Navigating the landscape of data privacy can be complex, and understanding how to handle a data subject access request (DSAR) under GDPR is a crucial aspect of maintaining compliance. This guide provides a detailed roadmap, designed to demystify the process and equip you with the knowledge to effectively respond to these requests.
From grasping the fundamentals of a DSAR to addressing intricate issues like third-party data and automated decision-making, this comprehensive resource offers practical insights and actionable strategies. We’ll explore each stage, providing clear explanations, best practices, and real-world examples to ensure you’re well-prepared to handle DSARs efficiently and in accordance with GDPR regulations.
Understanding the Basics of a DSAR
A Data Subject Access Request (DSAR) is a fundamental right under the General Data Protection Regulation (GDPR), allowing individuals to access their personal data held by an organization. This section clarifies the core concepts and provides essential context for handling these requests effectively. Understanding these basics is crucial for compliance and maintaining transparency with data subjects.
Definition of a Data Subject Access Request
A Data Subject Access Request (DSAR) is a formal request made by an individual to an organization, asking for information about their personal data that the organization holds. This request enables the individual to understand how their data is being used and to verify the lawfulness of its processing.
Who Can Make a DSAR
Anyone whose personal data is processed by an organization can make a DSAR. This includes, but is not limited to, customers, employees, website visitors, and individuals who have otherwise interacted with the organization. The right to make a DSAR is not limited by age or nationality.
Legal Basis for DSARs under GDPR
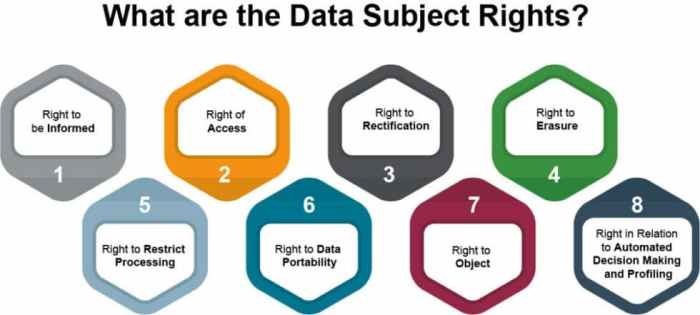
The legal basis for DSARs is primarily Article 15 of the GDPR. This article grants data subjects the right to access their personal data and includes the following:
- Right to confirmation: Data subjects have the right to obtain confirmation from the organization as to whether or not personal data concerning them is being processed.
- Right to access: If personal data is being processed, data subjects have the right to access that personal data. This includes obtaining a copy of the personal data.
- Right to information: Data subjects have the right to receive information about the purposes of the processing, the categories of personal data concerned, the recipients or categories of recipients to whom the personal data have been or will be disclosed, the period for which the personal data will be stored, and the existence of the right to rectification or erasure of personal data.
- Right to other information: This also includes information about the source of the data (if not collected from the data subject), the existence of automated decision-making, including profiling, and meaningful information about the logic involved, as well as the significance and the envisaged consequences of such processing for the data subject.
The GDPR emphasizes that organizations must respond to DSARs without undue delay and, in any event, within one month of receipt of the request. This deadline can be extended by two further months where necessary, taking into account the complexity and number of the requests. The organization must inform the data subject of any such extension within one month of receipt of the request, together with the reasons for the delay.
Receiving and Acknowledging a DSAR
Receiving and properly acknowledging a Data Subject Access Request (DSAR) is the crucial first step in fulfilling your obligations under GDPR. This stage sets the tone for the entire process and directly impacts your organization’s compliance and reputation. It is essential to have clear procedures and trained personnel to handle DSARs efficiently and respectfully.
Proper Channels for Receiving a DSAR
Establishing designated channels for receiving DSARs ensures requests are handled consistently and efficiently. This clarity minimizes the risk of requests being overlooked or delayed.
- Designated Contact Points: Clearly define specific channels for receiving DSARs. This typically includes an email address (e.g., [email protected]), a dedicated postal address, and potentially a web form on your website. These contact points should be easily accessible and prominently displayed in your privacy policy and on your website.
- Avoiding Unofficial Channels: While it’s important to be responsive, discourage the submission of DSARs through informal channels such as personal employee email addresses or social media. These channels are less secure and make it harder to track and manage requests effectively.
- Training and Awareness: Train all employees, especially those in customer service, reception, or any role that may interact with data subjects, to recognize and properly forward DSARs to the designated contact points. This awareness prevents accidental mishandling or delays.
- Record Keeping: Implement a system for logging all received DSARs, including the date and time of receipt, the method of submission, and the contact information of the data subject. This record-keeping is crucial for tracking progress and demonstrating compliance.
Information Needed to Validate a DSAR
Validating a DSAR is a critical step to ensure that the request is legitimate and that personal data is only disclosed to the correct individual. Verification processes help to prevent data breaches and protect the privacy of data subjects.
