The transition of web applications to cloud environments represents a fundamental shift in modern software deployment and management. This guide offers a structured approach to understanding and executing this complex process, focusing on the technical aspects of migrating a web application to the cloud. The migration journey is not merely a transfer of data and code, but a strategic re-evaluation of infrastructure, architecture, and operational practices.
This document provides a detailed roadmap, from the initial assessment of the existing application to the optimization and scaling of the migrated system. It explores critical concepts such as cloud computing models, migration strategies, and security considerations, ensuring a comprehensive understanding of the key elements involved in a successful cloud migration. Each section is designed to provide actionable insights and practical guidance for web application developers, system administrators, and IT professionals.
Understanding Cloud Migration Fundamentals
Cloud migration involves transferring data, applications, and workloads from on-premises infrastructure to a cloud environment. This process requires a thorough understanding of cloud computing models, deployment strategies, and the underlying motivations driving the transition. A successful migration strategy is built upon a solid foundation of these fundamental concepts.Cloud computing has revolutionized how organizations manage their IT resources, offering scalability, cost-effectiveness, and increased agility.
Understanding the core models—IaaS, PaaS, and SaaS—is crucial for making informed decisions about migrating web applications.
Core Cloud Computing Models: IaaS, PaaS, and SaaS
The selection of a cloud computing model significantly impacts the management overhead, level of control, and the resources available for web application migration. Each model provides a different level of abstraction, allowing businesses to choose the best fit for their needs.
- Infrastructure as a Service (IaaS): IaaS provides the fundamental building blocks for cloud IT, including virtual machines, storage, and networking. Users have the most control over their infrastructure and are responsible for managing the operating systems, middleware, and applications. Examples include Amazon Web Services (AWS) EC2, Microsoft Azure Virtual Machines, and Google Compute Engine. This model is ideal for organizations that require significant flexibility and control over their infrastructure, but it also requires a higher level of technical expertise for management.
- Platform as a Service (PaaS): PaaS provides a platform for developing, running, and managing applications without the complexity of managing the underlying infrastructure. Developers can focus on coding and deployment, while the cloud provider handles the operating systems, middleware, and runtime environments. Examples include AWS Elastic Beanstalk, Google App Engine, and Microsoft Azure App Service. PaaS simplifies application development and deployment, making it suitable for rapid prototyping and agile development.
- Software as a Service (SaaS): SaaS delivers software applications over the internet, typically on a subscription basis. Users access the software through a web browser or mobile app, without needing to manage the underlying infrastructure or software. Examples include Salesforce, Google Workspace, and Microsoft 365. SaaS is the easiest to use and manage, but users have the least control over the software and its underlying infrastructure.
The choice of cloud model directly influences the migration strategy. For example, migrating a web application to IaaS might involve lifting and shifting the application to a virtual machine in the cloud. Migrating to PaaS might involve refactoring the application to take advantage of the platform’s features, while SaaS would typically involve migrating the application’s data and configuration to the SaaS provider’s platform.
Cloud Deployment Models: Comparison
Cloud deployment models determine where the cloud infrastructure is located and how it is managed. The choice of deployment model impacts factors like security, cost, performance, and compliance. The following table provides a comparison of the primary cloud deployment models.
| Deployment Model | Description | Advantages | Disadvantages |
|---|---|---|---|
| Public Cloud | Infrastructure is owned and operated by a third-party cloud provider, and resources are shared among multiple tenants. | Cost-effective, scalable, readily available, minimal upfront investment, and offers a wide range of services. | Less control over infrastructure, security concerns (shared resources), potential for vendor lock-in, and may not meet all compliance requirements. |
| Private Cloud | Infrastructure is dedicated to a single organization and can be located on-premises or hosted by a third-party provider. | Greater control over infrastructure, enhanced security, meets specific compliance requirements, and allows for customization. | Higher initial investment, requires in-house expertise for management, less scalable than public cloud, and can be more expensive to maintain. |
| Hybrid Cloud | A combination of public and private cloud, allowing organizations to leverage the benefits of both models. | Flexibility, scalability, cost optimization, allows for workload portability, and supports data residency requirements. | Increased complexity in management, requires integration between different environments, and security challenges in managing data across multiple environments. |
| Multi-Cloud | Utilizing multiple cloud providers for different workloads or applications. | Avoids vendor lock-in, optimizes costs, improves performance, and leverages the strengths of different cloud providers. | Increased complexity in management, requires expertise in multiple cloud platforms, and potential challenges in data integration and security. |
The choice of deployment model depends on an organization’s specific needs, including security requirements, budget constraints, compliance regulations, and the level of control required over the infrastructure. For example, a financial institution might opt for a private cloud to meet stringent security and compliance requirements, while a startup might choose a public cloud for its cost-effectiveness and scalability.
Primary Drivers for Cloud Migration
Several key factors motivate organizations to migrate their web applications to the cloud. These drivers often intertwine, and the relative importance of each varies depending on the organization’s specific circumstances.
- Cost Reduction: Cloud computing offers the potential to reduce IT costs by eliminating the need for upfront capital expenditures on hardware and software. Pay-as-you-go pricing models allow organizations to pay only for the resources they consume, which can lead to significant savings, especially for applications with fluctuating workloads. For instance, a retail company might see significant cost savings by scaling its infrastructure up during peak shopping seasons (like Black Friday) and scaling down during slower periods.
- Scalability and Elasticity: Cloud platforms provide virtually unlimited scalability, allowing organizations to easily adjust their resources to meet changing demands. This elasticity ensures that web applications can handle traffic spikes without performance degradation and that resources are not underutilized during periods of low demand. An example is a video streaming service that automatically scales its infrastructure to accommodate a surge in viewers during a popular event.
- Improved Agility and Innovation: Cloud platforms enable faster development cycles, allowing organizations to deploy new features and updates more quickly. The availability of pre-built services, such as databases, analytics tools, and machine learning services, accelerates innovation. A software company might leverage cloud services to quickly prototype and deploy new features for its web application, iterating rapidly based on user feedback.
- Enhanced Reliability and Availability: Cloud providers offer robust infrastructure with built-in redundancy and disaster recovery capabilities. This leads to improved application availability and reduces the risk of downtime. A global e-commerce platform can leverage cloud services to ensure high availability across multiple geographic regions, minimizing the impact of localized outages.
- Increased Security: Cloud providers invest heavily in security, offering advanced security features and expertise that can be difficult for organizations to replicate on their own. This can lead to improved security posture and reduced risk of data breaches. A healthcare provider might migrate its web application to the cloud to benefit from the cloud provider’s security certifications and expertise in protecting sensitive patient data.
These drivers often work together. For example, a company might migrate to the cloud to reduce costs, improve scalability, and enhance security. The relative importance of each driver depends on the organization’s priorities and the specific characteristics of its web application.
Assessing Your Current Web Application
Before embarking on a cloud migration, a thorough assessment of the existing web application is crucial. This process provides a comprehensive understanding of the application’s architecture, dependencies, and resource consumption, enabling informed decisions regarding the migration strategy and minimizing potential risks. A detailed evaluation facilitates the selection of the most appropriate cloud services and ensures a smooth transition, optimizing performance and cost-effectiveness.
Evaluating Application Architecture
The architecture of a web application dictates its functionality and performance characteristics. Evaluating this architecture involves dissecting its components and their interactions. This analysis helps in identifying potential bottlenecks and dependencies that may impact the migration process.
- Component Identification: Identifying all software and hardware components, including web servers (e.g., Apache, Nginx), application servers (e.g., Tomcat, JBoss), databases (e.g., MySQL, PostgreSQL, MongoDB), caching systems (e.g., Redis, Memcached), and load balancers. For example, a simple web application might use Apache as a web server, a PHP application server, and a MySQL database.
