The integration of Amazon Simple Notification Service (SNS) with AWS Lambda represents a pivotal architecture in modern, event-driven cloud applications. This pairing facilitates message fan-out, enabling the efficient distribution of notifications and events to multiple consumers. Understanding this architecture is crucial for building scalable, resilient, and cost-effective systems that react to events in real-time. This guide provides a comprehensive exploration of this integration, detailing each component and its configuration.
SNS acts as a central hub, decoupling event producers from consumers. Lambda, a serverless compute service, allows for executing code in response to these events without managing servers. The synergy of these two services provides a robust solution for a variety of use cases, including but not limited to, application notifications, system alerts, and data processing pipelines. This analysis will delve into the practical steps, from topic creation to advanced optimization strategies, equipping readers with the knowledge to implement this powerful architecture effectively.
Introduction to SNS and Lambda Integration
Amazon Simple Notification Service (SNS) and AWS Lambda are fundamental components within the AWS ecosystem, enabling the creation of highly scalable and event-driven applications. Their integration provides a powerful mechanism for processing events asynchronously, allowing for efficient message distribution and serverless computation. This combination is particularly well-suited for scenarios requiring rapid response to events, parallel processing, and decoupled application components.
Core Concepts of Amazon SNS
Amazon SNS serves as a fully managed publish/subscribe messaging service. Its primary function is to facilitate the decoupling of applications by enabling them to send and receive messages without direct dependencies. This architecture allows for greater flexibility and scalability.
- Publishers and Subscribers: SNS operates on a publish/subscribe model. Publishers, such as applications or services, send messages to SNS topics. Subscribers, which can be various endpoints like AWS Lambda functions, email addresses, SMS numbers, or other services, then receive copies of these messages.
- Topics: Topics are logical access points and act as communication channels. Publishers send messages to topics, and SNS then distributes these messages to all subscribers of that topic. Topics provide a layer of abstraction, decoupling publishers from subscribers.
- Message Filtering: SNS supports message filtering, allowing subscribers to receive only the messages that match specific criteria. This is achieved through filtering policies, which can be defined based on message attributes. For example, a subscriber could filter messages based on the ‘severity’ attribute, receiving only those with a value of ‘critical’.
- High Availability and Durability: SNS is designed for high availability and durability. It automatically replicates messages across multiple Availability Zones within a region, ensuring that messages are not lost in the event of a failure.
Overview of AWS Lambda
AWS Lambda is a serverless compute service that enables developers to run code without provisioning or managing servers. It automatically manages the underlying infrastructure, scaling compute resources based on demand. Lambda functions are triggered by events, such as messages from SNS, HTTP requests, or changes in data storage.
- Event-Driven Execution: Lambda functions are triggered by events. When an event occurs, Lambda automatically invokes the function, executes the code, and manages the underlying compute resources. This event-driven nature is a key characteristic of serverless architectures.
- Scalability: Lambda automatically scales the execution of functions based on the number of incoming events. This eliminates the need to manually provision and manage servers, ensuring that the application can handle varying workloads.
- Pay-per-use Pricing: Lambda follows a pay-per-use pricing model. Developers are only charged for the compute time consumed by their functions, making it cost-effective for applications with fluctuating workloads.
- Supported Languages: Lambda supports a wide range of programming languages, including Node.js, Python, Java, Go, and C#. This allows developers to use the languages they are most comfortable with.
Benefits of Integrating SNS and Lambda for Message Fan-Out
The integration of SNS and Lambda provides several significant benefits for building event-driven applications. This combination is particularly effective for distributing messages to multiple consumers and processing them concurrently.
- Asynchronous Processing: SNS enables asynchronous communication between publishers and subscribers. When a message is published to an SNS topic, it is immediately available to all subscribers, even if they are temporarily unavailable. This ensures that the publisher does not need to wait for the subscriber to process the message, improving the overall responsiveness of the system.
- Parallel Processing: Lambda functions can be invoked concurrently in response to SNS messages. This allows for parallel processing of messages, significantly improving the throughput of the application.
- Decoupling of Components: The integration of SNS and Lambda promotes loose coupling between application components. Publishers do not need to know about the subscribers, and subscribers do not need to know about the publishers. This makes it easier to maintain and evolve the application.
- Scalability and Cost Efficiency: The combination of SNS and Lambda offers excellent scalability and cost efficiency. SNS handles the distribution of messages, while Lambda automatically scales the compute resources to handle the processing of those messages. This eliminates the need to provision and manage servers, reducing both operational overhead and costs.
- Real-time Applications: SNS and Lambda are well-suited for building real-time applications. For example, a real-time analytics application might use SNS to distribute data streams to multiple Lambda functions for processing and analysis. Another example could be a system monitoring application where SNS distributes alerts to different Lambda functions that perform actions based on the alert type, such as sending notifications or triggering automated remediation steps.
Setting up an SNS Topic
Creating an Amazon Simple Notification Service (SNS) topic is the foundational step for enabling message distribution to various subscribers, including AWS Lambda functions. This process involves defining the topic’s properties, access controls, and delivery settings to ensure efficient and secure communication. The following sections detail the procedures and considerations for setting up an SNS topic within the AWS environment.
Creating an SNS Topic in the AWS Management Console
The creation of an SNS topic via the AWS Management Console is a straightforward process, guided by a series of steps that configure the topic’s basic parameters.
- Navigating to the SNS Service: Access the AWS Management Console and search for “SNS” in the services search bar. Select the SNS service to navigate to the SNS dashboard.
- Initiating Topic Creation: On the SNS dashboard, click on “Topics” in the left-hand navigation pane. Then, click the “Create topic” button.
- Choosing Topic Type: Select the topic type. Standard topics support fanout scenarios and are the most commonly used for Lambda integrations. FIFO (First-In, First-Out) topics are designed for scenarios requiring message ordering, but they have limitations on subscriber types and throughput.
- Configuring Topic Details: Provide a name for the topic (e.g., “LambdaTopic”). This name must be unique within your AWS account and region. Optionally, provide a display name, which can be more descriptive and is visible to subscribers.
- Configuring Access Policy: This is a crucial step. Define the access policy to control which AWS accounts and users can publish to the topic and subscribe to it. The policy can be created using the console’s visual editor or by directly writing a JSON policy.
