Navigating the complexities of granting access to third-party contractors is a critical aspect of modern cybersecurity. This comprehensive guide delves into the essential strategies for ensuring secure access, safeguarding sensitive data, and maintaining the integrity of your organization’s systems. It explores the multifaceted challenges of managing external access while emphasizing the importance of robust policies, advanced technologies, and continuous monitoring to mitigate potential risks.
This document will meticulously Artikel the key components of a secure third-party contractor access management strategy, from defining access needs and conducting thorough risk assessments to implementing advanced access control methods and establishing rigorous onboarding and offboarding procedures. We will also cover best practices in Identity and Access Management (IAM), data security, network segmentation, and the crucial role of training and awareness programs.
Finally, it will delve into the legal and contractual aspects, including the essential elements of service level agreements (SLAs) and incident response planning, ensuring a holistic approach to third-party contractor access management.
Defining Third-Party Contractor Access Needs
Understanding and meticulously defining the access requirements of third-party contractors is paramount for maintaining a robust security posture. This process involves a thorough assessment of their job functions, the data and resources they need to access, and the potential risks associated with their access. A well-defined access management strategy minimizes the attack surface, prevents unauthorized data breaches, and ensures compliance with relevant regulations.
Types of Access Required by Third-Party Contractors
Contractor access needs vary significantly depending on their role and the nature of the project. A comprehensive access management plan must account for different access types.
- Network Access: This encompasses access to the organization’s internal network, including the internet, intranet, and any internal servers or applications. This may involve VPN access, Wi-Fi access, or dedicated network connections. For instance, a network engineer might require full network access to diagnose and resolve network issues, while a marketing consultant might only need access to specific marketing-related servers.
- Data Access: Data access refers to the ability to view, modify, or delete data stored on the organization’s systems. This could include access to customer data, financial records, intellectual property, or other sensitive information. Data access controls should be granular, granting access only to the specific data required for the contractor’s tasks. For example, a data analyst would need access to data warehouses to analyze data, while a legal consultant would need access to legal documents.
- Application Access: This grants contractors access to specific software applications necessary for their work. This could include access to CRM systems, project management tools, email clients, or other business-critical applications. Access should be restricted to the specific modules and functionalities needed. For example, a software developer might require access to code repositories and development environments.
- Physical Access: Physical access controls the contractor’s ability to enter and move around the organization’s physical premises. This includes access to buildings, offices, data centers, and other secure areas. Physical access may be granted through access badges, key cards, or other security measures. For example, a security guard contractor would need access to all areas of the building, while a cleaning contractor might only need access to specific areas during specific hours.
- System Administration Access: This provides contractors with elevated privileges to manage and maintain the organization’s IT infrastructure. This access should be granted sparingly and with strict monitoring, as it carries significant security risks. Examples include access to servers, databases, and security systems.
Categorizing Contractors Based on Access Levels and Job Functions
Categorizing contractors based on their required access levels and job functions streamlines the access management process. This approach allows organizations to apply consistent security policies and controls, while minimizing the risk of unauthorized access.
A common method is to create access tiers. For example:
- Tier 1: Limited Access: Contractors in this tier have the least amount of access, typically involving access to public-facing websites or limited network access for basic tasks. An example would be a cleaning contractor.
- Tier 2: Standard Access: Contractors in this tier require access to specific applications and data relevant to their job function, but with restrictions on sensitive information. An example would be a marketing consultant with access to the marketing CRM and shared drives.
- Tier 3: Elevated Access: This tier grants contractors access to more sensitive data and systems, with stricter monitoring and control. An example would be a network engineer with access to network configuration tools.
- Tier 4: Administrator Access: Contractors in this tier possess the highest level of access, with the ability to manage and administer critical systems. Access is typically limited to essential personnel. An example would be a third-party IT administrator with access to the company’s server infrastructure.
Categorizing contractors based on job function also facilitates access management. For instance, developers would need access to code repositories and development environments, while accountants would need access to financial systems. Job function-based access allows for a more tailored and efficient approach to granting permissions.
Designing a System for Identifying and Documenting Contractor Access Needs
A well-defined system for identifying and documenting contractor access needs is crucial for maintaining a secure environment. This system should be integrated into the onboarding process and regularly reviewed.
Here’s a structured approach:
- Needs Assessment Form: Create a standardized form that Artikels the specific access requirements for each contractor. This form should be completed by the project manager or the individual responsible for managing the contractor.
- Job Function and Role Definition: Clearly define the job function and role of the contractor, outlining their responsibilities and tasks. This information will inform the required access levels.
- Data and System Inventory: Maintain an inventory of all data and systems, including their sensitivity levels. This inventory helps to determine the appropriate access permissions.
- Access Request and Approval Workflow: Establish a formal process for requesting, reviewing, and approving access requests. This workflow should involve the project manager, IT security personnel, and other relevant stakeholders.
- Least Privilege Principle: Implement the principle of least privilege, granting contractors only the minimum access necessary to perform their job functions.
- Regular Access Reviews: Conduct regular reviews of contractor access to ensure that permissions remain appropriate and that contractors no longer have access to resources they no longer need.
- Documentation and Audit Trails: Maintain comprehensive documentation of all access requests, approvals, and modifications. Implement robust audit trails to track all contractor access and activities.
Risk Assessment and Security Policy Development
Developing a robust risk assessment and a comprehensive security policy are critical steps in securely managing third-party contractor access. These measures proactively identify vulnerabilities, establish clear guidelines, and ensure that contractor activities align with your organization’s security posture. The following sections detail the process and provide a framework for creating effective policies.
