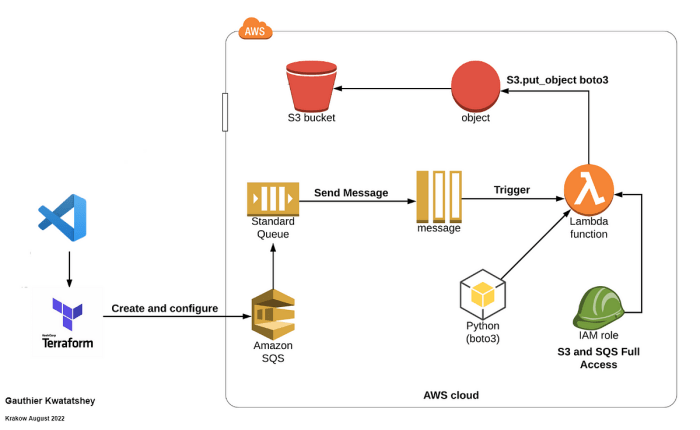
Using SQS to Trigger Lambda Functions: A Comprehensive Guide
This comprehensive guide explores how to leverage Amazon SQS as a trigger for your AWS Lambda functions, enabling robust, event-driven architectures....
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This comprehensive guide explores how to leverage Amazon SQS as a trigger for your AWS Lambda functions, enabling robust, event-driven architectures....
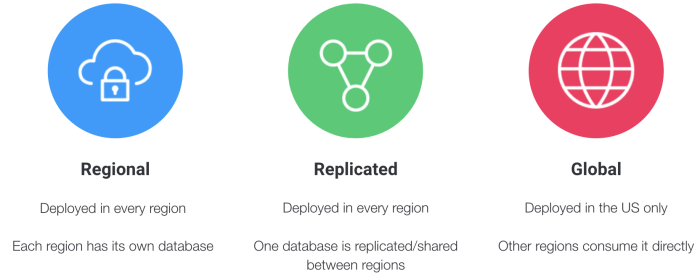
Multi-region architecture, while offering enhanced scalability, availability, and disaster recovery capabilities, demands careful planning for success...

This comprehensive guide outlines the critical steps for enforcing mandatory tagging across all resources, ensuring improved organization, compliance,...
Securing cloud resources is critical, and implementing Least Privilege Access (LPA) is a foundational security practice. LPA limits user and applicati...

This comprehensive guide explores the essential strategies for continuous cloud optimization, covering crucial areas like cost management, performance...
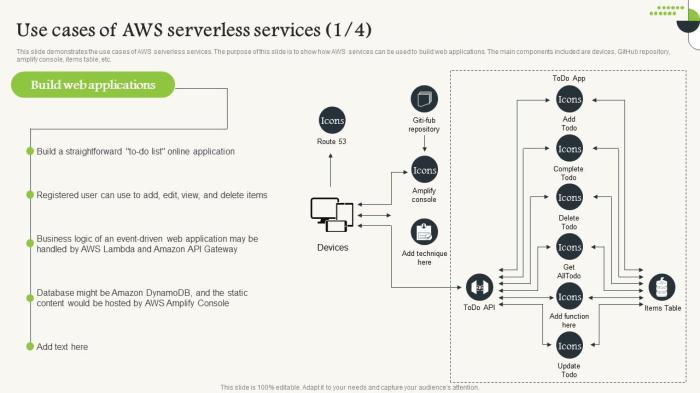
The serverless-first development approach is revolutionizing software architecture by making serverless computing the cornerstone of application desig...
This comprehensive guide explores the development of real-time serverless applications using WebSockets, covering everything from fundamental concepts...

This article delves into the world of serverless frameworks, exploring their role in streamlining deployment automation for modern applications. From...
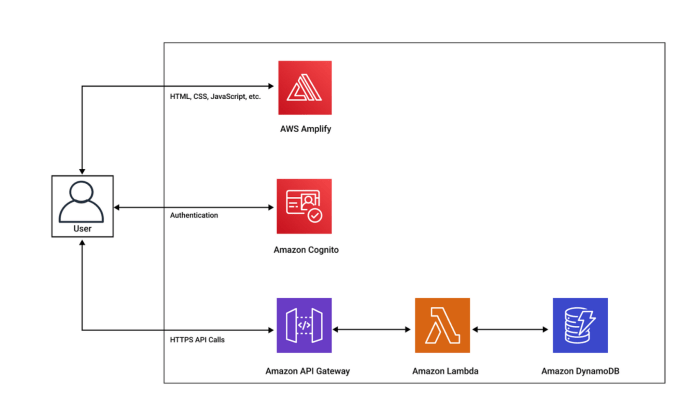
Serverless applications thrive on scalability, but managing state within their ephemeral nature presents a unique hurdle. This article explores how Dy...

Serverless environments, while offering scalability and agility, introduce unique security challenges due to their ephemeral and distributed nature. T...

This comprehensive guide delves into the critical practice of container vulnerability scanning, explaining its core concepts and importance in securin...
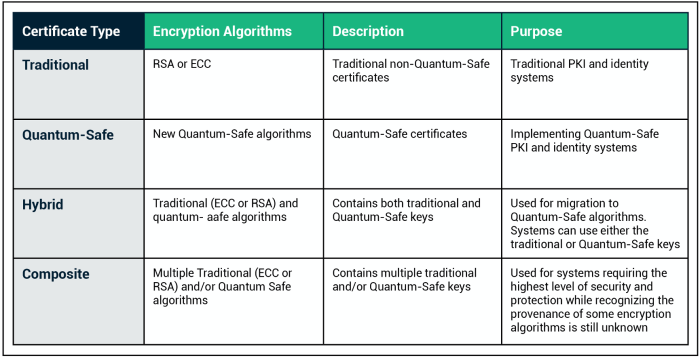
Explore the groundbreaking field of quantum cryptography and its revolutionary impact on cybersecurity in this comprehensive article. From fundamental...