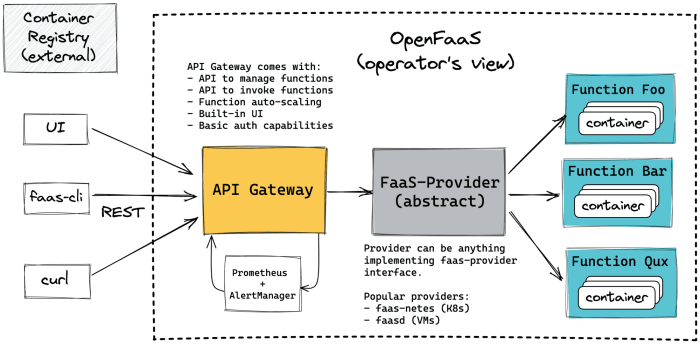
Managing infrastructure as code (IaC) for serverless applications represents a paradigm shift in software development and deployment. This approach leverages automation and declarative configurations to define, provision, and manage serverless resources such as functions, APIs, and databases. By embracing IaC, developers can streamline the entire infrastructure lifecycle, enhancing scalability, reducing operational costs, and improving overall efficiency. The transition from traditional infrastructure management to IaC for serverless environments demands a deep understanding of its core principles, available tools, and best practices to realize its full potential.
Serverless computing, at its core, abstracts away server management, allowing developers to focus on writing and deploying code without worrying about underlying infrastructure. This characteristic necessitates a robust and adaptable infrastructure management strategy. IaC emerges as the ideal solution, enabling automated provisioning, version control, and consistent deployments across various environments. This ensures that infrastructure configurations are reproducible, traceable, and easily maintained, thereby promoting agility and reducing the risk of human error.
The benefits extend to enhanced collaboration, streamlined CI/CD pipelines, and improved cost optimization, making IaC a critical component of any modern serverless architecture.
Introduction to Infrastructure as Code (IaC) for Serverless
Infrastructure as Code (IaC) has become a critical practice for modern software development, and its importance is amplified within serverless architectures. This approach treats infrastructure as code, allowing for automated provisioning, management, and version control of resources. This contrasts with traditional, manual infrastructure management, which is prone to human error and difficult to scale. IaC, when applied to serverless environments, unlocks significant benefits in terms of agility, efficiency, and cost-effectiveness.Serverless computing is a cloud computing execution model where the cloud provider dynamically manages the allocation of machine resources.
Developers write and deploy code without needing to manage the underlying servers. The cloud provider handles all aspects of server management, including provisioning, scaling, and patching. This model allows developers to focus on writing code and business logic, rather than operational overhead.
Core Concepts of IaC
IaC fundamentally involves defining and managing infrastructure through code. This code is typically written in declarative formats, specifying the desired state of the infrastructure. This approach contrasts with imperative methods, where the steps to achieve a particular state are defined.* Declarative Approach: IaC primarily utilizes declarative approaches, where the desired end-state of the infrastructure is defined. The IaC tool then automatically provisions and configures the resources to match this defined state.
Example
In a serverless environment, a developer might declare that they want an AWS Lambda function with specific memory and timeout settings. The IaC tool, such as AWS CloudFormation or Terraform, will handle the creation and configuration of the Lambda function based on this declaration.
Version Control
IaC allows infrastructure definitions to be stored in version control systems, such as Git. This enables tracking changes, rolling back to previous configurations, and collaborating on infrastructure management.
Benefits
Auditability
Every change to the infrastructure is logged and can be traced back to a specific commit.
Collaboration
Multiple team members can work on infrastructure changes concurrently.
Rollbacks
Easily revert to a previous infrastructure state in case of errors or issues.
Automation
IaC facilitates automation in infrastructure provisioning and management. IaC tools automatically provision, configure, and manage infrastructure resources based on the code definitions.
Impact
Reduced Manual Effort
Automates repetitive tasks, reducing the need for manual intervention.
Faster Deployment
Speeds up the deployment of infrastructure resources.
Consistency
Ensures consistent infrastructure configurations across environments.
Benefits of IaC for Serverless
IaC offers several advantages when applied to serverless architectures, leading to improved scalability, cost optimization, and automation.* Scalability: Serverless architectures are inherently scalable, and IaC further enhances this capability. IaC allows for the automated provisioning of infrastructure components as needed to handle increasing workloads.
Mechanism
IaC tools can automatically provision additional Lambda function instances or other serverless resources based on defined triggers, such as CPU utilization or request rates.
Example
Using AWS Auto Scaling with an IaC definition allows for the automatic scaling of an API Gateway endpoint based on traffic volume, ensuring optimal performance and responsiveness.
Cost Optimization
IaC can help to optimize costs in serverless environments by enabling the efficient management of resources and preventing over-provisioning.
Methods
Resource Tagging
IaC allows for the tagging of resources, which can be used to track costs and allocate them to specific projects or teams.
Right-Sizing
IaC allows for the easy adjustment of resource sizes and configurations to match actual usage patterns, preventing unnecessary costs.
Automated Cleanup
IaC can be used to automatically delete unused resources, such as test environments, to minimize costs.
Example
Implementing IaC with tools like Terraform allows for defining and managing the resource configurations. For example, defining the memory allocation for Lambda functions. It can also be used to identify and eliminate unused resources, resulting in cost savings.
Automation
IaC automates the entire lifecycle of serverless infrastructure, from provisioning to deployment and management.
Impact
Faster Deployment Cycles
IaC streamlines the deployment process, allowing for faster iteration and quicker time-to-market.
Reduced Errors
Automation minimizes the risk of human error, leading to more reliable infrastructure.
Improved Consistency
IaC ensures that infrastructure configurations are consistent across all environments, reducing the risk of inconsistencies.
Example
Using IaC, developers can define the complete serverless infrastructure, including Lambda functions, API gateways, and databases, in a single code repository. This code can then be used to automatically deploy and manage the entire application stack, from development to production.
Choosing the Right IaC Tool for Serverless
Selecting the appropriate Infrastructure as Code (IaC) tool is crucial for successfully managing serverless applications. The choice significantly impacts development velocity, maintainability, and operational efficiency. Different tools offer varying levels of abstraction, feature sets, and provider support, necessitating a careful evaluation based on project needs and team expertise. This section will explore popular IaC tools for serverless, comparing their capabilities and outlining criteria for informed decision-making.
Popular IaC Tools for Serverless
Several IaC tools are well-suited for serverless deployments, each with its own strengths and weaknesses. These tools provide the means to define, provision, and manage serverless infrastructure in a programmatic and repeatable manner. They facilitate the automation of tasks such as creating and configuring functions, APIs, databases, and other necessary resources.
- AWS CloudFormation: CloudFormation is a native Infrastructure as Code (IaC) service provided by Amazon Web Services (AWS). It allows users to define their infrastructure using declarative templates, which are written in either YAML or JSON. CloudFormation is tightly integrated with the AWS ecosystem, offering seamless support for all AWS services, including serverless components like Lambda, API Gateway, DynamoDB, and S3.
Its key advantage lies in its deep integration with AWS, ensuring that new features and services are supported quickly.
- Terraform: Terraform, developed by HashiCorp, is a popular open-source IaC tool that supports multiple cloud providers, including AWS, Google Cloud Platform, Microsoft Azure, and others. It uses a declarative configuration language (HashiCorp Configuration Language – HCL) to define infrastructure. Terraform’s cross-cloud compatibility makes it an attractive option for organizations using a multi-cloud strategy. It offers a robust state management system and a rich ecosystem of providers and modules, enabling the reuse of infrastructure configurations.