Risk Assessment for Third-Party Contractor Access
Conducting a thorough risk assessment is the cornerstone of a secure contractor access management strategy. This process involves identifying potential threats, evaluating vulnerabilities, and determining the likelihood and impact of security incidents. The objective is to understand the risks associated with contractor access and implement appropriate controls to mitigate them.The risk assessment process should encompass the following key steps:
- Identify Assets: Begin by cataloging all assets that contractors may access. This includes physical assets (e.g., servers, offices), digital assets (e.g., data, applications, networks), and intellectual property. Understanding the value and sensitivity of each asset is crucial for prioritizing protection efforts. For instance, a company’s proprietary source code, which is essential for its competitive advantage, requires a higher level of security compared to publicly available marketing materials.
- Identify Threats: Determine the potential threats that could exploit vulnerabilities. Threats can originate from various sources, including malicious actors (e.g., hackers, disgruntled employees), accidental actions (e.g., human error, misconfiguration), and natural disasters. Consider both internal and external threats. For example, a contractor with malicious intent could attempt to steal sensitive data, while a poorly trained contractor could inadvertently expose vulnerabilities.
- Identify Vulnerabilities: Identify weaknesses in your security controls that could be exploited by threats. Vulnerabilities can exist in various areas, such as physical security, network infrastructure, software, and access control mechanisms. Examples include outdated software with known security flaws, weak password policies, or inadequate physical security measures.
- Analyze Risks: Assess the likelihood and impact of each threat exploiting a vulnerability. This involves evaluating the probability of the threat occurring and the potential consequences if it does. Consider factors such as the sensitivity of the assets, the sophistication of the threat, and the effectiveness of existing security controls. Use a risk matrix to visualize and prioritize risks. The risk matrix typically categorizes risks based on their likelihood (e.g., low, medium, high) and impact (e.g., low, medium, high), allowing for a clear ranking of risks.
- Develop Mitigation Strategies: Develop strategies to reduce the identified risks. Mitigation strategies can include implementing new security controls, improving existing controls, transferring the risk (e.g., through insurance), or accepting the risk. Prioritize mitigation efforts based on the risk assessment findings. For example, if a risk is assessed as high-likelihood and high-impact, the mitigation strategy should be a top priority.
- Document and Communicate Findings: Document the entire risk assessment process, including the assets, threats, vulnerabilities, risk analysis, and mitigation strategies. Communicate the findings to relevant stakeholders, including management, IT staff, and the contractors themselves. This ensures that everyone is aware of the risks and their responsibilities.
- Regular Review and Update: Risk assessments are not one-time events. They should be reviewed and updated regularly, typically at least annually, or more frequently if there are significant changes to the environment, such as new systems, new contractors, or new threats. This ensures that the assessment remains relevant and effective.
Security Policy Development for Contractors
A well-defined security policy is essential for governing contractor access and ensuring that contractors understand their responsibilities. The policy should clearly articulate acceptable use, access control procedures, and data handling practices. It serves as a reference for contractors and provides a framework for enforcing security measures.The security policy should be organized into clear, concise sections, suitable for contractor onboarding:
- Purpose and Scope: Define the purpose of the policy and its scope. Specify who the policy applies to (i.e., all third-party contractors) and the assets and resources covered by the policy (e.g., networks, data, systems).
- Acceptable Use: Artikel the acceptable use of company resources, including devices, networks, and data. This section should prohibit unauthorized activities, such as accessing restricted data, installing unauthorized software, or using company resources for personal gain. Include specific examples of prohibited behaviors. For instance, explicitly state that contractors are prohibited from accessing or sharing sensitive company information without explicit authorization.
- Access Control: Describe the procedures for granting, managing, and revoking access to company resources. This section should address topics such as user authentication, authorization, password management, and access reviews. Define the process for requesting access, the approval workflow, and the required documentation.
- Data Handling: Specify the procedures for handling company data, including storage, transmission, and disposal. This section should address data classification, data encryption, and data loss prevention (DLP) measures. Provide clear guidelines on how contractors should handle sensitive data, such as personally identifiable information (PII) or financial data. For example, mandate that all sensitive data transmitted over a network be encrypted using secure protocols (e.g., TLS/SSL).
- Incident Reporting: Describe the procedures for reporting security incidents, such as data breaches, malware infections, or unauthorized access attempts. Provide contact information for reporting incidents and Artikel the steps contractors should take if they suspect a security breach. Include examples of what constitutes a reportable incident.
- Compliance and Enforcement: State the consequences of violating the security policy. This section should Artikel the disciplinary actions that may be taken against contractors who violate the policy, up to and including termination of the contract. Include a statement about the contractor’s responsibility to comply with all applicable laws and regulations.
- Training and Awareness: Specify the security training requirements for contractors. This may include mandatory security awareness training, role-based training, and training on specific company policies and procedures. Document the training requirements and the process for verifying completion.
- Policy Review and Updates: State that the policy will be reviewed and updated regularly, typically at least annually, or more frequently if there are significant changes to the environment. Include a statement about the contractor’s responsibility to stay informed of any policy updates.
Access Control Methods and Technologies
Managing third-party contractor access securely is crucial for protecting sensitive data and maintaining the integrity of your systems. Effective access control is a cornerstone of this security, ensuring that contractors have only the necessary permissions to perform their duties. This section will delve into the methods and technologies used to implement robust access controls, providing a comprehensive overview of best practices.
Access Control Methods
Several access control methods are essential for managing third-party contractor access. Implementing these methods helps to minimize the attack surface and limit the potential impact of security breaches.
- Multi-Factor Authentication (MFA): MFA requires users to provide multiple forms of identification to verify their identity. This typically involves something they know (password), something they have (security token), and something they are (biometric). MFA significantly enhances security by adding an extra layer of protection against unauthorized access, even if a password is compromised.
- Role-Based Access Control (RBAC): RBAC assigns permissions based on a user’s role within the organization. This simplifies access management by allowing administrators to define roles and assign permissions to those roles. When a contractor is assigned a role, they automatically inherit the associated permissions. RBAC ensures that contractors only have access to the resources they need to perform their job functions, minimizing the risk of accidental or malicious misuse of privileged access.