- Identity Verification: Verify the identity of the data subject. This is paramount to prevent unauthorized access to personal data. Acceptable forms of verification include:
- Copy of Identification: Request a copy of a government-issued ID (e.g., passport, driver’s license). Always ensure this request is proportionate and necessary, and securely store the copy.
- Security Questions: Utilize security questions, especially if the data subject has an existing account with your organization.
- Account Verification: If the data subject has an online account, verify their identity through the account login process.
- Sufficient Information: Ensure the request provides enough information to locate the data. This may include the data subject’s name, contact details, and any other relevant information that could help identify the specific data they are requesting. If the request is vague, you may need to ask for more details.
- Proportionality: The level of verification should be proportionate to the sensitivity of the data and the potential risks involved. For example, a request for a less sensitive dataset might require less stringent verification than a request for financial records.
- Documentation: Document the verification process, including the methods used and the outcome. This documentation is essential for demonstrating compliance.
Timeframe for Acknowledging a DSAR
Acknowledging a DSAR promptly demonstrates your commitment to data privacy and sets expectations for the data subject. Adhering to the stipulated timeframe is a legal requirement under GDPR.
- Acknowledgment Deadline: You must acknowledge receipt of a DSAR without undue delay, and in any event, within one month of receiving the request.
- Content of the Acknowledgment: The acknowledgment should:
- Confirm receipt of the request.
- Provide an estimated timeframe for a full response.
- Inform the data subject if you require additional information to process the request.
- Inform the data subject if you intend to extend the timeframe for a full response (and the reasons for the extension).
- Extension of Timeframe: In complex cases, you may extend the timeframe for responding to the DSAR by a further two months. However, you must inform the data subject of the extension and the reasons for the delay within one month of receiving the request.
The GDPR allows for an extension when a DSAR is complex or involves a large number of requests. However, the data subject must be informed of the extension within one month of the original request.
- Record Keeping: Keep a record of all communications with the data subject, including the date of the acknowledgment, the content of the acknowledgment, and any extensions granted. This documentation is essential for demonstrating compliance.
Verifying the Data Subject’s Identity
Verifying the identity of the data subject is a crucial step in responding to a DSAR. It ensures that personal data is only disclosed to the correct individual, thereby protecting their privacy and complying with GDPR. Improper verification can lead to data breaches and significant penalties. This section Artikels the steps, processes, and acceptable forms of identification necessary for secure identity verification.
Steps Involved in Verifying a Data Subject’s Identity
The process of verifying a data subject’s identity should be robust and consistent. The steps Artikeld below provide a structured approach.
- Initial Contact and Information Gathering: Upon receiving a DSAR, the first step is to gather initial information from the data subject. This includes their full name, contact details (email, phone number, address), and any other information they provided when interacting with your organization.
- Matching Information with Existing Records: Cross-reference the provided information with your existing records to confirm the data subject’s identity. This might involve checking names, email addresses, and any other identifying details. The more data you have on file, the easier and more reliable this step becomes.
- Requesting Additional Verification Information: If the initial information is insufficient to verify the identity, request additional information from the data subject. This might include a copy of a government-issued ID, utility bill, or other documents that can help confirm their identity. The specific requirements should be proportionate to the sensitivity of the data requested.
- Verifying the Authenticity of Documents: If copies of documents are provided, verify their authenticity. This could involve checking for security features, comparing the document against known templates, or contacting the issuing authority to confirm its validity. Be aware of potential forgeries.
- Implementing Secure Communication Channels: Utilize secure communication channels for exchanging sensitive information, such as encrypted email or secure file transfer services. Avoid using unencrypted email for sending or receiving copies of IDs or other sensitive data.
- Documenting the Verification Process: Maintain a detailed record of the verification process, including the information requested, the documents received, the verification methods used, and the date and time of each step. This documentation is crucial for demonstrating compliance with GDPR.
Designing a Process for Secure Identity Verification
A well-designed process minimizes the risk of data breaches and unauthorized access. This process should include specific measures.
- Multi-Factor Authentication (MFA): Implement MFA where possible, particularly when data subjects access their personal data through online portals. This could involve a combination of password, a one-time code sent to a mobile device, and biometric verification.
- Secure Data Storage: Store copies of identification documents securely, adhering to strict data protection principles. Encrypt the data, restrict access to authorized personnel only, and regularly audit access logs.
- Data Minimization: Request only the minimum amount of information necessary to verify the data subject’s identity. Avoid requesting excessive or irrelevant personal data.
- Regular Training: Provide regular training to employees on identity verification procedures, data security best practices, and the importance of protecting personal data.
- Regular Review and Updates: Periodically review and update the identity verification process to ensure it remains effective and compliant with evolving data protection regulations and security threats. The digital landscape is constantly changing, so staying current is essential.
- Secure Document Disposal: Establish a secure process for the disposal of any physical copies of identification documents once the verification process is complete and the retention period has expired. Shred or incinerate the documents securely.
