Understanding the saga pattern for distributed transactions is crucial in modern software architecture, especially when dealing with complex, multi-step processes across multiple services. This pattern allows for resilient and reliable transactions across distributed systems, providing a robust alternative to traditional two-phase commit approaches. This in-depth exploration delves into the core principles, implementation strategies, and real-world applications of sagas, providing a comprehensive guide for developers.
The saga pattern excels in scenarios where a single, monolithic transaction is too complex or risky. By breaking down a transaction into smaller, individual sub-transactions (or “activities”), the saga pattern enhances the system’s fault tolerance and resilience. This approach decouples services and allows for independent processing and recovery, leading to a more robust and scalable application.
Introduction to Saga Pattern
The Saga pattern is a powerful approach for managing distributed transactions across multiple services or microservices. It provides an alternative to the traditional two-phase commit protocol, which can be cumbersome and less resilient in a distributed environment. The Saga pattern excels in scenarios where a single atomic transaction is impractical or undesirable.The Saga pattern’s core strength lies in its ability to decompose a complex transaction into a series of smaller, individual transactions, each handled by a specific service.
This decomposition improves fault tolerance and scalability. Furthermore, Sagas allow for more granular control over individual steps within a transaction, enabling the system to handle failures more gracefully.
Core Principles of Saga Pattern
The Saga pattern operates on the principle of compensating transactions. This means that for every transaction, a compensating transaction is defined. The compensating transaction undoes the effect of the original transaction if an error occurs at any stage. This allows for rollback procedures to be implemented at a finer granularity, minimizing the impact of failures. This principle of compensation is critical for maintaining data consistency in distributed systems.
Motivations for Using Sagas
Several factors motivate the use of Sagas in distributed systems. Firstly, two-phase commit protocols can become performance bottlenecks in highly distributed systems. Sagas, by their nature, are more resilient to failures and can operate with reduced coupling between components. Secondly, Sagas allow for more fine-grained control over the transaction flow, enabling the system to handle failures more gracefully.
Finally, Sagas promote a more modular and scalable architecture.
Key Components of a Saga Implementation
A Saga implementation typically involves the following components:
- Saga Orchestrator: This component coordinates the execution of the individual transactions. It acts as the central control point, monitoring the progress of each step and triggering compensating transactions when needed. The orchestrator does not perform any of the actual operations; it merely directs the flow.
- Saga Entities: These entities represent the individual steps or transactions within the Saga. Each entity is responsible for executing a specific part of the overall transaction. Entities often reside in different services.
- Compensation Logic: For each Saga Entity, a compensating transaction is defined. This logic ensures that the system can revert to a consistent state if any step fails.
Example: Order Processing Saga
Consider an e-commerce application that processes orders. The order processing involves multiple steps, such as creating an order, reserving inventory, and updating the payment. These steps can be handled by different services, each acting as a Saga Entity.
| Step | Saga Entity | Action | Compensation |
|---|---|---|---|
| Order Creation | Order Service | Create order in database | Cancel order in database |
| Inventory Reservation | Inventory Service | Reduce inventory count | Restore inventory count |
| Payment Processing | Payment Service | Process payment | Refund payment |
In this example, if the payment processing fails, the order service’s compensation logic is invoked to cancel the order and the inventory service’s compensation logic is invoked to restore the inventory count. This ensures that the system remains in a consistent state despite failures.
Types of Sagas
The Saga pattern, while fundamentally a framework for orchestrating distributed transactions, manifests in various forms, each tailored to specific needs and complexities. Understanding these variations is crucial for designing resilient and scalable distributed systems. This section delves into the different types of Sagas, highlighting their distinctions and implications.Different Saga implementations address the need for varied levels of control and compensation mechanisms.
This understanding is vital for selecting the appropriate strategy for specific distributed transaction scenarios.
Compensating Sagas
Compensating Sagas are a class of Saga pattern that are designed with a specific emphasis on maintaining system consistency. A core principle of this type is the ability to reverse or undo any operation if an error occurs during the transaction. This ensures the system remains in a valid state regardless of failures. The importance of a clear compensation mechanism cannot be overstated, as it is essential for the reliability and integrity of the system.
- Compensation Actions: These Sagas employ a compensating action for each operation. This compensating action, if executed, effectively reverses the original action. The sequence of actions is meticulously designed so that any failure in one operation can be rectified by the subsequent compensation action. This approach ensures transactional integrity.
- Robustness: The strength of compensating Sagas lies in their ability to revert to a prior state, making them ideal for applications where data consistency is paramount. This capability ensures the system always returns to a valid state, even in the event of errors.