- Configuring Encryption: If required, enable encryption using AWS Key Management Service (KMS). Select a KMS key to encrypt the messages. This ensures that messages are encrypted both in transit and at rest.
- Configuring Delivery Settings: Configure delivery settings, such as message attributes and filtering. Message attributes allow you to include metadata with your messages, which can be used for filtering. Filtering allows subscribers to only receive messages that match specific criteria based on these attributes.
- Creating the Topic: After reviewing the configuration, click the “Create topic” button. SNS will create the topic and display its ARN (Amazon Resource Name), which is a unique identifier for the topic.
SNS Topic Access Policies
Access policies are critical for controlling who can interact with your SNS topics. These policies define permissions, ensuring only authorized entities can publish messages or subscribe to the topic. Improperly configured access policies can lead to security vulnerabilities, allowing unauthorized access or denial-of-service attacks.
There are two primary methods for configuring access policies:
- IAM Policies: Identity and Access Management (IAM) policies grant permissions to IAM users, groups, or roles to interact with SNS topics. These policies define the actions the identities are allowed to perform (e.g., `sns:Publish`, `sns:Subscribe`) and the resources they can access (the topic ARN). IAM policies are best suited for controlling access from within your AWS account.
- Topic Access Policies: Topic access policies are resource-based policies attached directly to the SNS topic. They define which AWS accounts and principals are allowed to publish and subscribe to the topic. Topic access policies are essential for cross-account communication, allowing resources in one AWS account to interact with an SNS topic in another account.
Configuring the access policy involves specifying the following:
- Effect: Determines whether the policy allows or denies access.
- Principal: Specifies the entity that the policy applies to (e.g., an IAM user, a role, or an AWS account).
- Action: Defines the actions the principal is permitted to perform (e.g., `sns:Publish`, `sns:Subscribe`, `sns:Receive`).
- Resource: Identifies the SNS topic the policy applies to (using the topic ARN).
For example, to allow an IAM user named “lambda-publisher” to publish messages to a topic, the policy would include:
"Effect": "Allow",
"Principal": "AWS": "arn:aws:iam::123456789012:user/lambda-publisher",
"Action": "sns:Publish",
"Resource": "arn:aws:sns:us-east-1:123456789012:LambdaTopic"
In the example, `123456789012` is the AWS account ID, and `us-east-1` is the AWS region. The “Principal” section specifies the IAM user who is granted permission to publish messages. It is essential to adhere to the principle of least privilege, granting only the necessary permissions to the minimum number of entities.
Customizing Topic Delivery Settings
Customizing delivery settings in SNS allows for fine-grained control over how messages are delivered to subscribers, improving efficiency and enabling more sophisticated messaging patterns. These settings are configured at the topic level and affect all subscribers unless overridden at the subscription level.
Key delivery settings include:
- Message Attributes: Message attributes are metadata that can be added to a message. They provide additional context about the message, enabling subscribers to filter messages based on these attributes. For example, you could add an attribute called “MessageType” with values like “OrderCreated” or “PaymentProcessed.”
- Message Filtering: SNS supports filtering messages based on message attributes. Subscribers can define filter policies that specify which attributes and values they are interested in. Only messages that match these filter criteria will be delivered to the subscriber. This reduces the number of messages a subscriber needs to process.
- Delivery Retry Policies: SNS uses a retry mechanism to handle delivery failures. You can configure the retry policy, including the number of retries, the delay between retries, and the backoff strategy. These settings ensure messages are delivered even in the face of transient network issues or subscriber unavailability.
- Delivery Protocols: SNS supports several delivery protocols, including HTTP/HTTPS, email, SMS, and SQS. Each protocol has its own set of delivery settings. For example, with HTTP/HTTPS, you can configure the endpoint URL and the HTTP method (e.g., POST, GET).
For instance, consider a scenario where an e-commerce platform uses SNS to notify subscribers about different events. The platform publishes messages with the following attributes:
EventType: "OrderCreated"OrderStatus: "Pending"Region: "US-East-1"
A Lambda function subscribed to the topic could set a filter policy to only receive messages where `EventType` is “OrderCreated” and `OrderStatus` is “Pending”. This ensures that the Lambda function only processes new order creation events in the “Pending” state, improving its efficiency and reducing unnecessary processing.
Subscribing a Lambda Function to an SNS Topic
Subscribing a Lambda function to an SNS topic is a crucial step in enabling event-driven architectures. This process allows the Lambda function to react to messages published to the SNS topic, facilitating asynchronous processing and decoupling of services. The following sections detail the steps required to establish this connection and configure message filtering.
Subscribing a Lambda Function Using the AWS Console or CLI
Subscribing a Lambda function to an SNS topic can be accomplished using either the AWS Management Console or the AWS Command Line Interface (CLI). Both methods offer similar functionalities, providing flexibility depending on the user’s preference and automation requirements.
- Using the AWS Console: The AWS Management Console provides a graphical user interface for subscribing a Lambda function to an SNS topic. The process involves navigating to the SNS topic, selecting the “Create Subscription” option, and then choosing “AWS Lambda” as the protocol. The user then selects the target Lambda function from a dropdown list. The console guides the user through the necessary configuration steps, including the option to define filter policies.
- Using the AWS CLI: The AWS CLI offers a programmatic approach to subscribing a Lambda function to an SNS topic. The `aws sns subscribe` command is used, specifying the topic ARN (Amazon Resource Name), the protocol as “lambda”, and the ARN of the Lambda function. This method is particularly useful for automating the subscription process within infrastructure-as-code frameworks. An example command would be:
aws sns subscribe --topic-arn arn:aws:sns:REGION:ACCOUNT_ID:TOPIC_NAME --protocol lambda --notification-endpoint arn:aws:lambda:REGION:ACCOUNT_ID:FUNCTION_NAMEWhere `REGION`, `ACCOUNT_ID`, `TOPIC_NAME`, and `FUNCTION_NAME` need to be replaced with the appropriate values.
Configuring Subscription Filter Policies
Filter policies are essential for controlling which messages are delivered to the subscribed Lambda function. By defining filter policies, users can specify criteria based on message attributes, allowing the Lambda function to process only relevant messages, thereby optimizing resource utilization and reducing processing costs.
