What is a disaster recovery plan for the new cloud environment is a critical consideration for any organization leveraging cloud services. In an era where data is the lifeblood of business operations, the ability to swiftly recover from unforeseen events, ranging from natural disasters to cyberattacks, is paramount. This document delves into the intricacies of cloud-based disaster recovery, providing a structured approach to understanding, planning, and implementing effective strategies to ensure business continuity.
This exploration will cover the fundamental aspects of disaster recovery in the cloud, including defining core objectives, identifying potential threats, and outlining essential components. We will analyze various recovery strategies, comparing their strengths and weaknesses, and emphasizing the importance of aligning these strategies with specific Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO). Furthermore, the discussion will encompass practical procedures for data backup, recovery, and integration with broader business continuity plans, all while addressing critical considerations such as security, compliance, and cost optimization.
Understanding Disaster Recovery in the Cloud

A disaster recovery (DR) plan in the cloud is a comprehensive strategy designed to restore cloud-based infrastructure, applications, and data after a disruptive event. It Artikels the steps an organization will take to minimize downtime and data loss, ensuring business continuity. This is particularly critical given the shared responsibility model inherent in cloud computing, where both the cloud provider and the customer share responsibilities for security and resilience.
A well-defined DR plan is not merely a technical document; it’s a business imperative, safeguarding an organization’s operational capabilities and reputation.
Definition of a Cloud Disaster Recovery Plan
A cloud disaster recovery plan is a documented set of procedures and policies that enable an organization to recover its IT infrastructure and data in the cloud after a disaster. It defines the roles, responsibilities, and technical processes required to maintain or quickly restore business operations. The plan encompasses data backup and recovery, application failover, and infrastructure replication strategies, all tailored for the specific cloud environment and the organization’s Recovery Time Objective (RTO) and Recovery Point Objective (RPO).
Core Objectives of a Disaster Recovery Plan
The primary goals of a disaster recovery plan are multifaceted, focusing on both immediate response and long-term resilience.
- Minimize Downtime: The overarching objective is to reduce the period during which critical business functions are unavailable. This is achieved through rapid restoration of services.
- Data Protection: Ensuring the integrity and availability of data is paramount. This involves regular backups, data replication, and the ability to restore data to a usable state.
- Business Continuity: The plan aims to maintain business operations, or rapidly resume them, even in the face of significant disruptions. This includes restoring critical applications and systems.
- Compliance and Regulatory Adherence: Many industries are subject to regulations requiring specific data protection and recovery strategies. The DR plan helps organizations meet these compliance requirements.
- Cost Optimization: While DR involves costs, a well-designed plan can help to optimize these costs by leveraging cloud-native features, automating processes, and selecting appropriate recovery strategies based on business needs.
Common Types of Disasters Affecting Cloud Systems
Cloud environments, while inherently resilient, are susceptible to various types of disasters. Understanding these threats is crucial for designing an effective DR plan.
- Natural Disasters: Events such as hurricanes, earthquakes, floods, and wildfires can physically damage data centers, leading to service outages and data loss.
- Human Error: Mistakes made by IT staff, such as accidental deletion of data or misconfigurations, can result in significant disruptions.
- Cyberattacks: Malware, ransomware, and distributed denial-of-service (DDoS) attacks can compromise systems, encrypt data, and disrupt service availability. For instance, a successful ransomware attack can render data inaccessible, requiring a complete system restore from backups.
- Hardware Failures: Server, storage, and network equipment can fail, leading to service interruptions. The scale of such failures can range from individual component malfunctions to widespread outages.
- Software Bugs: Errors in applications or operating systems can cause system crashes and data corruption. The impact can vary depending on the severity of the bug and the affected systems.
- Power Outages: Disruptions to the power supply, either due to local failures or broader grid issues, can shut down data centers. Backup power systems, such as generators, are crucial for mitigating this risk.
- Network Outages: Connectivity problems, either internal to the cloud provider’s network or external to it, can prevent users from accessing services.
- Cloud Provider Outages: Although rare, outages at the cloud provider level can occur, affecting all customers using that provider’s services within the affected region or availability zone.
Key Components of a Cloud Disaster Recovery Plan
A robust cloud disaster recovery (DR) plan is crucial for maintaining business continuity in the face of unforeseen events. It provides a structured approach to minimizing downtime and data loss, ensuring that critical business functions can resume operations as quickly as possible. This section details the essential elements of a comprehensive cloud DR plan, outlining key components and their significance.
Data Backup and Recovery Strategies
Data backup and recovery are fundamental to any disaster recovery plan. The strategies employed directly impact the Recovery Point Objective (RPO) and Recovery Time Objective (RTO). Implementing these strategies requires careful consideration of data sensitivity, frequency of changes, and the acceptable levels of data loss and downtime.
- Backup Frequency and Retention Policies: Establishing a backup schedule and retention policy is paramount. The frequency of backups should align with the RPO, determining how often data needs to be backed up to minimize potential data loss. Retention policies define how long backup data is stored, balancing the need for historical data with storage costs. For example, a financial institution might require hourly backups with a 30-day retention period for transaction data, while less critical data might be backed up daily and retained for a shorter duration.
- Backup Types: Different backup types offer varying levels of data protection and recovery speed. Full backups create a complete copy of all data, offering the simplest recovery process but requiring the most time. Incremental backups only copy data that has changed since the last backup, reducing backup time but potentially increasing recovery time as multiple backup sets may be needed. Differential backups copy data that has changed since the last full backup, offering a balance between backup and recovery speed.
Choosing the right backup type or a combination of types is crucial for optimizing the DR plan.
- Backup Location and Storage: Backups should be stored in geographically diverse locations to protect against regional disasters. Cloud providers often offer multiple availability zones or regions, allowing for the replication of backup data across different physical locations. Consider the storage type (e.g., object storage, block storage, tape) and its associated costs, performance characteristics, and durability. For example, a company might store critical application data in a hot storage tier for rapid recovery and less critical data in a cold storage tier for cost-effectiveness.
- Recovery Procedures: Documenting detailed recovery procedures is essential. These procedures should Artikel the step-by-step process for restoring data and applications from backups. The procedures should include instructions for verifying backup integrity, restoring data to the primary or secondary site, and testing the restored systems to ensure functionality. Regular testing of these procedures is vital to validate their effectiveness and identify any potential issues.