- Complexity: Designing and implementing compensating actions can be more complex than non-compensating approaches, particularly in systems with intricate dependencies. The need to anticipate and plan for every possible failure path adds a layer of complexity.
Non-Compensating Sagas
Non-compensating Sagas differ significantly from their compensating counterparts. They focus on achieving a desired outcome without the rigorous need for a complete reversal. This approach sacrifices some transactional consistency in favor of a simpler design and potentially quicker execution.
- Limited Rollbacks: Non-compensating Sagas often handle failures by simply logging the errors or performing partial rollbacks. A complete reversal is not always possible or practical. The primary objective is to maintain a functional state, even if data integrity is not fully restored to the initial state.
- Simplified Design: The reduced emphasis on compensation makes non-compensating Sagas easier to design and implement. This simplicity can lead to faster development cycles and lower overhead, making them suitable for situations where complete consistency is not absolutely critical.
- Trade-offs: This approach carries a risk of leaving the system in an inconsistent state if failures occur. The design must consider the potential for data loss or partial updates in such scenarios. This is often the trade-off for a simpler design.
Comparison of Saga Types
| Saga Type | Description | Compensation Mechanism | Complexity |
|---|---|---|---|
| Compensating Saga | A Saga pattern where each operation has a corresponding compensating action to reverse the operation in case of failure. | Explicit compensation actions are defined for every operation. | Higher, due to the need for comprehensive compensation logic. |
| Non-Compensating Saga | A Saga pattern where compensation is not a primary concern. The focus is on achieving a desired outcome, even if it means accepting some level of inconsistency. | Limited or no explicit compensation; might rely on error logging or partial rollbacks. | Lower, due to the reduced need for complex compensation logic. |
Saga Implementation Strategies

The saga pattern, while conceptually elegant, requires careful consideration during implementation. Choosing the right approach for implementing a saga, particularly in a distributed environment, is crucial for ensuring its robustness and scalability. Effective implementation strategies leverage various techniques to manage transactions across multiple services, ensuring data consistency and fault tolerance.
Implementation Approaches
Several approaches exist for implementing sagas, each with its own trade-offs. A common approach involves using a dedicated saga orchestrator, a component responsible for coordinating the execution of individual sub-transactions, or steps, within the saga. Alternatively, sagas can be implemented without a central orchestrator, using a decentralized approach where each service manages its own sub-transactions and communicates directly with other services.
Message Queues in Saga Execution
Message queues play a critical role in saga execution, acting as a reliable communication channel between services. They decouple services, allowing them to operate asynchronously and independently. This asynchronous nature is essential for achieving fault tolerance. If one service fails, other services can continue their respective steps, ensuring the overall saga can recover.
Handling Failures in a Saga
Handling failures in a distributed saga is paramount. One approach is to employ compensation transactions. If a sub-transaction fails, a compensation transaction is executed to reverse the effects of the failed transaction. For example, if a payment fails, a compensation transaction could be used to return the funds to the original account. Another technique is to employ retry mechanisms, allowing for a specific number of attempts to complete a sub-transaction.
If all attempts fail, a compensation transaction should be triggered.
Event Sourcing in Saga Implementations
Event sourcing provides a powerful approach for saga implementations. By storing all changes as events, the system can reconstruct the state of the system at any point in time. This approach can simplify the implementation of compensation transactions, as the system can revert to a previous state by replaying the events in reverse order. This approach is particularly beneficial for complex sagas where the state changes are intricate.
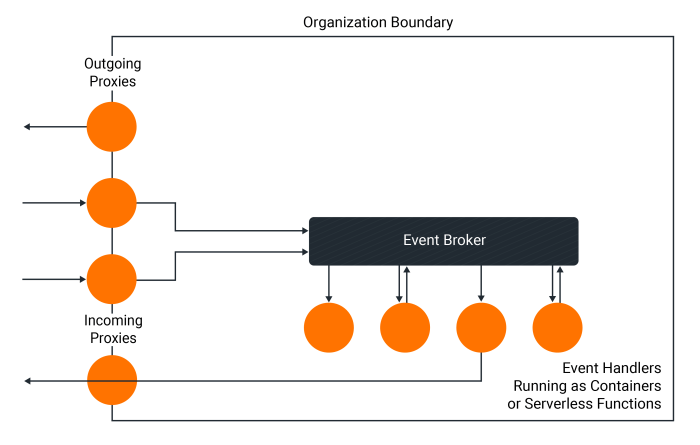
Saga Implementation Flowchart (with Message Queues)
This flowchart illustrates a basic saga implementation leveraging message queues. Each step represents a sub-transaction in the saga.
Explanation of the Flowchart
- The saga begins with an initial event, triggering a sub-transaction in the first service.