- Serverless Framework: The Serverless Framework is an open-source framework specifically designed for building and deploying serverless applications. It simplifies the process of creating, deploying, and managing serverless functions and related resources. The Serverless Framework uses a YAML configuration file (serverless.yml) to define the application’s infrastructure and deployment configurations. It abstracts away many of the complexities of serverless deployments, allowing developers to focus on writing code rather than managing infrastructure.
Comparison of IaC Tools for Serverless
A comparative analysis of these tools reveals their distinct characteristics. This comparison focuses on features particularly relevant to serverless development, including provider support, language used for configuration, and ease of use.
| Tool | Provider Support | Language | Ease of Use |
|---|---|---|---|
| AWS CloudFormation | AWS Only | YAML or JSON | Steep learning curve initially, but excellent integration with AWS services. |
| Terraform | Multi-cloud (AWS, GCP, Azure, etc.) | HCL (HashiCorp Configuration Language) | Moderate learning curve; powerful and flexible but can be complex for simple serverless deployments. |
| Serverless Framework | Multi-cloud (AWS, Azure, Google Cloud, etc.) | YAML | Easy to use, specifically designed for serverless; abstracts away many complexities. |
Criteria for Selecting an IaC Tool
Choosing the right IaC tool depends on several factors, including project requirements, team expertise, and organizational strategy. Carefully evaluating these criteria ensures that the selected tool aligns with the project’s needs and promotes efficient and sustainable serverless development.
- Provider Support: The primary cloud provider(s) used by the project should be the first consideration. AWS CloudFormation is the natural choice if the project is solely on AWS, while Terraform offers multi-cloud support for environments spanning multiple providers. The Serverless Framework also supports multiple providers.
- Team Expertise: The existing skills and experience of the development team are crucial. Teams familiar with YAML and JSON might find AWS CloudFormation or the Serverless Framework easier to adopt initially. Teams with experience in configuration management tools might be more comfortable with Terraform and HCL.
- Project Complexity: The complexity of the serverless application influences the choice. For simple serverless applications, the Serverless Framework’s simplicity can be advantageous. For more complex infrastructure deployments involving various resources and cross-cloud deployments, Terraform’s flexibility and multi-cloud support become more valuable.
- Integration with CI/CD Pipelines: The chosen IaC tool should integrate seamlessly with the project’s continuous integration and continuous delivery (CI/CD) pipelines. CloudFormation, Terraform, and the Serverless Framework all offer features and integrations that facilitate automated deployments and infrastructure management.
- Community Support and Documentation: A strong community and comprehensive documentation are vital for troubleshooting and learning. Terraform and the Serverless Framework have large and active communities, providing ample resources and support. AWS CloudFormation also benefits from extensive AWS documentation.
Designing Serverless Infrastructure with IaC
Designing serverless infrastructure with Infrastructure as Code (IaC) is a critical practice for automating deployments, ensuring consistency, and enabling scalability. This process involves defining your serverless components – functions, APIs, databases, and event triggers – in a declarative format, allowing for reproducible and version-controlled infrastructure. Effectively designing serverless infrastructure with IaC promotes agility, reduces operational overhead, and minimizes the risk of configuration drift.
Designing Serverless Infrastructure Components
Designing serverless infrastructure components involves defining each element within your serverless architecture using IaC. This approach ensures that all components are created and managed consistently. This includes functions, APIs, databases, and event triggers, all of which are crucial for building serverless applications.
- Functions: Serverless functions, often implemented using platforms like AWS Lambda, Azure Functions, or Google Cloud Functions, are the core compute units. Designing them with IaC involves defining their code, runtime environment (e.g., Node.js, Python), memory allocation, timeout settings, and any environment variables they require. IaC templates specify the function’s execution role, granting it the necessary permissions to access other resources.
- APIs: APIs, typically managed by API gateways such as AWS API Gateway, are the entry points for interacting with serverless functions. IaC templates define the API endpoints, request methods (e.g., GET, POST), and the integration with the underlying functions. They also manage authentication, authorization, and rate limiting. Configuration within IaC ensures consistent API behavior across environments.
- Databases: Serverless applications often rely on databases like Amazon DynamoDB, Azure Cosmos DB, or Google Cloud Datastore. IaC defines the database schema, including tables, indexes, and provisioned throughput. It also configures access control policies, ensuring secure access to the database resources. IaC helps to establish database infrastructure alongside the functions and APIs, providing a complete solution.
- Event Triggers: Event triggers, such as those from Amazon S3 bucket events, Azure Event Grid, or Google Cloud Pub/Sub, initiate function execution in response to specific events. IaC defines the event source, the event type (e.g., object creation, file upload), and the target function. This enables event-driven architectures, where functions react automatically to external events.
Best Practices for Organizing IaC Code
Adopting best practices for organizing IaC code is crucial for maintainability, reusability, and collaboration. A well-organized codebase minimizes errors, simplifies updates, and enhances team productivity. These practices include modularization, reusability, and version control.
- Modularization: Modularization involves breaking down the IaC code into reusable, self-contained modules. Each module represents a logical unit of infrastructure, such as a database, an API endpoint, or a specific function configuration. This approach enhances code organization, reduces redundancy, and promotes reusability. Modules can be parameterized to accommodate different configurations across environments (e.g., development, staging, production).
- Reusability: Reusability is achieved by designing modules that can be used across multiple projects or within the same project to deploy similar infrastructure components. This avoids code duplication and ensures consistency. Reusable modules should be well-documented, providing clear instructions on how to use them and what parameters they accept.
- Version Control: Version control, using systems like Git, is essential for managing IaC code. It allows for tracking changes, collaborating with team members, and reverting to previous versions if necessary. Each change to the IaC code should be committed with a descriptive message, explaining the purpose of the change. Branching and merging strategies are employed to manage feature development and releases effectively.
IaC Templates for Common Serverless Patterns
IaC templates streamline the deployment of common serverless patterns, such as API gateway integrations with Lambda functions. These templates provide a starting point for defining and deploying serverless architectures. Examples of templates for different patterns can be created with tools like AWS CloudFormation (YAML or JSON), Terraform (HCL), or Azure Resource Manager (JSON).
- API Gateway with Lambda Functions: This pattern defines an API endpoint that triggers a Lambda function. The IaC template defines the API Gateway, including its REST API, methods (e.g., GET, POST), and request/response models. It specifies the integration with the Lambda function, including the function’s ARN and any necessary permissions.
- Event-Driven Processing with S3 and Lambda: This pattern uses an Amazon S3 bucket to trigger a Lambda function. The IaC template defines the S3 bucket, including its access policies. It defines the Lambda function, its execution role, and its triggers for the bucket events (e.g., object creation, object deletion).
- Database with DynamoDB and Lambda: This pattern creates a DynamoDB table and a Lambda function that can interact with the table. The IaC template defines the DynamoDB table, including its schema and provisioned throughput. It defines the Lambda function, its execution role, and the permissions to access the DynamoDB table.