- Message Attributes: SNS messages can contain attributes, which are key-value pairs that provide metadata about the message. Filter policies can be configured to match specific attribute values. For example, a filter policy might specify that only messages with an attribute “severity” equal to “critical” should be delivered to the Lambda function.
- Filter Policy Syntax: Filter policies are defined using JSON format. The JSON structure specifies the attributes to filter on and the conditions for matching. The conditions can include exact matching, prefix matching, numeric range matching, and existence checking.
- Example Filter Policy: Consider a scenario where a Lambda function processes log events. A filter policy could be defined to forward only events with a “logLevel” attribute set to “ERROR” or “CRITICAL”. The following JSON demonstrates this:
"logLevel": ["ERROR", "CRITICAL"]
Granting Necessary Permissions for SNS to Invoke the Lambda Function
To enable SNS to invoke the Lambda function, the appropriate permissions must be granted. This involves configuring an IAM (Identity and Access Management) policy that allows the SNS service to execute the Lambda function.
- IAM Role for Lambda Function: The Lambda function requires an IAM role that grants it permissions to execute and access other AWS resources. This role also needs to include a policy that allows SNS to invoke the function.
- IAM Policy for SNS: An IAM policy must be attached to the Lambda function’s execution role. This policy should include a statement that allows the SNS service to invoke the Lambda function. The policy statement should specify the function’s ARN and the `lambda:InvokeFunction` action.
- Example IAM Policy Statement: The following JSON snippet shows an example of a policy statement that grants SNS permission to invoke a Lambda function:
"Sid": "AllowSNSToInvokeLambda",
"Effect": "Allow",
"Principal":
"Service": "sns.amazonaws.com"
,
"Action": "lambda:InvokeFunction",
"Resource": "arn:aws:lambda:REGION:ACCOUNT_ID:function:FUNCTION_NAME"This policy should be added to the Lambda function’s resource-based policy.
Writing the Lambda Function Code
The Lambda function serves as the computational engine that processes messages published to the SNS topic. This section delves into the creation of Python code specifically designed to interact with SNS messages, handling various message formats, and implementing error management strategies. The following sections provide a comprehensive overview of writing effective Lambda functions for SNS integration.
Python Code for Lambda Function
The core of the Lambda function lies in its Python code. This code is responsible for receiving messages from SNS, parsing them, and performing the intended actions. Below is a Python code snippet demonstrating a basic Lambda function that processes SNS messages. This example assumes that the Lambda function is triggered by an SNS event.“`pythonimport jsonimport boto3def lambda_handler(event, context): “”” Lambda function to process SNS messages.
Args: event (dict): Event data from SNS. context (object): Lambda context object. Returns: dict: Success or failure message. “”” try: for record in event[‘Records’]: sns = record[‘Sns’] message = sns[‘Message’] subject = sns[‘Subject’] print(f”Message Subject: subject”) print(f”Message Body: message”) # Process the message based on its content # Example: If the message is JSON, parse it try: message_data = json.loads(message) print(f”Parsed JSON Data: message_data”) # Perform actions with the parsed data except json.JSONDecodeError: print(“Message is not valid JSON.”) # Handle non-JSON messages appropriately return ‘statusCode’: 200, ‘body’: json.dumps(‘Message processed successfully!’) except Exception as e: print(f”An error occurred: e”) return ‘statusCode’: 500, ‘body’: json.dumps(f’Error processing message: str(e)’) “`This code retrieves the message and subject from the SNS event and prints them to the CloudWatch logs.
It also includes a basic attempt to parse the message as JSON.
Handling Different Message Formats and Payloads
SNS messages can be in various formats, including plain text, JSON, or even binary data. The Lambda function must be designed to handle these diverse formats effectively. A critical aspect of handling different formats is determining the message’s type and parsing it accordingly.
- Plain Text: Plain text messages can be directly processed. The Lambda function can extract and utilize the text content. For example, a notification service might send a plain text message containing an alert.
- JSON: JSON is a common format for structured data. The Lambda function can use the `json.loads()` function in Python to parse JSON messages. This allows for easy access to the message’s data fields. For instance, an IoT device might send a JSON message containing sensor readings.
- Binary Data: Binary data requires more sophisticated handling. The Lambda function might need to decode the data using a specific library, depending on the format. Base64 encoding is often used to represent binary data in SNS messages. A Lambda function might then decode the Base64 string. For example, image or audio files can be sent.
The function must include conditional logic to determine the message type and parse it accordingly. This involves checking the message’s content type or using a regular expression to identify the format. The example code includes a basic attempt to parse a JSON message. If the parsing fails, it logs an error and handles the non-JSON message appropriately.
Error Handling Mechanism within the Lambda Function
Robust error handling is crucial for any Lambda function. This is particularly true when dealing with external services like SNS, where failures can occur due to network issues, invalid message formats, or service outages. Implementing a proper error handling mechanism is necessary to maintain the reliability of the system.
- Try-Except Blocks: Using `try-except` blocks is fundamental. The code that interacts with SNS and processes messages should be enclosed within a `try` block. The `except` block should catch potential exceptions, such as `json.JSONDecodeError` (if parsing JSON fails), `boto3.exceptions.ClientError` (if there are issues with AWS services), or other relevant exceptions.
- Logging: Logging is essential for debugging and monitoring. Error messages should be logged to CloudWatch, including detailed information about the error, such as the message that caused the error, the time of the error, and the error type. This information is invaluable for troubleshooting and identifying the root cause of failures.
- Retry Mechanisms: For transient errors (e.g., temporary network issues), retry mechanisms can be implemented. The Lambda function can attempt to process the message multiple times, with increasing delays between retries. AWS SDKs often include built-in retry mechanisms.
- Dead-Letter Queues (DLQs): For messages that cannot be processed after multiple retries, DLQs provide a way to store them for later analysis. DLQs can be configured with SNS subscriptions or with Lambda function settings. When a message fails to process, it can be sent to the DLQ for inspection.
