Embarking on a cloud security audit can seem daunting, but with the right preparation, it becomes a manageable and even beneficial process. This guide provides a structured approach to help you navigate the complexities of cloud security audits, ensuring your organization’s data and infrastructure are protected. We’ll delve into the critical steps, from understanding the audit process to implementing post-audit remediation, equipping you with the knowledge to confidently face any cloud security audit.
This guide breaks down the process into manageable segments. We will explore defining the scope of the audit, preparing the necessary documentation and technical controls, conducting risk assessments, and considering the specific requirements of your cloud provider. Furthermore, we will discuss crucial aspects such as data protection, access control, security policies, communication strategies, and post-audit activities. Each section offers practical advice and actionable steps to ensure a successful audit outcome.
Understanding the Cloud Security Audit Process
A cloud security audit is a comprehensive assessment of an organization’s cloud infrastructure, security posture, and compliance with relevant standards and regulations. This process helps identify vulnerabilities, assess risks, and ensure that cloud resources are adequately protected. Understanding the different phases, roles, and timelines involved is crucial for effective preparation.
Phases of a Cloud Security Audit
The cloud security audit process typically involves several distinct phases, each with its own objectives and activities. Understanding these phases allows for a structured and organized approach to the audit.
- Planning and Preparation: This initial phase involves defining the scope of the audit, identifying the systems and data to be assessed, and selecting the appropriate audit methodologies. It also includes gathering relevant documentation, such as cloud configuration settings, security policies, and incident response plans. The audit team defines the audit objectives and the criteria against which the cloud environment will be evaluated.
This phase is critical for setting the stage for a successful audit.
- Information Gathering and Assessment: In this phase, the audit team collects information about the cloud environment. This may involve reviewing documentation, interviewing personnel, and conducting technical assessments, such as vulnerability scans and penetration tests. The team analyzes the collected information to identify potential security risks and vulnerabilities. This phase requires a deep understanding of the cloud environment and the security controls in place.
- Vulnerability Analysis and Risk Assessment: The audit team analyzes the findings from the information-gathering phase to identify vulnerabilities and assess the associated risks. This includes evaluating the likelihood of a vulnerability being exploited and the potential impact of such an event. Risk assessments are often prioritized based on the severity of the identified risks. The output of this phase is a prioritized list of vulnerabilities and their associated risks.
- Reporting and Remediation Recommendations: The audit team prepares a detailed report summarizing the audit findings, including identified vulnerabilities, risk assessments, and recommendations for remediation. The report is typically provided to the organization’s management and relevant stakeholders. The recommendations should be specific, actionable, and prioritized based on the identified risks.
- Remediation and Follow-up: The organization implements the remediation recommendations provided in the audit report. This may involve patching vulnerabilities, configuring security controls, and updating security policies. The audit team may conduct follow-up assessments to verify that the remediation efforts have been successful. This phase ensures that the identified vulnerabilities are addressed and the cloud environment is secured.
Roles and Responsibilities in a Cloud Security Audit
Cloud security audits involve various roles, each with specific responsibilities. Clear definition of these roles ensures a well-coordinated and effective audit process.
- Auditor: The auditor is responsible for conducting the audit, gathering evidence, analyzing findings, and preparing the audit report. They must possess expertise in cloud security, compliance, and relevant industry standards. They are independent and objective in their assessment.
- Cloud Provider: The cloud provider is responsible for providing the infrastructure and services used by the organization. They may provide information and documentation to the auditor. The cloud provider’s responsibilities also include implementing security controls at their end to protect the infrastructure.
- Organization’s Management: Organization’s management is responsible for defining the scope of the audit, providing resources for the audit team, and overseeing the remediation efforts. They are ultimately responsible for the security of the cloud environment.
- IT and Security Team: The IT and security team is responsible for implementing and maintaining the security controls in the cloud environment. They provide technical expertise and support to the audit team. They are responsible for remediating the vulnerabilities identified during the audit.
- Compliance Officer: The compliance officer ensures that the cloud environment complies with relevant regulations and standards. They provide guidance to the audit team and review the audit report to ensure compliance requirements are met.
Typical Timelines for Cloud Security Audits
The duration of a cloud security audit can vary depending on the scope, complexity, and type of audit. Understanding the typical timelines helps organizations plan and allocate resources effectively.
Here’s a table showing typical timelines for different types of cloud security audits:
| Type of Audit | Typical Timeline | Factors Influencing Timeline |
|---|---|---|
| Compliance Audit (e.g., SOC 2, ISO 27001) | 4-8 weeks | Scope of compliance, complexity of cloud environment, availability of documentation, and the number of systems and services involved. |
| Vulnerability Assessment | 1-2 weeks | Size and complexity of the cloud environment, the number of systems and services, and the types of vulnerabilities being assessed. |
| Penetration Test | 2-4 weeks | Scope of the test, the number of systems and services being tested, and the complexity of the cloud environment. |
| Internal Audit | 2-6 weeks | Scope, the size and complexity of the cloud environment, and the availability of resources. |
These timelines are estimates and can be influenced by various factors. For instance, the size and complexity of the cloud environment, the availability of documentation, and the responsiveness of the organization’s personnel can all impact the duration of the audit. It is essential to consider these factors when planning a cloud security audit and setting realistic expectations for the timeline.
Defining Scope and Objectives
Establishing a well-defined scope and clear objectives is paramount for a successful cloud security audit. This phase provides the framework for the entire audit process, ensuring it aligns with business needs and delivers actionable results. A clearly defined scope prevents scope creep and keeps the audit focused, while well-defined objectives ensure that the audit’s outcomes directly address the organization’s security priorities.
Defining the Scope of a Cloud Security Audit Based on Business Needs
Defining the scope involves identifying the boundaries of the audit. This is driven by the organization’s business requirements, risk profile, and the specific cloud services or assets under consideration. A thorough scope definition ensures the audit is relevant and efficient.The scope should include the following considerations:
- Identifying Critical Assets and Services: Determine which cloud-based assets and services are most vital to the business operations and revenue generation. Prioritize the audit based on the criticality of these assets. For example, if an e-commerce platform relies heavily on a specific database service, that service should be a high priority within the audit scope.
- Defining the Cloud Environment: Clearly specify which cloud environments (e.g., IaaS, PaaS, SaaS) and specific cloud providers (e.g., AWS, Azure, Google Cloud) are included in the audit. A hybrid cloud environment might require a more complex scope that encompasses both on-premises and cloud-based resources.
- Determining Audit Boundaries: Establish clear boundaries for the audit. This includes defining the specific systems, applications, data, and processes that will be examined. For instance, an audit of a SaaS application might focus on user access controls, data encryption, and data loss prevention measures.
- Considering Regulatory and Compliance Requirements: Identify all applicable regulations, standards, and compliance frameworks (e.g., GDPR, HIPAA, PCI DSS) that the organization must adhere to. The scope should include an assessment of compliance with these requirements. A healthcare provider operating in the cloud must ensure the audit covers HIPAA compliance for protected health information.