Example: API Gateway with Lambda Functions (AWS CloudFormation YAML)
This YAML template illustrates a basic API Gateway setup with a Lambda function integration:
Resources: MyLambdaFunction: Type: AWS::Lambda::Function Properties: Handler: index.handler Runtime: nodejs18.x Code: ZipFile: | exports.handler = async (event) => return statusCode: 200, body: 'Hello from Lambda!' ; ; Role: !GetAtt LambdaExecutionRole.Arn LambdaExecutionRole: Type: AWS::IAM::Role Properties: AssumeRolePolicyDocument: Version: '2012-10-17' Statement: -Effect: Allow Principal: Service: lambda.amazonaws.com Action: sts:AssumeRole Policies: -PolicyName: root PolicyDocument: Version: '2012-10-17' Statement: -Effect: Allow Action: -logs:CreateLogGroup -logs:CreateLogStream -logs:PutLogEvents Resource: arn:aws:logs:*:*:* MyApiGateway: Type: AWS::ApiGateway::RestApi Properties: Name: MyServerlessApi Description: API Gateway for Lambda function MyApiGatewayResource: Type: AWS::ApiGateway::Resource Properties: ParentId: !GetAtt MyApiGateway.RootResourceId PathPart: hello RestApiId: !Ref MyApiGateway MyApiGatewayMethod: Type: AWS::ApiGateway::Method Properties: HttpMethod: GET AuthorizerId: !Ref MyApiGatewayAuthorizer ResourceId: !Ref MyApiGatewayResource RestApiId: !Ref MyApiGateway AuthorizationType: NONE # Change to AWS_IAM or COGNITO_USER_POOLS for authentication MethodResponses: -StatusCode: '200' ResponseModels: application/json: 'Empty' MyApiGatewayIntegration: Type: AWS::ApiGateway::Integration Properties: HttpMethod: GET ResourceId: !Ref MyApiGatewayResource RestApiId: !Ref MyApiGateway Type: AWS_PROXY IntegrationHttpMethod: POST Uri: !Sub "arn:aws:apigateway:$AWS::Region:lambda:path/2015-03-31/functions/$MyLambdaFunction.Arn/invocations" MyApiGatewayDeployment: Type: AWS::ApiGateway::Deployment DependsOn: MyApiGatewayIntegration Properties: RestApiId: !Ref MyApiGateway StageName: prod MyApiGatewayInvokePermission: Type: AWS::Lambda::Permission Properties: FunctionName: !Ref MyLambdaFunction Action: lambda:InvokeFunction Principal: apigateway.amazonaws.com SourceArn: !Sub "arn:aws:execute-api:$AWS::Region:$AWS::AccountId:$MyApiGateway/*/*"Outputs: ApiEndpoint: Description: "API endpoint URL" Value: !Sub "https://$MyApiGateway.execute-api.$AWS::Region.amazonaws.com/prod/hello" In this example, the template defines a Lambda function, an IAM role for execution, an API Gateway with a GET method on the /hello resource, and the necessary integration between the API Gateway and the Lambda function. The template also outputs the API endpoint URL.
Implementing IaC Best Practices for Serverless
Adopting Infrastructure as Code (IaC) for serverless architectures brings significant benefits, including automation, repeatability, and version control. However, to fully realize these advantages, it’s crucial to implement best practices. This involves establishing robust version control, rigorous testing, and proactive security measures. This section delves into these key areas, providing practical guidance for building and managing serverless infrastructure effectively.
Version Control Strategies for IaC Code
Effective version control is paramount for managing IaC code, enabling collaboration, tracking changes, and facilitating rollbacks. Utilizing a distributed version control system like Git is a standard practice.
- Git Workflows: A well-defined Git workflow promotes collaboration and code quality. The Gitflow workflow is a popular choice, employing distinct branches for features, releases, and hotfixes. The feature branch model isolates new functionality, allowing developers to work independently. When a feature is complete, it’s merged into the `develop` branch. Release branches are created from `develop` to prepare for production deployments, and hotfix branches address critical issues in production.
The `main` branch represents the production-ready code. This branching model, while effective, can become complex for smaller teams. Alternative workflows, such as GitHub Flow or GitLab Flow, offer simpler approaches suitable for less complex projects. For example, in GitHub Flow, all changes are made directly to the `main` branch, with feature branches used for larger changes and pull requests for code review.
- Branching Models: The choice of a branching model depends on team size, project complexity, and deployment frequency. For smaller projects with continuous integration and continuous delivery (CI/CD) pipelines, a simpler model like GitHub Flow may suffice. Larger projects with frequent releases and a need for extensive testing often benefit from Gitflow. Consider the implications of each model on merge conflicts, code reviews, and the overall development process.
For example, a team using Gitflow might experience more merge conflicts due to the longer lifespan of feature branches, while a team using GitHub Flow might experience fewer, but needs to carefully manage deployments directly from `main`.
- Commit Messages: Clear and concise commit messages are essential for understanding the history of changes. They should explain
-why* a change was made, not just
-what* was changed. Use a consistent format, such as the conventional commits standard, which includes a type (e.g., `feat`, `fix`, `chore`), a scope (optional), and a description. This allows for automated generation of changelogs and easier identification of the purpose of each commit.For example, a commit message like `feat(auth): Implement user authentication using AWS Cognito` is much more informative than `updated authentication`.
- Code Reviews: Code reviews are crucial for ensuring code quality and catching potential issues before deployment. Implement a pull request process where changes are reviewed by other team members before merging into the main branch. This allows for peer review, identifying potential bugs, and enforcing coding standards. Automated checks, such as linters and static analysis tools, should be integrated into the pull request process to automatically check for style violations, security vulnerabilities, and other potential issues.
Strategies for Testing IaC Templates Before Deployment
Testing IaC templates is crucial to ensure they behave as expected and that deployments are reliable. This involves a layered approach that includes unit tests and integration tests.
- Unit Tests: Unit tests verify the functionality of individual components within an IaC template. For serverless applications, this might involve testing the configuration of a single Lambda function, an API Gateway route, or a DynamoDB table. The goal is to isolate each component and test its behavior in isolation. Tools like `Terratest` for Terraform or specialized testing frameworks for CloudFormation can be used to write these tests.
Unit tests should be fast to execute and provide quick feedback on code changes. For example, a unit test for a Lambda function could verify that the function’s configuration, such as memory allocation and timeout settings, are correct.
- Integration Tests: Integration tests verify the interaction between different components of the infrastructure. They simulate the deployment of the entire IaC template or a significant portion of it and validate that the deployed resources interact correctly. This might involve testing the communication between a Lambda function and an API Gateway, or the data flow between a Lambda function and a database.
Integration tests typically take longer to execute than unit tests because they involve deploying and interacting with real cloud resources. For example, an integration test could deploy an API Gateway, a Lambda function, and a DynamoDB table, then send a request to the API Gateway and verify that the data is correctly stored in the DynamoDB table.
- Test Doubles: Employing test doubles, such as mocks and stubs, can significantly improve the speed and reliability of testing. Mocks simulate the behavior of external dependencies, allowing you to test a component in isolation without relying on the availability of the actual resources. Stubs provide pre-defined responses for external calls, enabling controlled testing scenarios. For instance, when testing a Lambda function that interacts with a database, a mock database can be used to simulate the database’s behavior, preventing the need to deploy a real database for each test run.
- Infrastructure Validation Tools: Tools like `cfn-lint` for CloudFormation templates and `terraform validate` for Terraform configurations can be used to perform static analysis and validate the syntax and structure of IaC templates. These tools can identify common errors and potential issues before deployment. These validations should be integrated into the CI/CD pipeline to automatically check the IaC templates before deployment.
Security Considerations for IaC
Security is a critical aspect of IaC, and it must be integrated throughout the entire development lifecycle. This includes access control, encryption, and compliance.
- Access Control: Implement the principle of least privilege, granting only the necessary permissions to each user and service. Use IAM roles to define the permissions for your serverless resources, and avoid using hardcoded credentials in your IaC templates. Regularly review and audit IAM policies to ensure they are up-to-date and aligned with security best practices. For example, a Lambda function should only have the permissions required to access the resources it needs, such as a DynamoDB table or an S3 bucket.
- Encryption: Encrypt sensitive data both in transit and at rest. Use encryption keys managed by a key management service (KMS) to protect your data. Configure encryption for storage services like S3 and DynamoDB. For example, encrypting S3 buckets using KMS prevents unauthorized access to the data stored within. Ensure all data transferred between services is encrypted using TLS/SSL.
- Compliance: Adhere to relevant compliance standards, such as HIPAA, PCI DSS, and GDPR. Use IaC to automate the deployment and configuration of resources that meet these compliance requirements. Regularly audit your infrastructure to ensure it remains compliant. Tools like `AWS Config` can be used to monitor the configuration of your resources and detect any non-compliant changes.