- Dependency Mapping: Understanding the interdependencies between components. This includes identifying which components rely on others, the data flow between them, and the protocols used for communication (e.g., HTTP, HTTPS, TCP). For instance, the web server is dependent on the application server to process dynamic content.
- Technology Stack Analysis: Documenting the specific technologies used in each component, including versions and configurations. This ensures compatibility with cloud services. For example, if using a specific version of PHP, ensure the cloud platform supports it.
- Data Flow Analysis: Tracing the path of data from the user interface to the database and back. This includes understanding how data is processed, stored, and retrieved. This helps in understanding the impact of the migration on data integrity and performance.
- Security Posture Assessment: Evaluating the security measures implemented in the application, such as authentication, authorization, encryption, and input validation. This is critical for ensuring the application’s security in the cloud.
Assessing Resource Utilization
Understanding how the web application utilizes resources is essential for optimizing cloud costs and performance. This involves monitoring CPU usage, memory consumption, network traffic, and storage I/O. This data informs decisions about instance sizing, database selection, and network configuration.
- CPU Utilization Monitoring: Tracking the percentage of CPU resources consumed by the application. High CPU usage may indicate performance bottlenecks or inefficient code. Monitoring tools like Prometheus or Datadog can provide these metrics.
- Memory Consumption Analysis: Measuring the amount of memory used by the application. Memory leaks or inefficient memory management can lead to performance degradation.
- Network Traffic Analysis: Monitoring the amount of data transferred in and out of the application. High network traffic can impact performance and increase costs. Tools like Wireshark can analyze network traffic patterns.
- Storage I/O Monitoring: Measuring the read and write operations on storage devices. High I/O can indicate database bottlenecks or inefficient data access patterns.
- Performance Testing: Conducting load tests and stress tests to simulate real-world user traffic and identify performance limitations. Tools like JMeter or LoadRunner can be used to simulate user activity.
Creating a Cloud Migration Readiness Checklist
A checklist provides a structured approach to assessing application readiness for cloud migration. This checklist ensures all critical aspects are considered, minimizing the risk of unforeseen issues. This checklist serves as a guide throughout the assessment process.
- Application Code Analysis: Evaluate the codebase for cloud compatibility. This includes identifying any hardcoded dependencies on the existing infrastructure. For example, hardcoded IP addresses or file paths need to be addressed.
- Database Assessment: Evaluate the database for cloud compatibility, including database size, schema complexity, and data integrity requirements. Consider the performance and scalability of the chosen cloud database service.
- Security Compliance: Ensure the application meets security and compliance requirements. This includes assessing security configurations, encryption, and access controls. For example, compliance with PCI DSS or HIPAA regulations.
- Network Configuration: Assess network requirements, including network bandwidth, latency, and security. Plan for the cloud network configuration, including VPCs, subnets, and security groups.
- Cost Estimation: Estimate the potential costs of running the application in the cloud. This involves considering instance types, storage, networking, and other cloud services.
- Backup and Disaster Recovery Planning: Develop a backup and disaster recovery plan for the cloud environment. This includes defining recovery point objectives (RPO) and recovery time objectives (RTO).
- Monitoring and Logging Strategy: Plan the implementation of monitoring and logging tools for the cloud environment. This includes selecting appropriate monitoring tools and logging services.
Documenting the Existing Infrastructure
Comprehensive documentation is vital for a successful cloud migration. It provides a clear understanding of the current state of the application and infrastructure, which is essential for planning, execution, and troubleshooting. Accurate documentation facilitates the transfer of knowledge and minimizes the risk of errors during migration.
- Application Architecture Diagrams: Create detailed diagrams that illustrate the application’s architecture, including components, dependencies, and data flow. These diagrams serve as a visual representation of the application.
- Configuration Documentation: Document the configuration of all application components, including server settings, database configurations, and network settings. This documentation provides a detailed record of the application’s configuration.
- Dependency Lists: Create a list of all dependencies, including software libraries, third-party services, and external APIs. This list is crucial for ensuring all dependencies are accounted for during the migration.
- Security Policies and Procedures: Document all security policies and procedures, including access controls, encryption methods, and security protocols. This documentation ensures security compliance in the cloud.
- Performance Metrics: Record all performance metrics, including CPU usage, memory consumption, network traffic, and storage I/O. This data provides a baseline for performance monitoring after migration.
- User and Administrator Guides: Create user and administrator guides that provide information on how to use and manage the application. These guides ensure users and administrators can effectively operate the application.
Choosing the Right Cloud Provider and Services
Selecting the appropriate cloud provider and services is a critical step in a successful web application migration. This choice significantly impacts performance, scalability, cost-effectiveness, and operational efficiency. A thorough evaluation of available options, aligned with the specific requirements of the application, is paramount.
Comparing Services Offered by Major Cloud Providers (AWS, Azure, Google Cloud) Relevant to Web Application Hosting
Each major cloud provider – Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) – offers a comprehensive suite of services tailored for web application hosting. Understanding the core offerings of each provider is essential for making informed decisions.
- Compute Services: These services provide the infrastructure for running the application’s code.
- AWS: Offers Amazon Elastic Compute Cloud (EC2) for virtual machines with various instance types, including optimized options for compute, memory, and storage. AWS also provides serverless compute with AWS Lambda, allowing code execution without server management.
- Azure: Provides Azure Virtual Machines, similar to EC2, with various sizes and configurations. Azure also offers Azure Functions for serverless computing, enabling event-driven execution.
- GCP: Offers Google Compute Engine (GCE) for virtual machines, with customizable machine types and pricing models. GCP’s serverless offering is Cloud Functions, providing a platform for event-driven functions.
- Storage Services: Storage services are essential for storing application data, files, and other assets.
- AWS: Offers Amazon Simple Storage Service (S3) for object storage, providing high durability and scalability. AWS also provides Elastic Block Storage (EBS) for block storage and Elastic File System (EFS) for file storage.
- Azure: Provides Azure Blob Storage for object storage, Azure Disk Storage for block storage, and Azure Files for file storage.
- GCP: Offers Google Cloud Storage for object storage, Persistent Disk for block storage, and Cloud Filestore for file storage.
- Database Services: Databases are fundamental for storing and managing application data.
- AWS: Offers Amazon Relational Database Service (RDS) for managed relational databases (e.g., MySQL, PostgreSQL, SQL Server, MariaDB, Oracle), Amazon DynamoDB for NoSQL databases, and Amazon Aurora for high-performance, MySQL and PostgreSQL-compatible databases.
- Azure: Provides Azure SQL Database for managed relational databases, Azure Cosmos DB for NoSQL databases, and Azure Database for MySQL, PostgreSQL, and MariaDB.
- GCP: Offers Cloud SQL for managed relational databases (e.g., MySQL, PostgreSQL, SQL Server), Cloud Spanner for globally distributed, scalable databases, and Cloud Datastore/Firestore for NoSQL databases.
- Networking Services: These services manage network connectivity, security, and traffic.
- AWS: Offers Amazon Virtual Private Cloud (VPC) for isolated networks, Elastic Load Balancing (ELB) for traffic distribution, and Amazon Route 53 for DNS management.
- Azure: Provides Azure Virtual Network for isolated networks, Azure Load Balancer for traffic distribution, and Azure DNS for DNS management.
- GCP: Offers Google Virtual Private Cloud (VPC) for isolated networks, Cloud Load Balancing for traffic distribution, and Cloud DNS for DNS management.
Designing a Decision Matrix to Help Select the Appropriate Cloud Provider Based on Specific Application Requirements and Budget
A decision matrix provides a structured approach to evaluate and compare cloud providers based on specific criteria. This method allows for a systematic assessment, leading to a more informed decision. The matrix should consider various factors and assign weights based on their importance to the application’s needs.