Roles and Responsibilities within a Disaster Recovery Team
A well-defined disaster recovery team, with clearly assigned roles and responsibilities, is essential for a coordinated and effective response. This team ensures that the DR plan is executed efficiently and that all necessary actions are taken to minimize downtime and data loss. The following table Artikels typical roles and responsibilities within a cloud DR team.
| Role | Responsibilities | Skills and Expertise | Contact Information |
|---|---|---|---|
| Disaster Recovery Manager | Overall responsibility for the DR plan, including development, maintenance, testing, and execution. Coordinates the DR team and serves as the primary point of contact. | Project management, cloud technologies, business continuity planning, communication, leadership. | Email, Phone, Emergency Contact System |
| IT Infrastructure Lead | Responsible for the recovery of IT infrastructure components, including servers, storage, and networking. Manages the failover and failback processes. | Cloud infrastructure, virtualization, networking, storage systems, operating systems. | Email, Phone, Monitoring System Alerts |
| Application Lead | Responsible for the recovery of specific applications. Ensures application data consistency and functionality after recovery. Coordinates with IT infrastructure lead. | Application architecture, database administration, scripting, cloud application platforms. | Email, Phone, Application Monitoring Tools |
| Data Security and Compliance Officer | Ensures data security and compliance requirements are met during the recovery process. Manages data encryption, access controls, and compliance audits. | Data security, compliance regulations (e.g., GDPR, HIPAA), risk management, auditing. | Email, Phone, Security Incident Response System |
Testing and Validation
Regular testing and validation are critical to ensure the effectiveness of the disaster recovery plan. Testing helps identify weaknesses, validate recovery procedures, and familiarize the DR team with the recovery process. The frequency and type of testing should be determined based on the criticality of the systems and the rate of change within the environment.
- Testing Frequency and Types: Conduct regular testing, ranging from simple drills to full-scale failover exercises. The frequency of testing should be determined by factors such as the criticality of the applications, the rate of change within the environment, and the risk tolerance of the organization. Testing types can include tabletop exercises (simulated scenarios), failover simulations (testing the failover process without disrupting production), and full-scale recovery tests (simulating a complete disaster recovery).
- Test Plan Development: Develop a detailed test plan that Artikels the scope, objectives, procedures, and success criteria for each test. The plan should include specific steps for initiating the test, monitoring the recovery process, and validating the restored systems. It should also document the roles and responsibilities of the team members involved in the test.
- Test Execution and Monitoring: Execute the test plan meticulously, documenting all actions taken and any issues encountered. Monitor the recovery process closely, tracking key metrics such as recovery time, data loss, and system performance. Document any deviations from the plan and analyze the root causes.
- Results Analysis and Reporting: Analyze the test results to identify areas for improvement in the DR plan. Prepare a detailed report that summarizes the test findings, including any issues encountered, recommendations for remediation, and the overall effectiveness of the plan. Use the report to update the DR plan and improve the recovery procedures.
Communication and Notification
Effective communication is essential during a disaster. A well-defined communication plan ensures that all stakeholders are informed of the situation, the recovery progress, and any critical updates. This plan should include notification procedures, contact lists, and escalation paths.
- Notification Procedures: Establish clear procedures for notifying relevant stakeholders, including employees, customers, partners, and regulatory bodies. Define the communication channels to be used (e.g., email, phone, SMS, social media) and the content of the notifications. Ensure that contact information is up-to-date and readily available.
- Contact Lists and Escalation Paths: Maintain comprehensive contact lists for all key personnel, including the DR team, executive management, IT staff, and external vendors. Define escalation paths to ensure that critical issues are addressed promptly. The escalation path should Artikel the order in which individuals or teams should be contacted and the timeframe for escalation.
- Communication Tools and Platforms: Utilize communication tools and platforms that are reliable and accessible during a disaster. This may include redundant email systems, SMS messaging services, and dedicated communication platforms. Ensure that these tools are tested regularly and that all team members are familiar with their use.
- Public Relations and Media Management: Develop a plan for managing communications with the public and the media. This plan should include pre-approved statements, media contact information, and procedures for handling media inquiries. Coordinate all communications with the public and the media to maintain a consistent message and protect the organization’s reputation.
Security and Compliance
Integrating security and compliance into the disaster recovery plan is crucial for protecting sensitive data and meeting regulatory requirements. The DR plan should address data encryption, access controls, and compliance audits.
- Data Encryption and Access Controls: Implement robust data encryption both in transit and at rest to protect sensitive data from unauthorized access. Establish strict access controls to limit access to data and systems based on the principle of least privilege. Regularly review and update access controls to ensure that they remain effective.
- Compliance Requirements: Ensure that the DR plan complies with all relevant regulatory requirements, such as GDPR, HIPAA, and PCI DSS. This includes data residency requirements, data privacy regulations, and security standards. Conduct regular audits to verify compliance and address any identified gaps.
- Security Audits and Assessments: Conduct regular security audits and assessments to identify vulnerabilities and assess the effectiveness of security controls. Use the results of these audits to improve the DR plan and strengthen security posture. Implement penetration testing and vulnerability scanning to identify and address potential security weaknesses.
- Incident Response Planning: Integrate incident response procedures into the DR plan. This includes procedures for detecting, responding to, and recovering from security incidents. Define roles and responsibilities for incident response and ensure that the team is trained on incident handling procedures.
Selecting Cloud Disaster Recovery Strategies
Choosing the right cloud disaster recovery (DR) strategy is a critical decision, directly impacting an organization’s ability to maintain business continuity during disruptive events. The selection process involves a careful evaluation of Recovery Time Objective (RTO) and Recovery Point Objective (RPO) requirements, along with a cost-benefit analysis of various approaches. The following sections compare and contrast common cloud DR strategies, providing insights into their advantages and disadvantages to aid in informed decision-making.
Backup and Restore Strategy
The backup and restore strategy represents the most basic form of cloud DR. It involves regularly backing up data and applications to a separate location, either within the same cloud provider or to a different provider. In the event of a disaster, the data and applications are restored from the backup.
- Pros: This strategy is generally the least expensive to implement and maintain. It is relatively simple to understand and manage, making it suitable for organizations with limited technical resources or budget constraints.
- Cons: Backup and restore typically has the longest RTO and RPO. Restoring a large dataset can take considerable time, potentially leading to significant downtime. The effectiveness of this strategy heavily relies on the integrity of the backups and the efficiency of the restoration process.
- RTO/RPO Considerations: Backup and restore is best suited for applications with high tolerance for downtime and data loss. Organizations should accept a RTO measured in hours or days, and an RPO that might also be in hours or even a day. For example, a small business might use this strategy to protect non-critical data, accepting the risk of several hours of downtime.
Pilot Light Strategy
The pilot light strategy involves maintaining a minimal version of the production environment in the cloud, ready to be scaled up in case of a disaster. This typically includes core components such as databases and essential services. These components are kept running, but in a scaled-down state.
