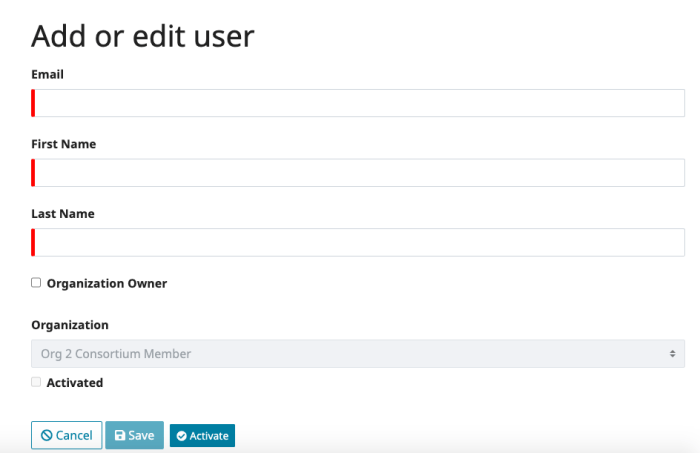
Managing Configuration Drift in Cloud Infrastructure: Best Practices and Strategies
Configuration drift, the insidious deviation of cloud infrastructure from its intended state, can lead to security vulnerabilities, performance degrad...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Configuration drift, the insidious deviation of cloud infrastructure from its intended state, can lead to security vulnerabilities, performance degrad...
Serverless data analytics is revolutionizing data processing through scalable, cost-effective, and agile solutions. This paradigm shift requires strat...
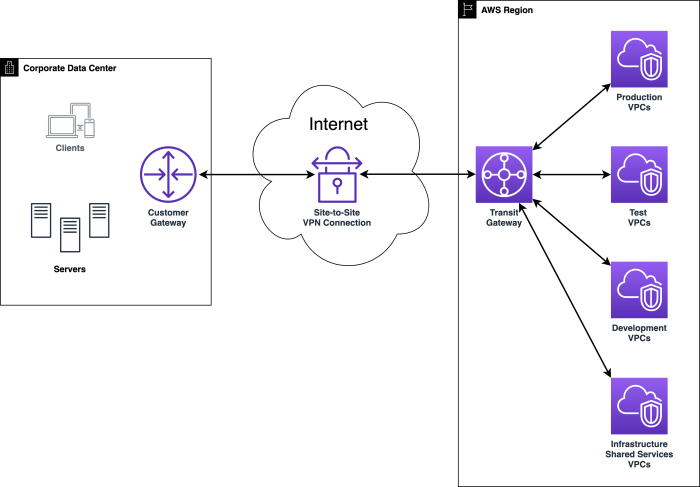
Understand the critical role of Virtual Private Networks (VPNs) in securing modern corporate communications. This article explores the core functional...

This article delves into the efficient and secure management of administrative tasks by introducing the concept of "Factor XII," a framework for execu...
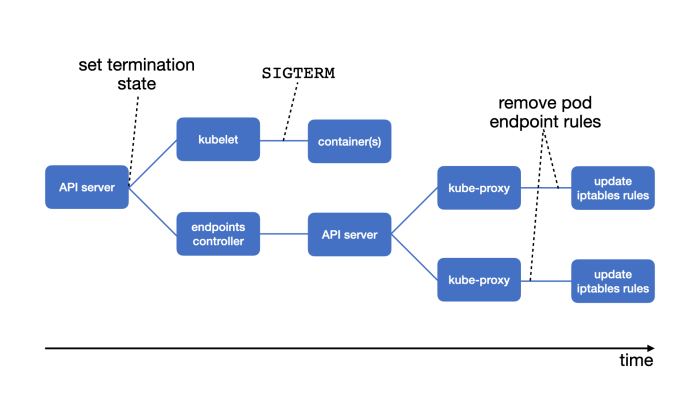
Kubernetes Network Policies act as cloud-native firewalls, providing essential security for containerized applications within your clusters. This arti...

Effectively managing cloud costs requires robust reporting practices, and this article provides a comprehensive guide to establishing them. It delves...
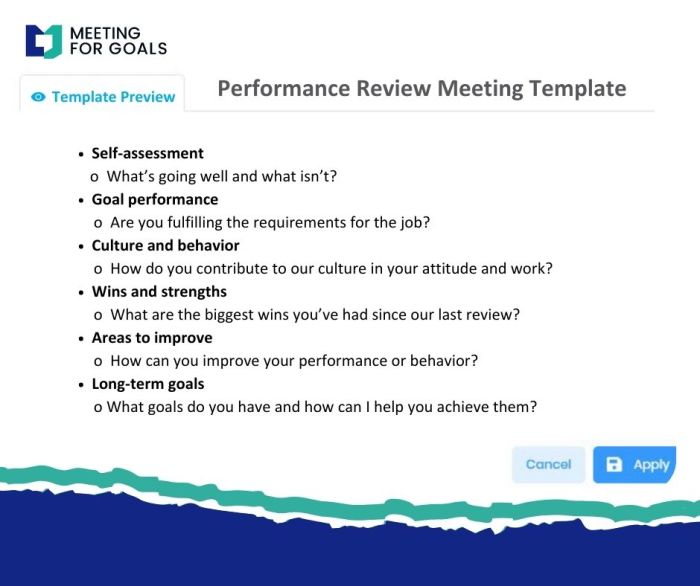
Navigating a cloud cost review meeting effectively is essential for optimizing cloud spending. This guide offers a structured approach, breaking down...

This article delves into the critical world of database version control, exploring its core concepts, benefits, and the common challenges encountered....

Migrating data to the cloud requires meticulous validation to ensure data integrity throughout the process. This comprehensive guide details essential...
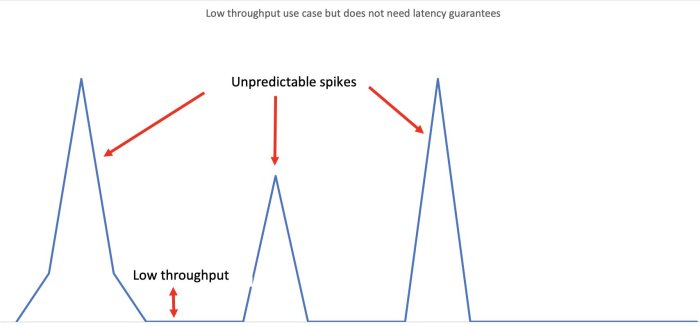
Serverless computing is revolutionizing machine learning inference by offering significant cost savings and unparalleled scalability for predictive mo...
Cloud architecture demands a strategic approach to ensure optimal performance and efficiency. This guide outlines key principles for designing, optimi...

Managing third-party contractor access is a crucial element of robust cybersecurity. This guide outlines essential strategies for securely granting ac...