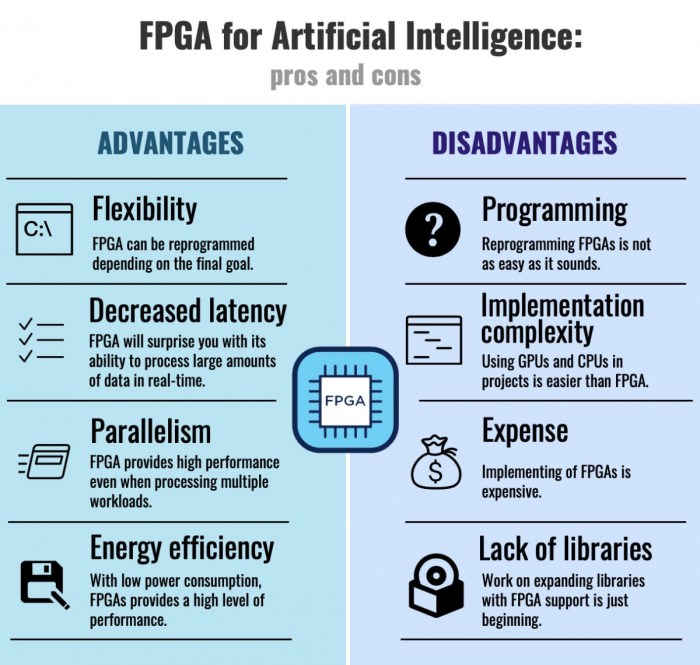
Embarking on a journey through the realm of software development, we uncover the pivotal role of CI/CD triggers. These triggers act as the catalysts, setting in motion the automated processes that streamline the software development lifecycle. They are the unsung heroes that ensure seamless integration, continuous testing, and rapid deployment of software updates.
This exploration delves into the various types of CI/CD triggers, from manual interventions to automated responses, each with its unique function and application. Understanding these triggers is crucial for optimizing your CI/CD pipelines, enhancing efficiency, and accelerating your software release cycles. Prepare to unravel the intricacies of each trigger type and discover how they contribute to a more agile and responsive development environment.
Introduction to CI/CD Triggers
CI/CD triggers are the engines that set the entire automation process in motion. They are the events or conditions that initiate the Continuous Integration and Continuous Delivery (CI/CD) pipeline, automating the build, test, and deployment of software. Understanding and effectively utilizing triggers is crucial for achieving the speed, efficiency, and reliability that CI/CD aims to deliver.A CI/CD trigger is essentially a mechanism that automatically starts a CI/CD pipeline in response to a specific event.
Its primary purpose is to automate the software release process, minimizing manual intervention and enabling faster, more frequent releases. This automation encompasses everything from code changes to infrastructure provisioning and deployment.CI/CD triggers are essential in various scenarios, including code commits to a repository, scheduled builds, and infrastructure changes. They streamline the development lifecycle, reduce the potential for human error, and accelerate the delivery of software updates.
For example, a developer pushing code to a shared repository could automatically trigger a build and test cycle, providing immediate feedback on the changes. Another example could be the automated deployment of a new version of an application following successful test results.
Common Trigger Types
Various types of triggers are used in CI/CD pipelines, each designed for different scenarios and needs. Understanding these triggers is crucial for building an effective and automated software delivery process.
- Code Repository Triggers: These triggers are activated by events within a code repository, such as a new code commit, a pull request creation or update, or a branch merge. They are fundamental for CI, automatically initiating builds and tests whenever code changes are introduced.
- Commit Triggers: A commit trigger initiates the pipeline upon every code commit to a specified branch. This ensures that every code change is immediately tested and validated.
- Pull Request Triggers: Pull request triggers are activated when a pull request is created or updated. This allows for automated testing and code review before merging changes into the main branch.
- Branch Merge Triggers: These triggers activate the pipeline when a branch is merged into another, typically the main or development branch. This triggers the final stages of the pipeline, such as deployment.
- Scheduled Triggers: Scheduled triggers initiate the CI/CD pipeline at predefined times or intervals. This is particularly useful for tasks such as nightly builds, database backups, or regular environment updates.
- Cron Jobs: Cron jobs, a standard time-based job scheduler, can be used to trigger pipelines at specific times or intervals.
- Periodic Builds: Pipelines can be configured to run periodically, such as every hour or day.
- Manual Triggers: Manual triggers require human intervention to start the CI/CD pipeline. This is useful for deployments to production environments, where an extra layer of approval might be necessary.
- Button Click: Pipelines can be triggered by a button click in the CI/CD platform’s interface.
- API Calls: Pipelines can be triggered by making API calls to the CI/CD platform.
- Webhook Triggers: Webhook triggers are activated by external events, such as notifications from other services or applications. This enables integration with various tools and services in the development ecosystem.
- Service Notifications: Pipelines can be triggered by notifications from services like monitoring tools, security scanners, or cloud providers.
- Third-party Integrations: Webhooks enable integration with tools like Slack, Microsoft Teams, or other platforms to trigger builds or deployments based on specific events.
- Environment-Specific Triggers: These triggers are activated by changes or events within specific environments, such as infrastructure updates or configuration changes.
- Infrastructure Changes: Changes to infrastructure, such as provisioning new servers or updating network configurations, can trigger the pipeline.
- Configuration Updates: Updates to application configurations, such as environment variables or settings files, can initiate a deployment.
Trigger Configuration and Best Practices
Configuring CI/CD triggers correctly is crucial for the smooth operation of the pipeline. Several best practices should be followed to ensure efficiency, reliability, and security.