- Pros: Pilot light offers a faster RTO than backup and restore, as the core infrastructure is already provisioned. It provides a good balance between cost and recovery speed.
- Cons: While faster than backup and restore, the RTO is still dependent on the time required to scale up the infrastructure and restore the remaining data. It’s more complex to manage than backup and restore, requiring expertise in both infrastructure and application scaling.
- RTO/RPO Considerations: This strategy is appropriate for applications with moderate tolerance for downtime and data loss. RTOs can range from hours to a few hours, and RPOs from minutes to a few hours, depending on the complexity of the scaling and restoration processes. A good example is an e-commerce platform that can tolerate a few hours of downtime, where critical customer data is continuously backed up.
Warm Standby Strategy
The warm standby strategy involves maintaining a scaled-down, but fully functional, version of the production environment in the cloud. The standby environment is kept synchronized with the production environment, typically using techniques such as database replication.
- Pros: Warm standby offers a significantly faster RTO than pilot light, as the infrastructure is already provisioned and running. It reduces the complexity of scaling during a disaster.
- Cons: This strategy is more expensive than pilot light due to the cost of maintaining the standby environment. It requires continuous synchronization, which can introduce overhead and complexity.
- RTO/RPO Considerations: This strategy is suitable for applications that require relatively low downtime and data loss. RTOs are typically measured in minutes or hours, and RPOs are often in minutes. For instance, a financial institution might use warm standby for its core banking systems, which require rapid recovery in case of a failure.
Multi-Site Strategy
The multi-site strategy, also known as active-active or active-passive with automated failover, involves running the production environment across multiple cloud regions or data centers. Traffic is typically routed to the primary site, and in case of a disaster, traffic automatically fails over to the secondary site.
- Pros: Multi-site provides the fastest RTO and RPO, often near-zero. It offers the highest level of availability and business continuity.
- Cons: This strategy is the most expensive, requiring the provisioning and operation of multiple environments. It’s also the most complex to implement and manage, demanding advanced technical expertise and robust automation.
- RTO/RPO Considerations: This is ideal for mission-critical applications that require minimal downtime and data loss. RTOs and RPOs are typically near-zero, or a few minutes at most. A good example is a global online retailer that cannot afford any significant downtime, relying on active-active deployments across multiple regions.
Choosing the Appropriate Strategy Based on RTO and RPO
The selection of the appropriate cloud DR strategy is primarily driven by the RTO and RPO requirements of the business. These objectives dictate the acceptable amount of downtime (RTO) and data loss (RPO) in the event of a disaster.
The table below illustrates the relationship between RTO/RPO and the recommended DR strategy:
| RTO | RPO | Recommended Strategy | Example Application |
|---|---|---|---|
| Hours to Days | Hours to Days | Backup and Restore | Non-critical applications, development/testing environments |
| Hours | Minutes to Hours | Pilot Light | E-commerce platforms, internal business applications |
| Minutes to Hours | Minutes | Warm Standby | Core business applications, financial systems |
| Near-Zero | Near-Zero | Multi-Site | Mission-critical applications, high-availability systems |
It is crucial to analyze the criticality of each application and its associated data. This involves determining the business impact of downtime and data loss. This assessment should include understanding the costs associated with each strategy, and the technical resources available for implementation and management. A comprehensive cost-benefit analysis is therefore critical for making an informed decision about the most suitable cloud disaster recovery strategy.
Data Backup and Recovery Procedures
Data backup and recovery are critical components of any robust disaster recovery plan, ensuring business continuity in the face of data loss or system failure. Effective procedures minimize downtime and data loss, protecting an organization’s valuable information assets. This section details the procedures for data backup and recovery within a cloud environment, focusing on the strategies and best practices necessary for success.
Procedures for Data Backup in a Cloud Environment
Cloud environments offer various methods for data backup, each with its advantages and disadvantages depending on the specific needs of the organization. These methods must be carefully selected and implemented to provide adequate data protection.Data backup in the cloud typically involves these key steps:
- Data Selection: Identifying the data to be backed up. This involves determining the scope of the backup, which could include entire virtual machines (VMs), specific databases, application data, or individual files. The selection process should consider the criticality of the data, its rate of change, and the recovery time objectives (RTO) and recovery point objectives (RPO) of the organization.
- Backup Method Selection: Choosing the appropriate backup method. Common methods include:
- Full Backup: Backing up all selected data. This is the most comprehensive but also the most time-consuming method.
- Incremental Backup: Backing up only the data that has changed since the last backup (full or incremental). This is faster than a full backup but requires a chain of backups for recovery.
- Differential Backup: Backing up only the data that has changed since the last full backup. This is faster than a full backup but slower than incremental backups.
- Backup Storage Location: Selecting a suitable storage location for backups. This could be within the same cloud provider, a different cloud provider, or an on-premises location. The choice depends on factors such as cost, performance, geographic redundancy, and compliance requirements. Consider the “3-2-1 backup rule”: 3 copies of your data, on 2 different media, with 1 copy offsite.
- Backup Scheduling and Automation: Automating the backup process using tools provided by the cloud provider or third-party solutions. Scheduling should be based on the RPO, ensuring that backups occur frequently enough to meet the data loss tolerance. Automation minimizes human error and ensures consistency.
- Encryption and Security: Implementing encryption to protect data at rest and in transit. This is critical for safeguarding sensitive information. Access controls and security measures should be in place to prevent unauthorized access to backup data.
- Backup Verification and Validation: Regularly testing backups to ensure their integrity and recoverability. This involves restoring data from backups to a test environment to verify that the data is intact and that the recovery process functions correctly.
Process of Data Recovery from Backups
Data recovery is the process of restoring data from backups to a functional state after data loss or system failure. The recovery process is crucial for minimizing downtime and restoring business operations.The data recovery process generally includes these steps:
- Identify the Data Loss: Determining the scope of the data loss, the affected systems, and the root cause of the issue. This helps in defining the recovery scope and selecting the appropriate backups.
- Locate the Backup: Identifying the backup containing the required data. This requires knowing the backup method used (full, incremental, differential) and the backup schedule.
- Select the Recovery Point: Determining the point in time to which the data should be restored. This is based on the RPO, the point in time before the data loss occurred.
- Initiate the Recovery Process: Using the cloud provider’s tools or third-party solutions to initiate the recovery process. This might involve restoring a virtual machine, database, or individual files.
- Data Restoration: Restoring the data to the original location or a new location. This could involve restoring the entire system or just the specific files or databases.
- Testing and Verification: After the data is restored, testing and verifying that the data is intact, the systems are functional, and business operations can resume. This includes validating data integrity and application functionality.