The example code includes a `try-except` block to catch exceptions and print error messages. This provides a basic level of error handling. More sophisticated error handling can include sending error notifications to an administrator or storing failed messages in a DLQ for later review. Implementing comprehensive error handling helps ensure that the Lambda function remains resilient to failures and that important messages are not lost.
Message Formatting and Structure
Understanding the structure of messages relayed from Simple Notification Service (SNS) to AWS Lambda functions is crucial for effective event-driven architectures. This involves not only knowing the message content itself but also the accompanying metadata that provides context and control. Correctly parsing and utilizing this information enables Lambda functions to process SNS notifications reliably and efficiently.
SNS Message Structure
The messages delivered by SNS to a Lambda function are formatted as JSON documents. These documents contain both the actual message body and metadata about the message and the notification itself. This structure allows the Lambda function to determine the source, the type of event, and the content of the message.The basic structure of an SNS message payload includes the following key components:
- Records: This is an array containing one or more message records. Even if only a single message is sent, it’s encapsulated within a ‘Records’ array. This design accommodates future scenarios where SNS might batch messages.
- SNS: This object contains metadata about the SNS notification.
- Message: The core content of the notification. This can be a string, a JSON object, or any other data type supported by SNS, depending on the message’s original format.
- MessageId: A unique identifier for the SNS message.
- TopicArn: The Amazon Resource Name (ARN) of the SNS topic that published the message.
- Timestamp: The time when the message was published.
- Type: The type of notification. Typically, this is “Notification”.
- UnsubscribeURL: A URL that, when accessed, will unsubscribe the Lambda function from the SNS topic.
- SignatureVersion: The version of the signature used to sign the message.
- Signature: The digital signature of the message, used to verify its authenticity.
- SigningCertURL: The URL of the certificate used to sign the message.
- Subject (optional): The subject line of the notification, if one was provided when the message was published to SNS.
Message Format Examples and Parsing
SNS supports a variety of message formats. The most common is JSON, which allows for complex data structures. Understanding how to parse these formats within the Lambda function is essential for extracting and utilizing the message data.Here’s an example of a JSON message format sent from SNS to a Lambda function and how to parse it using Python:“`json “Records”: [ “EventSource”: “aws:sns”, “EventVersion”: “1.0”, “EventSubscriptionArn”: “arn:aws:sns:REGION:ACCOUNT_ID:TOPIC_NAME:SUBSCRIPTION_ID”, “Sns”: “Type”: “Notification”, “MessageId”: “MESSAGE_ID”, “TopicArn”: “arn:aws:sns:REGION:ACCOUNT_ID:TOPIC_NAME”, “Subject”: “Optional Subject”, “Message”: “\”key1\”:\”value1\”, \”key2\”:\”value2\””, “Timestamp”: “YYYY-MM-DDTHH:MM:SS.SSSZ”, “SignatureVersion”: “1”, “Signature”: “SIGNATURE”, “SigningCertUrl”: “URL”, “UnsubscribeUrl”: “URL”, “MessageAttributes”: ]“`The following Python code demonstrates how to parse the JSON message and extract the message content and metadata:“`pythonimport jsondef lambda_handler(event, context): for record in event[‘Records’]: sns = record[‘Sns’] message = sns[‘Message’] message_id = sns[‘MessageId’] topic_arn = sns[‘TopicArn’] try: # Attempt to parse the message as JSON message_body = json.loads(message) print(f”Message ID: message_id”) print(f”Topic ARN: topic_arn”) print(f”Message Body (JSON): message_body”) # Accessing specific values in the JSON message if ‘key1’ in message_body: print(f”Value of key1: message_body[‘key1’]”) except json.JSONDecodeError: # If the message is not JSON, treat it as a string print(f”Message ID: message_id”) print(f”Topic ARN: topic_arn”) print(f”Message Body (String): message”) return ‘statusCode’: 200, ‘body’: ‘Message processed successfully’ “`In this example, the code first iterates through the ‘Records’ array.
Then, it accesses the ‘Sns’ object to retrieve the message details. The code attempts to parse the ‘Message’ field as JSON using `json.loads()`. If successful, it accesses the key-value pairs within the JSON object. If parsing fails (i.e., the message is not valid JSON), it catches the `json.JSONDecodeError` exception and treats the message as a plain string.
Data Structure for Multiple Messages
SNS can deliver multiple messages to a Lambda function in a single invocation. This is particularly useful for batch processing and improving efficiency. Understanding how to handle an array of messages is critical for processing these batched events.The data structure provided by SNS to the Lambda function is an array of ‘Records’. Each record represents a single message published to the SNS topic.
The Lambda function iterates through this array to process each message individually.Here’s how to structure your Lambda function to handle multiple messages:“`pythonimport jsondef lambda_handler(event, context): for record in event[‘Records’]: try: sns = record[‘Sns’] message = sns[‘Message’] message_id = sns[‘MessageId’] topic_arn = sns[‘TopicArn’] # Process each message message_body = json.loads(message) print(f”Message ID: message_id”) print(f”Topic ARN: topic_arn”) print(f”Message Body (JSON): message_body”) # Process the data within the message_body as needed except json.JSONDecodeError: print(f”Message Body (String): message”) # Handle non-JSON messages except Exception as e: print(f”Error processing message: e”) return ‘statusCode’: 200, ‘body’: ‘Messages processed successfully’ “`This example iterates through the ‘Records’ array, extracts the message content and metadata for each record, and processes it.
The try-except blocks handle potential errors during JSON parsing or processing of individual messages, ensuring that the function does not fail completely if one message is malformed. By handling multiple messages within a single invocation, the Lambda function can significantly reduce the overhead of function invocations and improve overall performance. This approach is particularly beneficial when processing large volumes of data or events.