- Specificity: Configure triggers to be as specific as possible. Avoid triggering pipelines unnecessarily.
- Security: Implement security measures, such as access controls and authentication, to protect triggers from unauthorized access.
- Idempotency: Ensure that pipelines are idempotent, meaning that running them multiple times with the same input produces the same result.
- Logging and Monitoring: Implement comprehensive logging and monitoring to track trigger events, pipeline execution, and any errors that occur.
- Testing: Thoroughly test all triggers to ensure they function correctly and trigger the appropriate actions.
- Documentation: Document all triggers, including their purpose, configuration, and any dependencies.
Trigger Examples in Action
Here are some real-world examples of how different trigger types can be used to automate various aspects of the software development lifecycle:
- Example 1: Code Commit Trigger: A developer commits code to the `main` branch of a Git repository. The commit trigger initiates a CI pipeline that performs the following actions:
- Builds the application.
- Runs unit tests.
- Runs integration tests.
- If all tests pass, deploys the application to a staging environment.
- Example 2: Pull Request Trigger: A developer creates a pull request to merge a feature branch into the `develop` branch. The pull request trigger initiates a CI pipeline that performs the following actions:
- Builds the application.
- Runs unit tests.
- Runs code analysis tools (e.g., linters, code quality checkers).
- Provides feedback to the developer on the pull request, indicating whether the build and tests passed and highlighting any code quality issues.
- Example 3: Scheduled Trigger: A scheduled trigger is configured to run a nightly build at 2:00 AM every day. The trigger initiates a CI pipeline that performs the following actions:
- Builds the application.
- Runs all tests (unit, integration, end-to-end).
- Generates a report of the test results.
- If the tests pass, archives the build artifacts.
- Example 4: Webhook Trigger: A security scanning tool detects a vulnerability in a deployed application. The webhook trigger initiates a CI/CD pipeline that performs the following actions:
- Notifies the development team via Slack or email.
- Triggers a rebuild of the application.
- Deploys the patched application to a staging environment for testing.
Manual Triggers
Manual triggers offer a human-in-the-loop approach to CI/CD pipelines, providing control over when a pipeline executes. This contrasts with automated triggers that initiate builds based on events like code commits. Manual triggers are particularly useful when specific approvals or human intervention are required before deploying changes.
Concept of Manual Triggers
Manual triggers allow developers or operations teams to initiate a CI/CD pipeline run on demand. Instead of automatically starting a build when code is pushed to a repository, a user manually clicks a button or submits a request through a CI/CD platform’s interface. This trigger type provides a crucial checkpoint, allowing for review, testing, and verification before deployment.
Advantages and Disadvantages of Using Manual Triggers
There are several benefits and drawbacks to using manual triggers. Understanding these trade-offs is critical when designing a CI/CD strategy.
- Advantages:
- Controlled Deployments: Manual triggers provide a layer of control, ensuring deployments only occur after human review and approval. This can prevent accidental deployments of broken or untested code.
- Flexibility: They offer flexibility, allowing teams to schedule deployments at convenient times, such as outside of peak hours, minimizing potential disruption to users.
- Risk Mitigation: Manual triggers allow for last-minute checks, such as reviewing logs or confirming the state of dependent services, before deploying to production, reducing the risk of deploying problematic code.
- Compliance: In regulated industries, manual triggers can help meet compliance requirements by providing an audit trail and ensuring human oversight of the deployment process.
- Disadvantages:
- Reduced Automation: Manual triggers decrease the level of automation in the CI/CD pipeline. This can lead to slower release cycles compared to automated triggers.
- Human Error: Relying on manual processes increases the potential for human error. A user might forget to trigger a build, trigger the wrong pipeline, or make incorrect decisions during the review process.
- Increased Overhead: Manual triggers add overhead to the deployment process, requiring additional time and effort from the development and operations teams.
- Potential Bottlenecks: If approvals or manual steps are not handled efficiently, manual triggers can become bottlenecks, slowing down the entire release process.
Step-by-Step Procedure for Implementing a Manual Trigger in a CI/CD Pipeline
Implementing a manual trigger involves configuring the CI/CD platform to recognize and respond to user-initiated events. Here’s a general procedure:
- Choose a CI/CD Platform: Select a CI/CD platform (e.g., Jenkins, GitLab CI, CircleCI, Azure DevOps, AWS CodePipeline) that supports manual triggers. Most platforms offer this functionality.
- Create or Modify the Pipeline: Define or modify the CI/CD pipeline to include the necessary steps for building, testing, and deploying the application.
- Configure the Manual Trigger: Within the CI/CD platform, configure the pipeline to accept a manual trigger. This usually involves selecting a trigger type (e.g., “Manual,” “On-demand”) and specifying the conditions under which the trigger is available.
- Define Approval Steps (Optional): If required, integrate approval steps into the pipeline. This might involve notifying approvers and waiting for their approval before proceeding with the deployment.
- Add Notifications (Optional): Configure notifications to alert relevant stakeholders (developers, operations teams, testers) when a manual trigger is initiated or requires action.
- Test the Trigger: Thoroughly test the manual trigger to ensure it functions correctly. Verify that the pipeline starts as expected when the trigger is activated and that all steps are executed in the correct order.
- Document the Process: Document the manual trigger process, including who is responsible for initiating the trigger, any required approvals, and the steps involved in each stage of the pipeline.