Acceptable Forms of Identification
The types of identification accepted should be clearly defined and proportionate to the sensitivity of the data requested. Here are examples of acceptable forms of identification.
- Government-Issued Photo ID: A valid passport, driver’s license, or national identity card. These documents typically include a photograph and other identifying information.
- Utility Bill: A recent utility bill (e.g., electricity, gas, water) showing the data subject’s name and address. This confirms the address associated with their account.
- Bank Statement: A recent bank statement showing the data subject’s name and address. This helps verify the financial relationship.
- Credit Card Statement: A recent credit card statement showing the data subject’s name and address.
- Other Official Documents: Other official documents that include the data subject’s name and address, such as a tax return or a council tax bill.
It is essential to note that the specific requirements may vary depending on the nature of the data requested and the risk involved. Always prioritize the security and privacy of the data subject’s information.
Locating and Retrieving Data
After successfully verifying the data subject’s identity, the next critical step in fulfilling a DSAR is locating and retrieving the requested personal data. This involves a systematic approach to identify all relevant data sources and efficiently extract the required information. The process must be thorough to ensure completeness while adhering to the principles of data minimization and accuracy.
Step-by-Step Guide for Locating Personal Data
Effectively locating personal data requires a structured approach. This ensures that all relevant information is considered and that no data is inadvertently overlooked. The following steps provide a clear framework for this process.
- Define the Scope: Clearly understand the scope of the DSAR. Identify the specific types of data requested and the time period it covers. Review the data subject’s request thoroughly.
- Identify Data Sources: Determine all potential locations where the data subject’s personal data might be stored. This could include databases, email systems, CRM systems, cloud storage, physical files, and any other relevant systems or repositories. Consider all departments and systems that may process personal data.
- Create a Data Inventory (If Applicable): If a data inventory or data map exists, use it to guide the search. This can significantly speed up the process by identifying where different types of data are stored. Regularly updating the data inventory is crucial for its effectiveness.
- Conduct Searches: Initiate searches across the identified data sources. Use the data subject’s name, email address, and any other relevant identifiers to locate the data. Employ a variety of search terms and techniques to ensure comprehensive results.
- Document the Search Process: Maintain a detailed record of the search process, including the data sources searched, the search terms used, and the date and time of the search. This documentation is essential for demonstrating compliance and can be invaluable if questions arise.
- Review Search Results: Carefully review the search results to identify the relevant personal data. Eliminate any irrelevant data or data that does not fall within the scope of the request.
- Verify Data Accuracy: Ensure the accuracy of the retrieved data. Cross-reference the data with other sources, if necessary, to confirm its validity.
- Document Findings: Document the data located, including the source, the data type, and any relevant context. This documentation will be essential for compiling the final response to the data subject.
Methods for Retrieving Data from Various Sources
Retrieving data effectively involves employing different methods depending on the data source. Each source requires a specific approach to ensure that the correct data is extracted and that the process is compliant with GDPR regulations.
- Databases: Use SQL queries to extract data. Identify the relevant tables and fields containing the data subject’s information.
Example SQL query:
SELECT
- FROM users WHERE email = '[email protected]'; - Email Systems: Search email archives using s, sender/recipient information, and date ranges. Export relevant emails in a suitable format (e.g., .pst, .eml).
- CRM Systems: Utilize the CRM’s search functionality to locate the data subject’s records. Export the relevant data in a report format or other accessible format.
- Cloud Storage: Search cloud storage platforms (e.g., Google Drive, Dropbox) using the data subject’s name or email address. Download relevant files.
- Physical Files: Manually search physical files (e.g., paper documents, contracts). Scan or photograph relevant documents. Ensure that any personal data extracted from physical files is handled securely.
- Other Systems: For other systems, such as HR systems or marketing automation platforms, use the system’s search and reporting features to extract the relevant data.
Data Retrieval Procedures for Different Data Types
The procedure for retrieving data varies depending on the data type. Ensuring the data is retrieved accurately and in a suitable format is crucial for fulfilling the DSAR.
- Text Data: Extract text data from various sources (e.g., emails, documents, database fields). Ensure that the text is presented in a readable format.
- Image Data: Retrieve image data from sources such as photos, scanned documents, or social media profiles. Ensure the images are provided in a format that the data subject can easily access (e.g., JPEG, PNG). Consider any privacy implications when providing image data, such as blurring or redacting sensitive information.
- Audio Data: Retrieve audio data from recordings or voice messages. Provide the audio files in a common format (e.g., MP3, WAV). Ensure compliance with any relevant regulations regarding the recording of audio data.
- Video Data: Retrieve video data from recordings or video files. Provide the video files in a common format (e.g., MP4). Similar to audio data, compliance with regulations is crucial.
- Structured Data: Retrieve structured data from databases, spreadsheets, or other structured data sources. Provide the data in a format that can be easily accessed and understood (e.g., CSV, Excel). Consider formatting the data in a clear and organized manner.