- Aligning with Business Objectives: Ensure the audit scope supports the organization’s overall business objectives. For example, if the business is expanding into new markets, the audit scope should address security risks associated with the new geographical locations and their specific regulatory landscapes.
Comparing Various Audit Methodologies
Different audit methodologies provide frameworks for conducting cloud security audits. The choice of methodology depends on the organization’s specific needs, industry, and regulatory requirements. Each methodology offers a structured approach to assess security controls and identify vulnerabilities.Here’s a comparison of some common audit methodologies:
- ISO 27001: ISO 27001 is an internationally recognized standard for information security management systems (ISMS). It provides a comprehensive framework for establishing, implementing, maintaining, and continually improving an ISMS. An audit based on ISO 27001 assesses the organization’s adherence to the standard’s requirements, covering aspects such as risk management, access control, and incident management. The standard offers a holistic approach to security, focusing on continual improvement and aligning security with business objectives.
- NIST Cybersecurity Framework: Developed by the National Institute of Standards and Technology (NIST), this framework offers a risk-based approach to managing cybersecurity risks. It is widely used in the United States and internationally. The NIST framework provides a set of guidelines and best practices for organizations to assess and improve their cybersecurity posture. It covers five core functions: Identify, Protect, Detect, Respond, and Recover.
The framework’s flexibility allows it to be adapted to various cloud environments and organizational needs.
- Cloud Security Alliance (CSA) Cloud Controls Matrix (CCM): The CSA CCM is a comprehensive set of security controls specifically designed for cloud computing. It provides a detailed framework of security controls based on the Cloud Security Alliance’s research and industry best practices. It covers various aspects of cloud security, including data security, identity and access management, and incident response. The CCM is particularly valuable for organizations using cloud services, as it provides a specific focus on cloud-related security challenges.
- SOC 2: SOC 2 (System and Organization Controls 2) is a compliance framework developed by the American Institute of Certified Public Accountants (AICPA). It focuses on the security, availability, processing integrity, confidentiality, and privacy of customer data. A SOC 2 audit assesses an organization’s adherence to these principles. It is particularly relevant for service providers that store or process customer data in the cloud.
Detailing How to Establish Clear and Measurable Audit Objectives
Establishing clear and measurable audit objectives is crucial for guiding the audit process and evaluating its effectiveness. These objectives should be specific, measurable, achievable, relevant, and time-bound (SMART). They should align with the overall goals of the organization and address the identified risks.To establish effective audit objectives:
- Identify Key Security Risks: Start by identifying the organization’s key security risks. This can be done through a risk assessment process, which considers threats, vulnerabilities, and potential impacts. For example, if the organization’s primary risk is unauthorized access to sensitive data, the audit objectives should address this risk.
- Define Specific Objectives: Translate the identified risks into specific, measurable objectives. For instance, instead of a general objective like “Improve security,” a more specific objective would be “Verify that all user access controls are properly configured and enforced to prevent unauthorized access to sensitive data.”
- Use Measurable Metrics: Define metrics to measure the achievement of each objective. This could involve the number of vulnerabilities found, the percentage of systems patched, or the time taken to respond to security incidents. For example, an objective to “Ensure data encryption” could be measured by the percentage of data at rest and in transit that is encrypted.
- Align with Business Goals: Ensure the objectives align with the organization’s overall business goals. For example, if the business is expanding into a new market, the audit objectives should include an assessment of the security controls related to the new market’s regulatory requirements.
- Document and Communicate Objectives: Clearly document all audit objectives and communicate them to the audit team and stakeholders. This ensures everyone understands the scope and goals of the audit.
Preparing for the Audit: Documentation
Proper documentation is crucial for a successful cloud security audit. It serves as the primary evidence of your organization’s security posture and adherence to relevant standards and best practices. Meticulous documentation allows auditors to quickly understand your cloud environment, assess your security controls, and identify potential vulnerabilities. It also streamlines the audit process, saving time and resources.
Essential Documentation for a Cloud Security Audit
A comprehensive set of documents is required to demonstrate the effectiveness of your cloud security program. These documents provide auditors with the necessary information to assess your security posture.
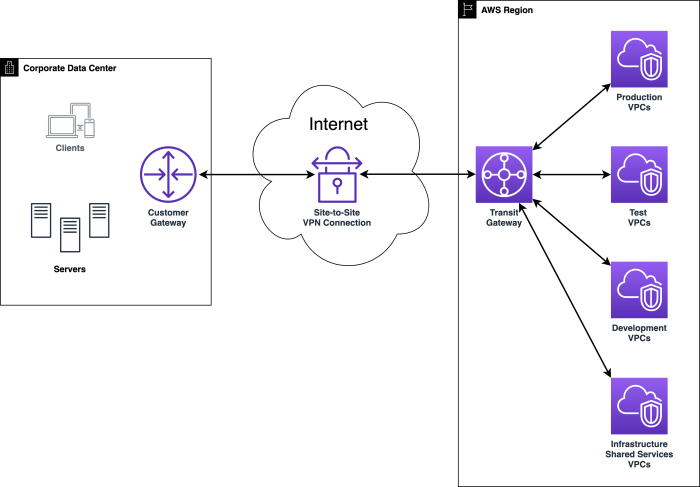
- Cloud Architecture Diagrams: These diagrams visually represent your cloud infrastructure, including the services used, their interconnections, and data flows. They should be up-to-date and accurately reflect your current environment. For instance, the diagram might show a virtual private cloud (VPC) with subnets, security groups, and instances running within.
- Security Policies and Procedures: This includes your organization’s written policies and procedures that govern cloud security practices. Examples include access control policies, incident response procedures, data loss prevention (DLP) policies, and vulnerability management procedures. These policies should align with industry best practices and regulatory requirements.
- Configuration Documentation: Detail the configuration settings of your cloud services. This includes settings for identity and access management (IAM), network security, storage, and compute instances. Provide screenshots or configuration files to demonstrate compliance.
- Inventory of Cloud Assets: A complete inventory of all your cloud assets, including instances, storage buckets, databases, and other resources. This inventory should include details such as asset names, resource types, owners, and their current status. This helps auditors verify that all assets are accounted for and appropriately secured.
- Risk Assessments: Documentation of your risk assessments, including identified threats, vulnerabilities, and the implemented controls to mitigate those risks. Risk assessments are a crucial component of any security program, and they provide a framework for prioritizing security efforts.
- Audit Logs: Logs from your cloud services, including access logs, activity logs, and security logs. These logs provide a record of all activities within your cloud environment and are essential for detecting and investigating security incidents.
- Incident Response Plan: A documented plan outlining the steps to be taken in the event of a security incident. This plan should include roles and responsibilities, communication procedures, and containment and recovery strategies.
- Compliance Reports: Reports demonstrating compliance with relevant regulations and standards, such as ISO 27001, SOC 2, or HIPAA. These reports provide independent verification of your security posture.
- Vendor Security Assessments: Assessments of third-party vendors who have access to your cloud environment or data. These assessments should evaluate the vendor’s security practices and their compliance with your security requirements.