Scheduled Triggers
Scheduled triggers are a crucial component of CI/CD pipelines, enabling automated execution based on predefined time intervals or specific dates. This functionality ensures that builds, tests, and deployments occur regularly, maintaining a consistent and up-to-date software delivery process without requiring manual intervention. They provide a proactive approach to software integration and deployment, optimizing development workflows.
Functionality of Scheduled Triggers
Scheduled triggers function by initiating a CI/CD pipeline at a specific time or according to a recurring schedule. This automation relies on a scheduling mechanism, which can vary depending on the CI/CD system. The core functionality involves defining a schedule, which the system then monitors. When the schedule’s criteria are met, the trigger activates the pipeline, initiating the build, testing, and deployment stages.
The scheduler typically runs in the background, ensuring the pipeline is triggered accurately and reliably. Some systems offer advanced scheduling capabilities, allowing for complex schedules such as specific days of the week, months, or even more intricate patterns.
Use Cases for Scheduled Triggers
Scheduled triggers prove highly beneficial in various scenarios, streamlining software development and deployment workflows. They are particularly useful for tasks that need to be performed regularly, such as nightly builds, periodic database backups, and routine security scans.
- Nightly Builds: Regularly scheduled nightly builds ensure that the latest code changes are integrated and tested. This approach identifies integration issues early, preventing them from accumulating over time. This proactive approach is widely adopted to maintain code quality and stability.
- Regular Database Backups: Automated database backups can be scheduled to run at regular intervals, such as daily or weekly. This protects against data loss and ensures business continuity. The schedule can be customized to align with off-peak hours to minimize disruption.
- Periodic Security Scans: Security scans can be scheduled to run automatically, checking the codebase for vulnerabilities and compliance issues. This helps to identify and address security threats proactively, maintaining the security posture of the application.
- Deployment of Minor Updates: Small, non-critical updates can be deployed automatically at scheduled intervals, ensuring that the application is always up-to-date with the latest features and bug fixes. This reduces the manual effort required for routine maintenance.
- Reporting and Data Processing: Scheduled triggers can be used to run reports or process data at regular intervals. This is particularly useful for generating business intelligence reports or processing large datasets.
Comparing Scheduling Options
Different CI/CD systems offer a range of scheduling options, providing flexibility in defining the trigger schedule. The following table compares various scheduling methods and their key characteristics:
| Scheduling Option | Description | Benefits | Considerations |
|---|---|---|---|
| Cron Jobs | Uses the cron syntax to define schedules (e.g., `0 0
| Highly flexible and allows for complex scheduling patterns. Widely supported across various systems. | Can be complex to understand and maintain, especially for intricate schedules. Requires familiarity with cron syntax. |
| Specific Dates | Triggers the pipeline on a specific date and time (e.g., `2024-12-25 00:00`). | Simple and straightforward for one-time deployments or events. Easy to configure. | Limited to single-occurrence triggers. Not suitable for recurring tasks. |
| Recurring Intervals | Triggers the pipeline at a defined interval (e.g., every hour, every day, every week). | Simple to set up for routine tasks. Easily maintainable for consistent deployments. | May not provide the granular control of cron jobs. Can be less flexible for complex schedules. |
| Calendar-Based Schedules | Uses a calendar interface to visually define schedules (e.g., clicking on dates to trigger). | User-friendly and intuitive, especially for non-technical users. Reduces the learning curve. | May have limited options for complex schedules. The interface might not be available in all CI/CD systems. |
Code Commit Triggers
Code commit triggers represent a cornerstone of modern CI/CD pipelines, automating the initiation of the build, test, and deployment processes whenever changes are committed to a code repository. This automation streamlines development workflows, reduces manual intervention, and accelerates the software delivery lifecycle.
Initiation of CI/CD Pipelines
Code commit triggers function as the primary enabler for continuous integration and continuous delivery. When a developer pushes code changes to a designated branch in the version control system, the trigger detects this event and automatically initiates the CI/CD pipeline. This pipeline then performs a series of automated steps, such as building the code, running unit and integration tests, and deploying the application to a staging or production environment.
Role of Version Control Systems
Version control systems, such as Git, are integral to the functionality of code commit triggers. Git provides a centralized repository for code, tracking changes, and managing different versions of the software. The commit trigger monitors the repository for specific events, such as pushes to a designated branch (e.g., `main`, `develop`), and triggers the pipeline accordingly. The commit message and associated metadata are often used to provide context for the build process and can be used for tasks such as automated changelog generation or notification.
- Branch-Specific Triggers: Configure triggers to activate only upon commits to specific branches. This allows for different pipelines based on the branch (e.g., a testing pipeline for `develop` and a production deployment pipeline for `main`).
- Merge Request/Pull Request Triggers: Many CI/CD systems can trigger a pipeline upon the creation of a merge or pull request. This allows developers to validate their changes before merging them into the main branch. The pipeline can run tests and provide feedback on the proposed changes.
- Tag-Based Triggers: Triggers can be set to initiate a pipeline when a specific tag is added to the repository. This is useful for versioning and releasing software. For example, creating a tag like `v1.0.0` could trigger a pipeline to build a production-ready artifact.
Configuration of Code Commit Triggers
Configuring a code commit trigger typically involves specifying the repository, the branch(es) to monitor, and the actions to take when a commit occurs. The specific steps vary depending on the CI/CD platform being used (e.g., Jenkins, GitLab CI, CircleCI, GitHub Actions). However, the general process involves these steps:
- Select the Repository: Specify the Git repository that contains the code.
- Choose the Trigger Event: Define the event that will trigger the pipeline. This is often a push to a specific branch, the creation of a pull request, or the addition of a tag.