For example, if your application handles sensitive patient data, you must ensure that all data is encrypted and that access to the data is strictly controlled.
- Security Scanning: Integrate security scanning tools into your CI/CD pipeline to automatically scan your IaC templates for vulnerabilities. These tools can identify potential security issues, such as misconfigured security groups, exposed secrets, and insecure configurations. Tools like `tfsec` for Terraform and `cfn-nag` for CloudFormation can automatically check for security vulnerabilities. For example, a security scan might identify a security group that allows unrestricted access from the internet, which can be easily addressed.
- Secret Management: Never hardcode sensitive information, such as API keys, database passwords, or access tokens, directly in your IaC templates. Use a secrets management service, such as AWS Secrets Manager or HashiCorp Vault, to securely store and manage your secrets. These services provide features like encryption, access control, and rotation of secrets. For example, instead of storing a database password in your IaC template, you should store it in Secrets Manager and retrieve it dynamically during deployment.
Automating Serverless Deployments with IaC
Automating serverless deployments with Infrastructure as Code (IaC) is crucial for achieving efficiency, consistency, and reliability in the development lifecycle. By integrating IaC with Continuous Integration and Continuous Delivery (CI/CD) pipelines, developers can streamline the process of building, testing, and deploying serverless applications, reducing manual effort and minimizing the risk of errors. This approach ensures that infrastructure changes are tracked, versioned, and easily rolled back if necessary.
Automating Deployments with CI/CD Pipelines
CI/CD pipelines automate the process of building, testing, and deploying code changes. When integrated with IaC, these pipelines manage the infrastructure provisioning and configuration alongside application code deployments. This unified approach ensures that the infrastructure aligns with the application code at every stage of the release process.The core stages of a CI/CD pipeline for serverless deployments typically include:
- Code Commit and Trigger: Developers commit code changes to a version control system (e.g., Git). The CI/CD pipeline is triggered automatically, often through a webhook or a scheduled event.
- Build Stage: The pipeline builds the application code, which might involve compiling code, packaging dependencies, and creating deployment artifacts.
- Infrastructure Provisioning/Update: The IaC tool (e.g., Terraform, AWS CloudFormation, Serverless Framework) is used to provision or update the serverless infrastructure based on the code changes. This stage involves defining resources such as Lambda functions, API Gateways, databases, and other necessary components.
- Testing Stage: Automated tests, including unit tests, integration tests, and end-to-end tests, are executed to validate the application code and the deployed infrastructure. This ensures that the changes function as expected.
- Deployment Stage: If all tests pass, the application code and infrastructure changes are deployed to the target environment (e.g., development, staging, production). This may involve updating Lambda function code, API Gateway configurations, and other related resources.
- Monitoring and Rollback: The pipeline monitors the deployed application and infrastructure. If any issues are detected, the pipeline can automatically roll back to a previous stable version.
CI/CD Configurations for Different IaC Tools and Cloud Providers
The specific configuration of a CI/CD pipeline varies depending on the IaC tool and the cloud provider being used. Here are some examples:
Terraform and AWS:
Terraform is a popular IaC tool that can be used with various cloud providers, including AWS. A typical CI/CD pipeline for Terraform on AWS might involve the following steps using a service like AWS CodePipeline:
- Source Stage: Retrieve the Terraform configuration files from a code repository (e.g., AWS CodeCommit, GitHub).
- Build Stage: (Optional) Perform any necessary build steps, such as installing dependencies or running linters.
- Plan Stage: Use `terraform plan` to generate an execution plan, showing the changes that Terraform will make to the infrastructure. This plan can be reviewed and approved.
- Apply Stage: Use `terraform apply` to apply the changes to the infrastructure.
- Test Stage: Run integration tests using tools like `terratest` to validate the infrastructure.
Example AWS CodePipeline Configuration (Terraform):
This example illustrates a simplified AWS CodePipeline configuration using Terraform.
Source: Points to the Git repository containing Terraform configuration files.
Build: This stage can be used to run any build commands or perform linting and testing. This stage often includes using tools such as `terraform fmt` for formatting, and `terraform validate` to validate the configuration.
Deploy: Executes `terraform init`, `terraform plan`, and `terraform apply` to provision or update the infrastructure. The configuration may use AWS credentials and specify the target AWS region.
Serverless Framework and AWS:
The Serverless Framework simplifies the deployment and management of serverless applications on various cloud providers. The framework often uses a YAML configuration file (`serverless.yml`) to define the serverless infrastructure.
- Source Stage: Retrieve the `serverless.yml` configuration file and application code from a code repository.
- Build Stage: Build the application code.
- Deploy Stage: Use the Serverless Framework’s `serverless deploy` command to deploy the application and infrastructure.
- Test Stage: Run integration tests to validate the application and infrastructure.
Example Serverless Framework Deployment with AWS CodePipeline:
Source: Retrieves the `serverless.yml` file and application code from a Git repository.
Build: Builds the application. This might include running npm install to install dependencies.
Deploy: Executes `serverless deploy` to deploy the application and infrastructure. The configuration includes AWS credentials and the target AWS region.
Azure and Azure DevOps:
Azure DevOps provides CI/CD capabilities that can be used to automate the deployment of serverless applications on Azure. Azure uses IaC through Azure Resource Manager (ARM) templates.
- Source Stage: Retrieve the ARM templates and application code from a code repository (e.g., Azure Repos, GitHub).
- Build Stage: (Optional) Build the application code.
- Deploy Stage: Deploy the infrastructure using the ARM templates and deploy the application code.
- Test Stage: Run integration tests to validate the application and infrastructure.
Example Azure DevOps Pipeline Configuration (ARM templates):
Source: Retrieves the ARM templates and application code from a Git repository (Azure Repos).
Build: Builds the application, which might include packaging the application code into a deployable format.
Release: Deploys the ARM templates to create or update the Azure resources (e.g., Azure Functions, API Management). This step might include deploying the application code to Azure Functions.
Rolling Out Updates and Managing Infrastructure Changes
Rolling out updates and managing infrastructure changes with minimal downtime is a critical aspect of CI/CD for serverless applications. Several strategies can be employed to achieve this:
- Blue/Green Deployments: This strategy involves maintaining two identical environments (blue and green). When a new version of the application is ready, it is deployed to the inactive environment (e.g., the green environment). Once the new version is validated, traffic is switched from the active environment (blue) to the green environment. This approach minimizes downtime and allows for a quick rollback to the previous version if necessary.
- Canary Deployments: Canary deployments involve gradually rolling out a new version of the application to a small subset of users (the “canary” group). If the canary deployment performs well, the rollout is gradually expanded to include more users. This allows for early detection of issues and minimizes the impact of any problems.
- Immutable Infrastructure: IaC promotes the concept of immutable infrastructure, where infrastructure changes are applied by creating new resources instead of modifying existing ones. This simplifies rollbacks, as the previous version of the infrastructure remains available.
- Automated Rollbacks: CI/CD pipelines should include automated rollback mechanisms. If any issues are detected during testing or monitoring, the pipeline should automatically roll back to the previous stable version of the application and infrastructure.
- Infrastructure Drift Detection: Implement checks to detect and remediate “infrastructure drift” – instances where the deployed infrastructure deviates from the IaC definitions. Tools like Terraform’s `terraform plan` or cloud provider-specific services can be used to identify and correct these deviations.
- Testing and Monitoring: Thorough testing (unit, integration, and end-to-end) and robust monitoring are essential. Testing validates the application’s behavior, and monitoring detects any issues in production. Alerting and logging should be implemented to quickly identify and address problems.