Organizing and Maintaining Documentation
Organizing and maintaining documentation is critical for its usability and effectiveness. A well-organized documentation system allows auditors to easily find the information they need, which significantly streamlines the audit process.
- Centralized Repository: Store all security-related documentation in a centralized, easily accessible repository. This could be a shared drive, a document management system, or a cloud-based platform.
- Logical Folder Structure: Create a logical folder structure to categorize and organize documents. A common approach is to organize documents by security domain (e.g., access control, network security, data security) or by cloud service (e.g., compute, storage, database).
- Clear Naming Conventions: Use consistent and descriptive naming conventions for all documents. This will make it easier to find and identify documents quickly. For example, use a naming convention that includes the document type, the date of creation or last update, and a brief description of the document’s contents.
- Regular Reviews and Updates: Regularly review and update documentation to ensure it reflects your current cloud environment and security practices. This is particularly important when changes are made to your cloud infrastructure or security policies.
- Access Control: Implement access controls to restrict access to documentation based on roles and responsibilities. Only authorized personnel should be able to view, edit, or delete sensitive documents.
- Automated Documentation Generation: Leverage automation tools to generate and update documentation automatically where possible. For example, some cloud providers offer tools to generate configuration reports or network diagrams.
Version Control for Security-Related Documents
Version control is essential for tracking changes to security-related documents and ensuring that auditors have access to the most up-to-date information. It helps in understanding the evolution of security controls and configurations over time.
- Version Control System: Utilize a version control system, such as Git, to track changes to documents. This allows you to see who made changes, when they were made, and what those changes were.
- Change Logs: Maintain change logs for all documents. These logs should include the date of the change, the name of the person who made the change, a description of the change, and the document version.
- Document Approval Workflow: Implement a document approval workflow to ensure that all changes to security-related documents are reviewed and approved by authorized personnel before they are implemented.
- Regular Backups: Regularly back up all documentation to prevent data loss. Store backups in a separate location from the primary repository.
- Rollback Capability: Implement a rollback capability, allowing for reverting to previous versions of documents if necessary. This is particularly important in case of errors or unintended consequences of changes.
- Document Retention Policy: Establish and adhere to a document retention policy that specifies how long documents should be retained. This policy should comply with regulatory requirements and organizational policies.
Preparing for the Audit
Preparing for a cloud security audit involves a comprehensive approach, ensuring that all aspects of your cloud environment are secure and compliant with relevant standards and regulations. This phase focuses on the practical steps required to demonstrate the effectiveness of your security measures. It’s crucial to be proactive and organized to ensure a smooth and successful audit.
Preparing for the Audit: Technical Controls
Technical controls are the technological safeguards implemented to protect your cloud resources and data. Preparing for the audit involves verifying these controls are correctly implemented and functioning as intended. This requires a systematic approach, organizing controls by security domains, creating checklists, and demonstrating their effectiveness through testing.
The organization of technical controls by security domains facilitates a structured approach to the audit process.
This method allows auditors to easily assess the effectiveness of controls within specific areas of security. This helps ensure that all critical aspects of cloud security are addressed comprehensively.
- Access Control: This domain focuses on managing user identities, authentication, and authorization. It’s crucial to verify that only authorized individuals have access to resources.
- Data Protection: This encompasses the measures used to protect data, including encryption, data loss prevention (DLP), and data backup and recovery. Ensuring data confidentiality, integrity, and availability is the primary goal.
- Network Security: This involves securing the network infrastructure, including firewalls, intrusion detection and prevention systems (IDS/IPS), and virtual private networks (VPNs). It ensures the network is resilient to threats.
- Incident Response: This domain covers the processes and tools used to detect, respond to, and recover from security incidents. Effective incident response is vital for minimizing the impact of security breaches.
- Configuration Management: This includes the security configuration of all cloud resources, ensuring that they are configured according to best practices and security standards.
Creating a checklist for verifying technical control implementations is a vital step in preparing for the audit. The checklist serves as a roadmap, ensuring that all necessary controls are assessed and documented. This also aids in identifying any gaps in security.
Here’s an example of a checklist entry for access control:
| Control | Verification Steps | Status | Evidence |
|---|---|---|---|
| Multi-Factor Authentication (MFA) |
| Compliant/Non-Compliant/N/A | Screenshots of MFA settings, Login attempt logs |
| Role-Based Access Control (RBAC) |
| Compliant/Non-Compliant/N/A | Role definition documents, Access logs |
Demonstrating the effectiveness of technical controls is a critical component of the audit. This is achieved through various testing methods. The type of testing depends on the nature of the control being assessed.
- Vulnerability Scanning: This involves using automated tools to identify known vulnerabilities in cloud resources. The results should be analyzed and remediated.
- Penetration Testing: This simulates real-world attacks to assess the effectiveness of security controls. Penetration tests should be conducted regularly to identify weaknesses.
- Configuration Review: This involves reviewing the configuration of cloud resources to ensure they align with security best practices and standards. Configuration reviews are usually performed through manual checks and automated tools.
- Log Analysis: Reviewing security logs is a critical part of assessing the effectiveness of controls. Logs should be analyzed to identify suspicious activities and security breaches.
For example, to test the effectiveness of data encryption at rest, you might:
Verify that encryption is enabled on all storage volumes. Then, you would retrieve data from the storage and confirm it is encrypted. Finally, you’d check the key management system to ensure that keys are rotated regularly and access is restricted.
Risk Assessment and Management
A robust risk assessment and management strategy is critical for cloud security. It allows organizations to proactively identify, analyze, and mitigate potential threats and vulnerabilities, ensuring the confidentiality, integrity, and availability of their cloud resources. This process is not a one-time event but a continuous cycle that should be integrated into the overall cloud security posture.
Conducting a Comprehensive Risk Assessment
A comprehensive risk assessment involves several key steps to identify and evaluate potential threats. It begins with asset identification, followed by threat and vulnerability analysis, and concludes with the calculation of risk.
- Asset Identification: This step involves identifying all cloud assets, including data, applications, infrastructure, and services. Understanding the assets and their importance is fundamental to prioritizing risk mitigation efforts. Examples of assets include virtual machines, databases, storage buckets, and application programming interfaces (APIs). Consider the sensitivity of each asset, its criticality to business operations, and its location within the cloud environment.
- Threat and Vulnerability Analysis: Identify potential threats and vulnerabilities that could impact the identified assets. Threats can be internal or external, and vulnerabilities represent weaknesses that can be exploited by threats. Threat modeling methodologies, such as STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege), can be helpful in identifying potential attack vectors. Vulnerability scanning tools and penetration testing are also essential components of this phase.
- Risk Analysis: Analyze the likelihood of each threat exploiting a vulnerability and the potential impact if it were to occur. This often involves assigning values to both likelihood and impact, then calculating an overall risk score. Risk is typically calculated using the following formula:
Risk = Likelihood x Impact
- Risk Prioritization: Prioritize risks based on their risk scores. High-risk items require immediate attention, while lower-risk items may be addressed later. Prioritization helps organizations allocate resources effectively and focus on the most critical threats.
