids, such as dashboards and charts, to present data and progress updates in a clear and easily understandable format. These visualizations can help stakeholders quickly grasp the current status and key metrics.
- Training and User Guides: Provide comprehensive training materials and user guides before and during the cutover. This empowers users and reduces the number of support requests. Include FAQs and troubleshooting steps to address common issues.
Post-Cutover Activities and Support
Following the successful execution of a final cutover, a structured approach to post-cutover activities and support is crucial to ensure system stability, user adoption, and the overall success of the migration. These activities focus on validating the migrated environment, providing ongoing support, and continuously improving system performance.
Post-Cutover Tasks for Smooth Transition
The post-cutover phase involves several critical tasks designed to validate the migration and stabilize the new environment. These tasks are executed in a phased approach, prioritizing critical functions and user impact.
- Verification of System Functionality: Immediately after the cutover, comprehensive testing is performed to verify that all core system functionalities are operating as expected. This includes testing critical business processes, data integrity checks, and ensuring that integrations with other systems are functioning correctly. For example, in a financial system migration, this involves validating transaction processing, reporting capabilities, and compliance with regulatory requirements.
- Data Validation and Reconciliation: A thorough reconciliation of data between the source and target systems is performed to confirm data integrity. This involves comparing data volumes, verifying data accuracy, and identifying and resolving any discrepancies. Automated data validation tools and scripts are employed to streamline this process and ensure data consistency.
- Performance Tuning and Optimization: The new system’s performance is monitored and optimized to ensure it meets the required performance benchmarks. This involves analyzing system resource utilization, identifying performance bottlenecks, and implementing necessary optimizations, such as database tuning, code optimization, and infrastructure adjustments.
- User Acceptance Testing (UAT): A period of UAT is initiated, allowing end-users to test the new system and provide feedback. This involves providing users with access to the new system and guiding them through various scenarios to validate that the system meets their requirements. Any issues or concerns raised by users are documented and addressed promptly.
- Knowledge Transfer and Documentation: Comprehensive documentation and knowledge transfer are essential for long-term system maintenance and support. This includes updating system documentation, providing training materials, and ensuring that support teams have the necessary knowledge to resolve issues effectively.
Support Mechanisms Required After Cutover
Robust support mechanisms are essential to address user inquiries, resolve issues, and ensure a positive user experience after the cutover. These mechanisms should be readily accessible and provide timely and effective support.
- Help Desk and Support Channels: A dedicated help desk or support center is established to provide users with a single point of contact for assistance. This includes providing multiple support channels, such as phone, email, and online chat, to cater to different user preferences.
- Incident Management and Resolution: A structured incident management process is implemented to track, prioritize, and resolve system issues. This includes defining service level agreements (SLAs) for response and resolution times, and providing regular updates to users on the status of their issues.
- User Training and Documentation: Ongoing user training and access to comprehensive documentation are provided to empower users to effectively utilize the new system. This includes offering training sessions, creating user guides, and providing online resources.
- Change Management and Communication: A change management process is established to manage system changes and communicate these changes to users. This includes notifying users of upcoming changes, providing training on new features, and soliciting feedback on the changes.
- Vendor Support and Escalation: Relationships with vendors are maintained to provide access to vendor support resources, and establishing escalation paths to address critical issues.
Monitoring System Performance and Addressing Issues
Continuous monitoring of system performance is critical to proactively identify and address any issues that may arise. This includes monitoring key performance indicators (KPIs), analyzing system logs, and implementing proactive measures to prevent problems.
- Performance Monitoring Tools: Specialized tools are employed to monitor system performance, including monitoring CPU utilization, memory usage, disk I/O, network traffic, and database performance. These tools provide real-time insights into system performance and allow for proactive issue detection.
- Log Analysis and Issue Detection: System logs are regularly analyzed to identify potential issues, such as errors, warnings, and performance bottlenecks. Log analysis tools are used to automate this process and identify patterns and anomalies.
- Performance Reporting and Analysis: Performance reports are generated regularly to track system performance trends and identify areas for improvement. This includes analyzing historical data, identifying performance degradation, and recommending optimizations.
- Issue Resolution and Remediation: A structured process is implemented to resolve system issues. This includes diagnosing the root cause of the issue, implementing a fix, and testing the fix to ensure that the issue is resolved.
- Proactive Problem Management: Proactive measures are implemented to prevent future issues. This includes identifying and addressing recurring issues, implementing preventative maintenance, and proactively monitoring system health.
Tools and Technologies for Cutover Planning
Effective cutover planning necessitates the strategic utilization of various tools and technologies. These resources streamline processes, enhance efficiency, and mitigate risks associated with the migration. The selection of appropriate tools is crucial for a successful transition, as they directly impact the execution, monitoring, and validation phases of the cutover.
Data Migration Tools
Data migration tools facilitate the transfer of data from the source system to the target system. They often provide features such as data extraction, transformation, and loading (ETL), data validation, and data reconciliation. The choice of a data migration tool depends on factors such as the volume of data, the complexity of the data structures, and the specific requirements of the migration project.