By implementing these strategies, organizations can achieve continuous delivery of serverless applications with minimal downtime, ensuring high availability and a positive user experience. For instance, Netflix utilizes canary deployments extensively to roll out changes to its streaming service, minimizing disruption to its millions of users. Similarly, companies like Amazon employ blue/green deployments to update their core services with minimal impact.
Monitoring and Managing Serverless Infrastructure with IaC
Integrating Infrastructure as Code (IaC) with monitoring and logging tools is crucial for maintaining the health, performance, and security of serverless applications. This integration allows for proactive issue detection, automated responses, and continuous improvement of the infrastructure. Effectively monitoring and managing serverless infrastructure ensures high availability and efficient resource utilization, directly impacting the overall success of the application.
Integrating IaC with Monitoring and Logging Tools
The seamless integration of IaC with monitoring and logging tools is essential for comprehensive serverless application management. This integration enables the collection, analysis, and visualization of critical data, facilitating informed decision-making and rapid response to potential issues. IaC facilitates this integration through automated configuration and deployment of monitoring agents and logging pipelines.
- Automated Configuration of Monitoring Agents: IaC tools, such as Terraform or AWS CloudFormation, can be used to automatically provision and configure monitoring agents on the serverless infrastructure. For example, in AWS, this involves defining resources for CloudWatch Logs and Metrics, which collect logs and metrics from Lambda functions, API Gateway, and other serverless services. These configurations are defined in code and deployed alongside the serverless application, ensuring consistent monitoring across all environments.
- Deployment of Logging Pipelines: IaC enables the automated deployment of logging pipelines that collect, process, and store logs generated by serverless applications. Tools like Fluentd or the AWS CloudWatch Logs agent can be configured via IaC to forward logs to centralized storage solutions like Amazon S3 or Elasticsearch. This allows for centralized log management, making it easier to search, analyze, and troubleshoot issues.
- Centralized Log Aggregation: IaC allows for defining centralized log aggregation. This involves configuring the infrastructure to forward logs from different serverless components to a single location. This facilitates the analysis of logs from multiple sources in a unified view, providing a comprehensive understanding of application behavior and performance. For instance, all Lambda function logs, API Gateway access logs, and database logs can be aggregated in a centralized log management system.
- Metric Collection and Visualization: IaC can be used to define custom metrics and set up dashboards to visualize the performance of serverless applications. For example, IaC can configure AWS CloudWatch dashboards to display metrics such as Lambda function invocations, execution times, and error rates. This provides real-time insights into the application’s health and allows for proactive identification of performance bottlenecks or potential issues.
- Integration with Alerting Systems: IaC facilitates integration with alerting systems. By defining thresholds for metrics, IaC can automatically trigger alerts when specific conditions are met. For example, an IaC template can be used to set up CloudWatch alarms that send notifications to a Slack channel or email address when the error rate of a Lambda function exceeds a predefined threshold.
Setting Up Alerts and Notifications Based on Infrastructure Metrics
Setting up alerts and notifications based on infrastructure metrics is a proactive approach to serverless application management. These alerts enable timely detection and response to issues, preventing potential outages and ensuring optimal performance. IaC streamlines the configuration and deployment of these alert systems.
- Defining Critical Metrics: Identify the key performance indicators (KPIs) that are critical to the application’s performance and health. These include metrics such as Lambda function invocation count, execution time, error rate, and API Gateway latency. IaC can be used to define these metrics and configure the infrastructure to collect and track them.
- Setting Thresholds and Conditions: Define thresholds and conditions for each metric that trigger alerts. For example, an alert can be configured to trigger when the average execution time of a Lambda function exceeds a certain value or when the error rate exceeds a specific percentage. IaC allows these thresholds and conditions to be defined in code, ensuring consistency across all environments.
- Configuring Alerting Channels: Configure the channels through which alerts will be delivered, such as email, Slack, or PagerDuty. IaC can be used to provision and configure these channels, ensuring that the appropriate individuals or teams are notified when alerts are triggered.
- Automated Alerting with IaC: IaC tools can automate the creation and management of alerts. For example, with AWS CloudFormation, you can define CloudWatch alarms that monitor Lambda function metrics. The configuration of the alarm, including the metric, threshold, and notification channels, is defined in a CloudFormation template and deployed alongside the serverless application.
- Examples of Alerting Scenarios:
- Lambda Function Errors: Set an alert to trigger when the error rate of a Lambda function exceeds 1%.
- API Gateway Latency: Configure an alert when the average API Gateway latency exceeds 500ms.
- Database Connection Errors: Set an alert to trigger when database connection errors occur.
Responding to Infrastructure Issues and Ensuring High Availability
A well-defined plan for responding to infrastructure issues is critical for ensuring high availability and minimizing downtime in serverless environments. IaC plays a vital role in facilitating automated responses and recovery strategies.
- Incident Response Plan: Develop a comprehensive incident response plan that Artikels the steps to be taken when an infrastructure issue is detected. This plan should include roles and responsibilities, communication protocols, and escalation procedures. The plan should be documented and easily accessible to all relevant team members.
- Automated Remediation Strategies: Implement automated remediation strategies using IaC to address common infrastructure issues. For example, if a Lambda function fails due to a resource limit, IaC can automatically scale the function’s memory or timeout settings.
- Health Checks and Monitoring: Implement health checks and continuous monitoring to detect issues proactively. Health checks can verify the availability and performance of serverless components, such as Lambda functions and API Gateways. Monitoring systems can track key metrics and trigger alerts when issues are detected.
- Implementing Circuit Breakers: Use circuit breakers to prevent cascading failures. If a service becomes unavailable or experiences high error rates, a circuit breaker can temporarily stop traffic to that service, preventing further issues and allowing the service to recover.
- Rollback and Recovery Procedures: Establish rollback and recovery procedures using IaC. If a deployment causes an issue, IaC can be used to automatically roll back to a previous, known-good version of the infrastructure. This ensures that the application can quickly recover from deployment failures.
- Disaster Recovery Plan: Develop a disaster recovery plan to address catastrophic events. This plan should include strategies for replicating the infrastructure in a different region or availability zone. IaC can be used to automate the deployment of the disaster recovery infrastructure and ensure that the application can quickly recover from a major outage.
- Example: Autoscaling Lambda Functions:
- Trigger: CPU utilization of a Lambda function exceeds 80%.
- Action: IaC automatically increases the concurrency limit of the Lambda function to handle the increased load.
Cost Optimization with IaC for Serverless
Infrastructure as Code (IaC) provides a powerful framework for optimizing serverless costs by enabling precise control over resource provisioning, automated scaling, and efficient monitoring. By leveraging IaC, organizations can proactively manage spending, reduce waste, and ensure that serverless applications operate within defined budgetary constraints. This approach shifts the focus from reactive cost management to a proactive, automated strategy that aligns infrastructure with actual application needs.
Resource Sizing and Configuration
IaC allows for precise control over the resources allocated to serverless functions and related services. This precision is crucial for minimizing costs by ensuring that resources are appropriately sized for the workload.
- Function Memory Allocation: Configuring the appropriate memory allocation for serverless functions is a critical cost factor. Allocating too much memory leads to overspending, while allocating too little can result in performance bottlenecks and increased execution time, indirectly impacting cost. IaC tools allow for the definition of memory settings directly within the configuration files. For instance, in AWS Lambda, the `memorySize` parameter can be adjusted based on the function’s requirements.
- Concurrency Limits: IaC facilitates the setting of concurrency limits, which control the maximum number of concurrent function invocations. Setting appropriate limits prevents uncontrolled scaling and potential cost overruns. For example, in AWS Lambda, this can be configured using the `ReservedConcurrentExecutions` parameter to set a hard limit or by configuring the `ProvisionedConcurrency` for predictable traffic.