- Risk Documentation: Document the entire risk assessment process, including assets, threats, vulnerabilities, likelihood, impact, risk scores, and prioritization. This documentation serves as a valuable reference for future audits and security improvements.
Prioritizing Risks Based on Likelihood and Impact
Risk prioritization is crucial for efficient resource allocation and effective security management. Risks are categorized based on their likelihood of occurrence and the potential impact if they materialize.
A risk matrix, also known as a probability/impact matrix, is a commonly used tool for this purpose. This matrix typically has likelihood on one axis (e.g., Very Low, Low, Medium, High, Very High) and impact on the other (e.g., Catastrophic, Major, Moderate, Minor, Negligible). Risks are then plotted on the matrix based on their assessed likelihood and impact, allowing for a visual representation of their relative severity.
The risk matrix provides a clear visual guide for prioritizing risks and making informed decisions about risk treatment.
Here’s an example of how a risk matrix might be used:
| Impact | ||||
|---|---|---|---|---|
| Catastrophic | Major | Moderate | Minor | |
| Likelihood | ||||
| Very High | Critical Risk | High Risk | Medium Risk | Low Risk |
| High | High Risk | High Risk | Medium Risk | Low Risk |
| Medium | High Risk | Medium Risk | Medium Risk | Low Risk |
| Low | Medium Risk | Medium Risk | Low Risk | Low Risk |
Risks categorized as “Critical” or “High” require immediate mitigation, while those categorized as “Medium” or “Low” can be addressed with less urgency.
Creating a Risk Treatment Plan
Once risks are prioritized, a risk treatment plan is developed to address them. This plan Artikels the specific actions that will be taken to mitigate identified risks. The plan should be comprehensive, detailed, and regularly reviewed.
There are typically four primary approaches to risk treatment:
- Risk Avoidance: Eliminate the risk by avoiding the activity or process that gives rise to it. This might involve discontinuing a service, removing a vulnerability, or choosing a different technology. For example, if a specific cloud service poses an unacceptable security risk, the organization might choose to avoid using that service altogether.
- Risk Mitigation: Reduce the likelihood or impact of the risk. This is the most common approach and involves implementing security controls to reduce the probability of a threat exploiting a vulnerability or to limit the damage if an incident occurs. Examples include implementing multi-factor authentication (MFA), encrypting data at rest and in transit, and regularly patching systems.
- Risk Transfer: Transfer the risk to a third party, such as an insurance company or a cloud provider. This involves shifting the financial burden of a potential incident to another entity. Using a cloud provider with robust security measures and incident response capabilities is a form of risk transfer.
- Risk Acceptance: Accept the risk if the cost of mitigation outweighs the potential impact. This is usually reserved for low-impact risks or risks that are difficult or expensive to mitigate. Risk acceptance requires careful consideration and should be documented, with ongoing monitoring to ensure the risk remains acceptable.
Each risk treatment option should be evaluated based on its effectiveness, cost, and feasibility. The chosen treatment strategy should be documented, along with the responsible parties, timelines, and resources required for implementation. Regular monitoring and review are essential to ensure the effectiveness of the risk treatment plan and to make adjustments as needed. Consider the case of a major cloud provider in 2021 where a misconfiguration led to a significant data breach.
A robust risk treatment plan, including regular audits, configuration management, and access controls, could have potentially prevented or minimized the impact of the incident.
Cloud Provider Specific Considerations
Understanding the nuances of cloud provider security is crucial for a successful audit. Each major cloud platform – Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) – has its own specific requirements, security features, and shared responsibility model. Auditors must be well-versed in these specifics to accurately assess the security posture of a cloud environment.
Specific Audit Requirements for Different Cloud Providers
Audit requirements vary significantly depending on the cloud provider. Understanding these differences is paramount for effective preparation. The following points highlight key considerations for each platform:
- Amazon Web Services (AWS): AWS offers a comprehensive suite of security services, including Identity and Access Management (IAM), security auditing via CloudTrail, and security assessments through Amazon Inspector. Audits often focus on IAM configurations, data encryption, network security group rules, and compliance with specific standards like PCI DSS or HIPAA. For instance, auditors would examine the implementation of multi-factor authentication (MFA) for privileged accounts and the proper configuration of S3 bucket permissions to prevent unauthorized access to sensitive data.
- Microsoft Azure: Azure’s security landscape includes Azure Active Directory (Azure AD) for identity management, Azure Security Center for threat detection, and Azure Policy for governance. Audits frequently involve assessing Azure AD configurations, compliance with Azure Policy, and the security of virtual machines and storage accounts. An example audit focus might be the review of Azure Key Vault implementation to ensure the secure storage and management of encryption keys, or a review of the implementation of Azure Sentinel for threat detection and response.
- Google Cloud Platform (GCP): GCP provides security features like Cloud Identity and Access Management (Cloud IAM), Cloud Security Command Center (Cloud SCC), and Cloud Armor for web application protection. Audits typically evaluate Cloud IAM permissions, network security configurations, and the use of encryption at rest and in transit. An example would be verifying the enforcement of least privilege access using Cloud IAM roles and permissions, or checking the implementation of VPC Service Controls to protect sensitive data from exfiltration.
Shared Responsibility Model Across Major Cloud Platforms
The shared responsibility model is a fundamental concept in cloud security. It defines the security responsibilities shared between the cloud provider and the customer. Understanding this model is essential for scoping the audit and assigning responsibilities.
The core principle of the shared responsibility model is that the cloud provider is responsible for the security
-of* the cloud, while the customer is responsible for the security
-in* the cloud. This translates into specific areas of responsibility, which differ slightly across the major cloud platforms:
- AWS: AWS is responsible for the security of the underlying infrastructure, including compute, storage, database, and networking services. The customer is responsible for securing their data, applications, operating systems, and configurations within the AWS environment. The customer must manage access control, data encryption, and network security within their AWS accounts.
- Azure: Microsoft Azure’s shared responsibility model is similar to AWS, with Microsoft managing the physical security of the data centers, hardware, and the underlying infrastructure. Customers are responsible for securing their data, applications, and identities. This includes configuring security settings, managing access control, and ensuring data protection within the Azure environment.
- GCP: Google Cloud’s shared responsibility model aligns with the other providers. Google manages the security of the global infrastructure, including data centers, hardware, and network. Customers are responsible for securing their data, applications, and configurations within the GCP environment. This includes managing access control, data encryption, and implementing security best practices for their workloads.
Understanding the shared responsibility model allows auditors to clearly define the scope of the audit and to identify the areas where the customer is accountable for security.
Key Security Features Offered by Each Cloud Provider
Each cloud provider offers a range of security features designed to help customers protect their data and applications. These features are often built-in, offering a baseline level of security, and can be customized to meet specific needs.
- AWS: AWS offers a broad spectrum of security services. Key features include:
- Identity and Access Management (IAM): Allows for granular control over access to AWS resources.
- Amazon GuardDuty: A threat detection service that monitors for malicious activity and unauthorized behavior.