- The first service sends a message to a message queue.
- The message queue delivers the message to the second service.
- The second service processes its sub-transaction and sends a message to the message queue.
- This process continues until all sub-transactions are complete.
- If any sub-transaction fails, a message is sent to the message queue indicating the failure.
- A compensation transaction is triggered to reverse the effects of the failed sub-transaction.
Benefits and Drawbacks of Sagas

The Saga pattern offers a powerful approach to managing distributed transactions, providing resilience and flexibility in complex microservice architectures. However, it’s crucial to understand both its advantages and limitations to make informed decisions about its applicability. This section delves into the trade-offs inherent in using Sagas, comparing them to alternative solutions.The Saga pattern’s strength lies in its ability to handle failures gracefully and maintain data consistency across multiple services.
This is achieved by breaking down a complex transaction into smaller, manageable sub-transactions, each with its own compensation logic. This approach enables greater fault tolerance, as a failure in one sub-transaction does not necessarily derail the entire process.
Advantages of Using the Saga Pattern
The Saga pattern presents several key advantages over traditional monolithic or two-phase commit approaches. These include increased resilience, improved performance, and enhanced flexibility.
- Resilience to Failures: Sagas are inherently more resilient to failures than two-phase commit protocols. If a single service fails during a transaction, the Saga can often continue the transaction using compensation logic in other services. This is a significant improvement, as two-phase commit would require a rollback across all services, potentially leading to data inconsistencies and cascading failures.
- Improved Performance: The decoupled nature of Sagas often leads to improved performance compared to two-phase commit. By breaking down a large transaction into smaller, independent steps, the Saga can potentially execute sub-transactions concurrently, leading to faster overall transaction processing.
- Enhanced Flexibility: Sagas allow for greater flexibility in the design and implementation of distributed transactions. They can be adapted to diverse microservice architectures and accommodate varying levels of complexity more readily than other approaches. This is because Sagas are more adaptable to the specific requirements of each sub-transaction.
Disadvantages and Limitations of Sagas
While Sagas offer significant advantages, they also present certain drawbacks. The complexity of implementing and managing Sagas can be a considerable challenge, particularly in complex systems. Furthermore, the implementation often involves a greater overhead.
- Implementation Complexity: Implementing a Saga requires careful design and coding. Compensation logic needs to be meticulously crafted to ensure data consistency across all steps. This intricate design and implementation can become a significant hurdle, particularly for complex transactions.
- Debugging Challenges: Debugging Saga transactions can be more challenging than debugging simpler transactions. Tracking the flow of events and identifying the root cause of failures can be a complex process. The distributed nature of Sagas can make it harder to pinpoint the source of problems.
- Increased Overhead: Sagas introduce overhead due to the need for communication between services and the maintenance of compensation logic. This overhead can be a concern, especially for simple transactions. It is crucial to carefully weigh the benefits of Saga against the potential increase in processing time.
Trade-offs Between Complexity and Resilience
The Saga pattern requires a more intricate design than simpler approaches, but this complexity often translates to greater resilience. The key is to find the optimal balance between these two factors.
A well-designed Saga architecture can provide significantly greater resilience to failures, but this comes at the cost of increased complexity in implementation and maintenance.
The trade-off lies in assessing the potential for failure within a specific system. If the likelihood of failures is high or the transaction involves multiple, interdependent services, the complexity of a Saga might be justified by the improved resilience it provides. Conversely, for simple transactions with low failure rates, a simpler approach might be sufficient.
Comparison with Two-Phase Commit
Sagas differ significantly from two-phase commit protocols. While both aim to ensure atomicity in distributed transactions, their approaches and characteristics differ considerably.
| Feature | Saga | Two-Phase Commit |
|---|---|---|
| Transaction Decomposition | Decomposes transaction into smaller, independent sub-transactions | Treats the transaction as a single, atomic unit |
| Failure Handling | Handles failures in individual sub-transactions gracefully using compensation logic | Requires a global rollback across all participating services if a failure occurs |
| Complexity | Higher implementation complexity | Lower implementation complexity |
| Resilience | High resilience to failures | Lower resilience to failures |
Sagas provide greater flexibility and resilience to failures in distributed systems, but this flexibility comes at the cost of added implementation complexity. Two-phase commit is simpler to implement but is less resilient and can be problematic in large-scale, fault-prone environments.
Saga State Management
Managing the state of a Saga is crucial for ensuring the integrity and consistency of distributed transactions. Incorrect state management can lead to data corruption, lost transactions, and application instability. This section details strategies for maintaining Saga state, preventing data corruption during failures, handling concurrency, and leveraging databases for state storage.Maintaining a consistent and accurate record of the Saga’s progress is paramount.