- Least Privilege: This principle dictates that users should only be granted the minimum level of access necessary to perform their tasks. This minimizes the potential damage from a security breach by limiting the scope of access that a compromised account can leverage. Regularly reviewing and adjusting permissions to adhere to the principle of least privilege is a critical security practice. For example, a contractor working on a specific project should only have access to the project’s files and resources, not the entire network.
Comparative Analysis of Access Control Technologies
Various technologies can be employed to implement access control, each with its strengths and weaknesses. Choosing the right technology depends on the specific needs of the organization and the nature of the third-party contractor relationship. The following table provides a comparative analysis of common access control technologies.
| Technology | Description | Advantages | Disadvantages |
|---|---|---|---|
| VPNs (Virtual Private Networks) | VPNs create an encrypted tunnel over a public network, allowing contractors to securely access internal resources. |
|
|
| Remote Access Tools (e.g., RDP, VNC) | These tools allow contractors to remotely connect to and control a computer or server. |
|
|
| Privileged Access Management (PAM) | PAM solutions manage and monitor privileged accounts, controlling access to critical systems and data. |
|
|
| Zero Trust Network Access (ZTNA) | ZTNA verifies every user and device before granting access to applications and resources. It operates on the principle of “never trust, always verify”. |
|
|
Implementing and Configuring Access Control Systems
Implementing and configuring access control systems for third-party contractors involves several key steps. A well-defined process is crucial for ensuring that access is granted securely and efficiently.
- Define Access Requirements: Clearly define the specific access needs of each contractor based on their role and project. This includes the resources they need to access (applications, data, systems) and the level of access required (read-only, read-write, etc.).
- Choose the Right Technologies: Select access control technologies that align with your security requirements and budget. Consider the complexity of the environment, the number of contractors, and the sensitivity of the data being accessed.
- Configure Access Control Systems: Configure the chosen technologies to enforce the defined access requirements. This may involve setting up user accounts, assigning roles, configuring permissions, and establishing security policies.
- Implement MFA: Enforce multi-factor authentication for all contractor access. This is a critical step in securing contractor accounts and protecting against unauthorized access.
- Establish Regular Audits: Regularly audit contractor access to ensure that permissions are still appropriate and that access control systems are functioning correctly. Review access logs and user activity to identify any anomalies or potential security breaches.
- Provide Training: Provide contractors with training on security policies, access control procedures, and the proper use of access control tools. This helps ensure that contractors understand their responsibilities and follow security best practices.
- Automate Access Management: Whenever possible, automate the process of granting, modifying, and revoking contractor access. This reduces the risk of human error and improves efficiency.
Secure Onboarding and Offboarding Procedures
Properly managing the lifecycle of third-party contractor access is paramount for maintaining a robust security posture. This includes establishing rigorous onboarding and offboarding procedures to ensure contractors have the necessary access for their work, and that access is promptly and completely revoked upon project completion or contract termination. Failing to do so can lead to significant security vulnerabilities, including data breaches and unauthorized access to sensitive information.
Secure Onboarding Procedures
A structured onboarding process is crucial for setting the foundation for secure contractor access. This process should be standardized and consistently applied to all third-party contractors. It ensures that access is granted in a controlled manner, minimizing the risk of security incidents.The following steps are essential for secure onboarding:
- Contractor Vetting and Verification: Before granting any access, conduct thorough vetting of the contractor and their personnel. This includes verifying their identity, checking references, and conducting background checks, especially for roles involving access to sensitive data or systems. The level of scrutiny should align with the sensitivity of the data and systems the contractor will interact with.
- Defining Access Requirements: Clearly define the specific access rights the contractor requires to perform their duties. This should be based on the principle of least privilege, granting only the minimum necessary access. Document these requirements meticulously, specifying the systems, data, and applications the contractor needs to access.
- Account Creation: Create a unique, individual account for each contractor. This account should be separate from any existing employee accounts. Enforce strong password policies and multi-factor authentication (MFA) to protect the account from unauthorized access.
- Access Provisioning: Grant access to the specified resources based on the defined requirements. Utilize access control methods such as role-based access control (RBAC) to streamline the process and ensure consistency. Regularly review and update access permissions as needed.
- Security Training: Provide comprehensive security training to the contractor, covering relevant company policies, data handling procedures, and security best practices. This training should include topics such as password security, phishing awareness, incident reporting, and acceptable use of company resources. Document that the contractor has completed the training.
- Device Provisioning (If Applicable): If the contractor requires company-provided devices, ensure these devices are securely configured with appropriate security software, such as antivirus and endpoint detection and response (EDR) solutions. Implement policies for device management, including encryption, remote wiping capabilities, and regular security updates.
- Onboarding Documentation: Maintain detailed documentation of the onboarding process, including the contractor’s access rights, security training records, and any devices issued. This documentation is essential for auditing and compliance purposes.
Offboarding Procedures
Offboarding is just as critical as onboarding. A well-defined offboarding process ensures that contractor access is immediately and completely revoked upon contract termination or project completion, mitigating the risk of unauthorized access and potential data breaches.Here are the critical steps for secure offboarding:
- Notification and Access Revocation: Immediately notify the relevant IT and security teams upon contract termination. Revoke all access rights promptly, including access to systems, applications, networks, and physical facilities. This should be a priority action.
- Account Deactivation/Deletion: Deactivate or delete the contractor’s account. The specific action (deactivation or deletion) will depend on the organization’s policies and any legal or regulatory requirements.
- Data Removal: Remove any company data from the contractor’s devices and personal accounts. If the contractor was using company-provided devices, retrieve them and wipe them securely. Ensure all company data stored on personal devices or cloud storage is deleted.
- Password Reset: If the contractor had any shared or privileged accounts, reset the passwords immediately.
- Access Audit: Conduct an audit to verify that all access has been revoked and that no unauthorized access remains.
- Documentation: Document the offboarding process, including the date and time of access revocation, account deactivation/deletion, and data removal.