- AWS Key Management Service (KMS): Enables the creation and management of encryption keys.
- Amazon Inspector: Automated security assessment service that helps improve the security and compliance of applications deployed on AWS.
- Azure: Microsoft Azure provides robust security features, including:
- Azure Active Directory (Azure AD): Manages identities and access to resources.
- Azure Security Center: Provides unified security management and threat protection across hybrid cloud workloads.
- Azure Key Vault: Securely stores and manages secrets, keys, and certificates.
- Azure Sentinel: A cloud-native SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) solution.
- GCP: Google Cloud offers advanced security features, such as:
- Cloud Identity and Access Management (Cloud IAM): Controls access to Google Cloud resources.
- Cloud Security Command Center (Cloud SCC): Provides a centralized view of security findings and recommendations.
- Cloud Armor: Web application firewall (WAF) that protects against web-based attacks.
- VPC Service Controls: Helps protect sensitive data by allowing you to define a security perimeter around Google Cloud resources.
Data Protection and Privacy
Data protection and privacy are paramount concerns in cloud security audits. Cloud environments, by their nature, involve the storage, processing, and transmission of sensitive data, making them attractive targets for malicious actors and necessitating stringent security measures. Regulatory compliance, maintaining customer trust, and mitigating legal liabilities all hinge on robust data protection and privacy practices. Understanding the specific regulations that apply to your organization and the data you handle is critical for a successful cloud security audit.
Data Protection Regulations and Their Impact
Various data protection regulations worldwide significantly influence how cloud security audits are conducted and what areas they prioritize. Compliance with these regulations is not merely a matter of legal obligation but also a fundamental aspect of responsible cloud adoption. Non-compliance can result in severe penalties, reputational damage, and loss of customer trust.* General Data Protection Regulation (GDPR): The GDPR, applicable to organizations processing the personal data of individuals within the European Union, sets a high standard for data protection.
Cloud security audits under GDPR focus on:
Data minimization
Ensuring only necessary data is collected and processed.
Data security
Implementing appropriate technical and organizational measures to protect data against unauthorized access, loss, or alteration.
Data subject rights
Providing individuals with access to, rectification of, and erasure of their personal data.
Data transfer
Ensuring that data transfers outside the EU comply with GDPR requirements, such as the use of Standard Contractual Clauses (SCCs) or other approved mechanisms.
Data Breach Notification
Having procedures in place to notify the relevant supervisory authority and affected individuals within 72 hours of becoming aware of a data breach.
Example
A company storing EU citizens’ data in the cloud must ensure its cloud provider offers sufficient guarantees to implement appropriate technical and organizational measures. The audit will verify that the provider’s security practices meet GDPR requirements.* California Consumer Privacy Act (CCPA) / California Privacy Rights Act (CPRA): The CCPA, and its successor the CPRA, grants California consumers rights regarding their personal information. Cloud security audits under CCPA/CPRA focus on:
Right to Know
Providing consumers with information about the categories and specific pieces of personal information collected.
Right to Delete
Allowing consumers to request the deletion of their personal information.
Right to Opt-Out
Giving consumers the right to opt-out of the sale of their personal information.
Right to Correct
Allowing consumers to request the correction of inaccurate personal information.
Example
A cloud-based e-commerce platform processing California residents’ data needs to have mechanisms in place to honor consumer requests for data access, deletion, and opt-out of sales. The audit will review these mechanisms for compliance.* Health Insurance Portability and Accountability Act (HIPAA): If you’re dealing with Protected Health Information (PHI) in the US, HIPAA regulations apply. This requires specific controls and compliance. Cloud security audits under HIPAA concentrate on:
Administrative safeguards
Implementing policies and procedures to protect PHI.
Physical safeguards
Securing physical access to facilities and data centers.
Technical safeguards
Implementing access controls, audit trails, and encryption.
Example
A healthcare provider using a cloud-based Electronic Health Record (EHR) system must ensure the system and the cloud provider comply with HIPAA regulations. The audit will examine encryption of data in transit and at rest, access controls, and business associate agreements.* Other Regulations: Depending on the industry and location, other regulations may apply, such as the Payment Card Industry Data Security Standard (PCI DSS) for handling credit card information, or industry-specific regulations like those for financial services.
Procedures for Ensuring Data Privacy in the Cloud
Implementing robust procedures is crucial for ensuring data privacy in the cloud. These procedures must be integrated into all stages of the cloud lifecycle, from design and deployment to ongoing operations and incident response. A proactive approach to data privacy minimizes risks and builds trust.* Data Classification and Inventory:
Classify data based on sensitivity levels (e.g., public, internal, confidential, restricted).
Create a data inventory to track the location, processing, and access controls for all data assets.
Example
A financial institution categorizes customer financial data as “Confidential” and uses encryption, access controls, and stringent monitoring.* Data Encryption:
Encrypt data at rest (stored data) and in transit (data being transmitted).
Use strong encryption algorithms (e.g., AES-256) and regularly rotate encryption keys.
Example
A company uses a key management service (KMS) within their cloud environment to encrypt all database volumes, protecting against unauthorized access even if the underlying storage is compromised.* Access Controls and Identity Management:
Implement the principle of least privilege
Grant users only the minimum access necessary to perform their job functions.
Use multi-factor authentication (MFA) to verify user identities.
Regularly review and revoke access rights.
Example
Using role-based access control (RBAC), an organization assigns specific permissions to users based on their roles, such as “database administrator” or “customer service representative,” ensuring they only have access to the necessary data and functionalities.* Data Loss Prevention (DLP):
Implement DLP solutions to monitor and prevent sensitive data from leaving the cloud environment.
Configure DLP policies to detect and block unauthorized data transfers.
Example
DLP policies are set up to prevent the accidental or malicious sharing of customer social security numbers via email or cloud storage services.* Data Retention and Disposal:
Establish data retention policies based on legal and business requirements.
Securely dispose of data when it is no longer needed.
Use data sanitization methods to ensure data is irretrievable.
Example
After seven years, the company securely deletes archived customer data, adhering to legal requirements.* Privacy-Enhancing Technologies (PETs):
Explore and implement PETs such as differential privacy, homomorphic encryption, and secure multi-party computation to protect data privacy.
These technologies enable data analysis without revealing the underlying data.
Example
Using differential privacy, an organization can analyze customer data trends without exposing individual customer records, maintaining privacy while gaining valuable insights.* Vendor Management:
Conduct thorough due diligence on cloud providers to ensure they meet your data privacy requirements.
Establish data processing agreements (DPAs) that define data protection obligations.
Regularly audit cloud providers to verify their compliance.
Example
Before selecting a cloud provider, a company evaluates their security certifications, data center locations, and data protection policies.
Data Breaches and Incident Response in the Cloud
A comprehensive incident response plan is essential for addressing data breaches in the cloud. The plan should Artikel the steps to take in the event of a breach, from detection and containment to notification and recovery.* Incident Detection and Analysis:
Implement robust monitoring and logging to detect potential security incidents.