Filtering Messages with SNS
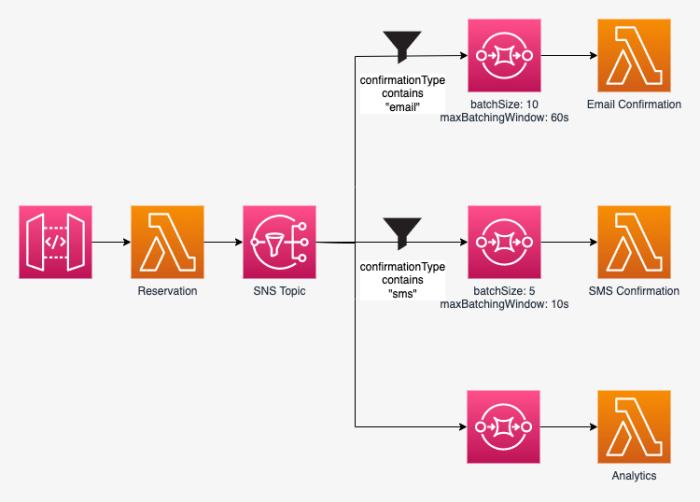
SNS message filtering provides a mechanism to selectively route messages published to a topic to specific subscribers, such as Lambda functions. This capability enhances the efficiency and cost-effectiveness of event-driven architectures by ensuring that only relevant messages trigger function executions, avoiding unnecessary processing and resource consumption. Filter policies, defined at the subscription level, dictate which messages are delivered based on their attributes.
Filtering Logic and Attribute-Based Filtering
Filter policies leverage message attributes to determine whether a message should be delivered to a subscriber. These attributes are key-value pairs included within the message payload. When a message is published to an SNS topic, the service evaluates the message attributes against the filter policies configured on each subscription. If a message matches the filter policy, it is delivered to the subscriber; otherwise, it is discarded.To illustrate this, consider a scenario involving an e-commerce platform that publishes order events to an SNS topic.
Different Lambda functions might be responsible for handling different order types (e.g., new orders, cancelled orders, shipped orders). The order events could include attributes such as `order_type` and `order_status`.The following examples demonstrate filter policies:* Filter Policy for New Orders: A Lambda function responsible for processing new orders could have a filter policy that specifies: “`json “order_type”: [“new”] “` This policy ensures that only messages with the attribute `order_type` set to the value `”new”` are delivered to the function.* Filter Policy for Shipped Orders: A separate Lambda function, potentially responsible for sending shipping notifications, might have a filter policy: “`json “order_status”: [“shipped”] “` This policy ensures that only messages with the attribute `order_status` set to `”shipped”` trigger the function.* Filter Policy Using Wildcards: SNS supports wildcard matching within filter policies.
This enables more flexible filtering based on patterns. For instance, a function could be designed to handle any order status updates: “`json “order_status”: [“shipped”, “delivered”, “cancelled”] “` This filter policy will deliver messages to the Lambda function if the `order_status` attribute has any of the specified values.
Configuring Filter Policies with Multiple Criteria
Filter policies can also be configured to handle multiple criteria, allowing for more complex filtering logic. This is achieved by specifying multiple attributes and their associated values within the filter policy. SNS evaluates these policies using logical AND and OR operations, depending on how the attributes are structured.* Logical AND Example: Suppose a Lambda function needs to be triggered only for high-value orders that are also shipped.
The filter policy might look like this: “`json “order_status”: [“shipped”], “order_value”: [ “numeric”: [“>”, 1000] ] “` This policy will only deliver messages if the `order_status` is `”shipped”` AND the `order_value` is greater than 1000.
The `numeric` attribute allows for comparison operations such as `>`, ` <`, `=`, `>=`, and `<=`.* Logical OR Example (Implicit): While SNS doesn’t explicitly support an OR operator in the same way as AND, you can achieve a similar result by using multiple values for a single attribute, as demonstrated in the wildcard example. “`json “order_status”: [“shipped”, “delivered”] “` This policy delivers messages if `order_status` is either `”shipped”` OR `”delivered”`.* Advanced Filtering with Arrays: Filter policies can also work with array values.
For example, to filter messages where the `product_categories` attribute contains “electronics” or “books”: “`json “product_categories”: [“electronics”, “books”] “` This policy triggers the Lambda function if the `product_categories` attribute includes either of the specified values.By leveraging these filtering capabilities, developers can create highly efficient and targeted event-driven architectures, reducing unnecessary resource consumption and streamlining the processing of messages within their applications.
Error Handling and Retries
Effective error handling and robust retry mechanisms are crucial for building resilient and reliable systems when integrating Amazon Simple Notification Service (SNS) with AWS Lambda functions. These mechanisms ensure that messages are processed successfully, even in the face of transient failures or intermittent service disruptions. This section delves into the built-in and customizable error handling strategies available within the SNS-Lambda integration.
Built-in Error Handling in Lambda and SNS
Lambda and SNS provide several built-in mechanisms to handle errors and manage retries, minimizing data loss and ensuring eventual consistency. Understanding these built-in features is the first step toward building a resilient system.
- Lambda’s Automatic Retries: By default, Lambda automatically retries a failed function invocation. The retry behavior depends on the invocation type. For asynchronous invocations (triggered by SNS), Lambda retries the function twice with an exponential backoff strategy. This means that the time between retries increases, allowing for transient issues to resolve before the function is retried. The total time the function can run, including retries, is limited by the Lambda function’s timeout setting.
- SNS’s Delivery Retry Policies: SNS offers built-in delivery retry policies that control how SNS attempts to deliver messages to subscribed endpoints, including Lambda functions. SNS uses a backoff strategy to retry failed deliveries. The default retry policy attempts delivery for a period of time, with the specific duration configurable. The default retry policy is designed to handle common, temporary issues.
- Error Reporting: Both Lambda and SNS provide error reporting mechanisms through AWS CloudWatch. Lambda logs function execution details, including errors, to CloudWatch Logs. SNS also logs delivery attempts and failures, which can be monitored through CloudWatch. This allows for centralized monitoring and debugging of message delivery issues.
Configuring Retry Policies in SNS
SNS retry policies are configurable to optimize message delivery based on the specific requirements of the application. Proper configuration can prevent excessive retries and potential message duplication, or, conversely, ensure that messages are delivered despite temporary disruptions.
- Configurable Parameters: SNS retry policies can be configured to adjust several parameters, including:
- Delivery Attempts: Specifies the maximum number of delivery attempts.
- Minimum Backoff Delay: Sets the minimum delay (in seconds) between retry attempts.
- Maximum Backoff Delay: Sets the maximum delay (in seconds) between retry attempts.
- Backoff Rate: Defines the rate at which the delay between retries increases (exponential backoff).