This includes tracking the status of each individual transaction within the Saga, ensuring that the system can recover from failures and resume processing where it left off. Efficient state management is key to building resilient and reliable distributed systems.
State Management Strategies
Various strategies can be employed for managing Saga state. These strategies encompass different approaches to persisting the Saga’s current state, enabling recovery and avoiding data corruption. Choosing the appropriate strategy depends on the specific needs of the application.
- Database-based State Management: Storing Saga state in a dedicated database is a common and robust approach. This allows for easy persistence, recovery, and querying of Saga information. A relational database, such as PostgreSQL or MySQL, can be leveraged to store Saga instances, including their current status, transactions, and any relevant data associated with each step of the Saga.
This approach provides ACID properties, ensuring data consistency and atomicity during state transitions. This also facilitates efficient querying and retrieval of Saga data for various operations.
- Message Queue-based State Management: Utilizing message queues, such as Kafka or RabbitMQ, to track the state of a Saga can be advantageous in scenarios requiring high throughput and asynchronous processing. Each Saga step can be represented as a message, and the queue acts as a repository for the Saga’s current state. This approach is well-suited for scenarios where the Saga involves multiple independent tasks or when handling large volumes of data.
- In-memory State Management: In certain cases, maintaining Saga state in memory might be sufficient, especially for short-lived Sagas or those with limited data. This approach is generally suitable for applications where the overhead of database interactions or message queues is considered excessive or unnecessary. However, it is crucial to consider the potential loss of data in case of application crashes or system failures.
For production-level applications, this approach is usually not recommended.
Maintaining Consistency and Avoiding Data Corruption
Maintaining consistency and avoiding data corruption during failures requires meticulous planning and implementation. This involves techniques for ensuring that all steps of a Saga are consistently applied or rolled back when a failure occurs. Using idempotent operations is a critical aspect in avoiding unwanted side effects and ensuring that the same operation applied multiple times produces the same result.
- Idempotent Operations: Employing idempotent operations is crucial to ensure that a Saga step can be re-executed without altering the system’s state in undesirable ways. This approach allows for safe retry mechanisms, enabling successful completion of the Saga even if a failure occurs during processing.
- Compensation Transactions: Implementing compensation transactions allows for gracefully handling failures during Saga execution. Each step in the Saga has a corresponding compensation transaction that reverses the effects of a failed step. This approach ensures data integrity even in the event of errors.
- Rollback Strategies: Implementing a rollback strategy is a vital component in managing Saga failures. Rollback strategies should be carefully designed to ensure that any changes made by a failed step are reverted to the previous state. This approach helps in maintaining data consistency in the face of failures.
Handling Concurrency and Race Conditions
Concurrency and race conditions are potential pitfalls in Saga execution. Appropriate mechanisms are needed to coordinate multiple concurrent Saga executions to avoid conflicting updates and maintain data integrity.
- Optimistic Locking: Implementing optimistic locking can mitigate the impact of race conditions. Optimistic locking allows the system to detect conflicts by comparing the expected state with the actual state before committing changes. This approach is less complex than pessimistic locking, but it may lead to more frequent conflicts.
- Pessimistic Locking: Pessimistic locking acquires exclusive locks on resources during the execution of a Saga step, preventing concurrent access and thus avoiding race conditions. This strategy is generally more reliable, but it can lead to higher contention and reduced throughput.
- Saga Coordination: Saga coordination mechanisms are crucial in managing concurrency. These mechanisms allow Saga instances to communicate and coordinate their execution, ensuring that no conflicts arise and that the Saga’s overall state remains consistent.
Using a Database to Store Saga State
Using a database to store Saga state provides a structured and persistent way to track Saga progress. It ensures that the state is preserved even after application restarts.
- Saga State Table: A dedicated table, specifically designed for Saga state management, can be created. This table would store details such as Saga ID, current step, transaction status, and timestamps for each step. This table is vital for querying and retrieving Saga information during processing and recovery.
- Data Modeling: Careful data modeling is crucial for effective state management. Appropriate data structures should be selected to store Saga-related information efficiently and accurately, ensuring that the data accurately reflects the Saga’s progress.
Saga Orchestration
The saga pattern relies on a central orchestrator to coordinate the execution of multiple sub-transactions, ensuring that the overall business logic is maintained and that the system remains consistent. This orchestrator acts as the conductor of a complex symphony, ensuring that each individual microservice plays its part in the overall transaction. It’s responsible for initiating, monitoring, and compensating for failures within the distributed system.The orchestrator is not directly involved in the execution of individual sub-transactions; rather, it manages the flow of these sub-transactions, ensuring that the desired outcome is achieved or, if necessary, undoing the effects of previous steps.