Use security information and event management (SIEM) systems to analyze logs and identify anomalies.
Example
A SIEM system flags unusual activity on a database server, triggering an investigation.* Containment and Eradication:
Contain the breach to prevent further damage.
Isolate affected systems and accounts.
Eradicate the root cause of the breach.
Example
Upon detecting a malware infection, the compromised server is immediately isolated from the network.* Notification and Reporting:
Notify affected individuals and regulatory authorities as required by law.
Follow the incident response plan’s established communication protocols.
Example
A company follows GDPR guidelines to notify the relevant data protection authorities and affected individuals within the specified timeframe after a data breach.* Recovery and Post-Incident Activities:
Restore systems and data from backups.
Implement preventative measures to prevent future incidents.
Conduct a post-incident review to identify lessons learned.
Example
After recovering from a ransomware attack, the company implements improved endpoint protection, enhanced network segmentation, and employee security awareness training.* Data Breach Notification:
Have established procedures to report data breaches as required by regulations like GDPR and CCPA/CPRA.
Ensure timely notification to regulatory bodies and affected individuals.
Example
If a breach affects the personal data of EU citizens, the organization is required to notify the relevant supervisory authority and affected individuals within 72 hours of becoming aware of the breach.
Access Control and Identity Management
Effective access control and identity management are cornerstones of cloud security. They ensure that only authorized individuals and systems can access sensitive resources, preventing unauthorized data breaches and system compromises. A well-defined strategy in this area is critical for meeting compliance requirements and maintaining the confidentiality, integrity, and availability of cloud-based assets.
Designing a Robust Access Control Strategy for Cloud Environments
A robust access control strategy involves defining who can access what resources and under what circumstances. This strategy should align with the principle of least privilege, granting users only the necessary access to perform their duties. This approach minimizes the potential impact of a security breach.
- Identity and Access Management (IAM) Systems: Implement centralized IAM systems, such as AWS IAM, Azure Active Directory, or Google Cloud IAM. These systems allow for the creation, management, and control of user identities and their access permissions.
- Role-Based Access Control (RBAC): Employ RBAC to assign permissions based on roles within the organization. This simplifies access management and reduces the likelihood of errors. For example, a “database administrator” role might have permissions to manage database instances, while a “developer” role might have permissions to access development environments.
- Attribute-Based Access Control (ABAC): Consider ABAC for more granular control. ABAC uses attributes associated with users, resources, and the environment to determine access. This provides greater flexibility and can be used to enforce complex access policies.
- Regular Access Reviews: Conduct regular reviews of access permissions to ensure that they are still appropriate. This helps identify and remediate excessive or unnecessary access rights. Schedule these reviews at least annually, or more frequently for sensitive data or critical systems.
- Principle of Least Privilege: Enforce the principle of least privilege, granting users only the minimum necessary access to perform their jobs. This reduces the attack surface and limits the damage that can be caused by compromised accounts.
- Network Segmentation: Implement network segmentation to isolate critical resources and limit lateral movement within the cloud environment. This prevents attackers from easily moving between systems if one is compromised.
- Monitoring and Auditing: Implement robust monitoring and auditing capabilities to track access attempts and identify suspicious activity. This includes logging all access events and regularly reviewing the logs.
Creating Procedures for Managing User Identities and Access Rights
Managing user identities and access rights requires clearly defined procedures to ensure consistency and security. These procedures should cover user onboarding, offboarding, and ongoing access management.
- User Onboarding: Develop a standardized process for creating new user accounts, including assigning roles, permissions, and access to necessary resources. This process should include strong password policies and multi-factor authentication (MFA) setup.
- User Offboarding: Establish a procedure for deactivating user accounts and revoking access rights when employees leave the organization or change roles. This process should be automated as much as possible to prevent delays.
- Password Management: Enforce strong password policies, including minimum length, complexity requirements, and regular password changes. Use a password manager for storing and managing passwords securely.
- Access Reviews: Implement a regular schedule for reviewing user access rights to ensure that they are still appropriate. Remove or modify permissions as needed. Document the review process and any changes made.
- Privileged Access Management (PAM): Implement PAM solutions to manage and secure privileged accounts, such as administrator accounts. These solutions provide features like password rotation, session recording, and access control.
- Automation: Automate access management tasks whenever possible, such as user provisioning, deprovisioning, and password resets. This reduces the risk of human error and improves efficiency.
- Documentation: Maintain clear and up-to-date documentation of all access control procedures, including roles, permissions, and access policies. This documentation should be readily available to authorized personnel.
Demonstrating How to Implement Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide two or more verification factors to access an account. This significantly reduces the risk of unauthorized access, even if a password is compromised.
- Selecting MFA Methods: Choose MFA methods that are appropriate for the cloud environment and the sensitivity of the data. Common MFA methods include:
- Hardware Tokens: Physical devices that generate time-based one-time passwords (TOTP).
- Software Tokens: Mobile applications that generate TOTPs.
- Biometrics: Fingerprint or facial recognition.
- Push Notifications: Notifications sent to a mobile device for approval or denial.
- SMS Codes: Text messages containing a verification code. (Note: SMS is generally considered less secure than other methods.)
- Implementing MFA: Implement MFA across all cloud services and applications. This can be achieved through the cloud provider’s IAM service or by using third-party MFA solutions.
- Enforcing MFA Policies: Enforce MFA policies to ensure that all users are required to use MFA. This can be done through configuration settings in the IAM system.
- Educating Users: Educate users about the importance of MFA and how to use it. Provide clear instructions and support to ensure that users can successfully implement MFA.
- Testing and Monitoring: Regularly test the MFA implementation to ensure that it is working correctly. Monitor MFA logs to identify any issues or suspicious activity.
- Examples of MFA Implementation:
- AWS IAM: Configure MFA for all IAM users and the root account. Require MFA for console access and API calls.
- Azure Active Directory: Enable MFA for all users through Azure AD Conditional Access policies.
- Google Cloud IAM: Enforce MFA for all users through Google Cloud Identity and Access Management.
- Integration with Single Sign-On (SSO): Integrate MFA with single sign-on (SSO) solutions to provide a seamless and secure user experience. This allows users to authenticate once and access multiple cloud applications without re-entering their credentials.
Security Policies and Procedures
Developing and maintaining robust security policies and procedures is critical for any organization operating in the cloud. These documents provide the framework for secure cloud operations, guiding employees, and ensuring consistent security practices. Properly implemented policies and procedures are essential for passing a cloud security audit and mitigating potential risks.
Creating and Implementing Security Policies
Creating and implementing effective security policies involves a structured approach, ensuring they are comprehensive, relevant, and enforceable. This process should be iterative, incorporating feedback and adapting to the evolving cloud environment.
- Policy Development: Begin by identifying the organization’s security objectives and risk tolerance. Research industry best practices and relevant compliance requirements (e.g., GDPR, HIPAA, PCI DSS). Develop clear and concise policy statements that address specific security areas.
