
Detecting & Preventing Data Loss/Corruption After a Migration: A Comprehensive Guide
Migrating data requires meticulous planning to ensure data integrity throughout the process. This article provides a comprehensive guide to proactivel...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Migrating data requires meticulous planning to ensure data integrity throughout the process. This article provides a comprehensive guide to proactivel...

Ensuring business continuity in the cloud hinges on resilient network architecture. This guide provides a detailed overview of the core principles, st...

Discover insights and practical tips in this comprehensive guide about What Is A Data Lakehouse Architecture.
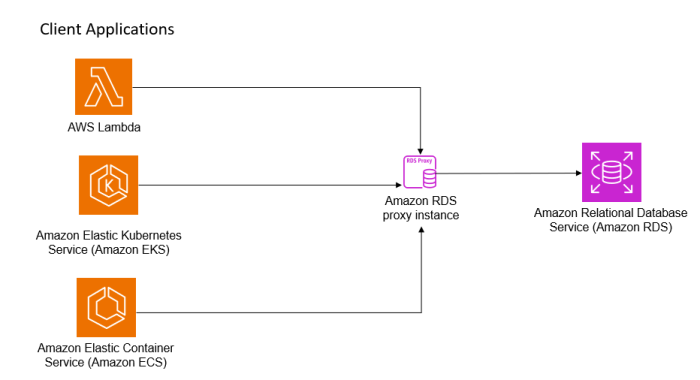
Amazon RDS Proxy provides a powerful solution for optimizing database connection management, which is critical for application performance and scalabi...

This comprehensive guide explores the crucial integration of FinOps into the DevOps lifecycle, providing a roadmap for optimizing cloud spending and f...
This comprehensive guide outlines the crucial steps for conducting regular cloud security risk assessments, ensuring the protection of your valuable a...
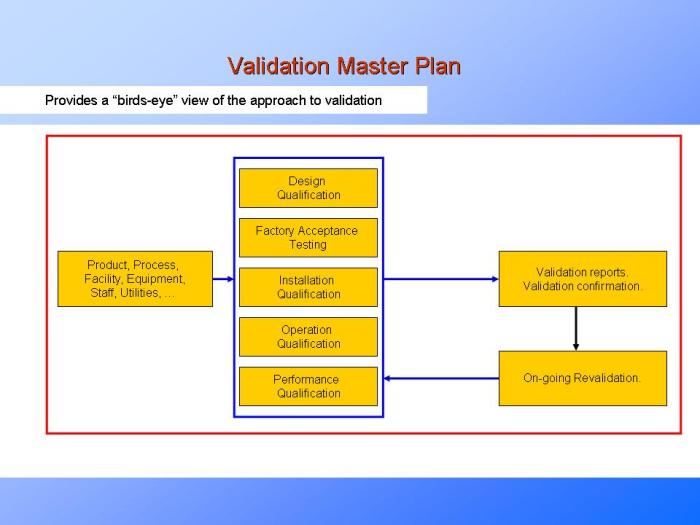
This comprehensive guide delves into the critical world of data validation and testing, exploring their core purpose within data management and the es...
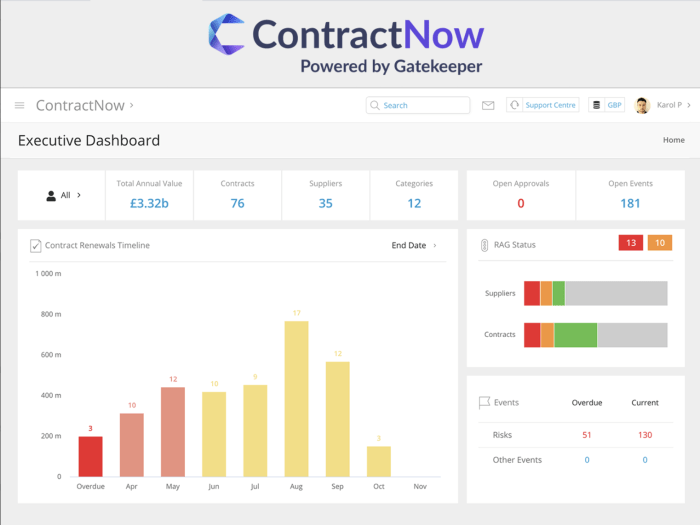
In today's cloud-driven world, negotiating cloud contracts and enterprise agreements is essential for optimizing costs and ensuring successful cloud a...
Cybersecurity Key Risk Indicators (KRIs) serve as vital early warning signals, enabling organizations to proactively manage and mitigate evolving cybe...

Navigate the complex legal landscape of cloud computing with this comprehensive guide. This article delves into critical areas like data privacy regul...

Serverless computing simplifies application development by abstracting away server management, allowing developers to focus solely on code. This moder...
This comprehensive article delves into the transformative technology of homomorphic encryption, exploring its core functionality, diverse types, and u...