- Failback (if applicable): If the recovery was performed on a secondary site or a different environment, failback involves returning the recovered data and applications to the primary production environment once it is operational.
Best Practices for Data Backup Frequency and Retention Policies
Establishing appropriate backup frequency and retention policies is critical for ensuring data protection and meeting RTO and RPO objectives. These policies must be aligned with the organization’s business requirements, compliance regulations, and risk tolerance.Here are some best practices for data backup frequency and retention policies:
- Data Classification: Classifying data based on its criticality, sensitivity, and regulatory requirements. This helps in determining the appropriate backup frequency and retention period for each data category.
- Recovery Time Objective (RTO) and Recovery Point Objective (RPO): Defining RTO and RPO based on business requirements.
RTO is the maximum acceptable downtime after a disaster. RPO is the maximum acceptable data loss.
These objectives dictate the backup frequency and retention policies.
- Backup Frequency:
- High-Criticality Data: Backups should be performed frequently, potentially every few hours or even continuously.
- Medium-Criticality Data: Backups can be performed daily or weekly.
- Low-Criticality Data: Backups can be performed weekly or monthly.
- Retention Policies:
- Short-Term Retention: For frequently accessed data, retain backups for a short period (e.g., a few days or weeks) to facilitate quick recovery from minor incidents.
- Long-Term Retention: For data that needs to be archived or retained for compliance reasons, retain backups for an extended period (e.g., months or years).
- Automation: Automating the backup process, including backup scheduling and retention management, to ensure consistency and reduce the risk of human error.
- Regular Testing: Regularly testing backups to ensure that the data can be recovered successfully and that the RTO and RPO can be met.
- Documentation: Maintaining detailed documentation of backup procedures, retention policies, and recovery processes. This documentation should be updated regularly.
- Compliance: Adhering to relevant industry regulations and compliance requirements (e.g., GDPR, HIPAA) when defining backup and retention policies.
Business Continuity Planning and Cloud Integration
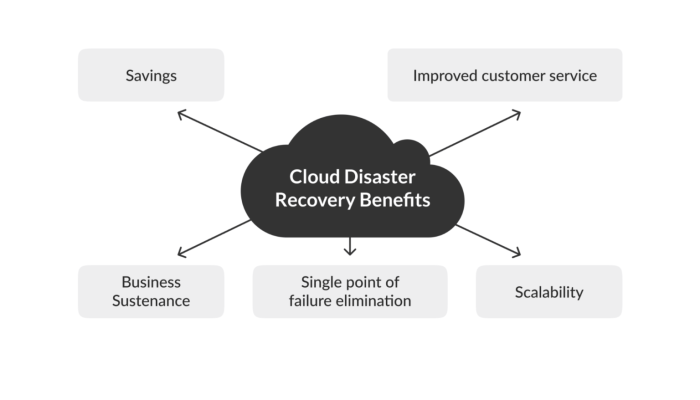
Business Continuity Planning (BCP) and cloud Disaster Recovery (DR) are intrinsically linked, forming a comprehensive strategy to ensure business operations can withstand disruptions. While DR focuses on restoring IT systems and data after an event, BCP encompasses a broader scope, outlining the steps necessary to maintain critical business functions during and after a disruption. Effective cloud integration enhances both BCP and DR capabilities, leveraging the cloud’s inherent flexibility, scalability, and geographic distribution to improve resilience.
Business Continuity Planning Integration with Cloud Disaster Recovery
The integration of BCP and cloud DR involves aligning recovery strategies with business objectives and critical processes. This integration ensures that DR plans support the overarching BCP goals of minimizing downtime, protecting revenue streams, and maintaining customer satisfaction. Cloud DR solutions are selected and configured to support the specific recovery requirements identified within the BCP.
- Alignment of Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs): BCP defines the acceptable downtime (RTO) and data loss (RPO) for critical business functions. Cloud DR strategies, such as backup and restore, failover, and replication, are then chosen to meet these objectives. For example, a high-priority application might require an RTO of minutes and an RPO of seconds, necessitating a real-time replication strategy in the cloud.
- Prioritization of Business Processes: BCP identifies and prioritizes business processes based on their criticality to the organization. This prioritization informs the DR plan, ensuring that the most critical processes are recovered first. Cloud DR solutions often support process prioritization through features like automated failover and orchestrated recovery sequences.
- Integration of Communication and Notification Procedures: BCP includes communication plans to inform stakeholders during a disruption. Cloud DR plans integrate these procedures by providing mechanisms for notifying relevant personnel about system failures, recovery progress, and restoration completion.
- Regular Testing and Validation: Both BCP and DR plans must be regularly tested and validated to ensure their effectiveness. Cloud-based DR solutions often facilitate testing through non-disruptive failover simulations and recovery drills, allowing organizations to assess their readiness without impacting production systems.
Business Continuity Scenarios and Corresponding Recovery Plans
Various business continuity scenarios require tailored recovery plans. These plans leverage cloud-based DR capabilities to mitigate the impact of disruptions, ensuring business operations can continue with minimal interruption.
- Scenario: Data Center Outage
- Description: A physical data center housing critical IT infrastructure experiences a power failure, natural disaster, or other catastrophic event, rendering the systems unavailable.
- Recovery Plan:
- Cloud-Based Replication: Automatically failover to a cloud-based replica of the affected systems. This ensures that the business continues operating in the cloud environment with minimal downtime.
- Data Restoration: Restore data from cloud-based backups to a cloud environment if a full replication is not implemented. This method requires a longer recovery time but minimizes data loss.
- Process:
- Activate the failover plan.
- Verify data integrity in the cloud environment.
- Notify stakeholders of the outage and recovery progress.
- Transition business operations to the cloud.
- Scenario: Cyberattack and Ransomware Infection
- Description: A ransomware attack encrypts critical data and systems, rendering them inaccessible. The organization must restore data without paying the ransom.
- Recovery Plan:
- Cloud-Based Backup and Recovery: Restore clean data from cloud-based backups that predate the infection. This minimizes data loss and avoids paying the ransom.
- System Rebuild: Rebuild infected systems in the cloud environment using clean images.
- Process:
- Isolate infected systems from the network.
- Identify the last known clean backup.
- Restore data and rebuild systems in the cloud.
- Thoroughly scan restored data for malware.
- Bring systems back online in a controlled manner.
- Scenario: Regional Natural Disaster
- Description: A hurricane, earthquake, or other natural disaster disrupts business operations within a specific geographic region, impacting physical infrastructure and connectivity.