- Stakeholder Involvement: Engage stakeholders from various departments, including IT, legal, compliance, and business units. This collaborative approach ensures policies are practical and address the needs of all relevant parties.
- Policy Review and Approval: Subject the draft policies to thorough review by legal and security experts. Obtain formal approval from senior management to demonstrate organizational commitment.
- Policy Communication and Training: Distribute the approved policies to all relevant employees. Provide comprehensive training on the policies, ensuring employees understand their responsibilities and how to comply. Regular training updates are also essential.
- Policy Implementation and Enforcement: Implement technical controls and processes to enforce the policies. This might include access controls, data encryption, and security monitoring. Establish clear procedures for reporting and addressing policy violations.
- Policy Review and Updates: Regularly review and update the policies to reflect changes in the cloud environment, emerging threats, and evolving business needs. Conduct periodic audits to assess policy effectiveness and compliance.
Organizing Security Procedures for Common Cloud Security Tasks
Well-defined security procedures streamline common cloud security tasks, promoting consistency and efficiency. Organizing these procedures ensures that tasks are performed correctly and consistently, reducing the likelihood of errors and vulnerabilities.
- Access Management Procedures: Document procedures for granting, modifying, and revoking user access to cloud resources. Include steps for user account creation, role assignment, and multi-factor authentication (MFA) implementation. For example, a procedure might detail how to onboard a new employee, including the steps to provision their cloud access based on their job role.
- Incident Response Procedures: Establish procedures for identifying, responding to, and recovering from security incidents. Define roles and responsibilities, communication protocols, and steps for containment, eradication, and recovery. An example would be the steps to take when a potential data breach is detected, including isolating affected systems and notifying relevant stakeholders.
- Data Backup and Recovery Procedures: Artikel procedures for regularly backing up cloud data and restoring it in the event of data loss or a disaster. Specify backup schedules, retention policies, and testing procedures. An example includes the steps to perform a full data backup of critical databases every week, storing the backups in a separate geographical location.
- Vulnerability Management Procedures: Detail procedures for identifying, assessing, and mitigating vulnerabilities in cloud infrastructure and applications. Include steps for vulnerability scanning, patch management, and penetration testing. For instance, a procedure might require scanning all virtual machines for vulnerabilities on a monthly basis and applying security patches within a specified timeframe.
- Change Management Procedures: Document procedures for managing changes to cloud infrastructure and applications. This ensures that changes are properly planned, tested, and approved before implementation, minimizing the risk of security breaches. An example is documenting the process for deploying a new software update to a production environment, including testing in a staging environment and obtaining approval from the change management board.
Creating Templates for Security Policy Documents
Using templates for security policy documents streamlines the policy creation process and ensures consistency across all policies. These templates provide a standardized structure and include essential elements, reducing the time and effort required to develop and maintain security policies.
- Template Structure: Develop templates that include a standard structure with sections for policy purpose, scope, definitions, responsibilities, policy statements, and enforcement.
- Policy Purpose: Clearly state the purpose of the policy and its objectives.
- Scope: Define the scope of the policy, specifying which systems, data, and users it applies to.
- Definitions: Provide clear definitions of key terms used in the policy.
- Responsibilities: Assign responsibilities for implementing and enforcing the policy to specific roles or departments.
- Policy Statements: State the specific security requirements and guidelines. For example, a password policy template should define password complexity requirements, length, and expiration periods.
- Enforcement: Artikel the consequences of violating the policy.
- Examples of Policy Templates: Develop templates for common security policies, such as:
- Password Policy
- Acceptable Use Policy
- Data Encryption Policy
- Incident Response Policy
- Access Control Policy
Communication and Collaboration
Effective communication and collaboration are crucial for a successful cloud security audit. This involves not only conveying the audit findings accurately but also fostering a collaborative environment with the auditors. A strong relationship with the audit team ensures a smoother process and a more beneficial outcome. This section provides guidance on effectively communicating audit findings, collaborating with auditors, and building a positive relationship with the audit team.
Communicating Audit Findings to Stakeholders
Clearly and concisely communicating audit findings is essential for ensuring stakeholders understand the risks and vulnerabilities identified. This includes tailoring the communication style to the audience and providing actionable recommendations.
The following points highlight key aspects of effective communication:
- Tailoring Communication to the Audience: Different stakeholders require different levels of detail. Technical teams need in-depth explanations of vulnerabilities, while executive management requires a high-level summary of risks and their business impact. For example, when presenting to the CISO, focus on the overall security posture and the strategic implications of the findings. When communicating to the engineering team, detail the specific technical flaws and remediation steps.
- Using Clear and Concise Language: Avoid technical jargon whenever possible, especially when communicating with non-technical stakeholders. Use plain language to explain complex concepts. For example, instead of saying “exploitable vulnerability due to improper input validation,” say “a security flaw that could allow unauthorized access.”
- Providing Actionable Recommendations: Audit findings are more valuable when accompanied by clear, specific, and actionable recommendations. These recommendations should prioritize the most critical vulnerabilities and provide a roadmap for remediation. For instance, instead of simply stating “weak password policy,” recommend “implement multi-factor authentication and enforce a minimum password length of 12 characters.”
- Presenting Findings with Context: Place the findings within the context of the overall cloud security posture. Explain how the vulnerabilities relate to business objectives and risk tolerance. For example, if a vulnerability could lead to data breaches, explain the potential financial and reputational impact.
- Creating Comprehensive Reports: Develop detailed audit reports that include an executive summary, findings with severity levels, remediation recommendations, and timelines. Include supporting evidence such as screenshots, logs, and code snippets to substantiate the findings.
- Holding Regular Follow-Up Meetings: Schedule regular follow-up meetings to discuss progress on remediation efforts. This demonstrates commitment to addressing the findings and provides an opportunity to address any roadblocks.
Collaborating with Auditors
A collaborative approach with the auditors can significantly improve the audit process. Open communication and a willingness to provide necessary information are key to a successful audit.
Collaboration with auditors involves several key elements:
- Providing Timely and Accurate Information: Respond promptly to auditor requests for information, including documentation, logs, and access to systems. Ensure the information is accurate and complete. For example, if the auditors request access to security logs, provide the necessary credentials and ensure the logs cover the audit period.
- Being Transparent and Open: Be transparent about the cloud environment, including its architecture, security controls, and any known vulnerabilities. Openness fosters trust and facilitates a more thorough audit.
- Facilitating Access to Resources: Provide auditors with access to the necessary resources, such as subject matter experts, system administrators, and security engineers. This allows auditors to gather the information they need efficiently.
- Seeking Clarification When Needed: Do not hesitate to ask auditors for clarification if you do not understand their requests or findings. This ensures you are addressing the issues correctly. For example, if an auditor identifies a vulnerability, ask for a detailed explanation of the flaw and its potential impact.
- Providing Feedback on the Audit Process: Offer feedback on the audit process, including its efficiency and effectiveness. This helps improve future audits.
- Documenting All Interactions: Maintain a detailed record of all communications and interactions with the auditors, including emails, meeting minutes, and any agreements reached. This provides a clear audit trail.