- Configure the Pipeline: Define the steps of the CI/CD pipeline. This includes building the code, running tests, and deploying the application.
- Provide Authentication: Configure the CI/CD system to access the repository. This often involves providing credentials or setting up SSH keys.
For example, in a GitHub Actions workflow, you might define a trigger in your `workflow.yml` file:“`yamlon: push: branches: – main – develop“`This configuration specifies that the workflow will be triggered whenever a push event occurs on either the `main` or `develop` branch. This streamlined approach ensures that every code change undergoes a rigorous automated process, enhancing code quality and accelerating the delivery pipeline.
Branch-Based Triggers
Branch-based triggers are a fundamental aspect of modern CI/CD pipelines, enabling automated builds, tests, and deployments based on changes made to specific branches within a version control system. They provide a granular level of control over the CI/CD process, allowing teams to tailor their workflows to different development activities and release strategies.
Functionality of Branch-Based Triggers
Branch-based triggers function by monitoring a repository for changes to designated branches. When a commit or pull request is made to a branch that is configured for triggering, the CI/CD system automatically initiates a pipeline run. This pipeline typically includes steps such as building the application, running unit and integration tests, and deploying the code to a staging or production environment, depending on the branch configuration.
The trigger mechanism often uses webhooks, which are automated notifications sent from the repository (e.g., Git, GitLab, Bitbucket) to the CI/CD system, signaling the occurrence of an event, such as a new commit or a pull request merge.
Best Practices for Utilizing Branch-Based Triggers
Implementing branch-based triggers effectively requires careful planning and adherence to best practices. These practices ensure efficient workflows, minimize errors, and facilitate a smooth development process.
- Define Clear Branching Strategies: Establish a well-defined branching model, such as Gitflow or GitHub Flow, to guide your development process. This helps in mapping branches to specific development phases and release cycles.
- Configure Triggers for Relevant Branches: Configure triggers only for branches that require automated CI/CD pipelines. Common examples include:
- Main/Master/Production Branch: Trigger a pipeline for deployments to the production environment upon merges to this branch.
- Develop/Staging Branch: Trigger a pipeline for deployments to a staging environment for testing and validation.
- Feature Branches: Trigger pipelines to build, test, and potentially deploy feature branches to isolated environments for feature validation and review.
- Release Branches: Trigger pipelines for building release candidates, running final tests, and preparing for production deployment.
- Hotfix Branches: Trigger pipelines for quickly deploying bug fixes to production.
- Implement Environment-Specific Configurations: Use environment variables or configuration files to customize the pipeline behavior based on the target environment. For instance, use different database connection strings or API endpoints for staging and production deployments.
- Automate Testing at Every Stage: Integrate comprehensive testing, including unit tests, integration tests, and end-to-end tests, into your pipelines. This ensures code quality and reduces the risk of deploying faulty code.
- Use Pull Requests for Code Reviews: Require pull requests for all code changes, and integrate code review processes into your workflow. This helps catch potential issues before they are merged into the target branch.
- Implement Branch Protection Rules: Use branch protection rules in your version control system to enforce policies, such as requiring code reviews, passing tests, and preventing direct commits to protected branches.
- Monitor Pipeline Execution: Monitor the execution of your pipelines and analyze the results. Set up notifications to alert the team of failures or other important events.
- Optimize Pipeline Performance: Optimize the pipeline execution time by using techniques like caching dependencies, parallelizing tests, and minimizing unnecessary steps.
Examples of Different Scenarios
Branch-based triggers are incredibly versatile and can be adapted to various development workflows. Here are some specific scenarios illustrating their use:
- Feature Branch Workflow:
- Scenario: A developer creates a feature branch named `feature/new-login-page` from the `develop` branch to implement a new login page.
- Trigger: A branch-based trigger is configured to initiate a pipeline when a commit is pushed to any branch starting with `feature/`.
- Pipeline Actions: The pipeline builds the application, runs unit tests, and deploys the feature branch to a dedicated staging environment for the feature. A code review is initiated via a pull request.
- Outcome: The feature is tested and reviewed in isolation before merging into the `develop` branch.
- Release Branch Workflow:
- Scenario: A release branch named `release/v1.2.0` is created from the `develop` branch to prepare for a new release.
- Trigger: A trigger is configured to initiate a pipeline when a commit is pushed to any branch starting with `release/`.
- Pipeline Actions: The pipeline builds the application, runs all tests, and prepares a release candidate.
- Outcome: A stable release candidate is created and deployed to a pre-production environment for final testing.
- Hotfix Branch Workflow:
- Scenario: A hotfix branch named `hotfix/critical-bug-fix` is created from the `master` branch to address a critical bug in production.
- Trigger: A trigger is configured to initiate a pipeline when a commit is pushed to any branch starting with `hotfix/`.
- Pipeline Actions: The pipeline builds the application, runs tests, and deploys the hotfix directly to the production environment.
- Outcome: The critical bug is quickly fixed and deployed to production.
- Production Deployment Workflow:
- Scenario: Code is merged into the `master` branch, signifying a production-ready release.
- Trigger: A trigger is configured to initiate a pipeline upon commits to the `master` branch.
- Pipeline Actions: The pipeline builds the application, runs all tests, and deploys the application to the production environment.
- Outcome: The latest version of the application is deployed to production.
Pull Request Triggers
Pull Request (PR) triggers are a crucial component of modern CI/CD pipelines, especially in collaborative development environments. They automate the process of testing and validating code changes submitted via pull requests, ensuring code quality and preventing integration issues before merging into the main codebase. This proactive approach streamlines the development workflow and enhances overall software quality.