This separation of concerns is crucial for maintaining the overall integrity of the transaction.
Role of the Saga Orchestrator
The saga orchestrator is the central component responsible for managing the entire saga. It receives the initial request, orchestrates the interactions with various microservices, and monitors their execution. Critically, it also handles compensation actions if any sub-transaction fails. This ensures that the system remains in a consistent state, even in the face of partial failures.
Approaches for Orchestrating Sub-Transactions
Several approaches can be employed to orchestrate the sub-transactions within a saga. These include using message queues for asynchronous communication, employing a dedicated API gateway for handling requests, and utilizing a centralized orchestration service. The choice of approach depends on the specific needs of the application and the complexity of the saga.
- Message Queues: Message queues are a common approach for orchestrating sub-transactions. The orchestrator publishes messages to the queue, triggering actions in the various microservices. The microservices respond by publishing messages back to the queue, allowing the orchestrator to track progress and handle compensation actions. This approach offers loose coupling between the microservices, making it suitable for systems with evolving needs.
- API Gateway: An API gateway can act as a central point for coordinating interactions between the orchestrator and the microservices. The gateway can handle routing, authentication, and authorization, streamlining the communication process. This approach enhances security and simplifies the management of dependencies between microservices.
- Centralized Orchestration Service: A dedicated service can be created specifically for orchestrating the saga. This service would handle all interactions with the microservices, ensuring a consistent and controlled execution flow. This approach is well-suited for complex sagas with numerous sub-transactions.
Coordinating Multiple Microservices
The orchestrator must coordinate interactions with multiple microservices involved in a saga. This involves a clear understanding of the sequence of operations, dependencies between services, and potential failure points. Careful consideration of error handling and compensation mechanisms is essential.
- Communication Protocols: The orchestrator needs to use suitable communication protocols, such as REST APIs or message queues, to interact with the microservices. The choice of protocol should be guided by factors such as performance requirements and complexity of interactions.
- Dependency Management: The orchestrator needs to understand and manage dependencies between microservices to ensure the proper order of execution. Failure to manage these dependencies can lead to cascading failures and inconsistencies.
- Fault Tolerance: The orchestrator must incorporate fault tolerance mechanisms to handle potential failures in individual microservices. This involves implementing retry mechanisms, timeout policies, and compensation actions.
Orchestrator Design Example
An orchestrator might use a state machine to manage the execution flow. The state machine transitions from one state to another based on the success or failure of individual sub-transactions. The state machine defines the valid transitions and the actions to be performed in each state.
A simple example could be a state machine that has states like “Initiate Order,” “Process Payment,” “Fulfill Order,” and “Cancel Order.” The orchestrator would transition between these states based on the outcomes of each sub-transaction.
The design should include mechanisms for monitoring the progress of each sub-transaction, handling failures, and executing compensation actions. Error handling and logging are also crucial aspects of the orchestrator design.
Error Handling and Recovery
The saga pattern, while offering significant advantages for distributed transactions, is susceptible to various failure points. Robust error handling and recovery mechanisms are crucial for ensuring the overall success of the application and maintaining data consistency. Understanding common error scenarios and implementing effective strategies for detecting and recovering from failures is paramount.Effective error handling in a saga implementation involves more than just catching exceptions.
It necessitates a comprehensive approach that considers the interconnected nature of the individual steps within the saga. This requires a clear understanding of how to gracefully handle partial successes and failures, enabling the system to compensate for any setbacks and ultimately achieve a consistent state.
Common Error Scenarios
Failures can arise at any stage of a saga. Network issues, timeouts, service outages, and unexpected exceptions in individual steps are all potential sources of errors. Data validation failures, conflicting data, or resource unavailability can also disrupt the execution flow. Incorrect data formats or missing information during the processing of a step can also lead to errors.
The failure of a single step can have cascading effects on subsequent steps, potentially leading to a broader system failure if not handled properly.
Techniques for Detecting and Recovering from Failures
Robust error detection is crucial to mitigate the impact of failures. Implementing proper logging mechanisms is essential for monitoring the progress of each step in a saga. Using timeout mechanisms for individual steps allows the system to detect and react to prolonged delays or unresponsive services. Monitoring service health and checking the availability of resources before initiating a step is essential for proactive error prevention.
Employing appropriate exception handling and error codes throughout the saga workflow allows for the precise identification of the source of the failure.
Strategies for Handling Partial Successes and Compensating for Failures
Partial successes, where some steps in the saga complete successfully while others fail, pose a significant challenge. Implementing compensation logic is vital for reversing the effects of failed steps. This requires defining a compensating transaction for each operation in the saga. For instance, if a payment step fails, a compensation step will be required to return the payment.