- Database Capacity: Serverless applications often interact with databases. IaC enables the configuration of database capacity, such as provisioned throughput in Amazon DynamoDB or the instance size in relational databases. Automating these settings through IaC ensures that the database scales appropriately with the application’s needs, minimizing both over-provisioning and performance issues.
Auto-Scaling and Event-Driven Architecture
Auto-scaling is a core benefit of serverless, and IaC is essential for effectively implementing and managing auto-scaling policies. By defining scaling rules within the IaC configuration, resources are automatically adjusted based on demand, ensuring optimal resource utilization and cost efficiency.
- Scaling Policies: IaC tools enable the definition of scaling policies based on various metrics, such as CPU utilization, request queue length, or custom metrics. For example, AWS Application Auto Scaling allows for the configuration of scaling policies that automatically adjust the number of Lambda function instances based on CloudWatch metrics.
- Event-Driven Architectures: IaC facilitates the deployment and management of event-driven architectures, which are inherently cost-effective. By triggering functions only in response to events (e.g., file uploads, database updates), resources are utilized only when needed, minimizing idle time and associated costs. IaC tools such as AWS SAM (Serverless Application Model) streamline the configuration of event sources and function triggers.
- Idle Resource Management: IaC can incorporate strategies to reduce the cost of idle resources. This can be achieved by automatically scaling down resources during periods of low activity. For instance, a database can be scaled down to a smaller instance size during off-peak hours using scheduled IaC updates.
Cost Monitoring and Alerting
IaC, combined with cloud provider monitoring tools, enables comprehensive cost monitoring and alerting. This proactive approach helps identify potential cost anomalies and ensures that spending remains within budget.
- Cost Tracking with CloudWatch and IaC: IaC configurations can integrate with cloud provider monitoring services like AWS CloudWatch. This allows for the creation of custom metrics and dashboards to track serverless costs. For example, IaC can define CloudWatch alarms that trigger notifications when costs exceed a predefined threshold.
- Budgeting and Alerts: IaC can be used to configure budgeting alerts within cloud provider services. These alerts notify teams when spending approaches or exceeds the defined budget. For example, AWS Budgets can be configured using IaC to set cost thresholds and receive notifications via email or other channels.
- Cost Analysis and Reporting: IaC enables the automation of cost analysis and reporting. IaC can deploy services to automatically analyze cost data and generate reports. For example, IaC can be used to configure AWS Cost Explorer to visualize spending trends and identify areas for optimization.
Examples of IaC Configurations for Cost Optimization
The following examples illustrate how IaC configurations can be used to implement cost-saving strategies.
- AWS Lambda Function with Memory Optimization:
Consider a Lambda function that processes image uploads. The initial IaC configuration might define the function’s memory size as 1024MB. However, monitoring reveals that the function rarely uses more than 512MB. Using IaC, the `memorySize` parameter can be adjusted to 512MB, reducing the cost per invocation.
“`yaml
Resources:
MyImageProcessorFunction:
Type: AWS::Serverless::Function
Properties:
FunctionName: MyImageProcessor
Handler: index.handler
Runtime: nodejs18.x
MemorySize: 512
Timeout: 30
“`This YAML configuration, written using AWS SAM, defines a Lambda function named `MyImageProcessorFunction`.
The `MemorySize` parameter is set to 512MB, which is a cost-optimized setting.
- DynamoDB Auto-Scaling Configuration:
For a DynamoDB table used by a serverless application, IaC can define auto-scaling policies to adjust provisioned capacity based on traffic. For example, the configuration below uses AWS CloudFormation to set up auto-scaling for the table’s read capacity.
“`yaml
Resources:
MyTable:
Type: AWS::DynamoDB::Table
Properties:
TableName: MyTable
AttributeDefinitions:-AttributeName: id
AttributeType: S
KeySchema:-AttributeName: id
KeyType: HASH
ProvisionedThroughput:
ReadCapacityUnits: 5
WriteCapacityUnits: 5
MyTableReadScaling:
Type: AWS::ApplicationAutoScaling::ScalableTarget
Properties:
MaxCapacity: 100
MinCapacity: 5
ResourceId: !Join [‘/’, [!Ref MyTable, table]]
RoleARN: !GetAtt AutoScalingRole.Arn
ScalableDimension: dynamodb:table:ReadCapacityUnits
ServiceNamespace: dynamodb
MyTableReadScalingPolicy:
Type: AWS::ApplicationAutoScaling::ScalingPolicy
Properties:
PolicyName: MyTableReadScalingPolicy
PolicyType: TargetTrackingScaling
ScalingTargetId: !Ref MyTableReadScaling
TargetTrackingConfiguration:
PredefinedMetricSpecification:
PredefinedMetricType: DynamoDBReadCapacityUtilization
ScaleInCooldown: 60
ScaleOutCooldown: 60
TargetValue: 70.0
“`This CloudFormation configuration defines a DynamoDB table (`MyTable`) and sets up auto-scaling for read capacity using the `AWS::ApplicationAutoScaling::ScalableTarget` and `AWS::ApplicationAutoScaling::ScalingPolicy` resources.
The policy uses `DynamoDBReadCapacityUtilization` as the metric and adjusts capacity to maintain 70% utilization.
Techniques for Monitoring and Controlling Serverless Spending
Effective monitoring and control are essential for maintaining cost-efficiency in serverless environments. Several techniques can be employed.
- Regular Cost Reviews: Implement a regular schedule for reviewing serverless costs. This involves analyzing cost reports, identifying cost drivers, and making adjustments to IaC configurations. These reviews should occur at least monthly, but ideally weekly or even daily for high-traffic applications.
- Cost Allocation Tags: Utilize cost allocation tags within IaC configurations. These tags allow for the grouping of resources by project, environment, or team. This granular view enables accurate cost tracking and chargeback within the organization. For example, in AWS, tags can be applied to Lambda functions, API Gateways, and other resources.
- Proactive Alerting: Configure proactive alerts based on cost metrics. Set up alerts for unexpected cost spikes or deviations from established budgets. Integrate these alerts with communication channels (e.g., Slack, email) to ensure timely responses.
- Resource Lifecycle Management: Implement automated resource lifecycle management. Use IaC to define the creation, modification, and deletion of resources. This prevents orphaned resources from accumulating costs. This approach ensures that resources are cleaned up when no longer needed.
Serverless IaC Security Considerations
Infrastructure as Code (IaC) for serverless environments, while offering significant benefits in terms of automation, scalability, and cost efficiency, introduces new security challenges. Misconfigurations in IaC templates can lead to vulnerabilities that expose serverless applications to various threats. A proactive approach to security, integrated throughout the IaC lifecycle, is crucial for protecting serverless deployments.
Identifying Security Vulnerabilities Associated with IaC Deployments for Serverless Environments
IaC deployments in serverless architectures are susceptible to a range of security vulnerabilities, often stemming from configuration errors. Understanding these vulnerabilities is the first step towards implementing effective security measures.
- Insecure IAM Role Configurations: Improperly configured Identity and Access Management (IAM) roles are a primary source of vulnerabilities. Overly permissive roles, granting excessive privileges, can allow attackers to escalate their access or compromise resources. Conversely, insufficient permissions can disrupt application functionality. For example, a function granted write access to a sensitive data store without proper restrictions can be exploited to exfiltrate data.
- Unencrypted Data at Rest and in Transit: Serverless applications often handle sensitive data. Failure to encrypt data both at rest (e.g., in databases or object storage) and in transit (e.g., during API calls) can lead to data breaches. IaC templates must enforce encryption settings to protect data confidentiality. An example is an S3 bucket storing user uploads without server-side encryption enabled.