- Device Return: If the contractor was provided with company-owned devices, ensure the devices are returned and properly secured. This involves wiping the device, verifying the data is securely deleted, and then securely storing or repurposing the device.
Documentation and Record-Keeping Requirements
Maintaining comprehensive documentation throughout the onboarding and offboarding processes is crucial for security, compliance, and auditing purposes. This documentation provides a clear record of access rights, security training, and access changes.The following documentation and record-keeping practices are essential:
- Onboarding Documentation:
- Contractor agreement, including scope of work and confidentiality clauses.
- Vetting results, including background check reports.
- Access request forms, detailing the required access permissions.
- Account creation records, including account details and password reset history.
- Security training records, including dates of completion and content covered.
- Device provisioning records, including device serial numbers and configurations.
- Offboarding Documentation:
- Contract termination notice.
- Access revocation logs, detailing the date and time of access revocation.
- Account deactivation/deletion records.
- Data removal verification.
- Device return confirmation.
- Regular Audits: Conduct regular audits of contractor access to verify that access rights are appropriate and that the onboarding and offboarding procedures are being followed correctly.
By implementing these procedures and maintaining thorough documentation, organizations can significantly reduce the risk of security breaches and ensure the secure management of third-party contractor access.
Identity and Access Management (IAM) Best Practices
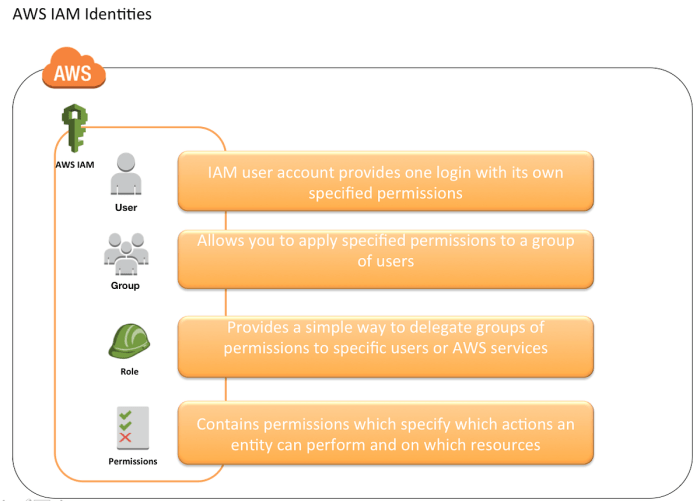
Managing third-party contractor access securely necessitates robust Identity and Access Management (IAM) practices. IAM is crucial for verifying identities, controlling access to resources, and ensuring compliance with security policies. Effective IAM not only minimizes the risk of unauthorized access but also streamlines the process of onboarding and offboarding contractors, improving operational efficiency.
Identity Verification and Access Provisioning
Implementing rigorous identity verification and access provisioning procedures is fundamental to securing access for third-party contractors. These practices ensure that only authorized individuals gain access to the necessary resources, minimizing the risk of data breaches and security incidents.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring contractors to verify their identity using multiple factors, such as something they know (password), something they have (mobile device), and something they are (biometric). This prevents unauthorized access even if a contractor’s password is compromised. For example, a contractor attempting to access a company’s cloud-based project management software might be prompted to enter a one-time code generated by an authenticator app on their smartphone after entering their username and password.
- Role-Based Access Control (RBAC): RBAC grants access based on a contractor’s role within the project. This principle ensures that contractors only have access to the resources and data necessary to perform their specific tasks. For instance, a software developer might have access to the source code repository, while a marketing contractor would have access to marketing materials and customer data relevant to their campaigns.
- Least Privilege Principle: This principle dictates that contractors should be granted the minimum level of access necessary to perform their job functions. By limiting access, the potential damage from a compromised account is significantly reduced. A good example is restricting a contractor’s access to a database to only the specific tables and columns they need, rather than granting them full database administrator privileges.
- Regular Access Reviews: Periodic reviews of contractor access rights are essential to ensure that access remains appropriate and aligned with current project requirements. These reviews should involve the project manager and the contractor’s supervisor to validate the continued need for access. If a contractor’s role or project responsibilities change, their access rights should be promptly adjusted.
- Automated Provisioning and De-provisioning: Implementing automated processes for onboarding and offboarding contractors significantly reduces the risk of human error and ensures timely access management. These automated systems can automatically create, modify, and disable user accounts based on predefined rules and workflows.
Checklist for IAM Policy and Procedure Compliance
A comprehensive checklist helps organizations systematically ensure that their IAM policies and procedures are being followed consistently. This checklist serves as a practical tool for verifying compliance and identifying areas for improvement.
- Identity Verification: Verify the contractor’s identity using reliable methods (e.g., background checks, verification of credentials).
- Access Request Approval: Ensure all access requests are approved by the appropriate authority (e.g., project manager, security officer).
- Role Assignment: Assign access rights based on the contractor’s role and the principle of least privilege.
- MFA Enforcement: Implement and enforce MFA for all contractor access to sensitive systems and data.
- Password Management: Enforce strong password policies and provide guidance on password best practices.
- Access Reviews: Conduct regular access reviews to ensure that access rights are still appropriate.
- De-provisioning: Immediately revoke access upon the contractor’s departure or project completion.
- Audit Logging: Enable comprehensive audit logging to track all access attempts and activities.
- Policy Updates: Regularly update IAM policies and procedures to address emerging threats and changing business needs.
- Training and Awareness: Provide contractors with security awareness training, including IAM policies and procedures.
IAM Workflow for Automated Access Provisioning and De-provisioning
An automated IAM workflow streamlines the process of granting and revoking access, reducing manual effort and minimizing the risk of errors. The workflow should encompass the entire lifecycle of a contractor’s access, from initial request to final termination.
Workflow Stages:
- Access Request: The project manager or authorized personnel submits an access request for a new contractor. The request specifies the contractor’s role, the required resources, and the project duration.