Careful consideration of the possible failure points and their corresponding compensation logic is crucial. This involves meticulously planning for potential failures and crafting the compensating actions to undo the partial successes. A detailed compensation strategy minimizes the risk of leaving the system in an inconsistent state.
Saga Recovery Process Diagram
The diagram below illustrates a typical recovery process after a saga failure. The initial step involves the detection of the failure. Next, the system attempts to identify the failed step and the impacted state. The process then initiates the execution of the corresponding compensating transaction. Finally, the system verifies that the compensation step has been successfully completed.
If successful, the system returns to a consistent state. If not, the system must retry or escalate the issue.
+-----------------+ +-----------------+ +-----------------+| Saga Initiated | --> | Step 1 Success | --> | Step 2 Failure |+-----------------+ +-----------------+ +-----------------+| | | | | || | | | | || | | | | || | | | | || | | | | Compensating || | | | --> | Step 2 Undo |+-----------------+ +-----------------+ +-----------------+| | | | | || | | | | || | | | | || | | | | || | | | | Saga Recovery |+-----------------+ +-----------------+ +-----------------+
Note: The diagram above depicts a simplified scenario. Real-world implementations may involve more complex scenarios, such as retries, error escalation, and alternative compensation strategies.
Monitoring and Debugging Sagas
Monitoring and debugging distributed transactions, especially those implemented using the Saga pattern, can be challenging due to the inherent complexity of coordinating multiple, potentially independent, transactions. Effective monitoring and debugging strategies are crucial for identifying and resolving issues, ensuring system reliability, and minimizing downtime. Robust monitoring and debugging capabilities help prevent cascading failures and ensure the overall health of the application.Thorough monitoring and debugging techniques provide invaluable insights into the execution flow of Saga transactions.
This enables developers to pinpoint errors and anomalies, facilitating rapid issue resolution and improving the overall performance of the system.
Strategies for Monitoring Saga Execution
Monitoring Saga execution requires capturing and analyzing data related to individual transactions within the Saga. This encompasses tracking the status of each transaction, identifying delays or failures, and correlating these events across the entire Saga. Comprehensive monitoring allows developers to understand the execution path and quickly identify any deviations from the expected behavior.
- Transaction Logging: Implementing detailed logging for each step within a Saga is essential. This includes logging timestamps, transaction IDs, and the status of each transaction (e.g., success, failure, pending). Comprehensive logs facilitate correlation of individual events within a Saga, enabling rapid analysis of execution flows.
- Event Streaming: Employing event streaming allows for real-time monitoring of Saga execution. Events generated during each transaction step are published to a dedicated stream, providing a continuous view of the Saga’s progress. This approach provides a real-time picture of the overall status, aiding in rapid identification of anomalies.
- Metrics Collection: Collecting key metrics, such as transaction duration, error rates, and the number of retries, provides a high-level overview of Saga performance. These metrics allow for the identification of potential bottlenecks and performance degradation patterns, enabling proactive optimization.
Methods for Debugging Saga Issues
Debugging Saga issues necessitates effective techniques for tracing the execution flow, isolating the source of errors, and understanding the relationships between different transactions within the Saga. Comprehensive logging, combined with effective debugging tools, enables the rapid identification and resolution of complex problems.
- Tracing and Correlation: Implement mechanisms for tracing the execution of each Saga. This includes correlating events from different transactions within the Saga to provide a holistic view of the execution flow. Tracing enables the precise identification of the point where a Saga deviates from its expected behavior, facilitating pinpoint debugging.
- Transaction Context Propagation: Ensure that crucial transaction context information is propagated across different services involved in a Saga. This context can include unique transaction identifiers, timestamps, and the current state of the Saga. This enables tracing and correlation across different microservices.
- Rollback and Retry Mechanisms: Understanding the Saga’s rollback and retry mechanisms is crucial for debugging. Analyzing how the system handles failures and retries provides valuable insights into the root causes of issues and helps in the development of effective recovery strategies. This involves inspecting error handling procedures and identifying possible points of failure.
Examples of Monitoring Tools for Saga Systems
Numerous tools are available to assist in monitoring Saga systems. The choice of tool depends on the specific requirements and infrastructure of the system. Tools vary in their capabilities, including tracing, logging, and visualization features.
- Jaeger: A popular open-source distributed tracing system. Jaeger can effectively trace and visualize the execution flow of a Saga, identifying delays or failures in individual transactions.