- Vulnerable Dependencies: Serverless functions rely on dependencies (libraries, packages). IaC templates may not always include mechanisms for managing and updating these dependencies, leading to the inclusion of known vulnerabilities. Regularly scanning and patching dependencies is crucial.
- Insufficient Input Validation: Serverless functions that accept user input without proper validation are vulnerable to injection attacks (e.g., SQL injection, cross-site scripting). IaC templates should incorporate input validation and sanitization practices.
- Lack of Network Security Controls: Serverless functions can be deployed within a Virtual Private Cloud (VPC) or accessed via public endpoints. Inadequate network security controls, such as missing firewalls or poorly configured security groups, can expose functions to unauthorized access.
- Misconfigured API Gateways: API Gateways act as the entry point to serverless functions. Misconfigurations, such as open access control lists (ACLs) or lack of authentication, can allow unauthorized users to invoke functions.
- Secrets Management Issues: Hardcoding secrets (API keys, passwords) directly into IaC templates is a critical security risk. Attackers can easily access these secrets if the templates are compromised. Secure secrets management practices, such as using dedicated secret stores, are essential.
Methods for Implementing Security Best Practices within IaC Templates, Including IAM Roles and Encryption
Implementing security best practices within IaC templates is essential for building secure serverless infrastructure. This involves incorporating various security controls and configurations during the infrastructure provisioning process.
- Least Privilege IAM Roles: Grant IAM roles only the minimum necessary permissions. This principle of least privilege limits the impact of potential security breaches. IaC templates should define IAM roles with granular permissions, specifying exactly what resources a function can access and what actions it can perform.
- IAM Role Boundaries: Consider implementing IAM role boundaries to restrict the maximum permissions that can be granted to a role. This adds an extra layer of security by preventing overly permissive role assignments.
- Data Encryption at Rest: Configure encryption for data storage services (e.g., S3, DynamoDB) within the IaC templates. Server-side encryption (SSE) should be enabled to protect data at rest. For example, when provisioning an S3 bucket using IaC, the template should specify the encryption configuration using a service-managed key (SSE-S3) or a customer-managed key (SSE-KMS).
- Data Encryption in Transit: Enforce HTTPS for all API calls and data transfers. This protects data in transit from eavesdropping. API Gateway configurations in IaC templates should require HTTPS connections.
- Automated Dependency Management: Integrate automated dependency scanning and updating into the IaC pipeline. Tools like Snyk or OWASP Dependency-Check can be used to identify and remediate vulnerabilities in dependencies. This can be achieved by incorporating security scanning steps into the CI/CD pipeline triggered by IaC changes.
- Input Validation and Sanitization: Implement input validation and sanitization in serverless function code. IaC templates can be used to enforce the use of specific input validation libraries or frameworks.
- Network Security Controls: Define and configure network security controls, such as firewalls and security groups, within the IaC templates. For example, when deploying serverless functions within a VPC, the IaC template should configure security groups with strict rules to control inbound and outbound traffic.
- API Gateway Security: Configure API Gateway security features, such as authentication, authorization, and rate limiting, within the IaC templates. This protects serverless functions from unauthorized access and abuse.
- Secure Secrets Management: Use dedicated secrets management services (e.g., AWS Secrets Manager, HashiCorp Vault) to store and manage secrets. IaC templates should retrieve secrets from these services rather than hardcoding them.
- Regular Security Audits: Integrate security audits into the IaC deployment pipeline. This can involve automated security scans and manual reviews of IaC templates to identify potential vulnerabilities.
Designing an IaC-Based Security Audit Process for Serverless Infrastructure
An IaC-based security audit process helps ensure that serverless infrastructure is deployed and maintained securely. This process involves a combination of automated and manual checks, integrated throughout the IaC lifecycle.
- Automated Security Scanning: Integrate automated security scanning tools into the IaC pipeline. These tools can scan IaC templates for security vulnerabilities and misconfigurations. Tools like tfsec, Checkov, and cfn-lint can be used for this purpose. The scan should be triggered automatically whenever the IaC templates are modified.
- Static Code Analysis: Perform static code analysis on serverless function code to identify potential security vulnerabilities, such as insecure coding practices or vulnerabilities in dependencies. Tools like SonarQube can be used for this purpose.
- Policy Enforcement: Implement policy-as-code to enforce security best practices. This involves defining security policies that are automatically checked against IaC templates. For example, a policy could enforce the use of encryption for all S3 buckets or require the use of least privilege IAM roles. Tools like Open Policy Agent (OPA) can be used to define and enforce these policies.
- Manual Code Reviews: Conduct manual code reviews of IaC templates and serverless function code to identify potential security vulnerabilities that may not be detected by automated tools. Code reviews should be performed by security experts or experienced developers.
- Vulnerability Scanning: Perform vulnerability scanning of deployed serverless infrastructure to identify any vulnerabilities that may have been introduced during deployment or runtime. This can involve using tools that scan for known vulnerabilities in dependencies or misconfigurations.
- Penetration Testing: Conduct penetration testing to simulate real-world attacks and identify any vulnerabilities that can be exploited by attackers. Penetration testing should be performed by qualified security professionals.
- Incident Response Plan: Develop and maintain an incident response plan to address security incidents. The incident response plan should Artikel the steps to be taken in the event of a security breach, including containment, eradication, and recovery.
- Regular Audits and Compliance Checks: Conduct regular security audits and compliance checks to ensure that serverless infrastructure meets security requirements and complies with relevant regulations. These audits should be performed periodically and should include a review of IaC templates, deployed infrastructure, and security logs.
- Continuous Monitoring and Logging: Implement continuous monitoring and logging to detect and respond to security threats. This involves collecting security logs from serverless functions, API Gateways, and other infrastructure components. These logs should be analyzed to identify suspicious activity and potential security breaches.
Case Studies: Real-World Serverless IaC Implementations
Understanding how Infrastructure as Code (IaC) translates into tangible benefits requires examining real-world applications. This section presents a case study illustrating a successful serverless IaC implementation, highlighting challenges faced, lessons learned, and the impact on key operational metrics.
Serverless IaC Implementation at a FinTech Startup
This case study focuses on a FinTech startup that adopted a serverless architecture for its core payment processing platform. The platform needed to handle a high volume of transactions with low latency, requiring a robust and scalable infrastructure. The startup chose to implement IaC using AWS CloudFormation, defining its entire infrastructure, including AWS Lambda functions, API Gateway, DynamoDB tables, and other related resources, as code.The implementation process encountered several challenges.
- Version Control and Collaboration: The initial lack of a structured version control system led to conflicts and difficulties in collaborating on infrastructure changes. This was addressed by integrating Git for version control and establishing clear branching strategies.
- Testing and Validation: Testing infrastructure changes proved challenging. They initially lacked automated testing frameworks for validating the infrastructure code. This was mitigated by incorporating tools like cfn-lint for static analysis and custom scripts for end-to-end testing of infrastructure deployments.
- Resource Dependency Management: Managing dependencies between different infrastructure components, particularly between Lambda functions and database tables, presented challenges. This was solved by leveraging CloudFormation’s `DependsOn` attribute and implementing a more robust dependency resolution strategy within the IaC code.
- Debugging and Troubleshooting: Debugging infrastructure deployments and identifying issues within the IaC code proved time-consuming. They integrated logging and monitoring solutions, such as AWS CloudWatch, into their IaC definitions, which significantly improved the ability to troubleshoot and identify root causes.
The implementation of IaC had a significant impact on the startup’s development velocity, cost savings, and operational efficiency.
- Development Velocity: The use of IaC streamlined the infrastructure provisioning process. The startup could now deploy new features and updates to their payment processing platform much faster, leading to a 30% reduction in deployment time. This increase in speed enabled them to iterate more quickly on product features and respond rapidly to market demands.