- Recovery Plan:
- Cloud-Based Failover to a Different Region: Failover to a cloud region located outside the affected area. This allows business operations to continue uninterrupted.
- Data Replication and Backup: Utilize data replication and backup strategies to ensure data availability in the unaffected cloud region.
- Process:
- Monitor the disaster situation.
- Activate the failover plan to the designated cloud region.
- Verify data and system functionality in the secondary cloud region.
- Notify employees and customers of the change.
- Maintain operations from the unaffected cloud region.
Flowchart: Activating a Disaster Recovery Plan
The following flowchart illustrates the general steps involved in activating a disaster recovery plan.
+---------------------------------------------------------------------+| Disaster Event Occurs |+---------------------------------------------------------------------+ | V+---------------------------------------------------------------------+| 1.Detection and Initial Assessment (System failure, etc.) |+---------------------------------------------------------------------+ | V+---------------------------------------------------------------------+| 2. Notification and Communication (DR team, stakeholders, etc.) |+---------------------------------------------------------------------+ | V+---------------------------------------------------------------------+| 3.
Declaration of Disaster (Formal activation of the DR plan) |+---------------------------------------------------------------------+ | V+---------------------------------------------------------------------+| 4. Failover/Recovery Initiation (Cloud-based systems, etc.) |+---------------------------------------------------------------------+ | V+---------------------------------------------------------------------+| 5.
Data Recovery and System Restoration (Backup/replication) |+---------------------------------------------------------------------+ | V+---------------------------------------------------------------------+| 6. Verification and Testing (Functionality, data integrity) |+---------------------------------------------------------------------+ | V+---------------------------------------------------------------------+| 7.
Business Operations Resumption (Cloud environment) |+---------------------------------------------------------------------+ | V+---------------------------------------------------------------------+| 8. Monitoring and Ongoing Management (Performance, security) |+---------------------------------------------------------------------+ | V+---------------------------------------------------------------------+| 9.
Post-Incident Review and Plan Updates (Lessons learned) |+---------------------------------------------------------------------+
Testing and Validation of Disaster Recovery Plans
Regularly testing and validating a disaster recovery (DR) plan is not merely a best practice; it is a critical component of ensuring business continuity in a cloud environment. These tests identify vulnerabilities, confirm the effectiveness of recovery procedures, and provide valuable insights into areas needing improvement.
The cloud’s dynamic nature, with its constant updates and evolving infrastructure, necessitates a proactive approach to DR testing to maintain resilience against disruptions.
Importance of Regular Testing
The primary objective of regular testing is to guarantee that the DR plan functions as intended under various failure scenarios. Without consistent testing, a DR plan can quickly become outdated and ineffective. The cloud environment, with its inherent complexity and dependence on numerous interconnected services, demands a rigorous testing regime.
- Validation of Recovery Objectives: Testing validates that Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs) can be met. RTOs define the maximum acceptable downtime, while RPOs determine the maximum data loss a business can tolerate. During testing, the actual recovery time and data loss are measured against these objectives to identify any discrepancies.
- Identification of Gaps and Weaknesses: Testing uncovers gaps in the DR plan, such as missing procedures, incorrect configurations, or inadequate resource allocation. These weaknesses can be addressed before a real disaster strikes, preventing potentially catastrophic outcomes.
- Verification of Technical Capabilities: Tests ensure that the underlying technical infrastructure, including backup systems, failover mechanisms, and network configurations, functions correctly. This verification covers both the cloud provider’s services and the organization’s own configurations within the cloud.
- Improvement of Team Preparedness: DR testing provides an opportunity for the IT team and other relevant personnel to practice their roles and responsibilities during a disaster. This hands-on experience enhances their understanding of the DR plan and improves their ability to respond effectively in a real emergency.
- Adaptation to Change: The cloud environment is constantly evolving. Regular testing allows organizations to adapt their DR plans to accommodate changes in technology, business requirements, and the threat landscape.
Testing Methods
Several testing methods can be employed to validate a cloud DR plan, each offering a different level of rigor and insight. The selection of testing methods should be based on the criticality of the applications, the complexity of the cloud environment, and the organization’s risk tolerance.
- Tabletop Exercises: These are the simplest form of DR testing, involving a discussion-based scenario walkthrough. Participants review the DR plan, discuss their roles and responsibilities, and simulate a disaster scenario. Tabletop exercises are cost-effective and can be used to identify high-level issues and gaps in the plan. They are particularly useful for training and raising awareness among team members.
- Walkthrough Tests: These tests involve a step-by-step review of the DR plan’s procedures, often without actually executing any recovery operations. Participants follow the documented steps and identify any potential issues or areas for improvement. Walkthrough tests are useful for verifying the completeness and accuracy of the plan.
- Simulation Tests: These tests involve simulating specific disaster scenarios, such as a server failure or a network outage. The IT team executes the DR plan’s procedures to recover the affected systems and data. Simulation tests provide a more realistic assessment of the plan’s effectiveness than tabletop exercises or walkthrough tests.
- Partial Failover Tests: These tests involve failing over a subset of the organization’s systems to the DR site. This allows for testing the recovery procedures without disrupting the entire production environment. Partial failover tests are suitable for verifying the functionality of specific applications or services.
- Full-Scale Failover Tests: These are the most comprehensive tests, involving the complete failover of all production systems to the DR site. Full-scale failover tests provide the most realistic assessment of the DR plan’s effectiveness, but they also involve the greatest risk and require careful planning and execution.
Checklist for Validating a Disaster Recovery Plan’s Effectiveness
A detailed checklist ensures a systematic and thorough evaluation of the DR plan. This checklist should be customized to the specific cloud environment and the organization’s requirements. The following is a sample checklist, which can be used as a foundation for developing a more comprehensive assessment.
1. Plan Documentation and Review:
- Is the DR plan documented, up-to-date, and readily accessible to all relevant personnel?
- Has the DR plan been reviewed and approved by management?
- Does the plan clearly define the scope, objectives, and responsibilities?
2. Backup and Recovery Procedures:
- Are backups performed regularly and according to the defined RPO?
- Are backup data verified for integrity and recoverability?
- Are recovery procedures documented and tested?
- Can data be restored within the defined RTO?
- Are recovery procedures tested for different types of data and applications?
3. Infrastructure and Network Configuration:
- Is the cloud infrastructure configured for high availability and fault tolerance?
- Are network configurations, including DNS, firewalls, and load balancers, properly replicated to the DR site?
- Are failover mechanisms tested to ensure seamless transition?
- Is there sufficient capacity at the DR site to handle the workload?
4. Application and Data Recovery:
- Are all critical applications and data included in the DR plan?