- Location Data: Retrieve location data from GPS logs or other location-tracking services. Provide the location data in a format that can be easily visualized or understood (e.g., a list of coordinates or a map). Be mindful of the sensitivity of location data and consider any privacy implications.
Determining the Scope of the Request

Defining the scope of a Data Subject Access Request (DSAR) is a crucial step in ensuring compliance with the General Data Protection Regulation (GDPR). Accurately understanding what data the data subject is seeking is essential for a proportionate and effective response. This involves carefully interpreting the request and, if necessary, seeking clarification from the data subject.
Defining the Scope of a DSAR
Defining the scope involves precisely identifying the data the data subject is requesting. This process requires careful consideration of the wording of the request and a thorough understanding of the data processing activities of the organization.The following are key aspects to consider when defining the scope:
- Understanding the Request’s Wording: The initial step is to carefully read the DSAR and identify the specific data the data subject is requesting. Look for s, such as “all data,” “specific categories of data,” or references to specific services or interactions.
- Identifying the Data Subject’s Intent: Consider the context of the request. What is the data subject trying to achieve? Understanding their motivation can help clarify the scope. For instance, if the data subject mentions a specific transaction or interaction, the scope might be limited to data related to that event.
- Considering Data Processing Activities: Review the organization’s data processing activities to understand what data is held and how it is used. This involves reviewing privacy notices, data inventories, and any other documentation that Artikels data processing practices. This helps to identify the data potentially relevant to the request.
- Documenting the Scope: Clearly document the determined scope. This documentation should include the specific data categories, timeframes, and processing activities covered by the request. This documentation serves as a reference throughout the DSAR process.
Handling Overly Broad or Ambiguous Requests
DSARs can sometimes be overly broad or ambiguous, making it difficult to determine the precise data the data subject is seeking. Handling these types of requests requires a proactive approach.The following strategies can be used to manage overly broad or ambiguous requests:
- Acknowledging the Request and Explaining the Issue: Acknowledge the DSAR promptly and inform the data subject that the request appears broad or unclear. Explain the difficulties in identifying the requested data without further clarification.
- Providing Examples of Data Held: Provide examples of the types of data the organization typically holds about the data subject. This can help the data subject narrow down their request.
- Suggesting Specific Data Categories: Suggest specific data categories or timeframes to help the data subject refine their request. For instance, if the request is for “all data,” suggest limiting it to “data related to marketing activities” or “data from the last year.”
- Seeking Clarification in Writing: Request clarification from the data subject in writing, outlining the specific information needed to process the request effectively. This creates a clear record of the communication.
- Providing a Reasonable Estimate: If the organization anticipates a significant effort to comply with a very broad request, provide a reasonable estimate of the time and resources required. This can help the data subject understand the implications of their request and potentially refine it.
Communicating with the Data Subject to Clarify the Request
Effective communication is crucial when clarifying a DSAR. Clear and respectful communication helps to build trust and ensures a positive experience for the data subject.The following communication strategies are recommended:
- Using Clear and Concise Language: Avoid technical jargon and use plain language that the data subject can easily understand.
- Being Respectful and Empathetic: Show respect for the data subject’s rights and demonstrate empathy for their concerns.
- Providing Options and Alternatives: Offer options to help the data subject refine their request. For example, if the request is for “all emails,” suggest limiting it to emails from a specific sender or within a certain timeframe.
- Documenting all Communication: Keep a detailed record of all communication with the data subject, including the date, time, and content of each interaction. This documentation is essential for demonstrating compliance.
- Setting Reasonable Timelines: Set reasonable timelines for responding to the data subject’s request for clarification and for providing the requested data. This demonstrates a commitment to timely compliance.
- Offering Multiple Communication Channels: Provide multiple communication channels, such as email, phone, or a dedicated portal, to make it easier for the data subject to respond.
Redacting and Protecting Data

Once you’ve identified the data subject’s personal data, the next crucial step is to redact and protect it. This process ensures compliance with GDPR by minimizing the risk of unauthorized disclosure. It balances the data subject’s right to access their information with the need to protect the privacy of others and the confidentiality of your organization’s data.
Importance of Data Redaction
Data redaction is vital for complying with GDPR. It involves permanently removing or obscuring sensitive information from a document or dataset before sharing it with the data subject. This practice protects the privacy of other individuals and confidential business information. Failing to redact data appropriately can lead to significant penalties, including fines of up to 4% of annual global turnover or €20 million, whichever is greater.
It also undermines trust with data subjects and can damage your organization’s reputation.
Redaction Techniques for Various Data Formats
Different data formats require specific redaction techniques to ensure effective protection. The appropriate method depends on the nature of the data and the format in which it is stored.
- Text Documents (e.g., Word, PDF): For text documents, common redaction methods include:
- Blackening/Blocking: This involves covering the sensitive information with a black box or solid color. This is a straightforward method but can be vulnerable if the underlying text is not permanently removed.
- Redaction with Metadata Removal: Using specialized redaction software, the sensitive information is removed, and the associated metadata (e.g., hidden text, comments) is also stripped to prevent potential recovery.