Purpose of Pull Request Triggers
The primary purpose of pull request triggers is to automatically initiate CI/CD processes when a pull request is created or updated. This automation allows for the early detection of potential problems.
- Early Error Detection: By running tests and other validations on code changes before merging, PR triggers catch bugs and issues early in the development cycle, reducing the cost and effort required to fix them.
- Code Quality Assurance: PR triggers enforce code quality standards by running linters, code style checks, and security scans. This ensures that the code adheres to the project’s guidelines and best practices.
- Integration Testing: PR triggers can include integration tests to verify that the changes integrate correctly with other parts of the system. This helps prevent integration conflicts and ensures that the different components of the software work together seamlessly.
- Reduced Risk of Merge Conflicts: By validating changes against the target branch before merging, PR triggers minimize the risk of merge conflicts and integration problems. This streamlines the merging process and reduces the time spent resolving conflicts.
Benefits of Using Pull Request Triggers for Code Review
Utilizing pull request triggers significantly enhances the code review process, leading to more efficient and effective reviews. This ultimately contributes to higher-quality code and a more collaborative development environment.
- Automated Code Analysis: PR triggers automate tasks like static code analysis and security scans, freeing up reviewers to focus on the more complex aspects of the code, such as design and logic. This allows for a more thorough and efficient review process.
- Faster Feedback Loops: By providing immediate feedback on code changes, PR triggers accelerate the feedback loop between developers and reviewers. This allows for quicker identification and resolution of issues, leading to faster iteration cycles.
- Improved Code Consistency: PR triggers ensure that code adheres to established standards and best practices, resulting in more consistent and maintainable code. This consistency simplifies code reviews and makes it easier for developers to understand and contribute to the codebase.
- Increased Developer Productivity: Automating testing and validation processes reduces the manual effort required by developers, freeing up their time to focus on writing code. This increase in productivity leads to faster development cycles and improved project outcomes.
Workflow of a Pull Request Trigger
The workflow of a pull request trigger typically involves a series of automated steps that are executed when a pull request is created or updated. The following diagram illustrates this workflow:
Diagram Description:
The diagram illustrates the workflow of a pull request trigger, beginning with a developer creating a pull request (PR) in a version control system (e.g., Git). The version control system then notifies the CI/CD platform. The CI/CD platform, in response, initiates a build process that includes several stages.
The first stage involves fetching the code from the PR branch.Following this, the code undergoes a series of automated checks, including:
- Code Compilation: The code is compiled to ensure there are no syntax errors.
- Static Code Analysis: Tools like linters and code style checkers are used to analyze the code for style violations, potential bugs, and security vulnerabilities.
- Unit Tests: Unit tests are executed to verify the functionality of individual components.
- Integration Tests: Integration tests are performed to ensure different components work together correctly.
Based on the results of these checks, the CI/CD platform provides feedback to the PR. If all checks pass, the PR is marked as “ready for review.” If any checks fail, the PR is marked as “failed,” and the developer receives feedback to address the issues. The developer can then make changes, push them to the PR branch, and trigger the process again.
This cycle continues until all checks pass, and the PR is ready to be merged.
Merge Request Triggers
Merge request triggers are a crucial element in CI/CD pipelines, particularly in collaborative development environments. They automate the process of validating changes before they are integrated into the main codebase. This proactive approach helps maintain code quality and stability by catching potential issues early in the development cycle.
Functionality of Merge Request Triggers
Merge request triggers initiate a CI/CD pipeline automatically whenever a merge request (also known as a pull request in some systems) is created or updated. The pipeline typically performs several tasks:
- Code Compilation: Compiles the code to ensure there are no syntax errors.
- Code Analysis: Performs static analysis to identify potential code quality issues, such as style violations, security vulnerabilities, and code smells. Tools like SonarQube or linters are often used.
- Automated Testing: Executes unit tests, integration tests, and potentially end-to-end tests to verify the functionality of the code changes.
- Dependency Management: Checks for any dependency conflicts or vulnerabilities.
- Artifact Creation (Optional): Builds artifacts (e.g., Docker images, deployable packages) if the tests pass.
If any of these steps fail, the merge request is typically blocked from being merged until the issues are resolved. This prevents broken code from being integrated into the main branch.
Comparison of Pull Request Triggers and Merge Request Triggers
Pull request triggers and merge request triggers share a fundamental similarity: they both initiate CI/CD pipelines based on code changes. However, there are subtle but important differences. While the terms “pull request” and “merge request” are often used interchangeably, especially across different version control systems, the context in which they are used can influence the specific behavior of the trigger.
- Trigger Initiation: Both trigger pipelines upon the creation or update of a request to merge code.
- Scope: Both primarily focus on validating changes before integration into a main branch.
- Specifics of Triggering Event:
- Pull Request Triggers: Often trigger on the creation of a pull request, or whenever the pull request branch is updated with new commits. They commonly run against the proposed changes, simulating the merge to the target branch.
- Merge Request Triggers: Might be more explicitly tied to the act of merging. The pipeline might run just before the merge, or after, depending on the CI/CD configuration. Some systems might treat them identically to pull request triggers.
- Target Branch Considerations: Both types of triggers typically involve running the pipeline against the proposed changes, with the changes being compared to the target branch.
- Tooling and System Dependency: The specific terminology (pull request or merge request) and the behavior of the triggers can be influenced by the version control system and CI/CD tools used (e.g., GitHub, GitLab, Bitbucket, Jenkins, CircleCI, etc.).