The following table illustrates a simplified decision matrix framework:
| Criteria | Weight (%) | AWS | Azure | GCP | Score (AWS) | Score (Azure) | Score (GCP) |
|---|---|---|---|---|---|---|---|
| Compute Performance | 20 | 4 | 3 | 5 | 0.8 | 0.6 | 1.0 |
| Storage Cost | 15 | 5 | 4 | 3 | 0.75 | 0.6 | 0.45 |
| Database Options | 15 | 5 | 4 | 4 | 0.75 | 0.6 | 0.6 |
| Networking Features | 10 | 4 | 5 | 4 | 0.4 | 0.5 | 0.4 |
| Scalability | 20 | 5 | 4 | 5 | 1.0 | 0.8 | 1.0 |
| Pricing Model | 10 | 4 | 3 | 4 | 0.4 | 0.3 | 0.4 |
| Support & Documentation | 10 | 5 | 4 | 4 | 0.5 | 0.4 | 0.4 |
| Total | 100 | 4.6 | 3.8 | 4.25 |
In this example:
- Criteria: The specific requirements of the web application are listed, such as compute performance, storage cost, and database options.
- Weight (%): The importance of each criterion is defined. For instance, if scalability is crucial, it receives a higher weight.
- Provider Ratings: Each provider (AWS, Azure, GCP) is rated on a scale (e.g., 1-5) for each criterion. A higher rating indicates better suitability.
- Score: The weighted score for each provider is calculated by multiplying the rating by the weight.
- Total Score: The sum of the scores provides an overall assessment of each provider’s suitability.
This matrix is a simplified illustration. A real-world decision matrix should include more detailed criteria, specific application requirements, and a thorough cost analysis. This approach helps to make a data-driven decision, optimizing the selection of a cloud provider.
Providing a Guide to Selecting the Right Cloud Services for Compute, Storage, and Database Needs
Choosing the correct cloud services is crucial for optimizing performance, scalability, and cost-efficiency. The selection process must be aligned with the specific requirements of the application, including expected traffic, data storage needs, and data processing requirements.
- Compute Services:
- Virtual Machines (VMs): Ideal for applications requiring full control over the operating system and environment. Select the instance type based on CPU, memory, and storage requirements. Consider AWS EC2, Azure Virtual Machines, or Google Compute Engine. For example, an e-commerce platform might start with a medium-sized instance and scale up during peak seasons.
- Serverless Computing: Best for event-driven applications and microservices. This allows developers to run code without managing servers. AWS Lambda, Azure Functions, and Google Cloud Functions are suitable choices. For example, image processing tasks or API endpoints can be implemented using serverless functions.
- Containerization (e.g., Docker): Useful for applications needing portability and consistency across different environments. Services like AWS Elastic Container Service (ECS), Azure Container Instances, and Google Kubernetes Engine (GKE) are beneficial.
- Storage Services:
- Object Storage: Suitable for storing large amounts of unstructured data, such as images, videos, and backups. AWS S3, Azure Blob Storage, and Google Cloud Storage are popular choices. For example, a content delivery network (CDN) can utilize object storage to serve static assets globally.
- Block Storage: Ideal for applications requiring persistent storage for VMs. AWS EBS, Azure Disk Storage, and Google Persistent Disk offer block storage solutions. For example, a database server often utilizes block storage for its data files.
- File Storage: Suitable for applications that need shared file systems. AWS EFS, Azure Files, and Google Cloud Filestore provide file storage options. For example, a content management system (CMS) may use file storage to share files across multiple servers.
- Database Services:
- Relational Databases: Suitable for structured data and applications requiring ACID transactions. AWS RDS, Azure SQL Database, and Google Cloud SQL offer managed relational database services. For example, a financial application requires a relational database to maintain data integrity.
- NoSQL Databases: Ideal for applications requiring high scalability and flexible data models. AWS DynamoDB, Azure Cosmos DB, and Google Cloud Datastore/Firestore provide NoSQL database options. For example, a social media platform may use a NoSQL database for user profiles and activity feeds.
- Database as a Service (DBaaS): Managed database services that handle administration tasks. This allows developers to focus on application development.
The selection of services should also consider factors like cost optimization, security, and performance. Implementing a proof-of-concept (POC) and conducting performance tests can help refine the service selection and ensure optimal performance.
Planning Your Migration Strategy
A well-defined migration strategy is critical for a successful cloud migration. It provides a roadmap, minimizes risks, and ensures that the transition aligns with the organization’s business objectives. This section explores various migration strategies and the process of creating a detailed migration plan.
Migration Strategies
Selecting the appropriate migration strategy depends on several factors, including the application’s complexity, business requirements, and available resources. Different strategies offer varying levels of effort, cost, and risk. Understanding each approach is crucial for making informed decisions.
- Rehosting (Lift and Shift): This involves migrating the application to the cloud with minimal changes. It’s the quickest and simplest approach, suitable for applications that are relatively straightforward and where immediate cost savings are desired. For example, migrating a virtual machine running a legacy web application to an Infrastructure-as-a-Service (IaaS) environment in the cloud. The application’s code and architecture remain largely unchanged.
This strategy prioritizes speed and cost-effectiveness.
- Replatforming (Lift, Tinker, and Shift): This strategy involves making some cloud-specific optimizations to the application without fundamentally changing its core architecture. It may involve changing the database, operating system, or using managed services. For instance, migrating a database from an on-premises SQL Server to a cloud-based database service like Amazon RDS or Azure SQL Database. This strategy aims to leverage cloud-native features for improved performance and scalability.
- Refactoring (Re-architecting): This entails significantly modifying the application’s code and architecture to fully leverage cloud-native services and features. It often involves breaking down a monolithic application into microservices, redesigning the database, and adopting cloud-native technologies. An example is transforming a Java-based monolithic application into a collection of microservices deployed on Kubernetes, utilizing cloud-native databases and message queues. This approach offers the greatest benefits in terms of scalability, resilience, and cost optimization but requires the most effort and investment.
- Rearchitecting: Similar to refactoring, rearchitecting involves a more fundamental redesign of the application to take full advantage of cloud-native capabilities. However, rearchitecting often involves a more extensive overhaul of the application’s architecture, potentially including a complete rewrite. An example is completely rewriting a legacy application using serverless functions, containerization, and cloud-native data stores. This approach offers the highest potential for performance, scalability, and cost savings but also carries the highest risk and requires significant expertise.
- Repurchase (Replace): This involves replacing the existing application with a Software-as-a-Service (SaaS) solution. This is a good option for applications that are not core to the business or where a SaaS solution provides a better fit. For instance, migrating from an on-premises CRM system to a cloud-based CRM like Salesforce or HubSpot. This strategy minimizes the migration effort and focuses on adopting a pre-built solution.
- Retire: This involves decommissioning the application entirely. This is appropriate for applications that are no longer needed or have become obsolete. For example, retiring a legacy application that duplicates the functionality of a more modern system. This strategy is the simplest in terms of execution but requires careful consideration to ensure that no critical functionality is lost.
Creating a Detailed Migration Plan
A comprehensive migration plan is essential for managing the complexities of a cloud migration project. It should Artikel the scope, objectives, timelines, resource allocation, and risk mitigation strategies. A well-structured plan ensures that the migration is executed efficiently and effectively.
- Define Objectives and Scope: Clearly articulate the business goals of the migration, such as cost reduction, improved scalability, or enhanced agility. Define the scope of the migration, including which applications and data will be migrated.
- Assess the Current Environment: Conduct a thorough assessment of the existing infrastructure, applications, and data. Identify dependencies, performance bottlenecks, and security vulnerabilities. This assessment provides a baseline for the migration.
- Choose a Migration Strategy: Select the most appropriate migration strategy based on the application’s characteristics, business requirements, and available resources. Consider the trade-offs between cost, effort, and risk.