- ETL Tools: These tools are designed to extract data from various sources, transform it into a format suitable for the target system, and load it into the target database. Examples include Informatica PowerCenter, Talend, and AWS Glue.
- Database Replication Tools: These tools replicate data in real-time or near real-time, minimizing downtime during the cutover. Examples include Oracle GoldenGate, Microsoft SQL Server Replication, and AWS Database Migration Service (DMS).
- Data Validation Tools: These tools verify the accuracy and completeness of the migrated data. They perform data quality checks and ensure data integrity. Examples include data quality modules within ETL tools and specialized data validation software.
System Monitoring Tools
System monitoring tools provide real-time visibility into the performance of both the source and target systems during the cutover. They track key metrics such as CPU utilization, memory usage, network traffic, and application response times. These tools are essential for identifying and resolving performance bottlenecks, ensuring a smooth transition, and maintaining service levels.
- Application Performance Monitoring (APM) Tools: These tools monitor the performance of applications and identify performance issues. Examples include Dynatrace, New Relic, and AppDynamics.
- Infrastructure Monitoring Tools: These tools monitor the underlying infrastructure, including servers, networks, and storage. Examples include SolarWinds, Nagios, and Prometheus.
- Log Management Tools: These tools collect, analyze, and visualize log data from various sources. Examples include Splunk, ELK Stack (Elasticsearch, Logstash, Kibana), and Sumo Logic.
Automation Tools
Automation tools streamline cutover tasks, reduce manual effort, and minimize the risk of human error. They can automate tasks such as data backup and restoration, system configuration, and script execution. Automation tools are critical for achieving efficiency and ensuring the consistency of the cutover process.
- Configuration Management Tools: These tools automate the configuration of systems and applications. Examples include Ansible, Chef, and Puppet.
- Scripting Languages: Scripting languages such as Python, PowerShell, and Bash are used to automate various tasks.
- Workflow Automation Tools: These tools automate the execution of complex workflows. Examples include Jenkins, Azure DevOps, and AWS Step Functions.
Comparative Table of Cutover Tools
The following table provides a comparative analysis of various cutover tools, highlighting their key features, pros, and cons. This information aids in the selection of the most appropriate tools for a specific migration project.
| Tool Name | Features | Pros | Cons |
|---|---|---|---|
| Informatica PowerCenter (ETL) | Data extraction, transformation, and loading; data quality; metadata management; workflow orchestration. | Robust ETL capabilities; large community support; extensive connectivity options. | Complex to implement and manage; can be expensive; requires specialized skills. |
| Oracle GoldenGate (Replication) | Real-time data replication; high availability; data transformation; support for various databases. | Minimal downtime; supports heterogeneous environments; strong data consistency. | Can be complex to configure; requires specialized expertise; licensing costs can be high. |
| Dynatrace (APM) | Real-time monitoring; AI-powered analysis; automatic dependency mapping; user experience monitoring. | Easy to use; provides deep insights into application performance; automated problem detection. | Can be expensive; requires a good understanding of application architecture; may require tuning. |
| Ansible (Configuration Management) | Agentless automation; idempotent operations; task automation; configuration management. | Easy to learn and use; open-source; supports a wide range of platforms; highly scalable. | Limited GUI; can be challenging to manage complex configurations; requires knowledge of YAML. |
Last Recap
In conclusion, a final cutover plan is the linchpin of a successful data migration. It demands meticulous planning, proactive risk management, and a clear understanding of the entire process. By carefully considering pre-cutover activities, executing the cutover with precision, validating data integrity, and establishing robust rollback procedures, organizations can minimize disruptions and ensure a seamless transition. The integration of a well-defined communication strategy and the provision of comprehensive post-cutover support are equally vital.
Embracing these principles is key to achieving a smooth and effective data migration, paving the way for improved system performance and enhanced operational efficiency.
Essential FAQs
What is the primary goal of a final cutover plan?
The primary goal is to minimize downtime and data loss while ensuring a smooth and successful transition from the old system to the new system during a data migration.
What are the key differences between a final cutover plan and a migration plan?
A migration plan is a high-level document outlining the overall strategy and scope of the migration project. A final cutover plan is a detailed, step-by-step guide specifically focused on the execution of the transition from the old system to the new system.
How important is a rollback plan?
A rollback plan is crucial. It provides a detailed procedure to revert to the original system in case of unforeseen issues during the cutover, minimizing potential damage and ensuring business continuity.
What are the critical elements of a communication plan during cutover?
The communication plan should Artikel the stakeholders, frequency, and methods of communication. It should include updates on progress, potential issues, and any actions required from stakeholders.
How can data be validated after the cutover?
Data validation involves comparing data between the old and new systems, checking for completeness, accuracy, and consistency. This can be achieved through data comparison tools, reconciliation reports, and user acceptance testing.