- Approval: The access request is routed to the appropriate approver (e.g., security officer, department head) for review and approval.
- Provisioning: Upon approval, the IAM system automatically provisions the necessary access rights. This may include creating user accounts, assigning roles, and granting access to specific applications and data.
- Notification: The contractor receives a notification with their login credentials and instructions for accessing the required resources.
- Monitoring and Auditing: The system continuously monitors the contractor’s access and activities, generating audit logs for security and compliance purposes.
- De-provisioning: Upon project completion or contractor termination, the system automatically revokes all access rights. This includes disabling user accounts and removing access to all resources.
Example:
Consider a scenario where a third-party software development contractor is hired to work on a new project. The project manager initiates an access request within the IAM system, specifying the contractor’s role as “Developer” and the project’s start and end dates. The request is automatically routed to the security officer for approval. Upon approval, the IAM system automatically creates a user account for the contractor, assigns the “Developer” role, and grants access to the project’s code repository, development environment, and project management tools. When the project concludes, the system automatically deactivates the contractor’s account, revoking all access rights, and ensuring the organization’s resources are protected.
Data Security and Protection Measures
Securing data accessed by third-party contractors is paramount to protecting sensitive information and maintaining the integrity of your organization. Implementing robust data security measures is not merely a technical requirement; it’s a fundamental aspect of responsible business conduct and legal compliance. Failing to adequately protect data can lead to significant financial losses, reputational damage, and legal repercussions. This section Artikels key data security measures and best practices to ensure the confidentiality, integrity, and availability of your data when contractors are involved.
Data Encryption Strategies
Data encryption is a critical security measure that transforms data into an unreadable format, protecting it from unauthorized access. This is particularly important when data is at rest (stored on servers, laptops, or external drives) and in transit (being transferred across networks or the internet).
- Encryption at Rest: This involves encrypting data stored on hard drives, databases, and cloud storage. Implementing encryption at rest ensures that even if a device is lost or stolen, the data remains inaccessible without the correct decryption key.
- Example: Using full-disk encryption (FDE) on laptops issued to contractors. This encrypts the entire hard drive, requiring a password or other authentication method to access the data.
- Encryption in Transit: Securing data during transfer is crucial. This involves using protocols like Transport Layer Security (TLS) or Secure Sockets Layer (SSL) to encrypt data transmitted over networks.
- Example: Using HTTPS for all web traffic, ensuring that data exchanged between a contractor’s web browser and your organization’s servers is encrypted.
- Database Encryption: Encrypting sensitive data within databases protects it from unauthorized access, even if the database server is compromised.
- Example: Using column-level encryption to protect specific fields containing sensitive information, such as social security numbers or credit card details.
Data Loss Prevention (DLP) Implementation
Data Loss Prevention (DLP) tools and strategies are designed to prevent sensitive data from leaving your organization’s control. DLP systems monitor, detect, and block unauthorized data transfers, whether accidental or malicious.
- DLP Tools: These tools can scan data at rest, in use, and in motion to identify and prevent data leakage.
- Example: Implementing DLP software that monitors email attachments to prevent contractors from sending sensitive documents outside the organization.
- Network Monitoring: Monitoring network traffic for suspicious activity, such as unauthorized file transfers or unusual data volumes, can help identify potential data breaches.
- Example: Using network intrusion detection systems (IDS) to detect and alert on unusual network activity associated with contractor accounts.
- Endpoint Security: Securing contractor devices, such as laptops and mobile phones, with endpoint security solutions that prevent data leakage.
- Example: Requiring contractors to use organization-approved devices with pre-installed DLP agents that monitor and control data access and transfer.
Data Handling Guidelines for Contractors
Clear and comprehensive data handling guidelines are essential to ensure contractors understand their responsibilities regarding data security. These guidelines should cover all aspects of data storage, transfer, and disposal.
- Data Storage Policies: Defining where and how contractors can store data.
- Example: Specifying that contractors must store sensitive data only on encrypted company-provided devices or within approved cloud storage solutions. Prohibiting the use of personal cloud storage services for company data.
- Data Transfer Protocols: Establishing secure methods for transferring data.
- Example: Requiring the use of secure file transfer protocols (SFTP) or encrypted email for transferring sensitive data. Prohibiting the use of unencrypted email or personal file-sharing services.
- Data Disposal Procedures: Implementing secure data disposal methods to prevent data breaches.
- Example: Requiring contractors to securely wipe devices before returning them, using data shredding software or physical destruction methods for hard drives.
- Data Classification: Categorizing data based on its sensitivity to ensure appropriate security controls are applied.
- Example: Classifying data as “Confidential,” “Internal Use Only,” or “Public” and applying different security measures accordingly. Confidential data might require stronger encryption and stricter access controls.
Implementing Data Security Measures
Successfully implementing data security measures requires a combination of technical controls, policy enforcement, and ongoing monitoring. This section Artikels practical steps to integrate these measures into a contractor access environment.
- Technical Controls Implementation: Implementing the technical solutions Artikeld above.
- Example: Deploying encryption software on contractor-issued devices, configuring DLP policies to monitor data transfers, and setting up secure file transfer protocols.
- Policy Enforcement: Ensuring contractors understand and adhere to data handling policies.
- Example: Providing contractors with comprehensive training on data security policies and procedures, including regular updates to reflect evolving threats. Requiring contractors to sign agreements acknowledging their responsibilities.
- Regular Auditing and Monitoring: Regularly auditing contractor access and data handling practices.
- Example: Conducting regular security audits to ensure compliance with policies and identify any vulnerabilities. Monitoring contractor activity through security information and event management (SIEM) systems to detect and respond to security incidents.
- Incident Response Planning: Developing a plan to address data breaches or security incidents.
- Example: Establishing clear procedures for reporting security incidents, containing breaches, and notifying affected parties. Regularly testing the incident response plan to ensure its effectiveness.