- Accessing and Modifying Retry Policies: Retry policies can be accessed and modified through the AWS Management Console, the AWS Command Line Interface (CLI), or the AWS SDKs. Configuration is done at the subscription level, allowing for different retry policies for different Lambda function subscriptions to the same SNS topic.
- Example Scenario: Consider a system that processes financial transactions. If a Lambda function fails to process a transaction message due to a temporary network issue, the default retry policy might not be sufficient. In this case, the retry policy can be configured to increase the number of delivery attempts and the maximum backoff delay to accommodate the intermittent network connectivity. This ensures a higher probability of the transaction being processed successfully.
Implementing Custom Error Handling and Logging in Lambda
While built-in error handling provides a baseline level of resilience, custom error handling and logging within the Lambda function are crucial for more granular control, improved debugging, and better visibility into the message processing workflow.
- Catching Exceptions: Implement `try…except` blocks to catch specific exceptions that might occur during message processing. This allows the Lambda function to handle errors gracefully, such as by logging the error, performing alternative actions, or attempting to retry the operation within the function.
- Logging: Implement comprehensive logging using a logging library (e.g., the Python `logging` module, or the Node.js `console` object). Log important information, including:
- Incoming message details (e.g., message ID, timestamp).
- The start and end of message processing.
- Any errors that occur, including the exception type and traceback.
- Key processing steps and their results.
- Dead-Letter Queues (DLQs): Configure a DLQ (e.g., an Amazon SQS queue) for the Lambda function. When a message fails to be processed after all retries (both Lambda’s and SNS’s), the message is sent to the DLQ. This allows for:
- Investigation: Analyzing the failed messages to identify the root cause of the failure.
- Recovery: Manually reprocessing the messages or implementing automated recovery strategies.
- Monitoring and Alerting: Set up CloudWatch alarms to monitor key metrics, such as the number of errors, the number of messages in the DLQ, and the function’s invocation duration. Configure these alarms to trigger notifications (e.g., through SNS or email) when certain thresholds are exceeded. This provides proactive alerting and enables quick response to issues.
- Idempotency: Implement idempotent processing to handle potential message duplication, particularly if the Lambda function is retried. Idempotency ensures that processing the same message multiple times has the same effect as processing it once. This can be achieved by:
- Checking for existing records: Before processing a message, check if it has already been processed (e.g., by checking a database for a record with the same message ID).
- Using unique identifiers: Generate unique identifiers for each message and use them to ensure that the processing logic is idempotent.
Monitoring and Logging
Effective monitoring and logging are crucial for maintaining the health and performance of an SNS-Lambda integration. They provide insights into message flow, identify potential bottlenecks, and facilitate rapid debugging in case of issues. CloudWatch offers comprehensive tools for monitoring both SNS and Lambda, while logging within the Lambda function itself is essential for detailed auditing and troubleshooting.
Monitoring SNS and Lambda Performance with CloudWatch
CloudWatch allows for the comprehensive monitoring of SNS and Lambda services. It provides various metrics and tools to observe the behavior of these services, helping to identify performance issues and optimize resource utilization.To monitor SNS:
- Topic Metrics: CloudWatch provides metrics for SNS topics, including:
NumberOfMessagesPublished: The number of messages published to the topic.NumberOfNotificationsDelivered: The number of messages successfully delivered to subscribers.NumberOfNotificationsFailed: The number of messages that failed to be delivered.PublishSize: The size of the messages published to the topic in bytes.Throttled: The number of publish requests throttled due to rate limits.
These metrics help to assess the volume of messages, delivery success rates, and potential throttling issues.
- Subscription Metrics: For each subscription, CloudWatch offers metrics like:
DeliverySuccessful: The number of successful deliveries to the subscription endpoint.DeliveryFailed: The number of failed deliveries to the subscription endpoint.ApproximateAgeOfOldestMessage: The approximate age of the oldest message in the subscription’s queue (relevant for services like SQS).
These metrics help to track the delivery success and identify potential issues with specific subscribers.
To monitor Lambda:
- Invocation Metrics: CloudWatch provides several key metrics for Lambda functions:
Invocations: The number of times the function was invoked.Errors: The number of function invocations that resulted in errors.Throttles: The number of times the function was throttled.Duration: The amount of time the function took to execute.ConcurrentExecutions: The number of concurrent function executions.
These metrics provide insights into function performance, error rates, and resource utilization.
- Error Metrics: CloudWatch also tracks errors in Lambda functions. Monitoring error metrics allows for early detection of issues.
Setting Up CloudWatch Alarms for Specific Metrics
CloudWatch alarms automatically monitor metrics and trigger actions based on predefined thresholds. This enables proactive issue detection and automated responses.Setting up alarms for SNS:
- Alarm for Failed Deliveries: Create an alarm on the
NumberOfNotificationsFailedmetric for an SNS topic. Configure the alarm to trigger if the number of failed deliveries exceeds a specific threshold over a certain period. This helps to identify issues with subscribers or message delivery. - Alarm for Throttling: Monitor the
Throttledmetric. An alarm can be set to notify when the number of throttled requests exceeds a threshold, indicating a need to increase throughput or optimize message publishing.
Setting up alarms for Lambda:
- Alarm for Errors: Set an alarm on the
Errorsmetric. Configure the alarm to trigger if the number of errors exceeds a threshold. This immediately alerts when function execution fails. - Alarm for Duration: Monitor the
Durationmetric. Create an alarm to trigger if the average function duration exceeds a predefined threshold. This helps to identify performance degradation or code inefficiencies. - Alarm for Throttles: Set an alarm on the
Throttlesmetric. This is important for detecting when the Lambda function is being throttled due to insufficient concurrency.
The process involves defining the metric to monitor, the statistic (e.g., Average, Sum, Maximum), the period (e.g., 1 minute, 5 minutes), the threshold, and the action to take when the alarm state changes (e.g., sending an email notification, triggering an automated remediation process).
Implementing Logging Within the Lambda Function
Effective logging within the Lambda function is critical for debugging and auditing. It provides detailed information about the execution of the function, including inputs, outputs, and any errors encountered.Best practices for Lambda function logging:
- Use a structured logging format: Use a structured logging format such as JSON to make logs easily searchable and analyzable.