- Design the Target Architecture: Design the cloud-based architecture, including the selection of cloud services, network configuration, and security controls. Ensure that the architecture meets the performance, scalability, and security requirements.
- Develop a Migration Timeline: Create a detailed timeline that Artikels the migration phases, tasks, and deadlines. Use a project management tool to track progress and manage dependencies. Consider using an Agile approach for greater flexibility.
- Allocate Resources: Identify and allocate the necessary resources, including personnel, budget, and tools. Ensure that the team has the skills and expertise required for the migration.
- Test and Validate: Develop a comprehensive testing plan to validate the migrated applications and data. Conduct performance, security, and functional testing to ensure that the migration is successful.
- Develop a Risk Mitigation Plan: Identify potential risks and develop mitigation strategies. Include contingency plans for unexpected issues or delays.
- Execute the Migration: Execute the migration according to the plan. Monitor progress, address issues, and communicate updates to stakeholders.
- Post-Migration Optimization: After the migration, optimize the cloud environment for performance, cost, and security. Continuously monitor and improve the migrated applications and infrastructure.
Phases of a Typical Cloud Migration Project
A typical cloud migration project can be divided into distinct phases, each with specific activities and deliverables. This phased approach provides a structured framework for managing the migration process.
Phase 1: Assessment and Planning
This phase involves evaluating the current state of the IT environment, defining migration goals, and selecting the appropriate migration strategy. It also includes creating a detailed migration plan, assessing risks, and identifying resource requirements.
Phase 2: Migration and Execution
This phase encompasses the actual migration of applications and data to the cloud. It includes activities such as setting up the cloud environment, configuring network and security settings, migrating data, and testing the migrated applications. This phase is iterative and may involve multiple migration waves.
Phase 3: Validation and Optimization
This phase focuses on validating the migrated applications and optimizing the cloud environment for performance, cost, and security. It includes performance testing, security audits, and cost optimization strategies. Continuous monitoring and improvement are crucial in this phase.
Diagram Description: The diagram visually represents the phases of a typical cloud migration project as a cyclical process. The diagram consists of three main sections, each representing a distinct phase. The first section, Assessment and Planning, is represented by a rounded rectangle. Inside this rectangle are the steps: “Assess Current Environment,” “Define Migration Goals,” “Select Migration Strategy,” and “Create Migration Plan.” The second section, Migration and Execution, is also represented by a rounded rectangle.
Inside are the steps: “Set Up Cloud Environment,” “Configure Network and Security,” “Migrate Data,” and “Test Applications.” The third section, Validation and Optimization, is another rounded rectangle. Inside are the steps: “Performance Testing,” “Security Audits,” and “Cost Optimization.” Arrows indicate the flow of the process, showing that the migration is an iterative process. An arrow flows from the Validation and Optimization phase back to the Migration and Execution phase, emphasizing the iterative nature of the process.
A final arrow leads back to the Assessment and Planning phase, indicating the importance of continuous improvement.
Preparing Your Application for Migration
Migrating a web application to the cloud requires meticulous preparation to ensure a smooth transition and optimal performance. This involves adapting the application code, configuring the infrastructure, and implementing security measures that are compatible with the cloud environment. A well-prepared application leverages the cloud’s benefits, such as scalability, cost-effectiveness, and improved availability.
Application Code Adaptation
Adapting the application code is a crucial step in preparing for cloud migration. It ensures compatibility with the cloud infrastructure and takes advantage of cloud-native features. This process often involves modifying the code to interact with cloud services and optimizing performance.
- Dependency Management: Cloud environments often have specific requirements for dependencies. Review and update the application’s dependencies to ensure compatibility with the cloud platform. This may involve upgrading libraries, replacing deprecated ones, or using cloud-specific SDKs. For example, if migrating a Python application to AWS, you might need to replace dependencies like `psycopg2` (for PostgreSQL) with a version compatible with AWS RDS.
- Configuration Management: Hardcoded configurations can be problematic in the cloud. Implement a centralized configuration management system to store and manage settings like database connection strings, API keys, and environment variables. This allows for easier updates and avoids the need to redeploy the application for configuration changes. Cloud providers offer services like AWS Parameter Store, Azure Key Vault, and Google Cloud Secret Manager to manage configurations securely.
- Statelessness and Scalability: Cloud environments thrive on stateless applications. Ensure the application does not store session data locally. Instead, use a shared session store like Redis or Memcached. This allows for horizontal scaling, where multiple instances of the application can handle requests concurrently without data inconsistencies. Consider using a load balancer to distribute traffic across multiple instances.
- Logging and Monitoring: Implement robust logging and monitoring to track application behavior and identify potential issues. Cloud providers offer logging and monitoring services, such as AWS CloudWatch, Azure Monitor, and Google Cloud Operations. Use these services to collect logs, metrics, and traces, enabling you to gain insights into application performance and troubleshoot problems. Ensure logs include relevant information like timestamps, request IDs, and error messages.
- Database Considerations: Evaluate the database strategy. If migrating a monolithic application, consider refactoring the database to be cloud-compatible. Consider database services provided by cloud providers (e.g., AWS RDS, Azure SQL Database, Google Cloud SQL) to manage and scale databases efficiently. If using a NoSQL database, choose a cloud-native service like AWS DynamoDB, Azure Cosmos DB, or Google Cloud Datastore.
Containerizing Your Application Using Docker
Containerization using Docker simplifies the deployment and management of applications in the cloud. Docker packages the application and its dependencies into a container, ensuring consistent behavior across different environments. This portability makes it easier to deploy and scale applications on cloud platforms.
- Dockerfile Creation: A Dockerfile is a text file that contains instructions for building a Docker image. Create a Dockerfile for the application, specifying the base image (e.g., Ubuntu, Alpine), installing dependencies, copying the application code, and defining the entry point. For a Python application, the Dockerfile might look like this:
FROM python:3.9-slim-busterWORKDIR /appCOPY requirements.txt .RUN pip install --no-cache-dir -r requirements.txtCOPY . .CMD ["python", "app.py"]This Dockerfile uses a Python base image, sets the working directory, copies the requirements file, installs dependencies, copies the application code, and defines the command to run the application.
- Image Building: Build the Docker image using the Dockerfile. This creates a self-contained package that includes everything the application needs to run. The command to build the image is typically `docker build -t [image_name]:[tag] .`, where `[image_name]` is the name of the image, `[tag]` is a version tag, and the `.` indicates the current directory (where the Dockerfile is located).
For instance, `docker build -t my-web-app:1.0 .`.
- Container Deployment: Deploy the Docker image to a container orchestration platform like Kubernetes, Amazon ECS, Azure Container Instances, or Google Kubernetes Engine. These platforms manage the containers, ensuring they are running and scaled according to the specified requirements. Deploying a container to a cloud platform involves configuring the deployment settings, such as the number of replicas, resource limits, and networking configurations.
- Container Orchestration: Container orchestration platforms automate the deployment, scaling, and management of containerized applications. They provide features such as service discovery, load balancing, and health checks. Kubernetes is a popular open-source platform that offers advanced features for managing complex deployments. Cloud providers offer managed Kubernetes services, such as Amazon EKS, Azure AKS, and Google GKE, to simplify the deployment and management of Kubernetes clusters.
Networking and Security Configuration
Configuring networking and security in the cloud is critical for protecting the application and ensuring its availability. Cloud providers offer various services and tools to manage network connectivity and security policies.
- Virtual Private Cloud (VPC): Create a VPC to isolate the application’s resources within a private network. This provides a secure and controlled environment for the application. Configure subnets, route tables, and security groups within the VPC to manage network traffic and access. For example, in AWS, a VPC allows you to define a virtual network that is logically isolated from other networks in the cloud.