Network Segmentation and Isolation Techniques
Effectively managing third-party contractor access necessitates robust network segmentation and isolation strategies. This approach minimizes the potential attack surface, containing breaches and preventing unauthorized access to sensitive internal systems. By carefully designing and implementing these techniques, organizations can significantly enhance their security posture and reduce the risk of data compromise.
Importance of Network Segmentation
Network segmentation is a critical security practice that divides a network into smaller, isolated segments. This isolation limits the impact of a security breach by preventing attackers from easily moving laterally across the entire network. If a contractor’s device is compromised, the damage is contained within their designated segment, protecting critical internal systems and data. This approach aligns with the principle of least privilege, granting contractors access only to the resources they absolutely need.
Network Isolation Techniques
Several techniques can be employed to achieve effective network isolation. These methods, often used in combination, create security barriers and control network traffic flow.
- Virtual LANs (VLANs): VLANs logically segment a network by grouping devices together, regardless of their physical location. This allows for the creation of isolated broadcast domains, where traffic within one VLAN does not reach other VLANs unless explicitly routed. For example, a dedicated VLAN can be created for contractor access, separating their traffic from internal corporate networks.
- Firewalls: Firewalls act as security checkpoints, inspecting and controlling network traffic based on predefined rules. They can be used to filter traffic between network segments, allowing only authorized communication. Firewalls can be configured to permit contractors access only to specific servers and applications, blocking access to other internal resources.
- Micro-segmentation: Micro-segmentation extends the principles of segmentation down to individual workloads or applications. This approach uses software-defined networking (SDN) and other technologies to create granular security policies, further isolating resources and minimizing the blast radius of a potential breach. This is particularly useful in cloud environments where workloads can be dynamically provisioned and deprovisioned.
- Network Access Control (NAC): NAC solutions enforce security policies before devices are allowed to connect to the network. They can check device posture (e.g., antivirus status, operating system patch level) and restrict access based on compliance. NAC can ensure that contractor devices meet minimum security requirements before being granted network access, and if a device fails a security check, it can be quarantined or denied access.
Designing a Secure Network Architecture
A well-designed network architecture is crucial for effectively implementing network segmentation and isolation. The architecture should prioritize minimizing the attack surface and restricting contractor access to only the necessary resources.
- Dedicated Contractor Network Segment: Create a separate network segment specifically for contractor access. This segment should be isolated from the internal corporate network using VLANs and firewalls.
- Restricted Access to Resources: Implement strict firewall rules to control contractor access to internal resources. Grant access only to the specific servers, applications, and data required for their work. For instance, a contractor working on a specific project should only have access to the project’s file shares and necessary development tools.
- Use of a Demilitarized Zone (DMZ): Consider placing publicly accessible services (e.g., web servers) in a DMZ. This isolates these services from the internal network, protecting them from direct attacks and preventing attackers from gaining access to internal resources if the service is compromised. Contractors might access the DMZ to work on public-facing applications, but should not have direct access to internal databases.
- Regular Security Audits and Monitoring: Implement regular security audits and monitoring to ensure that network segmentation and isolation policies are effective and that access controls are properly enforced. This includes reviewing firewall rules, monitoring network traffic, and analyzing logs for suspicious activity.
- Multi-Factor Authentication (MFA): Enforce MFA for all contractor access, especially for access to sensitive resources. This adds an extra layer of security, making it more difficult for attackers to gain unauthorized access, even if they have compromised a contractor’s credentials.
Monitoring and Auditing Contractor Access
Maintaining robust security necessitates continuous vigilance. Regularly monitoring and auditing contractor access is paramount to identifying and mitigating potential threats. This proactive approach helps ensure that contractors only access the resources they need, that their activities align with established policies, and that any anomalous behavior is quickly addressed.
Importance of Monitoring Contractor Access for Suspicious Activity
Monitoring contractor access for suspicious activity is critical for several reasons. It acts as a deterrent, discourages malicious actions, and provides early detection of potential security breaches.
- Early Threat Detection: Monitoring allows for the identification of unusual access patterns, such as access outside of regular working hours, access to sensitive data that is not part of the contractor’s scope of work, or multiple failed login attempts. These could be indicators of a compromised account or malicious intent.
- Compliance and Policy Enforcement: Continuous monitoring helps ensure contractors adhere to established security policies and compliance requirements. This includes verifying that contractors are using only authorized systems and accessing only permitted data.
- Incident Response Enablement: Monitoring provides valuable data for incident response efforts. If a security incident occurs, access logs and activity records can be used to quickly determine the scope of the breach, identify the affected systems and data, and assess the impact.
- Data Loss Prevention: By monitoring data access and transfer activities, organizations can detect and prevent unauthorized data exfiltration. This includes monitoring for unusual data downloads, file transfers to unauthorized locations, or attempts to access restricted data.
- Account Compromise Detection: Monitoring can help identify compromised contractor accounts. If an account is compromised, attackers may use it to access sensitive data, install malware, or move laterally within the network. Monitoring can detect these activities, such as unusual geographical access locations, unusual access times, or elevated privileges.
Creating a System for Auditing Contractor Access Logs
A well-defined system for regularly auditing contractor access logs is essential for proactively identifying and addressing security vulnerabilities. This system should be comprehensive, automated, and aligned with established security policies.
Establishing a system for auditing contractor access logs requires several key components:
- Define Audit Scope: Clearly define the scope of the audit. This includes specifying which systems, applications, and data will be audited, as well as the frequency of the audits. The audit scope should be based on the organization’s risk assessment and security policies.
- Log Collection and Storage: Implement a robust log collection and storage mechanism. All contractor access logs should be centrally collected and stored in a secure, tamper-proof location. This should include logs from all relevant systems, such as servers, applications, databases, and network devices.
- Automated Log Analysis: Automate the log analysis process as much as possible. This involves using security information and event management (SIEM) systems or other automated tools to analyze logs for suspicious activity.