- Replacement: Substituting sensitive data with generic terms or placeholders. For example, replacing a name with “Individual X” or a phone number with “[REDACTED]”.
- Images: Redacting images presents unique challenges. Methods include:
- Pixelization/Blurring: Obscuring sensitive information by blurring or pixelating it. This is commonly used for faces, license plates, or other identifiable features.
- Overlaying: Covering sensitive information with a solid color or shape.
- Spreadsheets (e.g., Excel): For spreadsheets, redaction involves:
- Deleting Columns/Rows: Removing entire columns or rows containing sensitive data.
- Hiding Columns/Rows: Concealing sensitive data while retaining the spreadsheet’s structure. Note that hidden data can sometimes be easily revealed.
- Replacing Values: Substituting sensitive data with generic terms or placeholders.
- Databases: Redaction in databases requires a more technical approach:
- Data Masking: Replacing sensitive data with realistic but fictitious values. For example, replacing a real social security number with a randomly generated one.
- Data Anonymization: Transforming data in a way that makes it impossible to identify the data subject. This may involve removing direct identifiers or aggregating data.
- Pseudonymization: Replacing direct identifiers with pseudonyms (e.g., a unique code). This allows for data analysis without revealing the data subject’s identity directly.
Scenarios Where Data May Need to Be Withheld
Under GDPR, there are specific circumstances where data can be withheld from a data subject. These exceptions are crucial for protecting the rights and freedoms of others, safeguarding confidential business information, and ensuring the proper functioning of legal processes.
- Data Relating to Other Individuals: If the data subject’s request includes personal data about other individuals, and disclosing that data would reveal their personal information, the data must be redacted or withheld. For example, if a request includes emails with correspondence between the data subject and another employee, the other employee’s personal information must be protected.
- Confidential Business Information: Information that, if disclosed, would harm the organization’s trade secrets, intellectual property, or competitive position can be withheld. This includes sensitive financial data, internal strategies, and confidential client information. For example, a DSAR requesting access to internal project documents could have commercially sensitive information redacted.
- Legal Professional Privilege: Communications between a lawyer and their client are protected by legal professional privilege. These communications do not need to be disclosed in response to a DSAR.
- Ongoing Legal Proceedings: Data related to ongoing legal proceedings may be withheld if disclosure would prejudice those proceedings.
- National Security and Public Interest: In exceptional circumstances, data may be withheld if disclosure could compromise national security, public safety, or the prevention of crime.
Exceptions and Limitations to DSARs
While the GDPR grants individuals extensive rights regarding their personal data, these rights are not absolute. There are specific circumstances where a data controller can refuse to fulfill a Data Subject Access Request (DSAR) or limit the information provided. Understanding these exceptions is crucial for compliance and maintaining a balance between individual rights and legitimate business interests.
Circumstances for Refusal of a DSAR
The GDPR provides a framework for when a DSAR can be justifiably refused. These refusals must be based on legitimate grounds and are subject to scrutiny by supervisory authorities.
- Manifestly Unfounded Requests: A request is considered manifestly unfounded if it is clear that the request has no genuine basis. This can include requests that are repetitive, frivolous, or intended to harass the data controller. For example, a data subject making numerous requests for the same information within a short period without any new justification could be considered manifestly unfounded.
- Excessive Requests: A request is excessive if it places an unreasonable burden on the data controller, considering the nature of the data and the resources required to fulfill the request. This determination is based on the volume of data, the complexity of the retrieval process, and the frequency of requests from the same data subject. For example, a request for all emails exchanged with a company over the past decade might be considered excessive.
- Requests that are not related to the data subject: If the data requested does not concern the data subject making the request, it can be refused. For example, if the data subject is requesting information about another individual, the request can be refused.
Valid Reasons for Withholding Data
There are several specific reasons why a data controller might withhold data in response to a DSAR. These reasons are often linked to balancing individual rights with the rights and freedoms of others, as well as the legitimate interests of the data controller.
- Protection of the Rights and Freedoms of Others: This is a key consideration. If disclosing the requested data would reveal personal information about another individual, or would infringe upon their rights, the data controller may withhold the information. For instance, if the data contains information about a third party’s health or financial situation, that information would be withheld unless the third party consents.
- Legal Obligations: Data controllers may be required by law to withhold certain information. This might include data subject to legal privilege, or information that would violate a court order.
- Trade Secrets and Intellectual Property: Information that would reveal a company’s trade secrets or infringe on its intellectual property rights may be withheld. This exception protects a company’s competitive advantage and confidential business information. For example, the withholding of specific algorithms or financial models could be justified.
- Ongoing Legal Proceedings: Data that is relevant to ongoing legal proceedings might be withheld if its disclosure would prejudice those proceedings. This is designed to protect the integrity of the legal process.
- Public Security and National Security: In exceptional circumstances, data may be withheld to protect national security, public safety, or the prevention of crime. This is a narrow exception, and its use would be subject to strict scrutiny.