- Security Groups: Security groups act as virtual firewalls, controlling inbound and outbound traffic to and from the application instances. Define rules within the security groups to allow only necessary traffic, such as HTTP/HTTPS traffic to the web server and database connections to the database server. Security groups can be configured to allow traffic from specific IP addresses, CIDR blocks, or other security groups.
- Network Access Control Lists (ACLs): Network ACLs provide an additional layer of security, allowing you to control traffic at the subnet level. ACLs are stateless, meaning that they evaluate traffic in both directions independently. Use ACLs to further restrict network traffic and enforce security policies.
- Load Balancing: Implement load balancing to distribute traffic across multiple application instances, improving availability and scalability. Cloud providers offer load balancing services, such as AWS Elastic Load Balancing, Azure Load Balancer, and Google Cloud Load Balancing. Configure the load balancer to distribute traffic based on various criteria, such as round-robin or least connections.
- Web Application Firewall (WAF): Deploy a WAF to protect the application from common web vulnerabilities, such as cross-site scripting (XSS) and SQL injection attacks. Cloud providers offer WAF services, such as AWS WAF, Azure Web Application Firewall, and Google Cloud Armor. Configure the WAF to block malicious traffic and protect against known attacks.
- Encryption: Implement encryption to protect data in transit and at rest. Use HTTPS for secure communication between the client and the application. Encrypt data stored in databases and storage services using encryption keys managed by cloud providers. Consider using services like AWS KMS, Azure Key Vault, and Google Cloud KMS to manage encryption keys securely.
- Identity and Access Management (IAM): Implement IAM to control access to cloud resources. Grant users and applications only the necessary permissions to perform their tasks. Use least privilege principles to minimize the potential impact of security breaches. Regularly review and update IAM policies to ensure they are aligned with security best practices.
Data Migration Strategies
Migrating data to the cloud is a critical aspect of web application migration. The chosen strategy directly impacts the migration’s success, affecting downtime, data integrity, and overall cost. Careful consideration of various methods and tools is essential to ensure a smooth and efficient transition.
Different Data Migration Methods and Their Trade-offs
Data migration methods can be broadly categorized into online and offline approaches, each possessing unique advantages and disadvantages. The selection depends on factors like the volume of data, acceptable downtime, and network bandwidth availability.
- Online Migration: This method involves transferring data while the source database remains operational. Changes made to the source database during the migration are typically synchronized with the target cloud database.
- Offline Migration: This method requires taking the source database offline to prevent data modifications during the transfer. This approach typically offers faster data transfer rates, especially for large datasets, but results in application downtime.
Here’s a comparison of the trade-offs:
| Feature | Online Migration | Offline Migration |
|---|---|---|
| Downtime | Minimal; application remains accessible. | Significant; application unavailable during migration. |
| Data Consistency | Requires robust synchronization mechanisms to handle ongoing changes. | Guaranteed; data frozen during the transfer. |
| Complexity | More complex due to synchronization requirements and potential for data conflicts. | Simpler, but requires careful planning for downtime. |
| Transfer Speed | Slower, limited by network bandwidth and synchronization overhead. | Faster, particularly for large datasets. |
| Cost | Potentially higher due to the need for synchronization tools and longer migration duration. | Potentially lower, depending on the chosen tools and services. |
Migrating Databases to the Cloud: Data Consistency and Integrity
Migrating databases involves transferring the data, schema, and potentially the database engine itself to the cloud environment. Maintaining data consistency and integrity throughout this process is paramount.
Key considerations for database migration include:
- Choosing the Right Database Service: Select a cloud-based database service (e.g., Amazon RDS, Azure SQL Database, Google Cloud SQL) that aligns with the application’s requirements regarding scalability, performance, and cost. Evaluate features like automatic backups, high availability, and disaster recovery.
- Data Extraction and Transformation: The process of extracting data from the source database and transforming it to fit the target schema. This might involve changing data types, cleaning data, or mapping data fields.
- Data Loading: Transferring the transformed data into the cloud database. This stage utilizes tools that can handle bulk loading for efficiency or incremental loading for minimal downtime.
- Data Validation: After loading, validate the data in the cloud database against the source database to confirm accuracy and completeness. This step helps identify data discrepancies.
- Schema Migration: Ensure the target database schema matches the source schema, which is especially important for relational databases. Tools are available to automate schema conversion or migrations.
- Maintaining Data Consistency: Implement strategies to ensure data consistency during online migrations. This includes using change data capture (CDC) or replication techniques to synchronize changes from the source to the target database.
To maintain data integrity, consider the following:
- Transactions: Use transactions to ensure that data modifications are either fully committed or rolled back in case of failures. This prevents partial updates that could compromise data integrity.
- Constraints: Implement constraints (e.g., primary keys, foreign keys, unique constraints) in the cloud database to enforce data integrity rules and prevent invalid data from being entered.
- Auditing: Enable auditing to track data changes and detect any unauthorized modifications.
- Backup and Recovery: Establish a robust backup and recovery strategy to protect data from loss or corruption. Cloud providers offer automated backup and recovery services.
Data Migration Tools and Services Offered by Cloud Providers
Cloud providers offer a range of tools and services to simplify and automate the data migration process. These tools often provide features like automated schema conversion, data transfer, and monitoring.
Commonly used tools and services include:
- AWS Database Migration Service (DMS): AWS DMS supports both homogenous and heterogeneous database migrations, including online and offline migrations. It can replicate data continuously, minimizing downtime. It supports various source and target database engines.
- Azure Database Migration Service (DMS): Azure DMS offers a similar functionality to AWS DMS, facilitating the migration of databases to Azure. It supports online, offline, and hybrid migrations. It provides tools for schema assessment and data validation.
- Google Cloud Data Transfer Service: Google Cloud provides services for transferring data into Google Cloud Storage and then into various database services like Cloud SQL and BigQuery. This can involve batch and streaming data transfers.
- Third-Party Migration Tools: Various third-party tools provide additional features and support for complex migrations, including advanced data transformation capabilities, support for more database types, and specialized monitoring features. Examples include Informatica, Attunity, and HVR.
Choosing the appropriate tools depends on factors like the source and target database types, the volume of data, the required downtime, and the budget. Consider evaluating the features and capabilities of each tool to find the best fit for the specific migration requirements.
Implementing the Migration Process
Migrating a web application to the cloud is a multifaceted undertaking, demanding meticulous planning and execution. This section Artikels the practical steps involved in migrating your application, focusing on deployment and automation to ensure a smooth and efficient transition. The approach varies depending on the chosen migration strategy (rehosting, replatforming, refactoring, etc.), but the fundamental principles of deployment and automation remain consistent.
Step-by-Step Migration Guide
The actual migration process is a phased approach, carefully orchestrated to minimize downtime and ensure data integrity. The specific steps will depend on the chosen migration strategy, the complexity of the application, and the chosen cloud provider. However, a general sequence can be Artikeld:
- Preparation and Planning Validation: Revisit the migration plan. Confirm all prerequisites are in place, including necessary cloud accounts, access credentials, and networking configurations. Conduct thorough testing in a pre-production environment to validate the migration plan and identify potential issues before the actual cutover.
- Infrastructure Provisioning: Provision the necessary infrastructure in the cloud environment. This involves creating virtual machines (VMs), setting up databases, configuring load balancers, and establishing network connections. Use Infrastructure as Code (IaC) tools (e.g., Terraform, AWS CloudFormation, Azure Resource Manager) to automate this process and ensure consistency. For example, if migrating to AWS, you might use CloudFormation to define the infrastructure components, such as EC2 instances, RDS databases, and load balancers, in a declarative manner.
- Application Code and Configuration Migration: Migrate the application code, configuration files, and any static assets to the cloud environment. This may involve uploading the code to a code repository (e.g., GitHub, GitLab) and deploying it to the cloud platform. Configure the application to connect to the cloud-based resources, such as databases and storage.