- Zipkin: Another open-source distributed tracing system that offers similar functionality to Jaeger. Zipkin can track transactions across multiple services, facilitating analysis of Saga execution.
- Grafana: A popular open-source platform for visualizing metrics. Grafana can be used to monitor Saga metrics, such as transaction duration, error rates, and throughput, enabling performance analysis.
Blueprint for Implementing a Monitoring Dashboard for Sagas
A monitoring dashboard provides a centralized view of Saga execution, enabling real-time monitoring and issue identification.
| Component | Description |
|---|---|
| Saga Status | Displays the overall status of each Saga (e.g., active, completed, failed). |
| Transaction Details | Provides a breakdown of individual transactions within a Saga, including timestamps, status, and associated errors. |
| Metrics Visualization | Displays key metrics, such as transaction duration, error rates, and throughput, to aid in performance analysis. |
| Tracing and Correlation | Visualizes the execution flow of a Saga, correlating individual transaction events. |
Security Considerations
The Saga pattern, while powerful for distributed transactions, introduces unique security challenges. Carefully addressing these vulnerabilities is crucial for maintaining data integrity and preventing unauthorized access or modification within the complex interactions of the participating services. Implementing robust security measures is paramount to ensuring the reliability and trustworthiness of the entire system.Understanding potential security breaches and vulnerabilities within a Saga implementation is vital to mitigating risks and building a secure system.
Security concerns often arise from the distributed nature of the Saga, the interconnectedness of services, and the potential for unauthorized access or manipulation during the transaction process.
Potential Security Vulnerabilities
Several potential security vulnerabilities can arise in Saga implementations. These vulnerabilities can compromise the integrity and confidentiality of data being processed, and can lead to unexpected outcomes or failures. Common concerns include:
- Data Exposure: Insecure data handling during the Saga’s various steps can expose sensitive data to unauthorized parties. This might occur during communication between services or storage of intermediate data.
- Tampering with Intermediate States: Malicious actors might attempt to alter intermediate states of the Saga, potentially leading to incorrect final outcomes or unintended consequences.
- Unauthorized Access to Services: Vulnerabilities in the authentication and authorization mechanisms of participating services can allow unauthorized users to interfere with the Saga execution.
- Replay Attacks: Replaying previously executed Saga steps can disrupt the transaction’s integrity or potentially lead to unauthorized actions. This is especially a concern in scenarios with long-running Saga executions.
- Denial-of-Service Attacks: Malicious actors might attempt to overload the Saga orchestration or participating services, disrupting the entire system and preventing legitimate transactions.
Strategies for Securing Saga Interactions
Effective security measures are crucial to mitigate these risks. Strategies to secure Saga interactions include:
- Robust Authentication and Authorization: Implementing strong authentication mechanisms, such as using API keys, OAuth, or other secure protocols, is vital. Appropriate authorization policies need to be in place to control access to resources and actions within the Saga.
- Secure Communication Channels: Using secure communication protocols like HTTPS ensures that data exchanged between services remains confidential and prevents eavesdropping. Employing encryption for data at rest is also essential.
- Input Validation and Sanitization: Thorough input validation and sanitization of data received from external sources or users is critical to prevent injection attacks and other malicious manipulations.
- Idempotency Checks: Ensuring that Saga steps are idempotent (meaning they can be repeated without altering the final outcome) can help prevent malicious actors from repeatedly executing the same actions, reducing the risk of data corruption or unexpected results.
- Rate Limiting: Implementing rate limiting mechanisms can help prevent denial-of-service attacks by controlling the frequency of requests to the Saga orchestration or participating services.
Authentication and Authorization in Saga Transactions
Authentication and authorization play a critical role in Saga transactions. These mechanisms control access to the Saga’s participating services and ensure that only authorized users can initiate or participate in the Saga.
- Authentication Mechanisms: Effective authentication mechanisms, such as API keys or tokens, are necessary to verify the identity of users and services initiating Saga executions. Strong passwords and multi-factor authentication (MFA) are crucial components of a robust authentication strategy.
- Authorization Policies: Clear authorization policies define which users or services are permitted to access specific resources or perform certain actions within the Saga. These policies should be fine-grained and based on the specific roles and responsibilities of the users and services involved.
Security Best Practices for Saga Development
A comprehensive set of best practices for secure Saga development is crucial to minimizing vulnerabilities and maximizing security.
- Principle of Least Privilege: Granting only the necessary permissions to users and services participating in the Saga. Avoid over-privileged access.
- Regular Security Audits: Conducting regular security audits to identify and address potential vulnerabilities in the Saga implementation.
- Security Awareness Training: Educating developers on security best practices to ensure awareness of potential vulnerabilities.