Building a Strong Relationship with the Audit Team
Building a positive relationship with the audit team is essential for a smooth and productive audit process. This involves showing respect, being responsive, and demonstrating a commitment to security.
The following actions contribute to building a strong relationship with the audit team:
- Being Respectful and Professional: Treat the auditors with respect and professionalism throughout the audit process. This includes being courteous, attentive, and responsive to their requests.
- Being Responsive to Requests: Respond promptly to auditor requests for information and clarification. This demonstrates your commitment to the audit and helps keep the process moving efficiently.
- Demonstrating a Commitment to Security: Show the auditors that you are committed to improving your cloud security posture. This can be done by actively addressing the audit findings and implementing the recommended remediation steps.
- Providing a Comfortable and Productive Environment: Ensure the auditors have a comfortable and productive environment to work in. This includes providing them with a dedicated workspace, access to necessary resources, and support as needed.
- Maintaining Open Communication: Keep the lines of communication open throughout the audit process. Regularly update the auditors on the progress of remediation efforts and any changes to the cloud environment.
- Expressing Appreciation: Thank the auditors for their work and provide positive feedback on their performance. This reinforces the importance of the audit process and encourages a collaborative relationship.
Post-Audit Activities and Remediation
Following the cloud security audit, the focus shifts to addressing the identified findings and recommendations. This phase is crucial for improving the organization’s security posture and mitigating potential risks. It involves a structured approach to remediate vulnerabilities, enhance security controls, and ensure ongoing compliance.
Addressing Audit Findings and Recommendations
The process of addressing audit findings and recommendations involves several key steps. It is important to remember that each finding requires careful consideration and a tailored approach to ensure effective remediation.
- Review and Prioritization: The initial step is a thorough review of the audit report. Each finding should be examined to understand its impact on the organization’s security posture. Prioritization is based on risk severity, likelihood of exploitation, and regulatory requirements. Findings are typically categorized as critical, high, medium, or low, depending on their potential impact.
- Root Cause Analysis: Determining the underlying causes of the findings is essential for effective remediation. This involves investigating the reasons behind the security issues. Understanding the root cause helps prevent recurrence of similar vulnerabilities in the future.
- Remediation Planning: Develop specific plans to address each finding. This includes defining the actions to be taken, assigning responsibilities, and establishing timelines. Plans should be detailed and include resource allocation.
- Implementation of Remediation: Execute the remediation plans. This may involve patching vulnerabilities, configuring security settings, implementing new security controls, or updating security policies. The implementation phase requires close collaboration between various teams, such as IT, security, and development.
- Verification and Validation: After implementing the remediation measures, verify their effectiveness. This can involve testing the implemented controls, reviewing system logs, and conducting follow-up audits. Verification ensures that the implemented solutions have successfully addressed the findings.
- Documentation and Reporting: Document all remediation activities, including the findings, the implemented solutions, and the verification results. Provide regular reports to stakeholders on the progress of the remediation efforts. This documentation is essential for maintaining a record of security improvements and demonstrating compliance.
Creating a Remediation Plan
A well-structured remediation plan is essential for effectively addressing audit findings. It provides a roadmap for implementing the necessary changes and tracking progress.
- Detailed Findings Summary: Begin the plan with a concise summary of each audit finding, including its description and the associated risk. Clearly state what was found to be non-compliant or vulnerable.
- Proposed Remediation Actions: For each finding, Artikel the specific actions that will be taken to remediate the issue. Be precise and include technical details. For example, instead of saying “patch the vulnerability,” specify the exact patch to be applied and the systems it affects.
- Responsible Parties: Assign ownership of each remediation action to specific individuals or teams. This ensures accountability and facilitates effective coordination. Include contact information for the responsible parties.
- Timelines and Deadlines: Establish realistic timelines and deadlines for completing each remediation action. Prioritize actions based on risk severity and regulatory requirements. Consider factors such as resource availability and complexity of the task.
- Resource Allocation: Identify the resources needed to implement the remediation actions, including personnel, tools, and budget. Ensure that sufficient resources are available to complete the remediation tasks on time.
- Testing and Validation Procedures: Describe the procedures that will be used to test and validate the effectiveness of the remediation actions. This includes the types of tests to be performed, the criteria for success, and the methods for documenting the results.
- Contingency Plans: Develop contingency plans to address potential roadblocks or delays in the remediation process. This may involve alternative solutions, additional resources, or adjustments to the timelines.
- Reporting and Communication: Define the frequency and format of reporting on the progress of the remediation efforts. This includes the stakeholders who will receive the reports and the communication channels to be used.
Tracking and Monitoring Remediation Efforts
Effective tracking and monitoring are critical for ensuring that remediation efforts are on track and that security improvements are being realized. This process involves establishing metrics, using tracking tools, and providing regular updates.
- Establish Key Performance Indicators (KPIs): Define specific KPIs to measure the progress and effectiveness of the remediation efforts. Examples include the percentage of vulnerabilities remediated, the time taken to remediate critical vulnerabilities, and the number of security incidents.
- Utilize Tracking Tools: Use tracking tools to manage and monitor the remediation process. Examples include project management software, ticketing systems, and vulnerability management platforms. These tools help to track progress, assign tasks, and manage deadlines.
- Regular Status Updates: Provide regular status updates to stakeholders on the progress of the remediation efforts. This can be done through status reports, meetings, or dashboards. Keep stakeholders informed of any challenges or delays.
- Monitor for Reoccurrence: Implement processes to monitor for the reoccurrence of vulnerabilities or security issues. This can involve automated vulnerability scanning, penetration testing, and regular security audits.
- Continuous Improvement: Use the data collected from tracking and monitoring to identify areas for improvement in the remediation process. This includes refining the remediation plans, improving communication, and optimizing the use of resources. For example, if a specific type of vulnerability consistently takes longer to remediate, the process for addressing that type of vulnerability should be reviewed and improved.
- Automation and Integration: Automate as much of the tracking and monitoring process as possible. Integrate tracking tools with other security tools, such as vulnerability scanners and SIEM systems, to streamline the process and improve efficiency.
Ending Remarks
In conclusion, preparing for a cloud security audit is not merely a compliance exercise; it’s a strategic investment in your organization’s security posture. By understanding the audit process, defining clear objectives, preparing meticulously, and fostering open communication, you can transform the audit into a valuable opportunity for improvement. This guide provides the roadmap to not only pass your audit but also to strengthen your cloud security, protect your valuable assets, and build trust with your stakeholders.
Expert Answers
What is the primary goal of a cloud security audit?
The primary goal is to assess the effectiveness of your cloud security controls and ensure they align with industry best practices and compliance requirements.
How long does a typical cloud security audit take?
The duration varies based on the scope and complexity, but it generally ranges from a few weeks to several months.
What are the most common reasons for audit failures?
Common reasons include inadequate documentation, poorly implemented security controls, and a lack of risk management.
How often should a cloud security audit be conducted?
The frequency depends on your industry, compliance requirements, and risk profile, but typically, audits are performed annually or bi-annually.