Legal Requirements for Informing the Data Subject of a Refusal
If a data controller decides to refuse a DSAR, they have specific obligations to the data subject. Failure to meet these obligations can result in penalties.
- Communication of the Refusal: The data controller must inform the data subject of the refusal without undue delay and at the latest within one month of receiving the request. This communication must be clear, concise, and transparent.
- Justification for the Refusal: The data controller must provide the data subject with the reasons for the refusal. This explanation should be specific and refer to the relevant grounds for refusal under the GDPR.
- Information on the Right to Complain: The data controller must inform the data subject of their right to lodge a complaint with a supervisory authority (e.g., a data protection authority) and their right to seek a judicial remedy. This information must include the contact details of the relevant supervisory authority.
- Timeliness: The response must be provided within the same timeframe as the initial response to the DSAR – usually within one month, extendable by a further two months if the request is complex.
DSARs and Third-Party Data
Handling Data Subject Access Requests (DSARs) involving third-party data presents unique challenges under GDPR. It requires a careful balancing act between the data subject’s right to access their personal data and the protection of the privacy of other individuals. This section Artikels the considerations and procedures necessary for navigating these complexities.
Challenges of Processing Third-Party Data
Processing third-party data within a DSAR can be complex, often requiring significant effort to ensure compliance. Several key challenges arise in these situations.
- Identifying Third-Party Data: Accurately identifying and isolating data relating to third parties within the scope of a DSAR can be time-consuming. This often involves reviewing large datasets and cross-referencing information.
- Data Minimization and Relevance: The principle of data minimization requires that only relevant personal data is processed. Determining the relevance of third-party data to the data subject’s request requires careful consideration of the context and purpose of the processing.
- Balancing Rights: Balancing the data subject’s right of access with the rights and freedoms of the third party, including their right to privacy, is crucial. This may involve redacting or withholding certain information.
- Obtaining Consent (if applicable): In some instances, it may be necessary to obtain consent from the third party before disclosing their personal data. However, this is not always feasible or legally required, and relying on legitimate interests is often more appropriate.
- Practical Difficulties: The format in which data is stored can make it difficult to identify and isolate third-party information. For example, unstructured data in emails or documents can require manual review and redaction.
Protocol for Notifying Third Parties
When third-party data is implicated in a DSAR, a clear protocol for notification and handling is essential. This ensures fairness, transparency, and compliance with GDPR.
- Assessment and Determination: Before taking any action, carefully assess whether the third-party data is genuinely relevant to the DSAR and whether disclosure is lawful and proportionate. This involves considering the nature of the data, the relationship between the data subject and the third party, and the potential impact of disclosure.
- Notification Trigger: Notify the third party if their personal data is likely to be disclosed in response to the DSAR. The notification should be timely, ideally before the data is disclosed, to allow the third party an opportunity to respond.
- Content of Notification: The notification should include:
- Identification of the data subject making the request.
- A description of the data that will be disclosed.
- The legal basis for disclosing the data (e.g., legitimate interest, consent).
- The purpose of the disclosure.
- Information about the third party’s rights, including the right to object to the disclosure or to request that the data be corrected or deleted.
- Method of Notification: The notification method should be appropriate to the sensitivity of the data and the relationship with the third party. This could include email, registered mail, or a phone call. Consider using a secure communication channel, especially for sensitive data.
- Handling Third-Party Objections: If the third party objects to the disclosure, carefully consider their objections. Assess whether the objections are valid and whether the disclosure can be modified or withheld to protect the third party’s rights. Document the decision-making process.
- Redaction and Anonymization: Where possible, redact or anonymize the third-party data to minimize the impact on their privacy. This may involve removing names, contact details, or other identifying information.
- Documentation and Record-Keeping: Maintain thorough records of all steps taken, including the assessment, the notification, any objections received, and the final decision. This documentation is crucial for demonstrating compliance with GDPR.
The European Data Protection Board (EDPB) has issued guidelines on the right of access, providing further guidance on handling third-party data in DSARs. These guidelines emphasize the importance of balancing the rights of the data subject and the third party, and they provide detailed examples of situations where redaction or withholding data may be appropriate.
DSARs and Automated Decision-Making
When automated decision-making is employed, Data Subject Access Requests (DSARs) take on an added layer of complexity. The GDPR places significant emphasis on transparency and the right to understand how decisions are made about an individual. This means that when an automated system makes a decision affecting a data subject, they have the right to access information about that process.
This includes the logic involved, the data used, and the impact of the decision.
Impact of DSARs on Automated Decision-Making
The involvement of automated decision-making significantly amplifies the scope of DSARs. Individuals have a right to understand how their data is used in algorithmic processes that significantly affect them. This requires organizations to provide detailed information about the automated decision-making process, including the criteria used, the data sources, and the reasoning behind the decisions.