- Are application recovery procedures documented and tested?
- Are data replication and synchronization processes functioning correctly?
- Are application dependencies identified and addressed in the recovery plan?
5. Testing and Validation:
- Have DR tests been conducted regularly, including tabletop exercises, simulation tests, and failover tests?
- Are test results documented and analyzed?
- Are any identified issues or gaps addressed and resolved?
- Is the DR plan updated based on the test results?
- Are the RTOs and RPOs validated during testing?
6. Communication and Coordination:
- Are communication procedures defined and tested?
- Are roles and responsibilities clearly defined for all team members?
- Are external stakeholders, such as cloud providers and vendors, included in the DR plan?
7. Security and Compliance:
- Are security measures, such as access controls and data encryption, implemented at both the production and DR sites?
- Does the DR plan comply with all relevant regulations and industry standards?
- Are security vulnerabilities identified and addressed?
8. Training and Awareness:
- Are all relevant personnel trained on the DR plan and their roles?
- Is the DR plan communicated to all stakeholders?
- Are training sessions conducted regularly to ensure knowledge retention?
9. Continuous Improvement:
- Is there a process for continuously monitoring and improving the DR plan?
- Are lessons learned from past incidents incorporated into the plan?
- Is the DR plan reviewed and updated regularly to reflect changes in the cloud environment and business requirements?
Cost Considerations and Optimization
The economic aspects of cloud disaster recovery are critical, influencing the feasibility and sustainability of any implemented strategy. Understanding the various cost components and employing optimization techniques ensures a cost-effective and resilient solution. This section examines the cost factors, optimization strategies, and methods for calculating the total cost of ownership (TCO) associated with cloud disaster recovery plans.
Overview of Costs Associated with Cloud Disaster Recovery Solutions
Cloud disaster recovery solutions incur costs across several categories. These costs vary based on the chosen recovery strategy, the size of the environment, and the level of service required. Careful consideration of each cost component is essential for informed decision-making.
- Compute Costs: These charges are incurred for the resources used during replication, failover, and failback. They are influenced by the size and complexity of the virtual machines, databases, and applications being protected. For example, using a “warm standby” approach, where standby instances are partially provisioned and ready for immediate use, will have higher compute costs compared to a “cold standby” approach, where resources are only provisioned during a disaster.
- Storage Costs: Storage costs arise from the storage used for backups, replicated data, and snapshots. The volume of data, the storage tier selected (e.g., hot, cold, archive), and the frequency of backups directly impact these costs. For instance, storing infrequently accessed data in a cheaper archive tier can significantly reduce storage expenses.
- Network Costs: Data transfer charges are incurred for data replication between regions or availability zones. These costs are affected by the amount of data transferred and the geographical distance between the primary and secondary sites. Utilizing a Content Delivery Network (CDN) can help to reduce data transfer costs by caching data closer to the end-users.
- Data Transfer Costs: These include costs associated with moving data between regions or zones, especially during replication and failover. They are influenced by the volume of data transferred and the network bandwidth used.
- Licensing Costs: Software licensing costs, particularly for operating systems, databases, and specialized recovery tools, can be a significant expense. Choosing open-source alternatives or optimizing license usage can help reduce these costs.
- Service Costs: Managed services offered by cloud providers, such as automated replication, failover, and recovery orchestration, come with associated service fees. While these services simplify disaster recovery, they contribute to the overall cost.
- Monitoring and Management Costs: These include the expenses associated with monitoring, alerting, and managing the disaster recovery environment. This involves the cost of monitoring tools, automation scripts, and the personnel time required to manage the environment.
- Testing Costs: Regular testing of the disaster recovery plan incurs costs related to the time and resources required for testing. This can include the cost of test environments and the personnel involved in the testing process.
Strategies for Optimizing Costs Without Compromising Recovery Capabilities
Optimizing cloud disaster recovery costs involves balancing cost-effectiveness with the desired recovery objectives. Several strategies can be employed to achieve this balance.
- Tiered Recovery Strategies: Implement different recovery strategies based on the criticality of the applications. Critical applications may require a “hot standby” approach for rapid recovery, while less critical applications can utilize a “cold standby” or “backup and restore” approach, which are more cost-effective.
- Right-Sizing Resources: Carefully select the appropriate instance sizes and storage tiers for the recovery environment. Over-provisioning resources can lead to unnecessary costs, while under-provisioning can compromise recovery performance.
- Automated Orchestration: Use automation tools to streamline the recovery process and reduce manual intervention, which can lower operational costs and improve recovery time.
- Data Compression and Deduplication: Implement data compression and deduplication techniques to reduce the amount of data stored and transferred, thus lowering storage and network costs.
- Lifecycle Management: Automate the lifecycle management of backups and replicated data. This includes automatically archiving older backups to cheaper storage tiers and deleting unnecessary data.
- Scheduled Backups and Replication: Optimize the frequency and timing of backups and replication to minimize costs. For example, backing up less frequently during off-peak hours can reduce network costs.
- Leveraging Cloud Provider Discounts: Take advantage of cloud provider discounts, such as reserved instances or spot instances, to reduce compute costs.
- Regular Cost Analysis and Optimization: Continuously monitor and analyze the costs associated with the disaster recovery plan and make adjustments as needed. This includes regularly reviewing resource utilization and identifying opportunities for cost savings.
Methods for Calculating the Total Cost of Ownership (TCO) of a Disaster Recovery Plan
Calculating the total cost of ownership (TCO) provides a comprehensive view of the costs associated with a disaster recovery plan over a specific period. This helps in making informed decisions and comparing different recovery strategies. The TCO calculation should include both direct and indirect costs.
- Direct Costs: These are the readily quantifiable costs directly associated with the disaster recovery solution.
- Compute Costs: Costs for compute instances, including on-demand, reserved, and spot instances.
- Storage Costs: Costs for storage services, including storage tiers and data transfer fees.
- Network Costs: Costs for data transfer between regions or zones.
- Software Licensing Costs: Costs for software licenses required for disaster recovery.
- Service Costs: Costs for managed services offered by cloud providers.
- Indirect Costs: These costs are less directly attributable but are still essential to consider.
- Personnel Costs: Costs associated with the personnel involved in managing and maintaining the disaster recovery plan.
- Monitoring and Management Costs: Costs for monitoring tools, alerting systems, and other management services.
- Testing Costs: Costs associated with testing the disaster recovery plan, including the time and resources required.
- Opportunity Costs: The cost of the time and resources spent on disaster recovery, which could be used for other business activities.