- Data Migration: Migrate the application’s data to the cloud database. The method depends on the database type and the chosen data migration strategy. Consider using database migration services provided by the cloud provider (e.g., AWS Database Migration Service, Azure Database Migration Service) to minimize downtime. If the application uses a relational database, such as MySQL or PostgreSQL, a common approach is to use logical replication or a backup-and-restore strategy.
- Testing and Validation: Thoroughly test the migrated application in the cloud environment. Conduct functional testing, performance testing, and security testing to ensure the application functions correctly, performs optimally, and is secure. Compare the performance of the application in the cloud with its performance in the on-premises environment.
- Cutover and DNS Updates: Once testing is complete and the application is validated, perform the cutover. This involves redirecting traffic from the on-premises application to the cloud-based application. Update the DNS records to point to the cloud-based application’s IP address or load balancer.
- Post-Migration Validation and Optimization: After the cutover, continue monitoring the application’s performance and health. Optimize the cloud resources based on the application’s needs. This may involve scaling resources, adjusting configurations, and implementing cost-optimization strategies. Implement monitoring and alerting to proactively identify and address any issues.
Leveraging Automation Tools for Migration
Automation is crucial for streamlining the migration process, reducing errors, and improving efficiency. Several tools can be used to automate various aspects of the migration.
Consider these areas for automation:
- Infrastructure as Code (IaC): IaC tools, such as Terraform, AWS CloudFormation, Azure Resource Manager, and Google Cloud Deployment Manager, enable the automated provisioning and management of cloud infrastructure. IaC allows you to define infrastructure as code, version it, and apply changes in a consistent and repeatable manner. This reduces manual configuration and minimizes the risk of human error.
- Configuration Management: Configuration management tools, such as Ansible, Chef, and Puppet, automate the configuration of servers and applications. These tools ensure that servers are configured consistently and in accordance with the desired state. They can be used to install software, configure settings, and manage dependencies.
- Deployment Automation: Deployment automation tools, such as Jenkins, GitLab CI/CD, and AWS CodePipeline, automate the deployment of applications to the cloud. These tools can be used to build, test, and deploy code automatically, reducing manual intervention and speeding up the deployment process. For instance, a CI/CD pipeline can be set up to automatically build and deploy an application to AWS Elastic Beanstalk whenever a new code change is pushed to a Git repository.
- Data Migration Automation: Data migration tools, such as AWS Database Migration Service (DMS) and Azure Database Migration Service, automate the process of migrating data from on-premises databases to cloud-based databases. These tools can minimize downtime and ensure data consistency. They support various database types and migration scenarios.
- Testing Automation: Automated testing tools, such as Selenium, JUnit, and Cypress, automate the testing of applications. Automated tests can be run frequently to identify and fix bugs early in the development cycle. They also ensure that the application functions correctly after migration.
By strategically employing these automation tools, organizations can significantly reduce the complexity, time, and cost associated with cloud migration, resulting in a more agile and efficient IT environment.
Testing and Validation
Following the migration of a web application to the cloud, comprehensive testing and validation are critical to ensure the application functions correctly, performs adequately, and remains secure. This phase verifies the successful transfer of the application and its data, ensuring a seamless user experience and minimizing potential disruptions. Rigorous testing helps identify and rectify any issues introduced during the migration process, guaranteeing the application’s stability and reliability in the cloud environment.
Importance of Post-Migration Testing
Thorough testing after migration is essential for several reasons, including verifying the application’s functional correctness, assessing its performance under various loads, and validating its security posture. It also allows for the identification of any compatibility issues that may arise due to differences between the on-premises and cloud environments.
- Functionality Verification: This confirms that all features and functionalities of the application work as expected after the migration. It involves testing all user interfaces, business logic, and data interactions.
- Performance Evaluation: It assesses the application’s speed, responsiveness, and scalability in the cloud environment. Performance testing ensures the application can handle the expected user load without performance degradation.
- Security Assessment: Security testing validates that the application’s security controls, such as authentication, authorization, and data encryption, function correctly in the cloud. It identifies potential vulnerabilities introduced during the migration.
- Data Integrity Check: This ensures that data migrated to the cloud is accurate, complete, and consistent. Data integrity is crucial for the application’s functionality and reliability.
- Compliance Validation: For applications subject to regulatory compliance, testing confirms that the migrated application meets all required compliance standards in the cloud environment.
Creating a Test Plan
A well-defined test plan is crucial for systematically validating the migrated application. This plan Artikels the testing scope, test cases, test data, and expected results. A robust test plan ensures a comprehensive and consistent testing approach.
- Define Testing Scope: Clearly identify the areas of the application to be tested. This includes all critical functionalities, user interfaces, and data interactions. Consider the scope based on the application’s criticality and the changes introduced during migration.
- Develop Test Cases: Create detailed test cases that cover all aspects of the application’s functionality, performance, and security. Each test case should have a specific objective, input data, and expected results. Test cases should be designed to cover both positive and negative scenarios.
- Identify Test Data: Determine the necessary test data to execute the test cases. This includes both real-world data and synthetic data designed to stress-test the application. Data should be representative of the application’s expected usage patterns.
- Establish Testing Environment: Set up a testing environment that mirrors the production environment as closely as possible. This includes the same operating systems, databases, and cloud services used in production.
- Define Performance Metrics: Identify key performance indicators (KPIs) to measure the application’s performance. These KPIs include response time, throughput, and resource utilization.
- Establish Security Testing Procedures: Artikel the security testing procedures, including vulnerability scanning, penetration testing, and security audits. Security testing should be performed regularly.
- Document Test Results: Record all test results, including any defects found and their resolution. Detailed documentation is crucial for tracking progress and identifying recurring issues.
- Define Test Execution Schedule: Create a schedule for executing the test cases. This schedule should align with the migration timeline and allow sufficient time for testing and remediation.
Performance Testing Methodologies
Performance testing evaluates the application’s ability to handle various workloads and identify performance bottlenecks. Different methodologies are used to simulate user traffic and assess the application’s responsiveness and scalability.
- Load Testing: This methodology simulates a specific number of concurrent users to assess the application’s performance under normal load conditions. Load testing helps determine the application’s capacity and identify any performance degradation. For example, a web application might be load tested to simulate 1,000 concurrent users to assess response times and resource utilization.
- Stress Testing: Stress testing pushes the application beyond its normal operating capacity to determine its breaking point. This helps identify the application’s resilience and stability under extreme load conditions. For example, an e-commerce website might be stress tested by simulating a sudden surge in user traffic to see how it handles a flash sale.
- Endurance Testing (Soak Testing): Endurance testing, also known as soak testing, assesses the application’s performance over an extended period under sustained load. This helps identify memory leaks and other long-term performance issues. For example, a database application might be subjected to endurance testing for 24 hours to monitor its memory usage and ensure stability.
- Spike Testing: Spike testing simulates a sudden and significant increase in user traffic to assess the application’s ability to handle unexpected bursts of activity. This helps identify potential bottlenecks and ensure the application remains responsive during peak loads. For example, a news website might use spike testing to see how it performs when a major news story breaks, causing a sudden influx of visitors.
Example: An e-commerce application migrated to AWS is subjected to load testing to simulate 5,000 concurrent users. The test results reveal that the application’s response time increases significantly, and CPU utilization reaches 90%. This indicates a performance bottleneck that needs to be addressed, such as scaling up the application servers or optimizing database queries.
