
FedRAMP Authorization: A Guide to Cloud Security for Government
This comprehensive guide provides a detailed overview of FedRAMP, the critical security authorization program for cloud services used by the U.S. gove...
152 posts in this category

This comprehensive guide provides a detailed overview of FedRAMP, the critical security authorization program for cloud services used by the U.S. gove...
Managing resources across multiple cloud providers like AWS, Azure, and GCP introduces complex challenges for consistent security and access control d...

Digital Rights Management (DRM) is a critical component of the digital landscape, serving to protect intellectual property in the realm of content cre...

This comprehensive article delves into the emerging field of Confidential Computing, defining its core concepts, key technologies, and significant ben...

Cloud environments present unique challenges for security forensics, but understanding the core principles is crucial for effective investigation. Thi...

This comprehensive guide to Cloud Identity and Access Management (IAM) explores core concepts, best practices, and emerging trends to secure your clou...

This comprehensive guide explores Interactive Application Security Testing (IAST), detailing its fundamental principles, advantages, and practical imp...
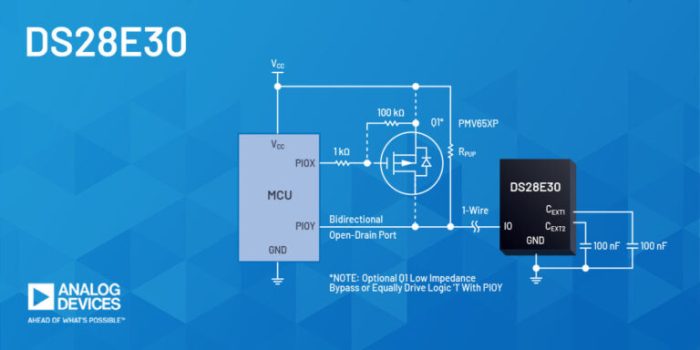
The proliferation of Internet of Things (IoT) devices necessitates robust security measures to protect against increasingly sophisticated cyber threat...

This article provides a comprehensive overview of the roles and responsibilities within a Security Operations Center (SOC), crucial for modern cyberse...

This article delves into the intricacies of legal hold and eDiscovery, focusing on the significant advantages of leveraging cloud technology for these...
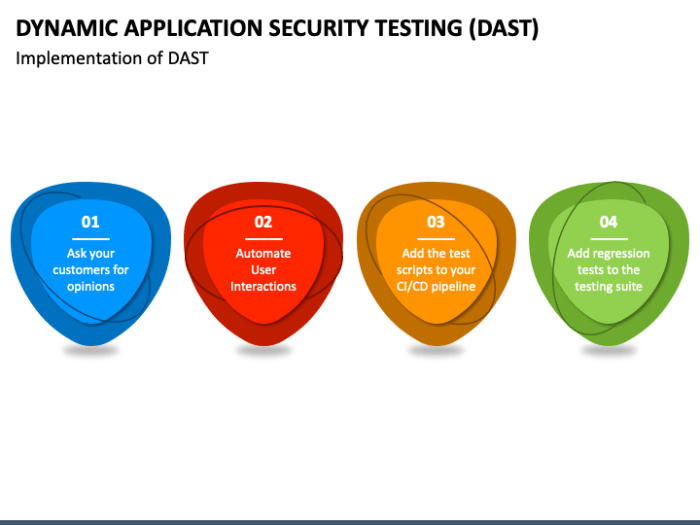
This comprehensive guide explores Dynamic Application Security Testing (DAST), providing a deep dive into its core concepts, functionality, and practi...

Managing third-party contractor access is a crucial element of robust cybersecurity. This guide outlines essential strategies for securely granting ac...