- Log key events: Log important events such as function invocations, message processing start and end times, and any errors or exceptions.
- Include relevant context: Include context information such as the message ID, the event source (SNS topic ARN), and any other relevant data to aid in debugging.
- Use different log levels: Utilize different log levels (e.g., DEBUG, INFO, WARNING, ERROR) to categorize log messages and control the verbosity of logging. For example,
console.log("INFO: Message processed successfully")orconsole.error("ERROR: Failed to process message"). - Handle sensitive data carefully: Avoid logging sensitive data, such as passwords or API keys. Consider masking sensitive information.
Example of logging within a Lambda function (Node.js):“`javascriptconst AWS = require(‘aws-sdk’);const sns = new AWS.SNS();exports.handler = async (event) => try console.log(`INFO: Event received: $JSON.stringify(event)`); // Log the entire event for debugging const message = JSON.parse(event.Records[0].Sns.Message); console.log(`INFO: Processing message: $JSON.stringify(message)`); // Log the parsed message // Process the message…
const result = await processMessage(message); console.log(`INFO: Message processed successfully. Result: $JSON.stringify(result)`); return statusCode: 200, body: JSON.stringify( message: ‘Message processed successfully’ ), ; catch (error) console.error(`ERROR: Error processing message: $error.message`); console.error(`ERROR: Stack trace: $error.stack`); // Log the stack trace for detailed debugging return statusCode: 500, body: JSON.stringify( message: ‘Error processing message’ ), ; ;async function processMessage(message) // Simulate processing return new Promise((resolve, reject) => setTimeout(() => if (Math.random() < 0.1) // Simulate a 10% failure rate reject(new Error("Simulated processing failure")); else resolve( status: "success", processedMessage: message ); , 100); // Simulate some processing time );```This example demonstrates logging the event, parsing the message, and logging the result or any errors. The use of `console.log` and `console.error` allows CloudWatch Logs to capture these events. The inclusion of the stack trace in the error logging provides detailed information for debugging.
Security Considerations
Securing SNS topics and Lambda functions is paramount to protecting sensitive data and ensuring the integrity of your message-driven architecture.
A robust security strategy encompasses access control, encryption, and monitoring to mitigate potential threats. Neglecting security can lead to unauthorized access, data breaches, and service disruptions.
IAM Roles and Permissions for Access Control
IAM (Identity and Access Management) roles and permissions are the cornerstone of access control within AWS. They define who can access which resources and what actions they are permitted to perform.To establish effective access control, consider the following:
- Principle of Least Privilege: Grant only the necessary permissions to each IAM role. Avoid overly permissive policies that could inadvertently expose resources. For example, a Lambda function subscribing to an SNS topic should only have permissions to receive messages from that specific topic and execute its code.
- IAM Roles for Lambda Functions: Each Lambda function should assume an IAM role that grants it the necessary permissions. This role should include permissions to:
- Receive messages from the SNS topic (
sns:Receive). - Log events to CloudWatch (
logs:CreateLogGroup,logs:CreateLogStream,logs:PutLogEvents). - Access any other AWS resources required by the function’s logic (e.g., DynamoDB tables, S3 buckets).
- Receive messages from the SNS topic (
- SNS Topic Access Policies: Configure SNS topic access policies to control who can publish messages to the topic and who can subscribe to it. These policies should restrict access to only authorized publishers and subscribers. An example of an SNS topic access policy is:
"Version": "2012-10-17", "Statement": [ "Effect": "Allow", "Principal": "AWS": "arn:aws:iam::123456789012:role/PublisherRole" , "Action": "SNS:Publish", "Resource": "arn:aws:sns:us-east-1:123456789012:MyTopic" , "Effect": "Allow", "Principal": "AWS": "arn:aws:iam::123456789012:role/LambdaFunctionRole" , "Action": "SNS:Subscribe", "Resource": "arn:aws:sns:us-east-1:123456789012:MyTopic" ]
- Least Privileged Access for Publishers: The IAM role used by message publishers (e.g., applications or services) should have limited permissions, allowing only publishing actions (
sns:Publish) to the specific SNS topic. This prevents accidental or malicious modification of other resources.
Encryption of Messages at Rest and In Transit
Encryption protects sensitive data from unauthorized access, both when it is stored (at rest) and when it is being transmitted (in transit). AWS provides several mechanisms to encrypt messages in SNS and Lambda.
Here’s how to implement encryption:
- Encryption at Rest for SNS Topics: Enable encryption for SNS topics using AWS Key Management Service (KMS). This ensures that messages stored within the SNS topic are encrypted with a KMS key.
- Create a KMS key. The KMS key is a unique identifier for the encryption.
- Configure the SNS topic to use the KMS key. This is done during topic creation or modification.
- Encryption in Transit: SNS automatically encrypts messages in transit using TLS (Transport Layer Security) when communicating with subscribers. This protects the data during its journey from the SNS topic to the Lambda function.
- Message Encryption within Lambda Function: If the message payload contains sensitive information, consider encrypting the message payload before publishing it to SNS. The Lambda function can then decrypt the payload upon receiving the message.
- Utilize encryption libraries within the Lambda function. Libraries like the AWS Encryption SDK can be used to encrypt and decrypt data.
- Manage the KMS key used for encryption securely, using IAM roles and access control policies.
- Example Scenario: A financial institution uses SNS and Lambda to process transaction notifications. To secure the data, they encrypt the transaction details before publishing them to SNS. The Lambda function, using its assigned IAM role, decrypts the transaction details upon receiving the message, processes the data, and then encrypts the results before storing them in a database. This end-to-end encryption strategy minimizes the risk of data breaches.
Advanced Use Cases and Optimizations
SNS-to-Lambda integration provides a robust framework for various advanced applications, extending beyond simple message forwarding. These advanced use cases often involve complex event processing and data transformation, demanding careful consideration of performance and cost optimization strategies. Effective utilization of these strategies allows for scalable and cost-efficient architectures.
Event Processing and Data Transformation
The SNS-to-Lambda integration facilitates complex event processing workflows. Lambda functions, triggered by SNS messages, can perform various data transformations and manipulations.