- Security Testing: Implementing security testing procedures, such as penetration testing, to identify and address potential security flaws before deployment.
- Secure Logging and Monitoring: Implementing robust logging and monitoring mechanisms to track Saga interactions and detect potential security anomalies.
Real-World Use Cases
The Saga pattern, while conceptually powerful, shines when applied to complex, distributed systems. Understanding its practical implementations across various industries reveals the significant value it offers. From streamlining order processing in e-commerce to ensuring accurate financial transactions in banking, Sagas have proven to be a robust solution.
E-commerce Order Processing
E-commerce platforms often involve numerous steps in processing an order, including inventory updates, payment processing, shipping confirmations, and customer notifications. A Saga orchestrates these independent steps as a single, atomic transaction, even if they involve different systems. A failure in one step, such as a payment failure, triggers a rollback of previous steps, preventing partial order completion. Successful implementations in this domain have streamlined order fulfillment, improved customer satisfaction, and reduced operational costs.
Financial Transactions
Complex financial transactions, such as fund transfers between accounts, involve multiple steps. Sagas enable reliable execution by ensuring all steps succeed or all steps are rolled back consistently. If a transfer fails, the Saga mechanism ensures the originating account remains unchanged, maintaining financial integrity. This critical aspect is paramount in financial applications where data accuracy and integrity are paramount.
Banking Systems
Within banking systems, Sagas are crucial for multi-step processes like loan applications. A Saga orchestrates the various tasks involved, such as credit checks, documentation verification, and approval processes. This ensures the loan application process is consistent and reliable, even when dealing with multiple external parties and systems.
Healthcare Systems
In healthcare, Sagas are valuable for processes involving multiple parties, such as insurance claims. The Saga manages the intricate steps, including data exchange between different systems and handling approvals from various entities. This facilitates a streamlined and accurate claim processing workflow.
Travel and Hospitality
Booking a complex travel package, encompassing flights, hotels, and car rentals, requires a distributed system. A Saga orchestrates the booking process across these different systems, ensuring all components are updated correctly and consistently. Failures in one aspect trigger rollbacks, ensuring a seamless and reliable booking experience.
Practical Use Cases
| Industry | Application | Saga Use Case |
|---|---|---|
| E-commerce | Order Processing | Orchestrates order placement, inventory update, payment processing, and shipping confirmation, ensuring a complete or canceled order, regardless of individual step failures. |
| Financial Services | Fund Transfer | Manages the transfer of funds between accounts, ensuring the transaction is fully completed or rolled back to the initial state if any step fails. |
| Healthcare | Insurance Claim | Facilitates the claim processing by managing the flow of data between various systems, handling approvals, and ensuring the accuracy of the entire process. |
| Travel and Hospitality | Complex Booking | Manages the booking of multiple components (flights, hotels, car rentals), guaranteeing a complete booking or a rollback to the initial state if any part fails. |
Challenges and Solutions
Implementing Sagas often involves complex error handling and recovery mechanisms. One key challenge is maintaining the consistency of data across different systems. This is addressed through careful design of compensation steps, which reverse the effects of failed steps. Another challenge is ensuring that the Saga orchestrator is robust and can handle failures gracefully. This is often achieved through distributed transaction monitoring and fault tolerance strategies.
Final Wrap-Up

In conclusion, the saga pattern offers a powerful solution for managing distributed transactions. Its ability to handle failures gracefully, through compensation and recovery mechanisms, makes it an attractive option for applications requiring high availability and resilience. While implementing sagas introduces complexity, the benefits in terms of fault tolerance and scalability often outweigh the challenges. This exploration has highlighted the key aspects of the saga pattern, enabling a deeper understanding of its potential applications in various domains.
Helpful Answers
What are the typical error scenarios encountered in Saga implementations?
Common error scenarios include failures in individual sub-transactions, network issues impacting message delivery, and issues with the saga orchestrator. Effective error handling strategies are critical to ensure consistent and reliable transaction processing.
How does the Saga pattern differ from two-phase commit?
Unlike two-phase commit, which requires all participants to be available and coordinated in a single transaction, sagas use message queues and asynchronous communication. This allows for greater resilience and scalability in the face of failures.
What are the key considerations for securing Saga interactions?
Security considerations in sagas include authentication and authorization of participating services, ensuring data integrity during message exchange, and secure storage of saga state. Appropriate security measures must be implemented at each stage to prevent unauthorized access or modification.
What are some common use cases for sagas in e-commerce?
Sagas are well-suited for e-commerce order processing, allowing for the decoupling of tasks like inventory updates, payment processing, and shipping. This decouples steps and enables independent recovery from failure. Other examples include order fulfillment and customer account management.