The distinction often comes down to the specific platform and the configuration of the CI/CD pipeline. In some systems, the terms are synonymous; in others, there might be subtle differences in the timing or scope of the triggered actions.
Real-World Example of a Merge Request Trigger’s Use
A software development team uses GitLab with a CI/CD pipeline configured to run tests and code analysis on every merge request. A developer submits a merge request to merge their feature branch into the `main` branch. The merge request trigger activates the pipeline. The pipeline performs the following steps: first, it compiles the code; second, it runs unit tests; third, it executes integration tests; and finally, it performs static code analysis using a tool like SonarQube. If any of the tests fail or if the code analysis identifies any critical issues, the merge request is blocked. The developer receives feedback and must address the identified problems before the merge request can be approved and merged. This process ensures that only high-quality code is integrated into the main branch, reducing the risk of bugs and improving the overall stability of the software.
Tag-Based Triggers
Tag-based triggers are a critical component of CI/CD pipelines, enabling automated processes to be initiated upon the creation of a new tag in a version control system. This trigger type is particularly useful for managing releases and ensuring consistent versioning throughout the software development lifecycle. By automatically building, testing, and deploying code when a tag is created, teams can streamline their release processes and reduce the potential for human error.
Tag-Based Trigger Significance
Tag-based triggers play a crucial role in automating the release process. They automate the building, testing, and deployment of a software version when a specific tag is created in the version control system, typically Git. This automation reduces the manual effort required for each release, minimizes the risk of errors, and ensures consistency across releases.
Situations for Tag-Based Trigger Appropriateness
Tag-based triggers are most appropriate in scenarios involving the release of software versions, such as:
- Release Management: When a new software version is ready for release, a tag is created, triggering the CI/CD pipeline to build, test, and deploy the tagged version to production or staging environments.
- Version Control: Tag-based triggers are ideal for projects that need to maintain a clear and consistent versioning strategy. Each tag represents a specific version of the software, making it easy to identify and revert to previous versions if needed.
- Automated Builds: Whenever a new tag is pushed, the CI/CD pipeline is triggered to automatically build the software, ensuring that the tagged version is built from the latest code.
- Testing and Quality Assurance: Tag-based triggers can be used to automatically run tests and quality assurance checks when a new tag is created, ensuring that the tagged version meets quality standards before deployment.
- Deployment to Production: In many cases, tag-based triggers are used to deploy the tagged version to a production environment, automating the release process and reducing the risk of manual errors.
Process for Automatic Software Version Creation on Tag Push
Designing a process for automatic software version creation on a tag push involves several steps, ensuring a smooth and reliable release workflow. Here’s a detailed breakdown:
- Tag Creation: A developer or release manager creates a new tag in the version control system (e.g., Git) to mark a specific commit as a release candidate. For instance, a tag like `v1.2.3` might be created.
- Trigger Activation: The CI/CD system is configured to recognize tag creation events. When a new tag is pushed to the repository, the trigger activates the pipeline.
- Build Process: The CI/CD pipeline starts a build process. This involves:
- Fetching Source Code: The pipeline fetches the source code associated with the newly created tag.
- Dependency Management: The pipeline installs all necessary dependencies.
- Compilation/Build: The source code is compiled or built into an executable artifact.
- Testing Phase: The built artifact undergoes various tests to ensure quality and stability. This includes:
- Unit Tests: Individual components of the software are tested.
- Integration Tests: Tests are performed to verify the interaction between different components.
- End-to-End Tests: The entire application is tested from start to finish.
- Artifact Creation: If all tests pass, the pipeline creates a deployable artifact. This could be a Docker image, a compiled binary, or a package.
- Deployment: The deployable artifact is deployed to the target environment. This can be a staging or production environment. The deployment process may involve:
- Environment Configuration: Setting up the environment (servers, databases, etc.) for the new version.
- Artifact Transfer: Transferring the artifact to the target environment.
- Service Restart: Restarting services to use the new version.
- Database Migrations: Running any required database migrations.
- Verification and Monitoring: After deployment, the pipeline performs verification steps and monitors the deployed version to ensure it functions correctly. This may include:
- Health Checks: Checking the application’s health.
- Performance Monitoring: Monitoring the application’s performance.
- Error Logging: Checking for any errors in the logs.
- Notification: The pipeline sends notifications about the release status. This may include notifications to developers, testers, and stakeholders.
This process ensures that each tag represents a stable and deployable version of the software, automating the release lifecycle from code commit to deployment.
Dependency Update Triggers
Dependency update triggers are a crucial component of modern CI/CD pipelines, enabling automated testing and deployment whenever a project’s dependencies are modified. This automation ensures that the software remains compatible with the latest versions of its dependencies and minimizes the risk of introducing vulnerabilities or breaking changes.
How Dependency Update Triggers Work
Dependency update triggers initiate a CI/CD pipeline when changes are detected in a project’s dependency files. These files, such as `package.json` for Node.js projects, `pom.xml` for Maven projects, or `requirements.txt` for Python projects, specify the external libraries and packages that the software relies on. The trigger monitors these files for any modifications, including:
- Version Updates: When a dependency version is updated (e.g., from version 1.0.0 to 1.1.0), the trigger is activated.
- New Dependency Additions: When a new dependency is added to the project’s dependency file.
- Dependency Removals: When a dependency is removed from the project’s dependency file.
Upon detecting a change, the trigger automatically initiates the CI/CD pipeline, which typically involves:
- Dependency Installation: The pipeline installs the updated dependencies.