- Establish Baseline and Thresholds: Establish a baseline of normal contractor activity. This will help identify deviations from the norm. Set thresholds for various activities, such as failed login attempts, data access patterns, and file transfers.
- Regular Reporting: Generate regular reports on contractor access activity. These reports should summarize the findings of the audit, identify any potential security breaches, and recommend remediation actions.
- Review and Remediation: Establish a process for reviewing audit findings and taking appropriate remediation actions. This may include investigating suspicious activity, revoking access, updating security policies, or implementing additional security controls.
- Documentation: Maintain detailed documentation of the audit process, including the audit scope, procedures, findings, and remediation actions.
Organizing a Process for Incident Response Related to Contractor Access
A well-defined incident response process is crucial for effectively handling security incidents related to contractor access. This process should be clearly documented, regularly tested, and updated to reflect changes in the threat landscape and the organization’s security posture.
The incident response process should include the following steps:
- Preparation: This involves establishing a dedicated incident response team, defining roles and responsibilities, developing incident response plans, and providing training to relevant personnel.
- Identification: Identify and verify security incidents related to contractor access. This involves monitoring access logs, reviewing security alerts, and investigating suspicious activity.
- Containment: Contain the incident to prevent further damage. This may involve isolating compromised systems, revoking contractor access, and blocking malicious activity.
- Eradication: Remove the cause of the incident. This may involve removing malware, patching vulnerabilities, or restoring compromised systems from backups.
- Recovery: Restore affected systems and data to their normal operating state. This includes verifying that systems are secure and that data is protected.
- Post-Incident Activity: After an incident, conduct a thorough review to identify the root cause, assess the impact, and implement measures to prevent similar incidents in the future. This should include updating security policies, improving security controls, and providing additional training.
- Communication: Maintain clear and timely communication throughout the incident response process, both internally and externally (as required). This includes notifying relevant stakeholders, such as management, legal counsel, and law enforcement (if necessary).
Training and Awareness Programs

A robust training and awareness program is crucial for ensuring third-party contractors understand and adhere to your organization’s security policies. This program equips contractors with the knowledge and skills necessary to recognize and mitigate security risks, protecting sensitive data and systems. It fosters a security-conscious culture, essential for maintaining a strong security posture.
Key Elements of a Comprehensive Security Awareness Training Program
A comprehensive security awareness program for third-party contractors should encompass several key elements to ensure its effectiveness. These elements should be integrated to create a cohesive and impactful learning experience.
- Onboarding Training: This is the initial training provided to contractors upon their engagement. It should cover fundamental security policies, acceptable use of IT resources, and the organization’s security expectations. This sets the baseline for security awareness.
- Role-Based Training: Tailoring training to the specific roles and responsibilities of the contractor is crucial. Different roles require different levels of access and exposure to sensitive information, necessitating customized training modules.
- Regular Refresher Training: Periodic refresher training, ideally at least annually, reinforces key concepts and keeps contractors up-to-date on the latest threats and vulnerabilities.
- Simulated Phishing Exercises: Conducting simulated phishing campaigns helps contractors recognize and respond to phishing attempts. Analyzing the results provides valuable insights into areas where further training is needed.
- Policy Acknowledgement: Contractors should be required to acknowledge and agree to adhere to all relevant security policies, often through a signed agreement or electronic acceptance.
- Reporting Procedures: Clear procedures for reporting security incidents, such as phishing attempts or data breaches, should be clearly communicated and readily accessible.
- Assessment and Feedback: Incorporating quizzes or assessments to evaluate understanding and providing feedback helps reinforce learning and identify areas needing improvement.
Importance of Regular Training Updates
The threat landscape is constantly evolving, with new attack vectors and techniques emerging frequently. Regular updates to the training program are essential to keep contractors informed and prepared to face these evolving threats.
- Addressing Emerging Threats: Training programs should be updated to address new threats, such as ransomware, advanced persistent threats (APTs), and zero-day exploits. For example, a training module could specifically address the latest ransomware variants and how to identify and report them.
- Adapting to New Technologies: As organizations adopt new technologies, such as cloud services or mobile devices, the training program must be updated to address the associated security risks. This includes training on secure usage of these technologies.
- Incorporating Lessons Learned: Security incidents, both within the organization and industry-wide, provide valuable lessons. Training updates should incorporate these lessons learned to prevent similar incidents in the future. For instance, after a data breach, the training might be updated to emphasize the importance of data encryption.
- Compliance with Regulations: Regulatory requirements, such as GDPR or CCPA, are constantly changing. Training programs must be updated to ensure contractors understand and comply with the latest regulations.
Examples of Training Modules
Training modules should cover various topics relevant to third-party contractor security, presented in an engaging and informative manner. The content should be tailored to the specific roles and responsibilities of the contractors.
- Phishing Awareness: This module teaches contractors how to identify phishing emails, recognize suspicious links and attachments, and report phishing attempts. It should include examples of common phishing tactics and simulated phishing exercises. For example, a training module could present a realistic phishing email and ask the contractor to identify the red flags.
- Social Engineering Awareness: This module covers social engineering techniques, such as pretexting and baiting, and how to avoid falling victim to them. It should provide examples of social engineering scenarios and teach contractors how to recognize and respond to them.
- Data Privacy and Protection: This module covers data privacy regulations, such as GDPR and CCPA, and the organization’s data protection policies. It should explain the importance of protecting sensitive data and the consequences of data breaches. For example, the training could Artikel the steps contractors must take to handle personal data securely.
- Password Security: This module emphasizes the importance of strong passwords, password management, and the risks associated with weak passwords. It should provide guidelines for creating and managing strong passwords.
- Malware and Virus Awareness: This module teaches contractors about malware and viruses, how they spread, and how to prevent infection. It should cover topics such as identifying suspicious files and websites.
- Physical Security: This module covers physical security measures, such as access control to facilities, secure handling of physical media, and the importance of reporting suspicious activity.
