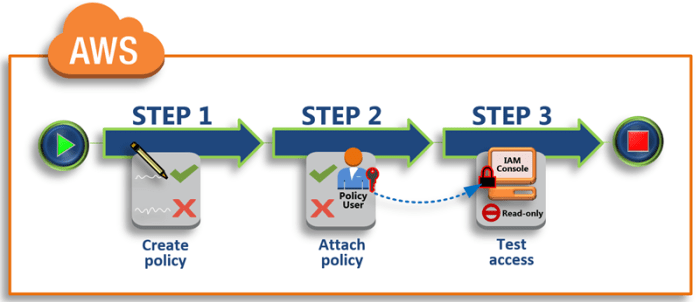
IAM Policies: Understanding and Implementing Secure Access Control
This comprehensive guide delves into the world of Identity and Access Management (IAM) policies, explaining their crucial role in securing access to y...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This comprehensive guide delves into the world of Identity and Access Management (IAM) policies, explaining their crucial role in securing access to y...

Facing Lambda deployment size limitations and slow cold starts? This comprehensive guide explores how to effectively manage large deployment packages...
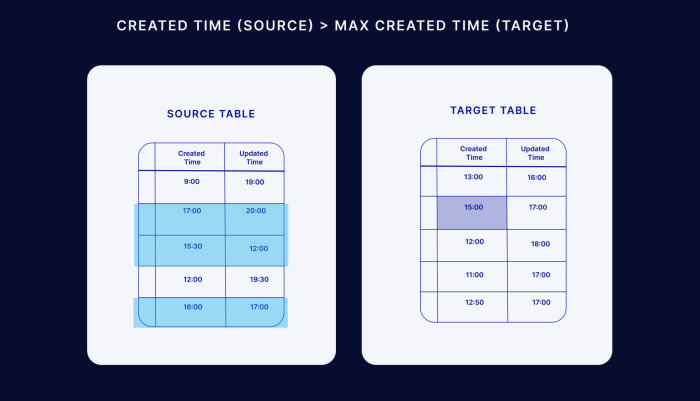
Change Data Capture (CDC) is a transformative data integration technique that streamlines data synchronization by focusing on capturing only the chang...
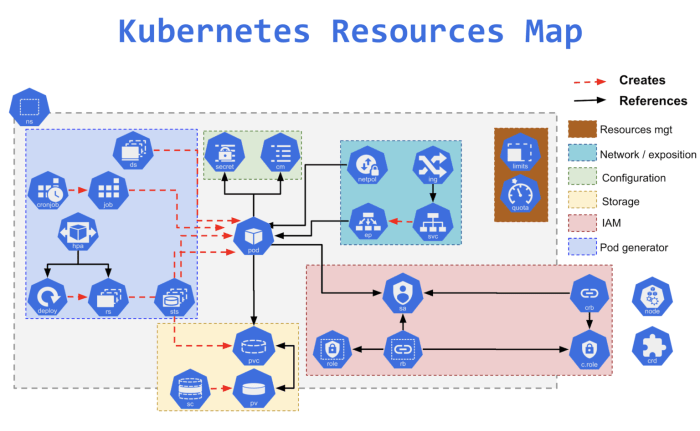
This article provides a comprehensive overview of the cost implications of Kubernetes, essential knowledge for businesses adopting container orchestra...
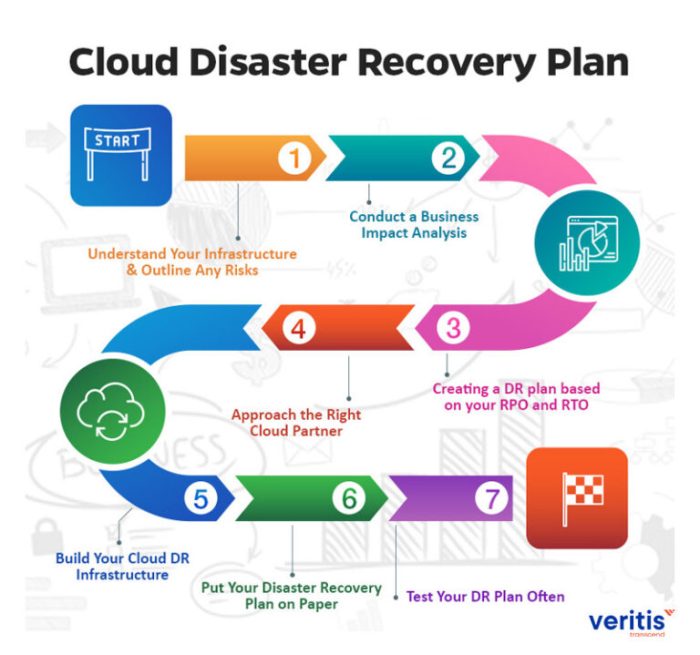
This comprehensive guide explores the critical elements of a cloud disaster recovery plan, covering everything from understanding core objectives and...
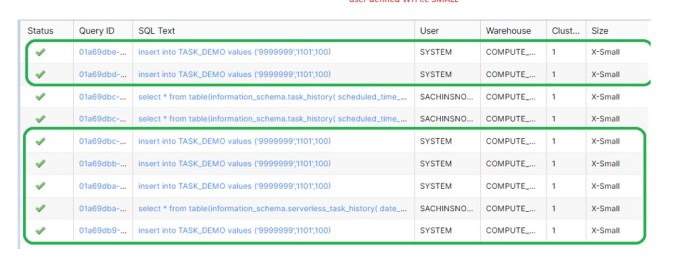
Serverless environments, while offering scalability and cost-efficiency, present challenges when executing tasks that exceed platform time limits. Thi...
Navigating the complexities of migration requires careful attention to legal and contractual obligations across various domains. This comprehensive gu...

This comprehensive guide explores Interactive Application Security Testing (IAST), detailing its fundamental principles, advantages, and practical imp...
Operational excellence is paramount in cloud design, offering a comprehensive strategy for building and managing cloud environments. This approach pri...

This article delves into the world of serverless stream processing, exploring its core components, benefits, and real-world applications. Readers wil...
This guide provides a detailed roadmap for developing a successful cloud-native database strategy. It covers crucial aspects like defining requirement...
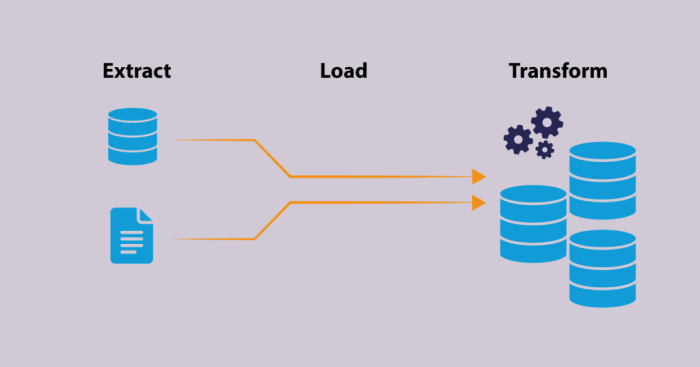
This article explores the transformative shift towards serverless ETL (Extract, Transform, Load) processes, detailing their core concepts, architectur...