Optimizing and Scaling in the Cloud
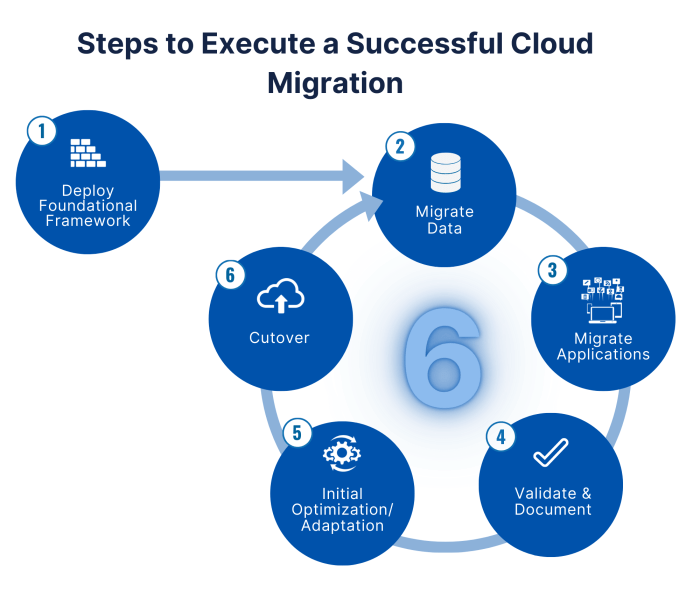
Migrating a web application to the cloud offers significant opportunities for optimization and scalability, moving beyond the limitations of on-premise infrastructure. Effectively leveraging cloud resources requires a strategic approach to performance tuning, resource allocation, and continuous monitoring. This section details strategies for optimizing application performance, implementing auto-scaling and load balancing, and establishing best practices for monitoring and management within a cloud environment.
Strategies for Optimizing Application Performance in the Cloud
Optimizing application performance in the cloud involves a multi-faceted approach, considering various factors that influence speed, responsiveness, and resource utilization. This includes code optimization, database tuning, and efficient use of cloud-specific services.
- Code Optimization: Reviewing and optimizing application code is a fundamental step. Identify and eliminate bottlenecks, such as inefficient algorithms or poorly written database queries. Profiling tools can help pinpoint performance-critical sections of the code. For example, a poorly optimized SQL query can significantly impact response times. Consider rewriting it or adding indexes to improve performance.
- Caching Strategies: Implementing effective caching mechanisms can dramatically improve performance by reducing the load on backend systems. This includes caching static content (images, CSS, JavaScript) at the edge using a Content Delivery Network (CDN). Implement server-side caching using tools like Redis or Memcached to store frequently accessed data.
- Database Optimization: The database is often a performance bottleneck. Optimize database queries, ensure proper indexing, and consider database scaling options. Choose the right database type (e.g., relational, NoSQL) for the application’s needs. Monitoring database performance metrics is crucial for identifying areas for improvement.
- Resource Allocation and Management: Carefully manage the allocation of cloud resources. Right-size virtual machines (VMs) to match workload demands, avoiding over-provisioning, which leads to wasted resources, or under-provisioning, which can degrade performance. Regularly review and adjust resource allocations based on application performance and traffic patterns.
- Leveraging Cloud-Specific Services: Cloud providers offer a range of services that can optimize performance. Utilize managed services for databases, caching, and message queues. These services are often optimized for the cloud environment and can reduce operational overhead.
- Application Monitoring and Profiling: Implement robust application monitoring to track performance metrics such as response times, error rates, and resource utilization. Use profiling tools to identify performance bottlenecks within the code. Continuous monitoring enables proactive identification and resolution of performance issues.
Implementing Auto-Scaling and Load Balancing
Auto-scaling and load balancing are crucial for ensuring application availability, performance, and cost-effectiveness in the cloud. These features dynamically adjust resources based on demand, distributing traffic across multiple instances and scaling the application up or down as needed.
- Load Balancing: Load balancing distributes incoming traffic across multiple instances of the application, preventing any single instance from being overloaded. This improves application availability and response times. Configure a load balancer to monitor the health of each instance and route traffic only to healthy instances. Consider using different load balancing algorithms, such as round robin or least connections, depending on the application’s needs.
- Auto-Scaling: Auto-scaling automatically adjusts the number of application instances based on predefined metrics, such as CPU utilization, memory usage, or request queue length. This ensures that the application has sufficient resources to handle peak loads and scales down resources during periods of low demand, optimizing costs. Define scaling policies that specify when to scale up or down and the number of instances to add or remove.
- Health Checks: Implement health checks to monitor the status of application instances. The load balancer uses health checks to determine if an instance is healthy and can receive traffic. Health checks typically involve sending requests to a specific endpoint and verifying the response.
- Configuration and Deployment: Integrate auto-scaling and load balancing into the application deployment process. Use Infrastructure as Code (IaC) tools to automate the configuration of these services. This ensures consistency and repeatability across different environments.
- Examples of Auto-Scaling in Action: Consider an e-commerce website that experiences a surge in traffic during a holiday sale. Auto-scaling can automatically increase the number of application instances to handle the increased load, ensuring that customers can continue to browse and make purchases without experiencing performance issues. During off-peak hours, the system can scale down to reduce costs.
Best Practices for Monitoring and Managing Your Application in the Cloud
Effective monitoring and management are essential for maintaining application health, identifying and resolving issues, and optimizing performance in the cloud. This involves establishing comprehensive monitoring, setting up alerts, and proactively managing resources.
- Comprehensive Monitoring: Implement comprehensive monitoring across all aspects of the application, including infrastructure, application code, and user experience. Collect metrics such as CPU utilization, memory usage, network traffic, response times, error rates, and database performance.
- Alerting and Notifications: Set up alerts based on predefined thresholds for critical metrics. Configure notifications to be sent to the appropriate teams when alerts are triggered. This enables proactive identification and resolution of issues before they impact users.
- Logging and Tracing: Implement robust logging to capture application events and errors. Use distributed tracing to track requests across multiple services and identify performance bottlenecks. Centralize logs for easy analysis and troubleshooting.
- Cost Optimization: Continuously monitor cloud costs and identify opportunities for optimization. Right-size resources, leverage reserved instances or savings plans, and use cost-effective storage options. Regularly review resource usage and identify any unused or underutilized resources.
- Security Monitoring: Implement security monitoring to detect and respond to security threats. Monitor for suspicious activity, such as unauthorized access attempts or unusual network traffic. Use security tools to scan for vulnerabilities and ensure compliance with security best practices.
- Automation and Orchestration: Automate routine tasks, such as deployments, scaling, and backups. Use orchestration tools to manage complex deployments and ensure consistency across different environments.
- Regular Reviews and Optimization: Regularly review application performance, resource utilization, and costs. Identify areas for improvement and implement optimizations based on data-driven insights. This includes reviewing logs, monitoring dashboards, and analyzing performance metrics.
Security Considerations in the Cloud
Migrating a web application to the cloud necessitates a fundamental shift in how security is approached. The shared responsibility model, where the cloud provider secures the infrastructure and the user secures their data and applications, is paramount. Effective security in the cloud requires a proactive, layered approach, encompassing various measures to protect against threats and ensure data integrity and availability.
This section details best practices, configuration steps, and mitigation strategies for cloud-based web application security.
Security Best Practices for Web Applications in the Cloud
Adhering to security best practices is crucial for safeguarding web applications in the cloud. These practices encompass a wide range of considerations, from access control to data encryption, and are essential for mitigating risks and maintaining a robust security posture.
- Implement Strong Access Controls: This involves using the principle of least privilege, granting users only the necessary permissions. Multi-factor authentication (MFA) should be enforced for all user accounts and administrative access. Regularly review and audit access permissions to ensure they remain appropriate. Consider role-based access control (RBAC) to simplify permission management.
- Encrypt Data at Rest and in Transit: Encryption is a fundamental security practice. All sensitive data, both while stored (at rest) and while being transferred over networks (in transit), should be encrypted. Use industry-standard encryption algorithms like AES-256 for data at rest and TLS/SSL for data in transit. Implement key management best practices to securely manage encryption keys.