Consider a scenario where an e-commerce platform uses SNS to notify Lambda functions about order events. These events might include order creation, payment confirmation, shipment updates, and order cancellation. Lambda functions can then be designed to:
- Data Enrichment: Enrich order data by retrieving customer information from a database or calling external APIs to get product details.
- Data Validation: Validate order data to ensure data integrity and accuracy, checking for inconsistencies or missing information.
- Data Aggregation: Aggregate order data for real-time dashboards and reporting. This could involve summarizing sales figures, calculating average order values, and tracking popular products.
- Data Transformation: Transform order data into different formats suitable for downstream systems. For instance, converting order data into CSV or JSON formats for analytics or integration with other services.
- Real-time Notifications: Send real-time notifications to customers about order status updates via SMS or email.
This architecture allows for decoupling of event producers (e.g., the e-commerce platform) from event consumers (e.g., analytics dashboards, notification services). This decoupling enhances scalability, maintainability, and fault tolerance.
Message Processing Patterns
Different message processing patterns can be employed to optimize the performance and cost-effectiveness of SNS-to-Lambda integrations. The choice of pattern depends on factors like message volume, processing complexity, and latency requirements.
- Single Message Processing: Each SNS message triggers a single Lambda function invocation. This is the simplest approach, suitable for low-volume scenarios or where individual message processing is critical.
- Batch Processing: Lambda functions can be configured to receive batches of SNS messages. This significantly reduces the number of function invocations and associated overhead, such as cold starts. Batching is particularly effective for high-volume scenarios where the processing of individual messages can be performed concurrently within the Lambda function. AWS Lambda supports batching up to a maximum of 10,000 messages or a payload size of 6 MB.
This allows for processing large volumes of messages with greater efficiency.
- Fan-out with Multiple Lambda Functions: SNS can fan out messages to multiple Lambda functions simultaneously. This allows for parallel processing of messages and enables the creation of complex event-driven architectures. For example, one Lambda function might be responsible for logging events, another for sending notifications, and a third for updating a database.
The following table summarizes the trade-offs between these processing patterns:
| Processing Pattern | Advantages | Disadvantages | Best Use Cases |
|---|---|---|---|
| Single Message Processing | Simplicity, Low latency for individual messages | High invocation overhead, Inefficient for high message volumes | Low-volume scenarios, critical individual message processing |
| Batch Processing | Reduced invocation overhead, Improved cost efficiency | Increased latency for individual messages, Potential for processing failures to affect multiple messages | High-volume scenarios, Batch-oriented processing tasks |
| Fan-out with Multiple Lambda Functions | Parallel processing, Scalability, Decoupling | Increased complexity, Potential for message duplication or ordering issues | Complex event-driven architectures, Parallel processing of different event streams |
Performance and Cost Optimization
Optimizing the performance and cost of SNS-to-Lambda integrations is crucial for achieving scalability and efficiency. Several strategies can be employed to achieve these goals.
- Batching: As previously mentioned, batching SNS messages significantly reduces the number of Lambda invocations and associated costs.
- Lambda Function Memory Allocation: Carefully consider the memory allocation for Lambda functions. Allocate only the necessary memory to avoid overpaying for compute resources. Monitor the function’s memory utilization using CloudWatch metrics.
- Lambda Function Duration: Optimize Lambda function code to minimize execution time. Shorter execution times result in lower compute costs. Optimize the code by improving performance by using efficient algorithms and data structures.
- Provisioned Concurrency: For critical applications with low-latency requirements, consider using provisioned concurrency. This ensures that Lambda functions are always initialized and ready to serve requests, minimizing cold start times. Provisioned concurrency incurs additional costs but can be essential for performance-sensitive applications.
- Dead-Letter Queues (DLQs): Implement DLQs to handle failed message processing attempts. This prevents messages from being lost and allows for debugging and reprocessing of failed messages. DLQs can be implemented by configuring the Lambda function to send failed events to an SQS queue or another SNS topic.
- Filtering: Leverage SNS message filtering to reduce the number of messages that are delivered to Lambda functions. This reduces the workload on the Lambda functions and associated costs.
- Monitoring and Alerting: Implement comprehensive monitoring and alerting using CloudWatch metrics and alarms. Monitor key metrics such as invocation count, error rate, and execution time. Set up alerts to proactively identify and address performance issues or cost anomalies.
By implementing these optimizations, organizations can significantly reduce the cost and improve the performance of their SNS-to-Lambda integrations, creating scalable and cost-effective event-driven architectures.
Last Word
In conclusion, the utilization of SNS for message fan-out to Lambda functions provides a powerful and flexible approach to building event-driven architectures. Through careful consideration of topic configuration, subscription management, message formatting, and error handling, developers can create systems that are highly scalable and responsive. By implementing best practices in security, monitoring, and optimization, the full potential of this integration can be realized, leading to more efficient and resilient cloud applications.
The ability to distribute messages to various consumers with ease and efficiency underscores the value of this integration in modern cloud computing environments.
Question Bank
What is the maximum message size that SNS can send to Lambda?
SNS messages can be up to 256 KB in size. However, it is important to consider Lambda’s payload size limits, which can vary depending on the invocation type. For synchronous invocations, the payload size limit is smaller than for asynchronous invocations.
How does SNS handle message delivery failures to Lambda?
SNS employs a retry mechanism for message delivery failures. By default, SNS retries message delivery several times. You can configure the retry policy, including the number of retries and the backoff strategy, within the SNS topic settings. Additionally, Lambda provides error handling capabilities, including dead-letter queues, to manage failed invocations.
Can I filter messages based on multiple criteria?
Yes, SNS allows for complex message filtering based on multiple attributes. You can define filter policies that specify multiple criteria using various operators (e.g., ‘equals’, ‘startsWith’, ‘contains’) and logical operators (e.g., ‘AND’, ‘OR’). This flexibility enables precise routing of messages to different Lambda functions based on their content.
How can I monitor the performance of the SNS-to-Lambda integration?
You can monitor the performance of SNS and Lambda using Amazon CloudWatch. CloudWatch provides metrics for SNS, such as message publishes, deliveries, and errors, as well as metrics for Lambda, such as invocation counts, errors, and duration. You can also set up CloudWatch alarms to be notified of issues, such as high error rates or long invocation times.