- Cost Savings: IaC facilitated the automation of infrastructure scaling and optimization. The startup implemented auto-scaling policies for their serverless components, dynamically adjusting resources based on demand. This resulted in a 20% reduction in infrastructure costs compared to their previous manual infrastructure management approach. They achieved cost savings by only paying for the resources they actually used.
- Operational Efficiency: IaC improved the reliability and consistency of the infrastructure. The startup automated the infrastructure deployment and configuration, reducing the risk of human error. This resulted in a 15% reduction in operational incidents and a significant improvement in the team’s ability to focus on core business logic rather than infrastructure management.
- Infrastructure as Code Benefits Summary: The startup’s adoption of IaC resulted in the ability to treat infrastructure as code. It facilitated version control, testing, and automated deployment. This enabled faster and more reliable deployments, leading to significant cost savings and improved operational efficiency.
Advanced IaC Techniques for Serverless
Advanced Infrastructure as Code (IaC) techniques significantly enhance the management, scalability, and resilience of serverless applications. Beyond basic provisioning, these techniques introduce sophisticated methods for maintaining infrastructure integrity, automating complex deployment strategies, and ensuring rapid recovery in the event of failures. This section explores these advanced concepts, focusing on drift detection, automated deployments, and disaster recovery planning.
Infrastructure Drift Detection and Remediation
Infrastructure drift refers to the divergence between the desired state of an infrastructure, as defined in the IaC code, and the actual state of the deployed resources. This drift can occur due to manual changes, configuration errors, or unexpected interactions within the system. Detecting and remediating drift is crucial for maintaining infrastructure consistency, security, and predictability.
Drift detection involves comparing the current state of the infrastructure with the state defined in the IaC code. Several tools and techniques can be employed for this purpose:
- Continuous Monitoring: Implement monitoring systems that regularly assess the infrastructure’s state. These systems can automatically flag discrepancies between the desired and actual configurations.
- Automated Scans: Utilize tools that scan the infrastructure and compare it against the IaC code. These tools identify resources that have been modified outside of the defined code.
- Version Control Integration: Integrate IaC code with version control systems (e.g., Git). This allows for tracking changes over time and comparing different versions of the infrastructure configuration.
Remediation involves automatically correcting any detected drift. The specific approach depends on the nature of the drift and the IaC tool being used. Common remediation strategies include:
- Automated Rollback: Automatically revert changes that deviate from the IaC code. This ensures that the infrastructure returns to its desired state.
- Configuration Synchronization: Update the infrastructure to match the IaC code. This may involve applying configuration changes, deleting unexpected resources, or provisioning missing resources.
- Alerting and Reporting: Notify relevant teams when drift is detected. This allows for manual intervention or investigation if automated remediation is not feasible or appropriate.
Example: Consider a scenario where a security group rule is manually modified in AWS. Using an IaC tool like Terraform with drift detection enabled, the tool can identify this change. If configured for automated remediation, the tool can revert the security group to the state defined in the Terraform configuration, ensuring that only authorized changes are applied.
Automating Complex Serverless Tasks: Blue/Green Deployments
Blue/green deployments provide a strategy for deploying new versions of serverless applications with minimal downtime and risk. This technique involves maintaining two identical environments: the “blue” environment (the current production environment) and the “green” environment (the new version being deployed). Traffic is gradually shifted from the blue environment to the green environment, allowing for testing and validation of the new version before fully transitioning.
Implementing blue/green deployments with IaC requires careful planning and automation. The IaC code should define the infrastructure for both environments, including:
- Compute Resources: Define the serverless functions or containers for both the blue and green environments.
- Networking: Configure routing and traffic management mechanisms (e.g., API Gateway, load balancers) to direct traffic between the two environments.
- Data Stores: Manage the data stores (e.g., databases, object storage) used by the serverless application, ensuring data consistency and compatibility between the blue and green environments.
The automation process typically involves the following steps:
- Provision the Green Environment: The IaC code is used to provision the green environment, including all necessary resources.
- Deploy the New Application Version: The new version of the serverless application is deployed to the green environment.
- Testing and Validation: Automated tests and manual verification are performed to ensure the new version functions correctly in the green environment.
- Traffic Shifting: Traffic is gradually shifted from the blue environment to the green environment. This can be done using weighted routing or other traffic management techniques.
- Monitoring and Rollback: Monitor the green environment for any issues. If problems are detected, traffic can be quickly rolled back to the blue environment.
- Decommissioning: Once the green environment is fully validated and stable, the blue environment can be decommissioned.
Example: Using AWS CloudFormation, a blue/green deployment strategy can be implemented for an API Gateway and its associated Lambda functions. The IaC code defines two API Gateway stages (e.g., “blue” and “green”) and Lambda function versions. The deployment process involves creating a new Lambda function version, updating the API Gateway’s “green” stage to point to the new version, and then gradually shifting traffic from the “blue” stage to the “green” stage using weighted routing.
IaC in Disaster Recovery Planning for Serverless Applications
Disaster recovery (DR) planning is critical for serverless applications to ensure business continuity in the event of infrastructure failures or other disruptions. IaC plays a central role in DR planning by enabling the automated provisioning and configuration of resources in a secondary region or environment.
The key components of IaC-based DR planning for serverless applications include:
- Replication Strategy: Define a strategy for replicating data and configurations to a secondary region or environment. This may involve using database replication, object storage replication, or other data synchronization mechanisms.
- Automated Failover: Automate the failover process to the secondary region. This includes updating DNS records, reconfiguring routing rules, and ensuring that the application can function in the secondary environment.
- Testing and Validation: Regularly test the DR plan to ensure it functions correctly. This involves simulating failures and verifying that the application can recover successfully.
The IaC code should define the infrastructure for both the primary and secondary regions, including:
- Compute Resources: Define the serverless functions or containers in both regions.
- Networking: Configure networking components (e.g., VPCs, subnets, security groups) in both regions.
- Data Stores: Configure database replication or other data synchronization mechanisms to ensure data consistency between the regions.
- Monitoring and Alerting: Implement monitoring and alerting to detect failures and trigger the failover process.
Example: Using Terraform and AWS services, a DR plan can be implemented for a serverless application that uses Lambda functions, API Gateway, and DynamoDB. The Terraform code can define the infrastructure in both the primary and secondary regions. The DR plan would involve replicating the DynamoDB table to the secondary region and using Route 53 to automatically switch traffic to the secondary region if the primary region becomes unavailable.
A health check monitors the primary region and triggers the failover if the application is unresponsive. This ensures that the application remains available even during a regional outage.
Final Wrap-Up
In conclusion, the effective management of infrastructure as code for serverless environments is paramount for realizing the full potential of serverless computing. By adopting IaC principles and leveraging the appropriate tools and best practices, organizations can achieve greater scalability, cost efficiency, and operational agility. The ability to automate deployments, enforce consistent configurations, and maintain a clear audit trail is crucial for ensuring the long-term success and maintainability of serverless applications.
This comprehensive approach enables development teams to focus on innovation, delivering value to their users, and ultimately, driving business success in an increasingly dynamic and competitive landscape.
User Queries
What are the primary benefits of using IaC for serverless?
IaC offers scalability, cost optimization, automation, version control, improved collaboration, and faster deployment cycles.
Which IaC tools are most popular for serverless deployments?
Popular tools include AWS CloudFormation, Terraform, and the Serverless Framework.
How does IaC improve security in serverless environments?
IaC allows for consistent security configurations, automated compliance checks, and version-controlled security policies, reducing human error.
What is the role of CI/CD in serverless IaC?
CI/CD pipelines automate the build, testing, and deployment of IaC templates, ensuring rapid and reliable infrastructure updates.
How can IaC help optimize serverless costs?
IaC facilitates resource sizing, auto-scaling configurations, and cost monitoring, enabling efficient resource utilization and cost control.