- Regularly Update and Patch Software: Keep all software, including operating systems, web servers, databases, and application frameworks, up-to-date with the latest security patches. Automate the patching process whenever possible to minimize the time vulnerabilities exist. Regularly scan for vulnerabilities using automated tools.
- Implement Web Application Firewalls (WAFs): WAFs are designed to protect web applications from common attacks such as SQL injection, cross-site scripting (XSS), and denial-of-service (DoS) attacks. Choose a WAF that offers features such as bot mitigation, rate limiting, and custom rule creation.
- Monitor and Log Security Events: Implement comprehensive logging and monitoring of security events. Centralize logs from all components of the application and infrastructure. Use security information and event management (SIEM) systems to analyze logs, detect anomalies, and generate alerts for suspicious activities.
- Conduct Regular Security Audits and Penetration Testing: Regularly assess the security posture of the application through security audits and penetration testing. Identify vulnerabilities and weaknesses and remediate them promptly. Simulate real-world attacks to evaluate the effectiveness of security controls.
- Implement Data Loss Prevention (DLP): DLP solutions help prevent sensitive data from leaving the organization’s control. They can identify and monitor sensitive data, and enforce policies to prevent unauthorized access, use, disclosure, disruption, modification, or destruction.
- Use Secure Configuration Management: Employ configuration management tools to ensure consistent and secure configurations across all infrastructure components. Automate configuration changes and enforce security policies.
- Educate and Train Personnel: Provide regular security awareness training to all employees, including developers, administrators, and end-users. Educate them about common threats, best practices, and security policies.
Configuring Security Groups, Firewalls, and Other Security Measures
Configuring security groups, firewalls, and other security measures is a critical aspect of cloud security. These tools act as the first line of defense, controlling network traffic and protecting the application from unauthorized access. The configuration process involves defining rules and policies that govern network traffic flow.
- Security Groups: Security groups act as virtual firewalls for instances (virtual machines) in the cloud. They control inbound and outbound traffic at the instance level.
- Configuration Steps:
- Define inbound rules to allow only necessary traffic (e.g., HTTP/HTTPS for web traffic, SSH for secure access).
- Define outbound rules to control traffic leaving the instance (e.g., allow access to databases).
- Use the principle of least privilege, allowing only the minimum required ports and protocols.
- Regularly review and update security group rules as the application evolves.
- Example: To allow web traffic (port 80 and 443) to a web server, create inbound rules that allow traffic from any source (0.0.0.0/0) on ports 80 and 443. For SSH access, allow traffic on port 22 from a specific IP address or range.
- Configuration Steps:
- Firewalls: Cloud providers offer firewalls that operate at the network level, protecting entire subnets or virtual networks.
- Configuration Steps:
- Configure firewall rules to control traffic flow between subnets or virtual networks.
- Define rules to allow or deny traffic based on source/destination IP addresses, ports, and protocols.
- Implement network segmentation to isolate different parts of the application.
- Use intrusion detection and prevention systems (IDS/IPS) to detect and block malicious traffic.
- Example: To restrict access to a database server to only the application servers, configure firewall rules to allow traffic on the database port (e.g., 3306 for MySQL) only from the application server’s IP address range.
- Configuration Steps:
- Network Access Control Lists (ACLs): ACLs provide an additional layer of network security.
- Configuration Steps:
- Define rules to allow or deny traffic based on source/destination IP addresses, ports, and protocols.
- ACLs operate at the subnet level, controlling traffic flow in and out of the subnet.
- Prioritize ACL rules to ensure the desired traffic flow.
- Example: You can configure an ACL to deny all inbound traffic to a specific subnet except for traffic on port 22 (SSH) from a specific IP address range.
- Configuration Steps:
- Other Security Measures:
- Web Application Firewalls (WAFs): Deploy WAFs to protect against application-layer attacks.
- Intrusion Detection and Prevention Systems (IDS/IPS): Implement IDS/IPS to detect and block malicious traffic.
- Regular Vulnerability Scanning: Perform regular vulnerability scans to identify and remediate vulnerabilities.
Examples of Security Threats and Mitigation Strategies
Cloud-based web applications face a variety of security threats. Understanding these threats and implementing appropriate mitigation strategies is essential for maintaining a secure environment.
- SQL Injection (SQLi): SQLi attacks exploit vulnerabilities in the application’s database interaction. Attackers inject malicious SQL code into input fields, allowing them to access, modify, or delete data.
- Mitigation:
- Use parameterized queries or prepared statements to prevent the execution of malicious SQL code.
- Validate and sanitize all user inputs to prevent the injection of malicious characters.
- Implement a WAF to detect and block SQLi attempts.
- Mitigation:
- Cross-Site Scripting (XSS): XSS attacks involve injecting malicious scripts into web pages viewed by other users. These scripts can steal user credentials, redirect users to malicious websites, or deface the website.
- Mitigation:
- Encode user-supplied data before displaying it on web pages.
- Use a Content Security Policy (CSP) to restrict the sources from which the browser can load resources.
- Implement a WAF to detect and block XSS attempts.
- Mitigation:
- Distributed Denial-of-Service (DDoS) Attacks: DDoS attacks aim to overwhelm a web application with traffic, making it unavailable to legitimate users.
- Mitigation:
- Use a cloud provider’s DDoS protection services.
- Implement rate limiting to restrict the number of requests from a single IP address.
- Use a WAF to detect and mitigate DDoS attacks.
- Mitigation:
- Data Breaches: Data breaches involve unauthorized access to sensitive data, leading to data theft or exposure.
- Mitigation:
- Encrypt data at rest and in transit.
- Implement strong access controls and multi-factor authentication.
- Regularly audit and monitor security logs.
- Implement data loss prevention (DLP) solutions.
- Mitigation:
- Account Takeover: Attackers gain unauthorized access to user accounts, often through phishing or credential stuffing.
- Mitigation:
- Enforce multi-factor authentication (MFA).
- Implement strong password policies.
- Monitor for suspicious login activity.
- Educate users about phishing attacks.
- Mitigation:
- Vulnerability Exploitation: Attackers exploit vulnerabilities in software or infrastructure to gain unauthorized access or control.
- Mitigation:
- Regularly update and patch software.
- Perform regular vulnerability scans.
- Implement a WAF.
- Use a web application firewall.
- Mitigation:
Epilogue
In conclusion, migrating a web application to the cloud is a multifaceted endeavor that requires careful planning, execution, and continuous optimization. By understanding the fundamentals, selecting the right cloud services, and implementing a well-defined migration strategy, organizations can leverage the benefits of cloud computing, including scalability, cost efficiency, and enhanced security. This guide serves as a foundational resource for navigating the complexities of cloud migration and achieving a successful transition, ultimately transforming the way web applications are developed, deployed, and managed.
FAQ Section
What are the key benefits of migrating to the cloud?
Key benefits include improved scalability, cost optimization through pay-as-you-go models, enhanced security features, increased availability and reliability, and the ability to focus on core business functions rather than infrastructure management.
What is the difference between rehosting and replatforming?
Rehosting, also known as “lift and shift,” involves moving an application to the cloud with minimal changes. Replatforming involves making some changes to the application to take advantage of cloud-native services but without fundamentally altering the core architecture.
How do I choose the right cloud provider?
The choice depends on factors like application requirements, budget, existing IT infrastructure, and the availability of services. Evaluating providers based on their compute, storage, database, and security offerings is crucial. A decision matrix can help with this evaluation.
What are the biggest challenges in cloud migration?
Common challenges include application compatibility, data migration complexity, security concerns, cost management, and the need for skilled personnel. Careful planning and execution are essential to mitigate these challenges.
How can I ensure data consistency during migration?
Data consistency can be ensured through methods like minimizing downtime, using data replication tools, and testing data integrity post-migration. Choosing the right migration method (online or offline) also impacts consistency.