- Code Compilation (if applicable): The code is compiled to ensure it still works with the new dependencies.
- Automated Testing: Unit tests, integration tests, and potentially end-to-end tests are executed to verify the software’s functionality and ensure compatibility with the updated dependencies.
- Deployment (if tests pass): If all tests pass, the software is deployed to the designated environment (e.g., staging or production).
Impact of Dependency Updates on the Software Development Lifecycle
Dependency updates have a significant impact on the software development lifecycle, influencing aspects like stability, security, and maintainability. Regularly updating dependencies helps to:
- Improve Security: Dependency updates often include security patches that address known vulnerabilities. Failing to update dependencies can leave a project exposed to exploits. For example, the Equifax data breach in 2017 was partly attributed to a vulnerability in the Apache Struts framework, which Equifax had not updated.
- Enhance Performance: Newer versions of dependencies often incorporate performance improvements, leading to faster execution times and reduced resource consumption.
- Fix Bugs: Dependency updates frequently include bug fixes that resolve issues in the underlying libraries, leading to a more stable and reliable application.
- Access New Features: Updates can introduce new features and functionalities that developers can leverage to enhance the software’s capabilities.
- Reduce Technical Debt: Staying current with dependencies helps to avoid accumulating technical debt, which can become costly and time-consuming to address later.
However, dependency updates can also introduce risks:
- Breaking Changes: New versions of dependencies may include breaking changes that can cause the software to malfunction.
- Compatibility Issues: Updates might introduce compatibility issues with other dependencies or the underlying operating system.
- Increased Complexity: Managing dependencies can become complex, especially in projects with a large number of dependencies.
To mitigate these risks, developers should carefully review the release notes of each dependency update, thoroughly test the software after updating dependencies, and consider using a dependency management tool that can help to identify and resolve compatibility issues.
Tools and Technologies that Support Dependency Update Triggers
Several tools and technologies support dependency update triggers, enabling automated dependency management and CI/CD workflows.
- CI/CD Platforms: Platforms like Jenkins, GitLab CI/CD, CircleCI, Travis CI, and GitHub Actions provide built-in support for dependency update triggers. These platforms allow developers to configure pipelines that automatically run when changes are detected in dependency files.
- Dependency Management Tools: Tools such as npm (for Node.js), Maven (for Java), pip (for Python), and Bundler (for Ruby) facilitate dependency management. They can be integrated with CI/CD pipelines to install, update, and manage dependencies.
- Dependency Scanning Tools: Tools like Snyk, OWASP Dependency-Check, and WhiteSource (now Mend) scan projects for vulnerabilities in dependencies and provide recommendations for updates. These tools can be integrated with CI/CD pipelines to automatically trigger builds when vulnerabilities are detected.
- Automated Dependency Update Tools: Tools like Renovate and Dependabot automate the process of updating dependencies. They monitor dependency files for updates, create pull requests with the updated dependencies, and trigger CI/CD pipelines to test the changes. Dependabot, for example, can automatically create pull requests for outdated dependencies in GitHub repositories, allowing developers to review and merge the updates.
API-Based Triggers
API-based triggers offer a powerful mechanism to initiate CI/CD pipelines programmatically, allowing for seamless integration with external systems and automated workflows. This approach enables organizations to extend their CI/CD capabilities beyond traditional code repositories and integrate them into a broader ecosystem of tools and services.
Role of API-Based Triggers
API-based triggers function as a bridge, connecting external systems to your CI/CD pipeline. When a specific event occurs in an integrated system, an API request is sent to the CI/CD platform, initiating the pipeline execution. This allows for highly customized automation based on various factors, such as events in project management tools, security scans, or external data updates. The primary role of an API-based trigger is to enable CI/CD pipelines to react to events happening outside of the typical code repository environment.
Use Cases for API-Based Triggers, Focusing on External Integrations
API-based triggers are especially valuable for integrating CI/CD with external services, enhancing automation and improving the overall development lifecycle.
- Integration with Project Management Tools: Triggering a pipeline when a task in a project management tool (like Jira or Trello) reaches a specific status, such as “Ready for Deployment” or “Code Review Approved.” This automates the deployment process based on project progress.
- Security Scans and Vulnerability Checks: Initiating a pipeline after a security scan completes and identifies vulnerabilities. This allows for automated remediation workflows, where the pipeline could automatically create a bug report, alert the development team, or even attempt to patch the vulnerability based on predefined rules.
- Database Updates and Schema Changes: Triggering a pipeline when a database schema change is detected or a new version of the database is deployed. This can include running tests, creating backups, and migrating data.
- Integration with Monitoring Systems: Starting a pipeline when a monitoring system detects a performance degradation or a critical error. This enables automated troubleshooting and deployment of fixes.
- User-Defined Events and Webhooks: Responding to custom events or webhooks from any system that can send an HTTP request, enabling highly customized workflows. This includes integrating with e-commerce platforms, content management systems, and other business applications.
Example of an API Request to Initiate a CI/CD Pipeline
The specific format of the API request will vary depending on the CI/CD platform used (e.g., Jenkins, GitLab CI, CircleCI, etc.). However, the general structure remains consistent: a POST request to a specific endpoint with relevant parameters.
Here’s an example using a simplified scenario:
Scenario: Trigger a CI/CD pipeline when a new user is registered in a CRM system. The CRM system sends a webhook (an HTTP POST request) to the CI/CD platform.