- TCO Formula: The TCO can be calculated using the following formula:
TCO = (Direct Costs + Indirect Costs)
Time Period
For example, if the direct costs for a year are $10,000 and the indirect costs are $5,000, the TCO for a one-year period is $15,000.
- Detailed Breakdown: Break down the costs into individual components to understand the cost drivers and identify areas for optimization. This allows for a more granular analysis of the costs and helps in making informed decisions.
- Cost Modeling Tools: Use cost modeling tools provided by cloud providers or third-party vendors to estimate the TCO of different disaster recovery strategies. These tools can help in comparing the costs of various options and making data-driven decisions.
- Regular Review and Adjustment: Regularly review and adjust the TCO calculation to account for changes in resource utilization, pricing, and business requirements. This ensures that the TCO calculation remains accurate and relevant over time.
Security and Compliance in Cloud Disaster Recovery
Cloud disaster recovery (DR) plans must incorporate robust security and compliance measures to protect sensitive data and maintain operational integrity during and after a disaster event. Neglecting these aspects can lead to data breaches, regulatory fines, and reputational damage. This section details critical security considerations and compliance strategies for effective cloud DR.
Security Considerations for Cloud Disaster Recovery
Implementing a secure DR plan requires a multi-layered approach, addressing various potential vulnerabilities.
- Data Encryption: Employ encryption at rest and in transit. At rest encryption protects data stored in cloud storage services, such as object storage or databases, from unauthorized access. In transit encryption, typically using Transport Layer Security (TLS) or Secure Sockets Layer (SSL), secures data during transfer between the primary and DR sites or between users and the cloud resources. For example, organizations should consider using Advanced Encryption Standard (AES) with a key length of 256 bits for robust encryption at rest.
- Access Control and Identity Management: Implement strong access control mechanisms, including multi-factor authentication (MFA) and role-based access control (RBAC). RBAC ensures users and systems have only the necessary permissions to perform their tasks, minimizing the potential impact of compromised credentials. Regularly review and update access privileges to reflect changes in personnel and roles.
- Network Security: Utilize virtual private clouds (VPCs) and network segmentation to isolate DR environments. Configure firewalls, intrusion detection/prevention systems (IDS/IPS), and web application firewalls (WAFs) to protect against unauthorized access and malicious activities. For instance, using a WAF can help mitigate distributed denial-of-service (DDoS) attacks that could disrupt DR operations.
- Security Monitoring and Logging: Implement comprehensive security monitoring and logging solutions to track and analyze security events. Centralized logging and security information and event management (SIEM) systems can help detect and respond to security incidents promptly. Regularly review logs for suspicious activities and anomalies.
- Vulnerability Management: Conduct regular vulnerability assessments and penetration testing to identify and address security weaknesses in the DR environment. Regularly patch and update all systems and applications to mitigate known vulnerabilities. Use automated vulnerability scanning tools to maintain an updated security posture.
Ensuring Compliance with Regulations During Disaster Recovery
Maintaining compliance with relevant regulations is crucial during DR to avoid legal and financial repercussions.
- Data Residency: Ensure that data is stored and recovered in compliance with data residency requirements. This may involve selecting cloud regions within specific geographic locations. For instance, GDPR requires that data of EU citizens remains within the EU unless specific conditions are met for transfer to other countries.
- Data Privacy: Implement measures to protect the privacy of personal data, adhering to regulations like GDPR, CCPA (California Consumer Privacy Act), and HIPAA (Health Insurance Portability and Accountability Act). This includes data minimization, purpose limitation, and data subject rights management.
- Data Security Standards: Adhere to industry-specific security standards, such as PCI DSS (Payment Card Industry Data Security Standard) for handling credit card data. These standards prescribe specific security controls for data protection.
- Auditability and Reporting: Maintain comprehensive audit trails and reporting capabilities to demonstrate compliance to regulatory bodies. This includes logging access to data, system changes, and security events. Regularly conduct audits to verify compliance.
- Incident Response Planning: Develop and maintain a robust incident response plan that aligns with regulatory requirements. The plan should Artikel procedures for detecting, containing, and recovering from data breaches or other security incidents, including notification requirements to regulatory bodies and data subjects.
Protecting Data During Transit and At Rest in a Disaster Recovery Environment
Securing data during transit and at rest is a fundamental requirement for cloud DR.
- Data Encryption in Transit: Employ encryption protocols like TLS/SSL to secure data transmitted between the primary and DR sites, and between users and cloud resources. Use strong cipher suites and regularly update certificates to prevent vulnerabilities. For example, use TLS 1.3 with robust cipher suites to ensure data confidentiality and integrity during data transfer.
- Data Encryption at Rest: Implement encryption for all data stored in the DR environment, using encryption keys managed securely. Use encryption services provided by the cloud provider, such as AWS KMS (Key Management Service) or Azure Key Vault, to manage encryption keys. Regularly rotate encryption keys to minimize the impact of key compromise.
- Secure Storage Configuration: Configure storage services with appropriate access controls and security settings. Implement object versioning to protect against data loss due to accidental deletion or corruption. Configure storage lifecycle policies to automatically manage data retention and archival.
- Network Security for Data Transfer: Use secure network connections, such as VPNs or direct connections, to transfer data between the primary and DR sites. Implement network segmentation and firewalls to control traffic flow and prevent unauthorized access. Monitor network traffic for suspicious activities.
- Data Integrity Checks: Implement mechanisms to verify data integrity during replication and recovery. Use checksums or hashing algorithms to detect data corruption. Regularly test data integrity to ensure data consistency.
Automation and Orchestration in Cloud Disaster Recovery
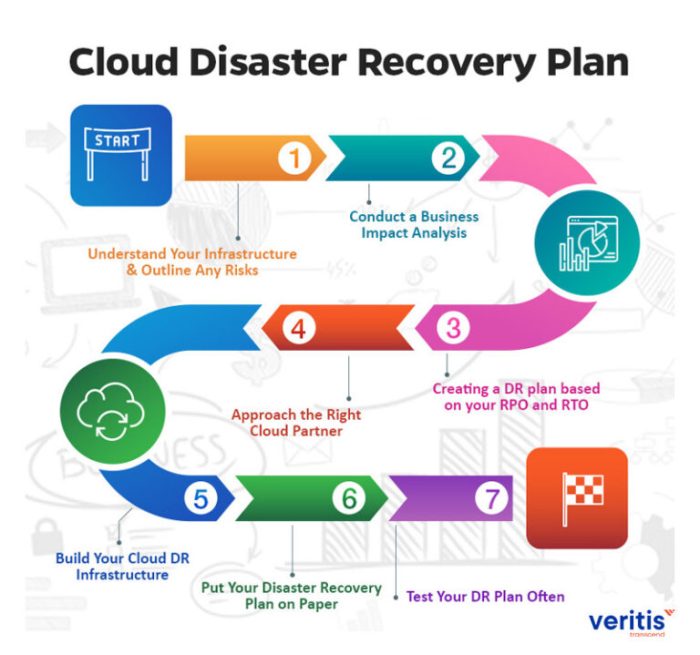
Automation and orchestration are critical components of a robust cloud disaster recovery plan. They minimize human intervention, accelerate recovery times, and reduce the potential for errors during a disaster. By automating repetitive tasks and coordinating complex processes, organizations can significantly improve their resilience and maintain business continuity.