Handling Requests Related to Algorithmic Processes
Responding to DSARs concerning algorithmic processes requires a structured approach. The following points Artikel key considerations:
- Understanding the Algorithmic Process: A comprehensive understanding of the algorithm is paramount. This involves knowing the data inputs, the processing steps, and the outputs. For example, in a loan application process, understand how the credit score, income data, and other factors are weighted and combined to generate a loan decision.
- Identifying the Data Used: Clearly identify the specific data points utilized by the automated system. This includes both the direct inputs and any derived data used in the decision-making process. In the same loan example, this includes the applicant’s credit history, employment details, and existing debts.
- Explaining the Logic: Provide a clear and concise explanation of the algorithm’s logic. This should include information about the key parameters, the decision rules, and the relative importance of different data points. It might involve explaining how a higher credit score influences the interest rate offered.
- Describing the Impact: Detail the impact of the automated decision on the data subject. This includes the specific outcome of the decision (e.g., loan approved or denied) and the reasons behind it. This should also cover any consequences of the decision, such as the interest rate charged or the terms of the loan.
- Providing Information on Data Sources: Explain where the data used in the process originated. This transparency allows the data subject to assess the reliability and potential biases of the data. For example, if credit history is sourced from a specific credit bureau, that should be disclosed.
- Providing the Right to Rectification and Erasure: Ensure that the data subject’s right to rectify inaccurate data or have data erased is facilitated. If the algorithm relies on incorrect or outdated data, the data subject should be able to request corrections or deletion.
Best Practices for Transparency in Automated Decision-Making
Transparency is critical when dealing with automated decision-making and DSARs. Organizations should adhere to the following best practices:
- Documentation: Maintain detailed documentation of all automated decision-making processes. This documentation should include the algorithm’s design, data inputs, processing steps, and outputs. This documentation is invaluable when responding to DSARs.
- User-Friendly Explanations: Provide explanations of the automated decision-making process in clear, plain language that is easy for the data subject to understand. Avoid using overly technical jargon.
- Data Minimization: Use only the data that is strictly necessary for the automated decision-making process. This helps to limit the scope of data access requests and reduces the risk of exposing sensitive information.
- Human Oversight: Implement human oversight mechanisms where appropriate. This could involve human review of decisions made by the automated system, especially in cases where the decision has a significant impact on the data subject. For example, in high-stakes decisions, such as loan approvals or job applications, a human reviewer can provide a second opinion.
- Regular Audits: Conduct regular audits of the automated decision-making processes to ensure they are fair, accurate, and compliant with GDPR. These audits can help identify and address any biases or errors in the algorithm.
- Provide a Point of Contact: Offer a clear point of contact for data subjects to ask questions and seek clarification about automated decision-making processes. This demonstrates a commitment to transparency and accountability.
- Consider Explainable AI (XAI) techniques: Explore the use of XAI techniques to make the decision-making process more transparent and understandable. XAI can provide insights into how the algorithm arrived at a particular decision.
Best Practices and Ongoing Compliance
Maintaining compliance with Data Subject Access Request (DSAR) regulations is an ongoing process. It requires proactive measures, including establishing robust internal policies, comprehensive employee training, and consistent monitoring. This section details how to create an internal DSAR policy, train employees effectively, and implement a checklist for continuous compliance.
Creating an Internal DSAR Policy
An internal DSAR policy serves as a crucial guide for handling requests consistently and efficiently. It ensures that all employees understand their roles and responsibilities. The policy should be clear, concise, and readily accessible to all relevant personnel.To create an effective internal DSAR policy, consider the following elements:
- Purpose and Scope: Clearly state the policy’s purpose, which is to comply with GDPR and other relevant data protection laws. Define the scope, specifying which departments or employees the policy applies to.
- Definitions: Provide clear definitions of key terms such as “data subject,” “personal data,” “DSAR,” “processing,” and “controller.” This ensures a shared understanding across the organization.
- Roles and Responsibilities: Define the roles and responsibilities of different individuals and departments involved in handling DSARs. This should include who is responsible for receiving requests, verifying identities, locating and retrieving data, redacting information, and communicating with the data subject.
- Request Process: Artikel the step-by-step process for handling DSARs. This should include how requests can be submitted (e.g., email, online form, physical mail), timelines for responding (within one month), and the information required from the data subject to verify their identity.
- Data Retrieval and Processing: Describe the methods for locating and retrieving data, including the use of search tools and data management systems. Explain how data will be processed, including any redaction or anonymization techniques.
- Exceptions and Limitations: Detail any exceptions or limitations to the right of access, such as requests that are manifestly unfounded or excessive, or situations where providing the data would adversely affect the rights and freedoms of others.
- Third-Party Data: Address how to handle requests involving third-party data, including the need to obtain consent or anonymize the data.
- Automated Decision-Making: Explain how to handle DSARs related to automated decision-making, including providing information about the logic involved.
- Record Keeping: Specify the requirements for maintaining records of DSARs, including the date of the request, the information provided, and the response.