API Request (Example): POST /api/v1/pipelines/trigger
Host: ci.example.com
Content-Type: application/json
Authorization: Bearer YOUR_API_TOKEN
"pipeline_id": "user-registration-pipeline",
"event_type": "user_registered",
"user_data":
"user_id": "12345",
"email": "[email protected]"
Explanation:
- POST /api/v1/pipelines/trigger: The API endpoint on the CI/CD platform to trigger a pipeline.
- Host: ci.example.com: The domain of the CI/CD platform.
- Content-Type: application/json: Specifies the format of the request body.
- Authorization: Bearer YOUR_API_TOKEN: Authentication header. Replace `YOUR_API_TOKEN` with a valid API token. This is essential for security.
- pipeline_id: Identifies the specific CI/CD pipeline to execute (e.g., “user-registration-pipeline”).
- event_type: A custom parameter indicating the event that triggered the pipeline (e.g., “user_registered”).
- user_data: Contains data related to the event, such as the user’s ID and email. This data can be used within the pipeline (e.g., to send a welcome email).
The CI/CD platform would receive this request, authenticate the API token, and initiate the “user-registration-pipeline.” The pipeline might then perform tasks such as:
- Sending a welcome email to the new user.
- Provisioning resources for the user (e.g., creating a database entry).
- Updating a monitoring dashboard with the new user information.
Event-Based Triggers
Event-based triggers are a sophisticated mechanism for automating CI/CD pipelines, enabling them to respond dynamically to external events. This approach moves beyond scheduled or code-commit-driven pipelines, allowing for a more reactive and efficient CI/CD process. This dynamic capability is crucial for modern software development, where rapid response to changes and external factors is often necessary.Event-based triggers provide a significant advantage in scenarios where the initiation of a pipeline is contingent on specific occurrences within the software development lifecycle or related systems.
These events can originate from various sources, including external services, system notifications, or user actions, ensuring that the pipeline is triggered only when relevant changes or conditions are met. This helps in optimizing resource utilization and ensures that pipelines are executed precisely when needed.
Types of Events and Their Impact on the Pipeline
Event-based triggers are versatile and can be configured to respond to a wide range of events. The following is a discussion of various event types and their impact on a CI/CD pipeline.
- Webhooks: Webhooks are HTTP callbacks triggered by events in a source system. When a specific event occurs, the source system sends an HTTP POST request to a configured URL. This request typically contains data about the event.
- Impact: Webhooks enable integration with external services, such as version control systems (e.g., GitHub, GitLab), issue trackers (e.g., Jira), and other third-party tools.
They can trigger pipelines based on events like code pushes, pull request updates, or issue status changes. For instance, a webhook configured in GitHub can trigger a pipeline to build and test code whenever a new commit is pushed to a specific branch.
- Impact: Webhooks enable integration with external services, such as version control systems (e.g., GitHub, GitLab), issue trackers (e.g., Jira), and other third-party tools.
- Service Hooks: Service hooks are similar to webhooks but are often provided by specific platforms or services to trigger actions in other services.
- Impact: Service hooks are commonly used for integrating CI/CD pipelines with cloud providers, monitoring tools, or other specialized services. For example, a service hook from a cloud provider can trigger a pipeline to deploy a new version of an application after a successful build and test process.
- System Events: These triggers are based on events generated by the operating system or infrastructure.
- Impact: System events can trigger pipelines in response to server events such as system failures, resource utilization alerts, or security breaches. For example, if a server reaches a high CPU utilization threshold, a pipeline could be triggered to automatically scale up the infrastructure or investigate the issue.
- Monitoring Alerts: Monitoring systems generate alerts based on predefined conditions or anomalies detected in the application or infrastructure.
- Impact: Monitoring alerts can initiate pipelines for incident response, such as rolling back a deployment or restarting a service. If a monitoring tool detects a critical error in the application logs, a pipeline can be triggered to automatically roll back to the previous stable version.
- Database Events: Changes in a database can trigger a pipeline.
- Impact: Database events are useful for tasks such as data migration, schema updates, or data validation. For example, if a database schema is updated, a pipeline can be triggered to run migration scripts and ensure that the application is compatible with the new schema.
- Timer-Based Events (with limitations): While not strictly event-based, some systems allow triggering pipelines based on timers or schedules that are indirectly linked to events. For example, a timer could trigger a pipeline to check for specific conditions.
- Impact: Timer-based events can be used for tasks such as periodic data backups, cleanup operations, or health checks. For instance, a timer could trigger a pipeline to perform a data backup every night.
Conclusion
In conclusion, the different types of CI/CD triggers are the essential building blocks of modern software development. From initiating builds with code commits to automating deployments based on specific events, these triggers empower teams to deliver high-quality software with speed and precision. By mastering the use of these triggers, you can significantly improve your development workflows, reduce errors, and accelerate your time-to-market.
Embracing these strategies will undoubtedly lead to a more efficient, reliable, and ultimately, more successful software development process.
General Inquiries
What is the primary purpose of a CI/CD trigger?
The primary purpose of a CI/CD trigger is to automatically initiate a CI/CD pipeline, enabling continuous integration, testing, and deployment processes.
How do manual triggers differ from automated triggers?
Manual triggers require human intervention to start a CI/CD pipeline, while automated triggers are activated by predefined events, such as code commits or scheduled times.
Are there any security considerations when using API-based triggers?
Yes, when using API-based triggers, it’s crucial to secure the API endpoints with authentication and authorization mechanisms to prevent unauthorized access and potential security breaches.
What are the benefits of using branch-based triggers?
Branch-based triggers enable teams to test changes in isolation, facilitating parallel development and preventing integration conflicts by automatically triggering builds and tests for specific branches.