Role of Automation in Streamlining Disaster Recovery Processes
Automation streamlines disaster recovery processes by eliminating manual steps and reducing the time required to recover systems and data. It ensures consistency, repeatability, and reliability in the execution of recovery procedures. This is achieved through pre-defined scripts, templates, and workflows that automatically handle tasks such as failover, failback, and data synchronization. The reduced reliance on manual intervention minimizes the risk of human error, which can be critical during high-pressure disaster scenarios.
Furthermore, automation facilitates proactive monitoring and alerting, enabling rapid detection of potential issues and automated responses before they escalate into major disruptions.
Examples of Automation Tools and Techniques for Cloud Disaster Recovery
A variety of tools and techniques are employed for automating cloud disaster recovery. Infrastructure as Code (IaC) tools, such as Terraform and AWS CloudFormation, are used to define and deploy infrastructure resources in a consistent and repeatable manner. These tools allow for the creation of identical environments in a recovery region, ensuring that applications and data can be quickly restored.
Configuration management tools, like Ansible and Chef, automate the configuration of servers and applications, ensuring that they are properly set up and configured after a failover. Orchestration platforms, such as AWS Step Functions and Azure Logic Apps, coordinate complex workflows, including the execution of multiple automated tasks in a specific order. Scripting languages, such as Python and Bash, are used to create custom scripts for tasks like data backup, data replication, and application failover.
Monitoring and alerting systems, such as Prometheus and Nagios, provide real-time insights into the health of the environment and automatically trigger recovery actions based on pre-defined thresholds.
- Infrastructure as Code (IaC): Tools like Terraform and AWS CloudFormation define and deploy infrastructure resources, enabling the creation of identical environments in a recovery region. For example, a Terraform script could define the network configuration, compute instances, and storage volumes required for an application in a disaster recovery region.
- Configuration Management: Ansible and Chef automate server and application configuration, ensuring consistent setup post-failover. A Chef recipe could be used to install and configure a web server, database, and application code on a new instance.
- Orchestration Platforms: AWS Step Functions and Azure Logic Apps coordinate complex workflows, automating the execution of multiple tasks. An AWS Step Function could orchestrate the following: 1) Initiate a database replication from the primary region to the recovery region. 2) Verify data synchronization. 3) Update DNS records to point to the recovery region.
- Scripting Languages: Python and Bash are used to create custom scripts for tasks such as data backup, data replication, and application failover. A Python script could be used to monitor the health of an application and automatically trigger a failover if a critical component fails.
- Monitoring and Alerting: Prometheus and Nagios provide real-time insights into the environment and trigger recovery actions. A Nagios check could monitor the CPU usage of a server and automatically trigger a failover if the usage exceeds a predefined threshold.
Sample Automated Failover Procedure
The following blockquote illustrates a sample automated failover procedure. This procedure Artikels the steps involved in automatically failing over a critical application from a primary region to a secondary, disaster recovery region in the cloud. It demonstrates how automation tools and techniques can be integrated to minimize downtime and ensure business continuity.
Scenario: A critical application running in AWS us-east-1 (Primary Region) experiences a complete outage.
Automation Components:
- Monitoring: CloudWatch monitors application health (e.g., CPU utilization, latency, error rates).
- Orchestration: AWS Step Functions orchestrates the failover process.
- Infrastructure as Code: Terraform manages infrastructure deployment in us-west-2 (Recovery Region).
Automated Failover Steps:
- Detection: CloudWatch detects application failure (e.g., exceeding error rate threshold).
- Trigger: An alarm in CloudWatch triggers an AWS Step Function execution.
- Verification: The Step Function checks the status of critical components (e.g., database, load balancer).
- Failover Initiation: If all components are healthy in the recovery region (us-west-2), the Step Function proceeds. If not, the Step Function attempts to remediate the issue.
- Database Failover: The Step Function initiates a database failover, promoting the standby database in us-west-2 to primary.
- Load Balancer Update: The Step Function updates the DNS records associated with the application’s load balancer, pointing traffic to the instances in us-west-2.
- Application Start: The Step Function starts the application instances in us-west-2.
- Validation: The Step Function verifies that the application is running and accessible.
- Notification: The Step Function sends a notification to relevant stakeholders, confirming the failover completion.
Expected Recovery Time: Less than 15 minutes, depending on database size and network conditions.
Wrap-Up
In conclusion, a well-defined and rigorously tested disaster recovery plan is not merely a technical necessity but a strategic imperative for organizations operating in the cloud. By understanding the multifaceted nature of cloud-based disasters, selecting appropriate recovery strategies, and incorporating robust security and compliance measures, businesses can significantly mitigate risks and ensure resilience. The proactive approach to disaster recovery, encompassing continuous testing, automation, and cost-effective optimization, will ultimately safeguard data, maintain operational integrity, and facilitate swift recovery in the face of adversity.
Embracing these principles is essential for navigating the complexities of the modern cloud environment and securing long-term business success.
User Queries
What is the primary goal of a disaster recovery plan?
The primary goal is to minimize downtime and data loss, enabling an organization to resume critical business functions as quickly and efficiently as possible following a disruptive event.
How does a cloud disaster recovery plan differ from a traditional on-premises plan?
Cloud-based plans leverage the scalability, flexibility, and geographical distribution of cloud infrastructure, offering potentially faster recovery times and reduced upfront costs compared to traditional on-premises solutions.
What are RTO and RPO, and why are they important?
RTO (Recovery Time Objective) is the maximum acceptable downtime, while RPO (Recovery Point Objective) is the maximum acceptable data loss. They are critical for aligning disaster recovery strategies with business needs and risk tolerance.
How often should a disaster recovery plan be tested?
Disaster recovery plans should be tested regularly, ideally at least twice a year, and whenever significant changes are made to the IT infrastructure or business operations.
What are the key considerations for security in a cloud disaster recovery plan?
Security considerations include data encryption, access controls, network security, and compliance with relevant regulations to protect data during transit, at rest, and throughout the recovery process.