Incident Response and Disaster Recovery Planning

Incorporating third-party contractors into your incident response and disaster recovery plans is critical for maintaining business continuity and minimizing the impact of security breaches or unforeseen events. Failure to do so can leave significant vulnerabilities, potentially exacerbating the damage and prolonging recovery times. A well-defined plan ensures that contractor access is properly managed during crises, protecting sensitive data and maintaining operational efficiency.
Integrating Contractors into Incident Response
Effective incident response necessitates clear protocols for handling contractor involvement. This ensures a coordinated and efficient response when a security incident impacts or involves third-party contractors.
- Define Roles and Responsibilities: Clearly delineate the roles and responsibilities of both your internal team and any relevant contractors during an incident. This includes identifying who is responsible for communication, containment, eradication, and recovery. Specify the contractor’s level of access during the incident and what actions they are authorized to take.
- Establish Communication Protocols: Implement clear communication channels and protocols to ensure rapid and accurate information sharing. Include contact information for key personnel from both your organization and the contractors. Consider using secure communication methods like encrypted messaging or dedicated incident response platforms.
- Contractor Incident Reporting: Ensure contractors understand their obligation to report any security incidents they observe or are involved in. Provide them with a clear reporting process, including whom to contact and what information to provide.
- Access Control During Incidents: Define how contractor access will be managed during an incident. This may involve temporarily restricting access, granting elevated privileges for specific tasks, or revoking access altogether. Ensure these actions are documented and audited.
- Containment and Eradication Procedures: Develop procedures for containing and eradicating threats that involve contractors. This might include isolating compromised systems, revoking compromised credentials, and scanning for malware. Contractor participation in these steps must be clearly defined.
- Forensic Investigation: Include contractors in forensic investigations when necessary, especially if they have access to affected systems or data. Ensure they adhere to established forensic procedures and chain-of-custody protocols.
- Post-Incident Review: Conduct a post-incident review that includes contractor performance. This review should identify lessons learned and areas for improvement in the incident response plan, especially regarding contractor involvement.
Steps for Security Incident Involving a Contractor
When a security incident involves a contractor, specific steps are crucial for an effective response. The following steps provide a structured approach to manage such situations:
- Verification and Assessment: Verify the incident and assess its scope and impact. Determine if the contractor’s access was a factor and the extent of the compromise. Gather initial evidence to understand the nature of the incident.
- Containment: Immediately contain the incident. This may involve isolating affected systems, revoking the contractor’s access, or implementing temporary network segmentation.
- Notification: Notify the appropriate stakeholders, including the contractor, relevant internal teams, and legal counsel if necessary. Ensure all parties are informed of the incident and the actions being taken.
- Investigation: Conduct a thorough investigation to determine the root cause of the incident, the extent of the damage, and the specific actions of the contractor. This may involve forensic analysis of systems and data.
- Eradication: Remove the threat and remediate any vulnerabilities exploited in the incident. This could include patching systems, removing malware, and restoring compromised data.
- Recovery: Restore affected systems and data to their pre-incident state. Verify the integrity of restored systems and data.
- Post-Incident Activities: Conduct a post-incident review to analyze the incident, identify lessons learned, and update the incident response plan. Evaluate the contractor’s performance and consider any necessary changes to the contract.
Disaster Recovery Checklist for Contractor Access
A well-defined disaster recovery plan must account for contractor access to ensure business continuity. This checklist Artikels key considerations:
- Contractor Access Requirements: Identify which contractors are essential for disaster recovery and what level of access they require to critical systems and data.
- Alternate Access Methods: Establish alternative access methods for contractors in case primary access methods are unavailable. This could include backup credentials, remote access solutions, or alternative communication channels.
- Access Verification and Validation: Implement procedures to verify and validate contractor access during disaster recovery. This ensures that only authorized contractors have access to critical resources.
- Data Backup and Recovery: Ensure that contractor-related data and configurations are included in backup and recovery plans. This is essential for restoring systems and data quickly and accurately.
- Communication and Coordination: Establish clear communication channels and protocols to coordinate contractor activities during disaster recovery. This includes providing contractors with up-to-date information and instructions.
- Contractor Availability and Response Time: Define the expected availability and response time of contractors during a disaster. Ensure that contractors are aware of their obligations and are prepared to respond quickly.
- Testing and Exercises: Regularly test the disaster recovery plan, including contractor access scenarios. This helps to identify any weaknesses and ensures that the plan is effective.
- Documentation and Training: Maintain up-to-date documentation of contractor access procedures and provide training to relevant personnel. This ensures that everyone understands their roles and responsibilities.
Final Thoughts
In conclusion, effectively managing third-party contractor access requires a proactive, multi-layered approach. By implementing the strategies Artikeld in this guide, organizations can significantly reduce their risk exposure, maintain data integrity, and foster a secure environment for both internal teams and external collaborators. Remember, ongoing vigilance, continuous improvement, and a commitment to security best practices are paramount in the ever-evolving landscape of cyber threats.
The implementation of a robust third-party access management system is not just a security measure; it is an investment in the long-term success and resilience of your organization.
FAQ Explained
What is the primary goal of managing third-party contractor access securely?
The primary goal is to balance the need for contractors to perform their duties with the imperative to protect sensitive data and maintain the security posture of the organization.
What are the key differences between RBAC and ABAC in access control?
RBAC (Role-Based Access Control) assigns permissions based on a user’s role, while ABAC (Attribute-Based Access Control) uses attributes of the user, the resource, and the environment to determine access.
How often should access reviews for third-party contractors be conducted?
Access reviews should be conducted at least quarterly, or more frequently if the contractor’s role or access requirements change significantly.
What should be included in a contractor’s security awareness training?
Training should cover topics like phishing, social engineering, data privacy, password security, and the organization’s specific security policies.
What are the legal implications of data breaches caused by third-party contractors?
Legal implications can include fines, lawsuits, and reputational damage, depending on the type of data breached and the jurisdiction.