- Review and Updates: Establish a process for regularly reviewing and updating the policy to reflect changes in data protection laws and organizational practices. This should include the frequency of reviews and who is responsible for updates.
Providing Training on DSAR Procedures
Effective training is essential for ensuring that employees understand and can implement the DSAR policy. Training should be ongoing and tailored to the specific roles and responsibilities of each employee.Steps for creating a comprehensive employee training program include:
- Identify Training Needs: Assess the current knowledge and skills of employees related to DSAR procedures. This can be done through surveys, interviews, or reviewing previous DSAR handling experiences.
- Develop Training Materials: Create training materials that are clear, concise, and easy to understand. These materials should include the following:
- A summary of the GDPR and its requirements related to DSARs.
- A detailed explanation of the internal DSAR policy.
- Step-by-step instructions on how to handle DSARs, including how to receive requests, verify identities, locate and retrieve data, redact information, and communicate with data subjects.
- Examples of different types of DSARs and how to respond to them.
- Scenarios and case studies to help employees apply the policy in real-world situations.
- Choose Training Methods: Select appropriate training methods, such as:
- In-person training sessions: Allow for direct interaction and Q&A.
- Online training modules: Provide flexibility and accessibility.
- Webinars: Facilitate interactive learning from remote locations.
- Hands-on exercises: Reinforce learning through practical application.
- Role-playing exercises: Simulate real-life DSAR scenarios.
- Deliver Training: Ensure that all relevant employees receive training. Training should be provided to new employees as part of their onboarding process. Regular refresher training should be conducted to keep employees up-to-date on the latest developments.
- Assess Training Effectiveness: Evaluate the effectiveness of the training program. This can be done through:
- Quizzes and tests: Assess employee understanding of the material.
- Feedback from employees: Gather insights on the training program’s clarity and relevance.
- Monitoring DSAR handling: Observe how employees handle DSARs in practice.
- Reviewing DSAR responses: Assess the accuracy and completeness of responses.
- Update Training Materials: Regularly update training materials to reflect changes in the DSAR policy, data protection laws, and organizational practices.
Designing a Checklist for Ongoing Compliance
A checklist provides a structured approach to ensure ongoing compliance with DSAR requirements. It helps to identify and address any gaps in processes, and it can be used to track progress over time. The checklist should be reviewed and updated regularly.An example checklist might include the following:
| Task | Frequency | Responsibility | Status | Notes |
|---|---|---|---|---|
| Review and update the DSAR policy | Annually | Data Protection Officer (DPO) | Ensure alignment with current data protection laws and organizational changes. | |
| Conduct employee training on DSAR procedures | Annually and for new hires | DPO/Training Department | Ensure all relevant employees are aware of the latest DSAR requirements. | |
| Monitor DSAR handling | Quarterly | DPO/Compliance Team | Review a sample of DSAR responses for accuracy and compliance. | |
| Conduct data audits | Annually | IT/Data Management Team | Verify that data is stored securely and in compliance with GDPR requirements. | |
| Review and update data processing agreements | As needed | Legal/DPO | Ensure that all agreements with third-party processors comply with GDPR. | |
| Maintain a DSAR log | Ongoing | Relevant Department | Track all DSARs received and responses provided. | |
| Address data breaches promptly | As needed | DPO/Incident Response Team | Ensure data breaches are reported to the relevant authorities and data subjects within the required timeframe. | |
| Conduct regular security assessments | Annually | IT/Security Team | Identify and address any vulnerabilities in data security systems. |
Concluding Remarks
In conclusion, mastering the intricacies of handling a data subject access request (DSAR) under GDPR is essential for any organization committed to data privacy. By implementing the strategies Artikeld in this guide, you can streamline your processes, ensure compliance, and foster trust with your data subjects. Remember, continuous learning and adaptation are key in this evolving field, so stay informed and proactively refine your approach to data privacy.
Top FAQs
What is the typical timeframe for responding to a DSAR?
You generally have one month from the date of receiving the request to respond. This timeframe can be extended by two months for complex requests, but you must inform the data subject within the initial month if an extension is needed.
Can a DSAR be submitted verbally?
While not strictly prohibited, it’s best practice to receive DSARs in writing (email or letter) for record-keeping purposes. This helps ensure clarity and provides a documented audit trail.
What happens if a data subject requests information that I don’t have?
You must inform the data subject if you don’t hold the requested personal data. You may need to search all your systems, and if you find nothing, you must state this in your response. Keep a record of the search you performed.
Are there any fees associated with responding to a DSAR?
Generally, there is no fee for responding to a DSAR. However, if a request is manifestly unfounded or excessive, you may charge a reasonable fee or refuse to act on the request. You must justify this decision to the data subject.
What is the difference between a DSAR and a request for rectification or erasure?
A DSAR is a request for access to the data a company holds about an individual. Rectification is a request to correct inaccurate data, and erasure (also known as the “right to be forgotten”) is a request to delete data. While related, these are distinct rights under GDPR.